- Home
- Security, Compliance, and Identity
- Core Infrastructure and Security Blog
- ConfigMgr CMG Least Privilege Setup Approach
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hi, Jonas here!
Or as we say in the north of Germany: "Moin Moin!"
I’m a Microsoft Cloud Solution Architect and this blog post is meant as a guide to setup a ConfigMgr Cloud Management Gateway (CMG) without the need for a Global Admin to use the ConfigMgr console.
I will also briefly explain what a CMG is and how the setup looks like in Azure. This part is a mix of the official documentation and of my own view on the product.
If you are just looking for the setup guide, you can directly jump to section Least privilege approach
Feel free to check out my other articles at: https://aka.ms/JonasOhmsenBlogs
Cloud Management Gateway (CMG) overview
The Cloud Management Gateway (CMG) provides a simple way to manage Configuration Manager clients over the internet. You deploy CMG as a cloud service in Microsoft Azure. Then without more on-premises infrastructure, you can manage clients that roam on the internet or are in branch offices across the WAN. You also don't need to expose your on-premises infrastructure to the internet.
Data flow overview
The following diagram is a simplified view of the CMG data flow.
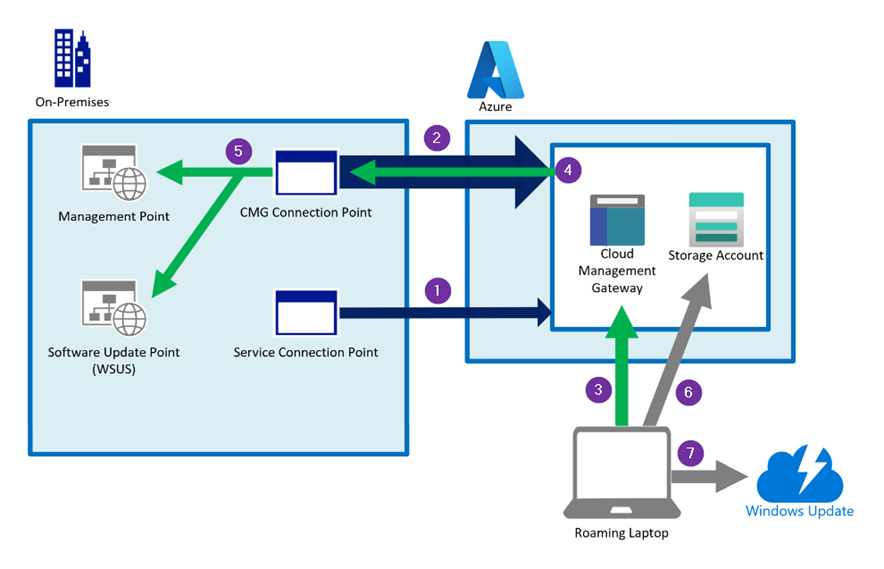
( 1 ) The ConfigMgr service connection point connects to Azure over HTTPS port 443.
It authenticates using Microsoft Entra ID. The service connection point deploys the CMG in Azure and carries out maintenance and updates the service if required.
( 2 ) The ConfigMgr CMG connection point connects to the CMG in Azure over HTTPS. It holds the connection open and builds the channel for future two-way communication. ( 2 / 4 )
If the CMG consists of more than one virtual machine the first VM will be contacted via port 443 TCP and all other VMs will be contacted via port 10124-10139 TCP
( 3 ) A ConfigMgr client connects to the CMG over port 443. It can authenticate using Microsoft Entra ID, a PKI client authentication certificate or via ConfigMgr site-issued token.
( 4 ) The CMG forwards the client communication over the existing connection to the on-premises CMG connection point. You don't need to open any inbound firewall ports.
( 5 ) The CMG connection point forwards the client communication to the on-premises Management Point and Software Update Point.
( 6 ) If the ConfigMgr client needs to download content in order to install an application for example, the clients will receive a necessary access token first and then downloads the content from a storage account.
( 7 ) A client can also be redirected to Microsoft Update to download updates directly from the Update CDN.
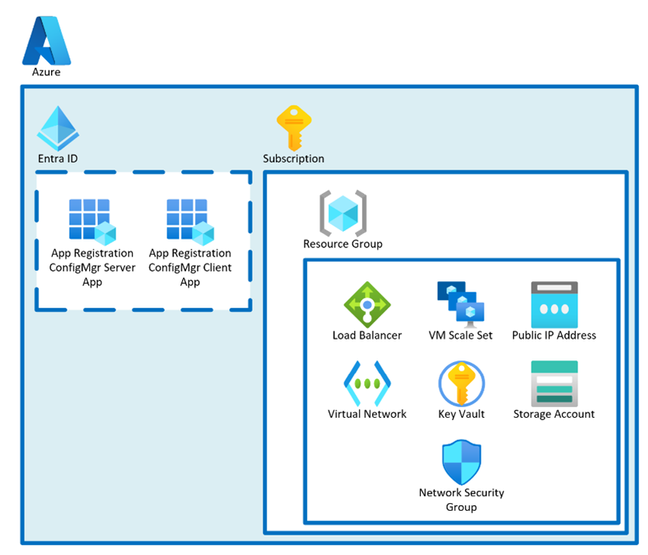
Azure resources
The main CMG components are a VM Scale Set with Load Balancer, Public IP, Virtual Network, and Network Security Group as shown in the diagram below.
