- Home
- Security, Compliance, and Identity
- Azure Network Security Blog
- Defending Against UDP Flood Attacks with Azure DDoS Protection
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction
`
Distributed Denial of Service (DDoS) attacks have become a frequent threat, wreaking havoc on businesses and their online services. These relentless assaults overwhelm network resources, rendering websites and applications inaccessible to genuine users. One such attack vector, the UDP flood, predominantly leverages reflected amplification techniques to magnify its impact, causing not only service interruptions but also significant consumption of network resources. In this blog post, we delve into how Azure DDoS Protection serves as a formidable defense mechanism against such DDoS attacks.
Azure DDoS Protection is a cloud-based service provided by Microsoft Azure that provides automatic detection and mitigation of DDoS attacks for Azure resources. Key features and benefits of Azure DDoS Protection include:
- Adaptive tuning of the DDoS mitigation policy thresholds based on the traffic patterns and characteristics of each application.
- Automatic detection and mitigation of DDoS attacks without requiring any user intervention or configuration changes.
- Detailed monitoring and reporting of DDoS attack incidents and mitigation actions.
Understanding DDoS Attacks
Distributed Denial of Service (DDoS) is a type of malicious cyberattack that aims to disrupt the normal functioning of a server, application, network, or service by overwhelming it with a large amount of traffic. Most DDoS attacks send this large volume of traffic from multiple sources to amplify the attack, making the target overwhelmed and therefore slowing down, crashing or being unavailable to legitimate users.
There are three main categories of DDoS attacks:
- Volumetric Attacks – This category of DDoS attack includes DDoS attack types that overwhelm the target with a large amount of traffic which often looks legitimate. This large volume of traffic saturates the network bandwidth of the target, making it unavailable to genuine users. Volumetric attacks are easy to generate; attackers can employ simple amplification techniques to generate high quantities of traffic blocking access to the targeted end-system. Examples of volumetric DDoS attacks include IPsec Floods, DNS amplification attacks, ICMP Flood and UDP Flood.
- Protocol Attacks - These are also known as state-exhaustion attacks. Protocol attacks exploit vulnerabilities in the network layer or transport layer of the OSI model, with the aim of consuming the entire capacity of the service or a transitional system such as a load balancer. Common protocols exploited for flows at the network layer include IP, ICMP, IPSec, IGMP, while TCP and UDP are exploited at the transport layer. One common example of a DDoS protocol attack is the TCP Syn Flood attack. This attack exploits the TCP three-way handshake by sending numerous TCP Initial Connection Requests - SYN packets - to a target victim. The victim machine then responds to each connection request with SYN/ACK packets and keeps waiting for the final ACK packet to finalize the handshake. However, this response never comes. All these requests remain "open" waiting for a response and due to the number of requests, it causes the system to exhaust all its resources and become unresponsive. Other examples of protocol attacks include fragmented packet attacks, ping of death and Smurf attacks.
- Resource (Application) Attacks – These attacks target the application layer (layer seven of the OSI model). The objective of these attacks is to exhaust the resources of the target application by exploiting flaws or vulnerabilities on the application itself. Examples of this DDoS attack types in this category include Slowloris, BGP hijacking, and HTTP protocol violations.
UDP Flood Attacks
UDP flood attacks are a widespread type of volumetric DDoS attack, specifically leveraging the reflected amplification technique. In these attacks, an attacker sends a UDP packet to a vulnerable third-party server, which then sends an amplified response to the target. This reflected amplification significantly multiplies the volume of traffic directed at the victim. Such an approach not only floods the target's resources but also consumes a vast chunk of network resources, making it particularly effective.
Recent UDP Attack Trends
In the past few months (January to June 2023), Azure has witnessed and successfully mitigated a variety of UDP flood amplification attacks.
Below is a snapshot of the prevalent UDP amplification attack trends:
|
Attack Type |
Attack Subtype |
Count |
|
UDP amplification attack |
DNS amplification attack |
23445 |
|
UDP amplification attack |
NTP amplification attack |
22065 |
|
UDP amplification attack |
CLDAP amplification attack |
6991 |
|
UDP amplification attack |
SSDP amplification attack |
9314 |
|
UDP amplification attack |
Memcached amplification attack |
7210 |
|
UDP amplification attack |
CharGEN amplification attack |
5617 |
This data underscores the diverse range of amplification techniques employed by attackers. Such variability demands a robust and versatile defense mechanism, ensuring that systems are prepared to fend off any subtype of UDP flood attack. Azure's infrastructure is designed to detect and counteract such threats proactively, ensuring the full security of workloads.
