- Home
- Security, Compliance, and Identity
- Core Infrastructure and Security Blog
- Intune iOS/iPadOS Management In a Nutshell
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hi, Jonas here!
Or as we say in the north of Germany: "Moin Moin!"
I’m a Microsoft Cloud Solution Architect and this blog post should give a brief overview of how to manage iOS and iPadOS devices with Microsoft Intune and how to get started.
If you are planning to migrate to Intune, I highly recommend the following link to a migration guide some colleagues wrote: https://aka.ms/intunemigrationguide
Feel free to check out my other articles at: https://aka.ms/JonasOhmsenBlogs
Device Enrollment
Enrollment is the process of registering a device with Intune and applying the necessary policies and settings to manage it. There are different methods of enrolling iOS and iPadOS devices, depending on the ownership and use case of the device.
- Automated Device Enrollment (ADE) via Apple Business Manager (ABM): This method allows you to enroll devices that are purchased through ABM, which is a web-based portal that lets you manage your Apple devices and content. You can link your ABM account to Intune, and automatically enroll devices when they are turned on for the first time. You can also assign devices to different Entra ID groups, and apply different policies and profiles to them. ADE gives you more control over the devices, and can prevent users from removing the management profile and ultimately the device from Intune management.
NOTE: This feature was formerly known as Device Enrollment Program (DEP)
NOTE: Existing devices can be added via Apple Configurator for iPhone app to ABM
- Apple Configurator: This method allows you to enroll devices that are not enrolled through ADE. You can use a Mac computer with the Apple Configurator app to prepare and enroll devices in bulk.
- User-initiated enrollment: This method allows users to enroll their devices by themselves, either through the Company Portal app or the Safari browser. You can configure the enrollment settings and requirements for user-initiated enrollment in the Intune portal. (The so called: Bring-Your-Own-Device (BYOD) process)
NOTE: Apple device enrollment requires the use of the Apple Push Notification service (APNs). To be able to communicate securely with APNs Intune requires an Apple MDM push certificate or APNs certificate.
Read more about the certificate HERE and HERE.
Each enrollment method and its features are described in more detail in the official Intune documentation HERE
Use the visual guide (PDF or Visio download) on the top of the page to get a better understanding of each method.
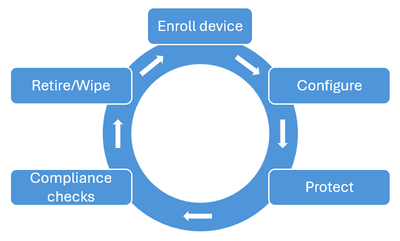
A typical Intune device lifecycle would include the following actions:
Enrollment Notifications for BYOD scenarios
Enrollment notifications are messages that are sent to the device user in the form of a push message to the Company Portal app or via email to the users mailbox.
They can be used in user initiated enrollments and can help to educate the users on the benefits of enrolling their devices, such as accessing the organization’s resources, protecting their data, and managing their devices remotely.
And if the user has not initiated the enrollment process themselves, thy can take action and inform the IT staff about it. (Not possible for automated enrollments at the time of writing)
Mobile Application Management (MAM)
While in the past the term “Intune MAM” was mostly used for securing apps on unenrolled devices (devices not managed by Intune or managed by a 3rd party MDM solution), now Intune mobile application management refers to the suite of Intune management features that lets you publish, push, configure, secure, monitor, and update mobile apps for your users.
Some of the features are:
- App assignment: This is the method of assigning the apps to users or devices, based on the app type and the deployment intent. You can use app assignment to specify whether the app is required, available, or to be uninstalled for users or devices. The Filter feature of Intune can help further filter the number of users or devices for assignments without the need to change Entra ID (formerly known as Azure AD) group memberships. (Entra ID groups are the basis for any assignment in Intune)
- App protection policies: These are policies that apply to the app data, regardless of the device enrollment status. You can use app protection policies to protect corporate data in apps, such as requiring a PIN to open an app, encrypting app related data, or preventing app data transfer to other apps and locations. (This feature works in conjunction with the “Dual Identity” feature of the Intune app sdk)
(App protection policies also work for unenrolled devices / MAM for unenrolled devices)
- App configuration policies: These are policies that apply to the app settings, such as the server URL, the username, or the app mode. You can use app configuration policies to pre-configure apps for users and reduce the need for manual input.