The network security group has two ports open to support the load balancer. Port 443 for single instance use and port 8443 for multi-instance use. (The ports 10124-10139 described in Data flow overview are mapped to 8443 of each instance)
NOTE: The VMs use a web server certificate defined/requested by the ConfigMgr administrator (Either PKI or public certificate)
A Key Vault is used to safely store certificates and secrets used by the CMG to function correctly.
A Storage Account is used as a temporary storage for some CMG functions, but mainly as ConfigMgr content storage.
Each content will be encrypted by the on-premises ConfigMgr infrastructure and afterwards send to the Storage Account. Clients can then request an access token to download the content from the Storage Account directly. (Read more about it here)
(The content will be decrypted locally with a decryption token)
All resources together result in the CMG functionality, and they function as a PaaS solution managed by Microsoft. Read more about it here
App Registration ConfigMgr Server App
The server app in the above diagram is used to facilitate authentication and authorization from managed clients, users, and the CMG connection point to the Azure-based CMG components. This communication includes traffic to on-premises management points and software update points (client to CMG connections), initial CMG provisioning in Azure (CMG setup), and Microsoft Entra ID discovery.
App permissions
The server app has a client secret configured and ConfigMgr stores the client secret in the ConfigMgr database to use that for authentication.
- The server app will have the Contributor role assigned for the chosen Azure Resource Group. The role grants ConfigMgr the necessary permissions to maintain the CMG Azure service. (For example all the items shown in the diagram above within the resource group)
- The server app has the Entra ID Graph API permission Directory.Read.All set.
To allow ConfigMgr to read User, Group or Device resources, depending on the Entra ID discovery settings in ConfigMgr.
In addition a scope is defined to allow access on behalf of the signed-in user or device using the Client App.
The scope is therefore used to access the server app from the client app to get a token. That token is then used to authenticate a client or user via the CMG.
App Registration ConfigMgr Client App
The client app represents managed clients and users that connect to the CMG.
App permissions
ConfigMgr clients use the client app to request an Entra ID token via delegated permissions on the server app IF ConfigMgr Client detects a client in Entra ID join state.
- The app is configured with delegated User.Read permission and permissions to impersonate the user against the server app.
In summary, the server app is used by the ConfigMgr infrastructure for Entra ID discovery and CMG maintenance and for client authentication requests coming from the client app.
While the client app is only used by ConfigMgr clients.
NOTE: It is also possible to onboard additional Entra ID tenants and therefore allow ConfigMgr to authenticate clients of those other tenants as well to access a CMG.
(Each added tenant will use a client and server app for authentication)
While there are other methods for client authentication like with a certificate or ConfigMgr token, this blog is focused on Entra ID authentication.
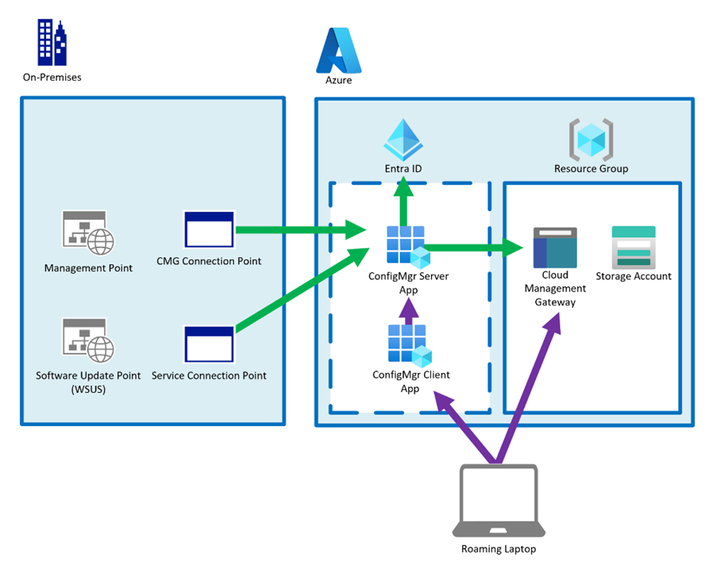
Simplified auth flow diagram
The following diagram shows a very simplified view of the authentication flow with the app registrations.
The ConfigMgr infrastructure will use the Server app for Entra ID discovery and CMG setup and maintenance (green arrows)
The client app is used to authenticate clients so that they can connect to the CMG (purple arrows)
Installation permission requirements
The CMG installation has different requirements like a web server certificate for the CMG webservice in Azure or the specific ULRs for outbound traffic from ConfigMgr to Azure.