UDP Flood Attack Process
Unlike TCP, UDP is a connectionless protocol, meaning it does not establish a connection before data transfer and does not ensure the data's integrity. This lack of connection and acknowledgment makes it easier for attackers to send high volumes of packets in a short span without any checks.
A typical UDP flood attack proceeds as follows:
- Initiation: The attacker typically deploys a botnet—a network of compromised devices. Using the botnet, the attacker sends a flurry of UDP packets to third-party servers. These packets appear to be originating from the intended victim's IP (IP Spoofing).
- Reflection and Amplification: These third-party servers, believing that the victim has requested data, send back amplified responses. Depending on the vulnerability exploited, this amplification can be many times the size of the original packets.
- Target Overwhelm: The target server or device, now inundated with this massive, amplified traffic, tries to process each packet, attempting to find the application listening on the specified port. Given the vast number of incoming UDP packets, this results in an overwhelming load on the target system.
- Depletion of Resources: As the system continues to process these rogue packets, its resources—like bandwidth and computational capabilities—are rapidly consumed. The system can become overwhelmed to the point where it can no longer manage legitimate traffic, leading to service interruptions or complete outages.
- Potential Collateral Damage: Often, attackers will spoof the source IP address in the initial UDP packets. The responses from third-party servers are directed towards the actual target, which they believe to be the original requester. This approach not only overwhelms the target but also obfuscates the true source of the attack, making it harder to trace.
How Azure DDoS Protection Stops UDP Flood Attacks
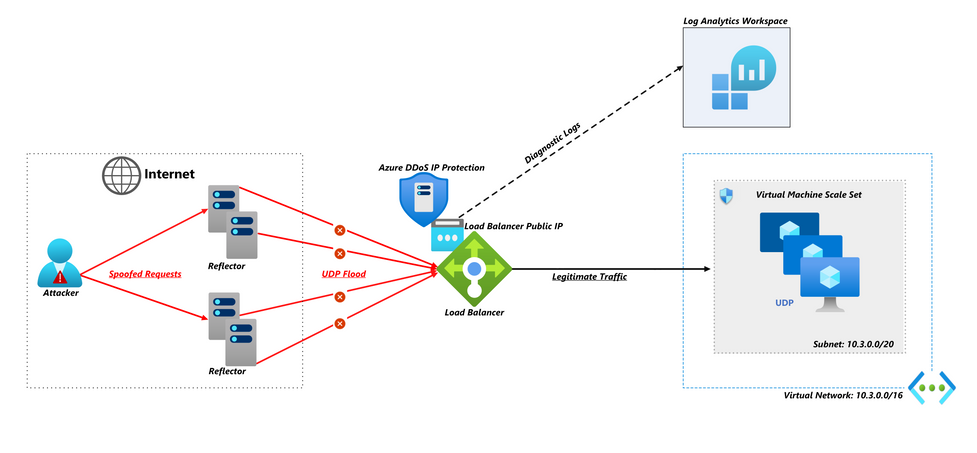
Azure DDoS Protection effectively mitigates against UDP Flood attacks. To demonstrate this capability, we have set up the following scenario in our Azure environment:
- Virtual Machine Scale set with Windows Server Virtual Machines. Each of these servers is configured to listen on UDP port 123. While we've chosen this well-known NTP port for our demonstration, it's crucial to note that attackers don't exclusively target well-known ports. They often employ scanning techniques to discover and target custom UDP ports, especially when these ports are used by unique applications.
- Azure Load Balancer distributes inbound flows arriving at its front end to the backend pool instances containing the Virtual Machine Scale Set. Diagnostic logging is enabled on the load balancer public IP address to send DDoS mitigation logs to a Log Analytics Workspace. You can refer to this article on how to configure the diagnostic logging - Configure Azure DDoS Protection diagnostic logging through portal | Microsoft Learn.
- Azure DDoS IP Protection enabled on the front-end public IP address of the load balancer. Azure DDoS IP Protection is one of the two Azure DDoS protection tiers. It provides the ability to provide DDoS protection on an individual IP address. It provides cost-effective and enterprise-grade protection against DDoS attacks for Azure resources that use public IP addresses. To learn more on the Azure DDoS protection tiers or SKUs please refer to – About Azure DDoS Protection tier Comparison | Microsoft Learn.