Such polices can also be targeted to apps running on devices without being enrolled in Intune. There are two types of app configuration policies, policies for managed devices (fully enrolled in Intune) and policies just for managed apps (running on devices enrolled or not / MAM for unenrolled devices)
- App inventory: Refers to the list of apps that are installed, along with the app details and status. Inventory data depends on the ownership state. For a personal device only managed app data can be retrieved, while a corporate owned device can inventory all data.
A typical Intune app lifecycle would include the following actions:
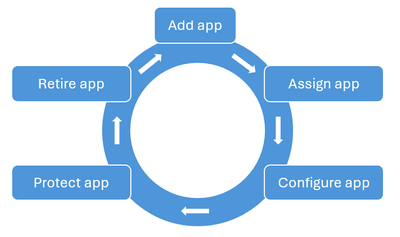
Device configuration policies
As mentioned in the MAM section, device configuration policies are policies that define the settings and features that you want to enable or disable on the enrolled devices, such as Wi-Fi, VPN, email or browser settings for example. You can use device configuration policies to customize the user experience and the functionality of the devices, and to apply the best practices for device management. You can create and assign device configuration policies in Intune Admin Center and monitor their status and impact.
NOTE: The possible configuration settings depend on the device enrollment type, either automated enrollment or user-initiated enrollment.
Compliance Policies
Compliance policies are policies that define the minimum security requirements for enrolled devices, such as the password complexity, device encryption state, or minimum OS version. You can use compliance policies to ensure that the devices meet the security standards of your organization, and to take actions on non-compliant devices, such as notifying end users, blocking access to corporate resources, or wiping the device. You can configure compliance policies in the Intune portal and assign them to the users or the devices.
Other than device configuration policies compliance policies typically just “report” a state rather than changing (configure) a state. (See note down below this section for exceptions).
There are two types of compliance settings in Intune:
- Compliance policy settings: Intune tenant wide compliance settings that every device receives. Basically the default compliance baseline.
- Device compliance policies: A set of security settings which can be assigned to individual device groups.
A device compliance policy not only contains checks for a compliant state, but also actions for noncompliance like the following:- Mark device noncompliant
- Send email or push notification to end user with instructions to remediate a noncompliant state (Notification language is defined by language settings of https://myaccount.microsoft.com per user)
- Remotely lock the noncompliant device
- Add device to retire list. An Intune admin can then take action on those devices.
NOTE: If a device compliance policy requires a password to unlock mobile devices, a password is automatically enforced regardless of the specific password settings of the policy.
Meaning, there will not only be a check if a password is used to unlock the device, but it will also be enforced.
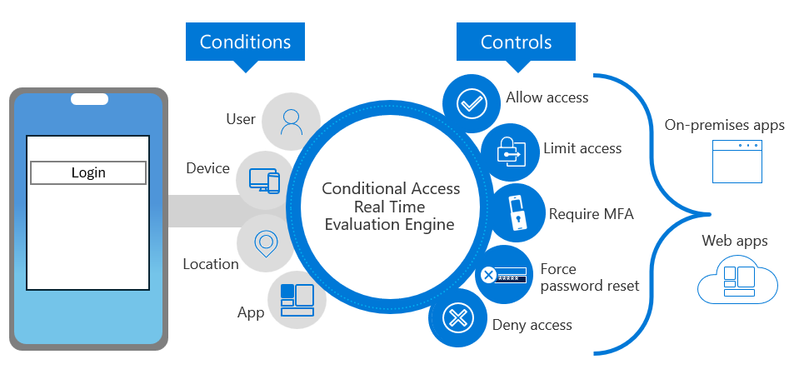
Conditional Access Policies
Conditional access policies let you define the conditions under which users can access specific applications (like Sharepoint, OneDrive or Teams), such as requiring multi-factor authentication, device compliance, or location-based rules. You can also use conditional access to block access for certain users, devices, or locations that do not meet your security standards.
