Update 6/6/2017: We updated this post to reflect availability for China plans.
Update 7/28/2017: Updated with links for support with Outlook for iOS and Android.
On-premises Exchange environments support the ability for certain mobile apps to utilize certificate-based authentication (CBA). Today, we are pleased to announce that CBA is available for customers using Office 365 Enterprise, Business, Education, Government, and China plans. This does not include Office 365 Defense. It will be available for Office 365 Defense and other Office 365 plans at a later date. This feature is available in Outlook for iOS, Outlook for Android and the Exchange ActiveSync (EAS) protocol.What is certificate-based authentication?
CBA allows users to authenticate using a client certificate. The certificate is used in place of the user entering credentials into the device.Why would I want certificate-based authentication?
By utilizing certificate-based authentication, administrators can allow their users to access resources without the need to enter credentials.Prerequisites
The following are required to use CBA:- Access to a certification authority (CA) to issue client certificates.
- For Office mobile clients, like Outlook for iOS & Android, a federation server; for more information on how to configure, see ADFS: Certificate Authentication with Azure AD & Office 365.
- Each CA must have a certificate revocation list (CRL) that can be referenced via an Internet-facing URL.
- Client certificates must be provisioned on mobile devices, typically done using MDM.
- For EAS clients, the RFC822 Name OR Principal Name value in the certificate’s Subject Alternative Name field must have the user’s email address.
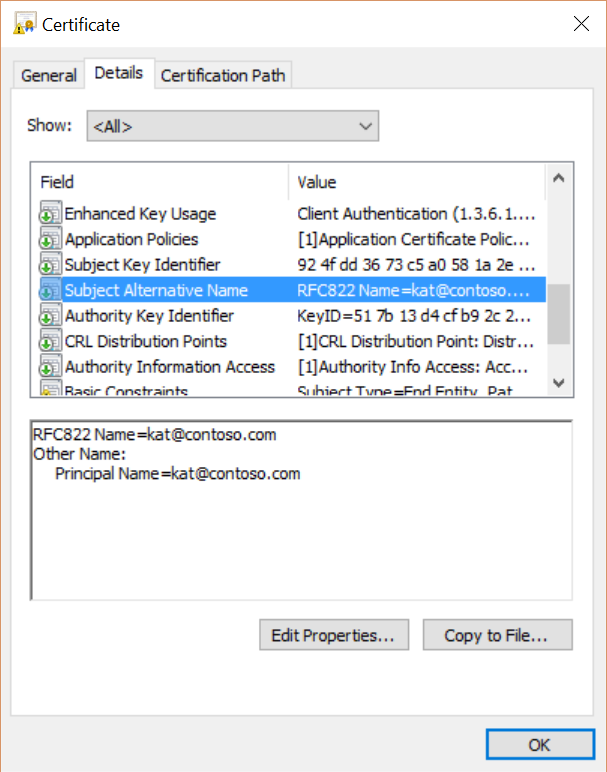 Figure 1: Client certificate with email address in RFC822 Name and Principal Name values in the SAN field
Figure 1: Client certificate with email address in RFC822 Name and Principal Name values in the SAN field
Using certificate-based authentication
Configuration in Azure Active Directory is required to use certificate-based authentication. All certificate authorities (and their associated CRL URLs) must be uploaded to Azure Active Directory. More information on getting started with CBA can be found in Get started with certificate-based authentication.Certificate-based authentication in Outlook for iOS/Android
Certificate-based authentication is supported with Outlook for iOS and Android for Office 365 accounts. For more information and requirements, please see:- iOS: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-certificate-based-authentication-ios
- Android: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-certificate-based-authentication-android
Certificate-based authentication in Exchange ActiveSync applications
Certain EAS applications may support certificate-based authentication. To determine if your application supports CBA, contact the application developer. Preview documentation on how EAS applications can support CBA can be found in Microsoft Exchange protocol documentation. Tyler Lenig Program Manager Office 365Updated Jul 01, 2019
Version 2.0The_Exchange_Team
Platinum Contributor
Joined April 19, 2019
Exchange Team Blog
You Had Me at EHLO.