The above setup, with an external load balancer, is an example of one of the Azure DDoS Protection reference architectures. For more information you can refer to Azure DDoS Protection reference architectures | Microsoft Learn.
You can view the configuration steps for the VMSS and load balancer below:
Enabling Azure DDoS IP Protection
Both Azure DDoS Network Protection and Azure DDoS IP Protection provide the same level of protection against UDP Flood attacks and can be used to protect our load balancer public IP address.
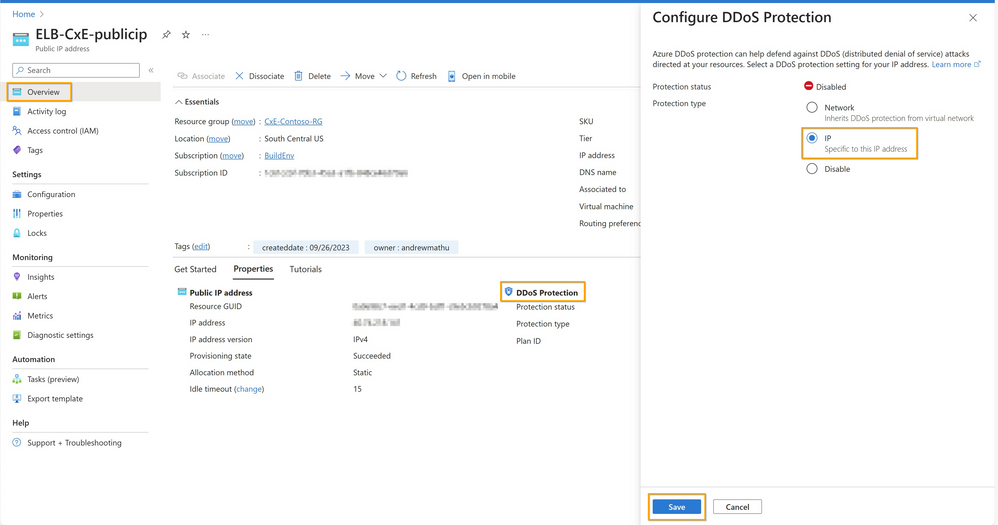
To configure Azure DDoS IP Protection, we follow the steps below:
- Navigate to the public IP address of the load balancer.
- In the Overview pane, select the Properties tab, then select DDoS Protection.
- In the Configure DDoS Protection pane, under Protection type, select IP (Specific to this IP address).
- Click on Save to finish the configuration.
Simulating the UDP Flood Attack
We simulate the UDP Flood attack by using Breaking Point Cloud. Breaking Point Cloud is one of the approved Azure DDoS Protection simulation partners. To learn more about the simulation partners you can refer to - Azure DDoS Protection simulation testing | Microsoft Learn. To learn more on using Breaking Point and the prerequisites required, please refer to this comprehensive blog on simulation testing - Strengthening Your Defenses: Simulation Testing for Azure DDoS Protection - Microsoft Community Hub.
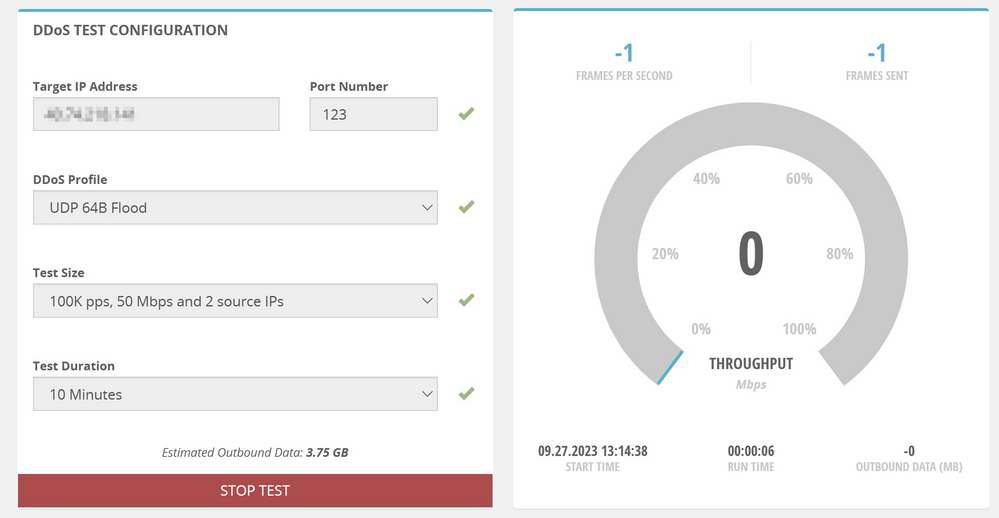
We login into our Breaking Point account and fill in the parameters below:
- Target IP address – Public IP Address of our load balancer
- Port Number – Port 123
- DDoS Profile – This is the type of DDoS attack we want to launch. We selected UDP64B Flood. This UDP flood attack will send a UDP packet that has a payload size of 64 bytes.