This section covers just the required permissions.
The CMG setup works in two steps:
Step 1: A new Azure service needs to be created in ConfigMgr.
The setup wizard asks for Global Administrator credentials to register the Server and Client App in Entra ID for the new Azure service in ConfigMgr.
- Those apps can also be created manually and later imported into ConfigMgr without the need for a Global Admin to login during the setup phase. See Least privilege approach
- This step is done once per Tenant/EntraID
- Existing app registrations are visible in ConfigMgr as a “Tenants” and each tenant has its own app registrations.
Step 2: The second step is to create the Azure resources shown under Azure resources
The CMG wizard then asks for Subscription Owner credentials to be able to create the required resources and to be able to set Contributor permissions for the Server app as described under App Registration ConfigMgr Server App
The subscription owner permission is only required once for the initial setup. After that, ConfigMgr will use the Server app for CMG maintenance tasks.
Least privilege approach
Using the ConfigMgr wizard requires Global Administrator privileges to create the app registrations and set up a Resource Group in Azure for the CMG deployment.
A Global Administrator can also prepare the app registrations and necessary permissions before the CMG setup to avoid the need for any Global Admin login during CMG setup.
The following section describes that process.
- Use a global administrator for the following actions or any other user with sufficient permissions.
- Select or create a subscription for CMG deployment
- Make sure that all required resources as well as VM sizes are available in the subscription and not blocked by any Azure policy for example
- Register the following resource providers
- Microsoft.KeyVault
- Microsoft.Storage
- Microsoft.Network
- Microsoft.Compute
- Select or create a new Resource Group in the selected subscription for CMG deployment
- Keep in mind that the server app will have contributor permissions on the Resource Group
- Create Entra ID ConfigMgr app registrations and make note of the required IDs as described here
- Go back to the selected Resource Group and assign the Contributor role for the ConfigMgr server app you created earlier:
- Go to: “Access control (IAM)”
- Click on “+ Add” and “add role assignment”
- Select “Privileged administrator roles” and select “Contributor”
- Click “Next” and “+ select members”
- Type the name of the ConfigMgr server app you just created, select the app in the list and click “Select”
- Click “Review + assign”
- Share all gathered data with the ConfigMgr Full-Admin
- Tenant name
- Tenant ID
- Subscription ID
- App names and IDs of both registered apps
- App ID URI or server app
- The server app secret and expiration date
- The resource group name and Azure region
A ConfigMgr Full-Administrator can now import the app registrations into ConfigMgr and start the CMG setup process.
It is important to use the PowerShell cmdlet shown below and not the wizard to avoid the need for global admin permissions at this point in the setup process.
- Start the ConfigMgr console as a ConfigMgr full administrator
- Import the app registrations into ConfigMgr as described here
- Request a service certificate for the CMG as described here
- Add all the gathered data to the following script
- Adjust or add any of the parameters as needed
- Run it in ConfigMgr context and monitor CloudMgr.log for installation details:
# Password for the CMG service certificate
$ServiceCertPassword = ConvertTo-SecureString -AsPlainText 'PASSWORD-STRING' -Force
$paramSplatting = @{
GroupName = 'NAME' # Azure resource group name
ServerAppClientId = 'ID' # ID of ConfigMgr server app
ServiceCertPath = "C:\Temp\cmg.pfx" # Path to CMG service certificate
ServiceCertPassword = $ServiceCertPassword
SubscriptionId = 'ID' # SubscriptionId
TenantId = 'ID' # TenantId
VMSSVMSize = 'StandardB2S' # Choose VM Size
VMInstanceCount = 1 # Count of VM instances
EnableCloudDPFunction = $True
CheckClientCertRevocation = $false
EnforceProtocol = $True
Region = 'WestEurope' # Set region. SEE NOTE BELOW
}
# Actual install command
New-CMCloudManagementGateway @paramSplatting
# Read more about the Cmdlet here:
# https://learn.microsoft.com/en-us/powershell/module/configurationmanager/new-cmcloudmanagementgateway?view=sccm-ps
<#
NOTE: New-CMCloudManagementGateway in version 2309 only accepts EastUS, SouthCentralUS, WestEurope, SoutheastAsia, WestUS2 and WestCentralUS as values for the region parameter at the moment, even though more regions can be chosen.
#>
This two-step process does not require any extra permissions for the ConfigMgr administrator in Azure.
However, the ConfigMgr administrator should have at least read permissions on the resource group hosting the CMG to be able to check the service if required.
NOTE: When using the ConfigMgr CMG setup wizard you might see a permission request as shown below:

Those permissions are only required for the duration of the setup and can be deleted after CMG setup is done.
I hope you enjoyed reading this blog post. Stay safe!
Jonas Ohmsen
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.