Conditional access policies are applied after a user signs in to an application, but before they are granted access. The policies are enforced by Entra ID (formerly known as Azure AD), which evaluates the user's identity, device, and network information against the conditions and requirements of the policy.
The user is either allowed to access an application, blocked or prompted to perform additional actions, such as verifying their identity with a second factor.
While Conditional Access (CA) is an Entra ID feature it is integrated into Intune and shown in the Intune Admin Center. (Additional permissions are required to configure CA)
A conditional access policy can grant access based on the following Intune related conditions:
(There are more conditions available, these are just the ones coming from Intune)
- Require devices to be marked as compliant.
- The state is based on Intune Device Compliance Policy
- Require approved client app
- List of defined apps installed on a device, e.g. for unenrolled devices
- Require app protection policy
- App protection policy must be assigned from Intune, e.g. for unenrolled devices
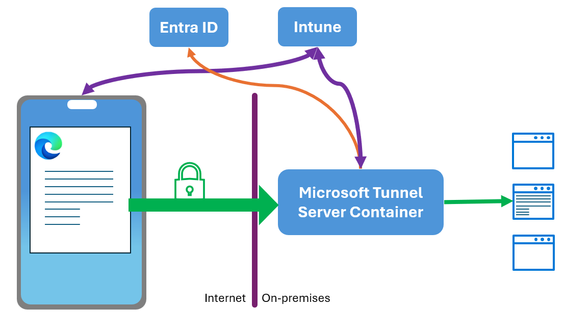
Microsoft Tunnel
Microsoft Tunnel is a VPN gateway solution for Microsoft Intune that runs in a container on Linux and allows access to on-premises resources from iOS/iPadOS and Android Enterprise devices using modern authentication and Conditional Access.
Microsoft Tunnel can also be used for applications running on devices not enrolled in Intune. (MAM without device enrollment) This feature can be added to Microsoft Tunnel after deployment and is called: “Microsoft Tunnel for Mobile Application Management”.
Via Intune app configuration policies Microsoft Tunnel can be configured to only apply for some apps for some resources (app based VPN). Meaning, a defined list of apps can use Microsoft Tunnel for specific resources located in your on-premises network.
Read more about Microsoft Tunnel HERE
While Microsoft Tunnel can tunnel any traffic, Microsoft Entra application proxy might be enough for http/https-based traffic.
Microsoft Entra application proxy consists of a proxy connector installed on-premises with access to an on-premises web application and the application proxy service running in Azure.
Users can access your on-premises applications the same way they access Microsoft 365 and other SaaS apps integrated with Microsoft Entra ID.
Read more about Microsoft Entra application proxy HERE
Microsoft Defender for Endpoint on iOS
Microsoft Defender for Endpoint on iOS is a product of its own. It is an excellent addition to the other mentioned Intune related security features like app protection policies, device compliance polices, conditional access or Microsoft Tunnel.
Read more about the feature HERE
How to start with Intune iOS/iPadOS management
This document should give you some key information as a starting point, but the easiest way to start with Intune iOS/iPadOS management is to follow the iOS/iPadOS deployment guide HERE
If you are planning to migrate to Intune, I highly recommend the following link to a migration guide some colleagues wrote: https://aka.ms/intunemigrationguide
Additional notes
This section contains some notes that might help with the initial setup of Intune iOS/iPadOS management.
APNs certificate
Familiarize yourself with the APNs certificate management tasks and recommendations from the Intune support team described HERE.
Apple Business Manager (ABM)
Different ABM accounts used for app synchronization can result in multiple application entries for one app.
It might be helpful to either use one ABM account to synchronize all required applications, or assign a scope tag to the location token in Intune.
Scope tags are used for role based access, but in the example above, they can help to later identify which app was synchronized with what ABM location token.
App protection policies for different device types
If one user needs to have different app protection policies for different device types (enrolled or unenrolled), apps on enrolled devices need to have an app configuration policy with the IntuneMAMUPN value set.
Read more about it HERE
I hope you enjoyed reading this blog post. Stay safe!
Jonas Ohmsen
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.