- Test Size – This specifies a profile that contains the data rate (bits or packets/second) and the number of IPs from which the test will be generated. We select 100K pps, 60Mbps, and 2 source IPs.
- Test Duration – We select 10 minutes.
We click on “Start test” to begin the attack:
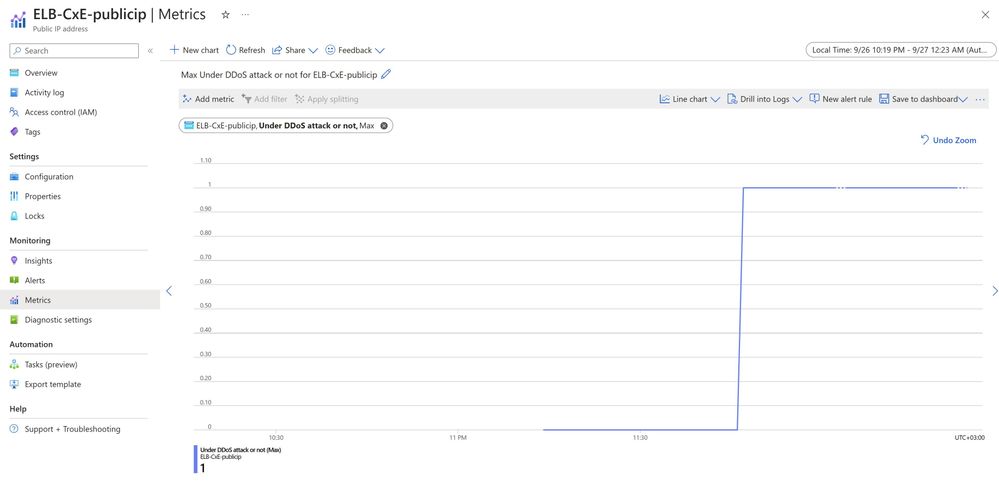
In the metrics section of the load balancer public IP address, we select the metric Under DDoS Attack or Not. We view that the DDoS attack is underway:
Analyzing the Azure DDoS Protection Logs
After carrying out the simulated UDP Flood attack, the next step is to view the Azure DDoS Protection logs in our Log Analytics workspace. In the logs section of the Log Analytics Workspace where we are sending our DDoS logs, we run the following queries to view the generated logs:
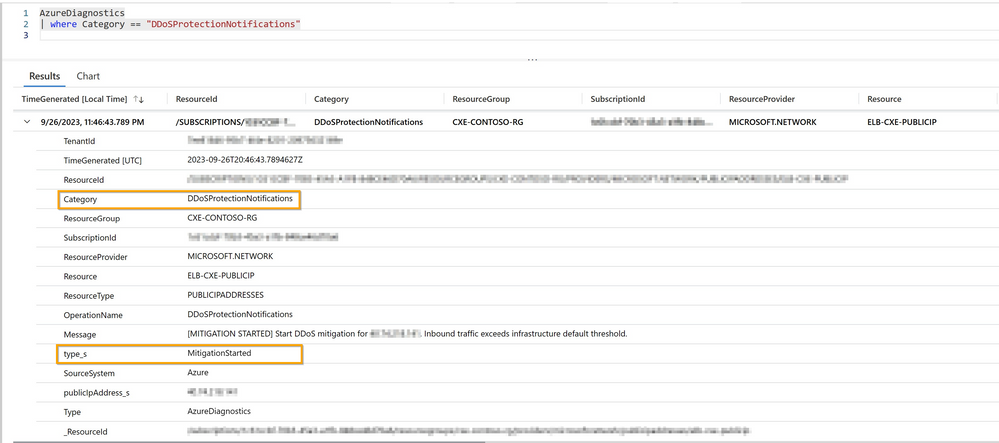
AzureDiagnostics
| where Category == "DDoSProtectionNotifications"
The above query allows us to view the DDoS Protection Notification Logs. The notifications logs inform us anytime a public IP resource is under attack, and when attack mitigation is over. In our query results, we see the sample below of the notification log details:
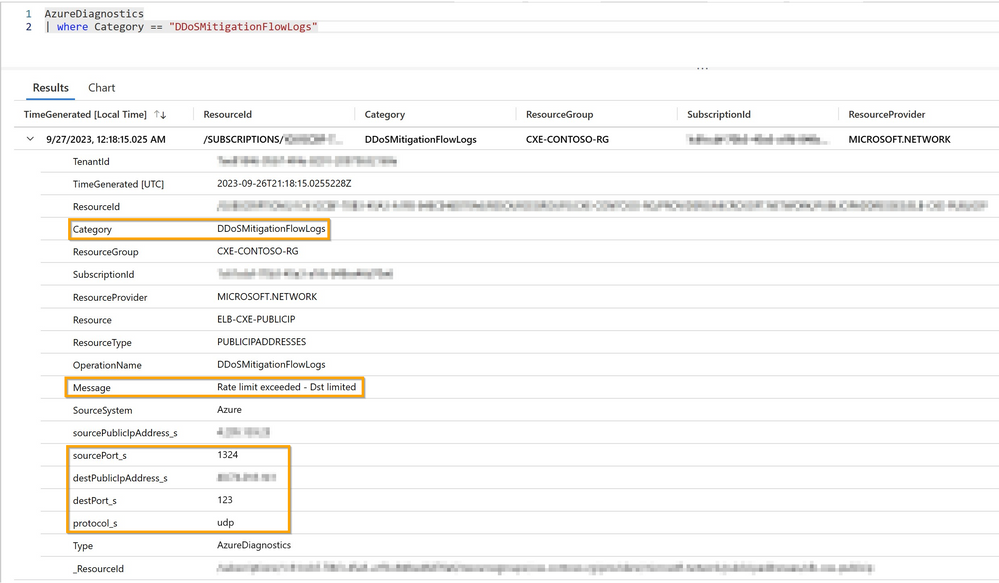
AzureDiagnostics
| where Category == "DDoSMitigationFlowLogs"
The above query displays DDoS Mitigation Flow Logs. These logs allow us to review in near-real time the dropped traffic, forwarded traffic and other attack insights during an active DDoS attack. In our query results we see below a sample of the mitigation flowlog details:
We view numerous UDP packets being dropped by Azure DDoS IP Protection due to exceeding the destination rate limit. We can also summarize the logs to view the specific number of packets dropped in our UDP flood attack by using the following query:
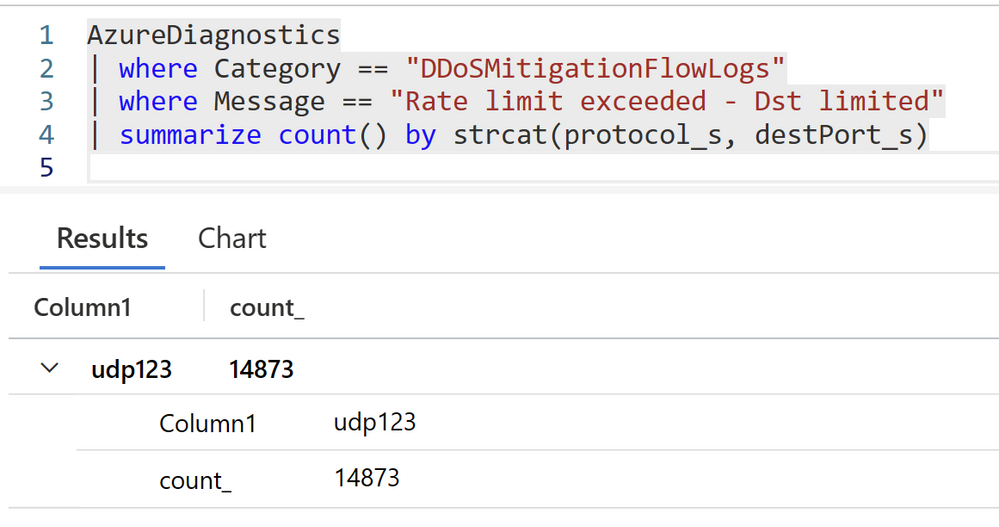
AzureDiagnostics
| where Category == "DDoSMitigationFlowLogs"
| where Message == "Rate limit exceeded - Dst limited"
| summarize count() by strcat(protocol_s, destPort_s)
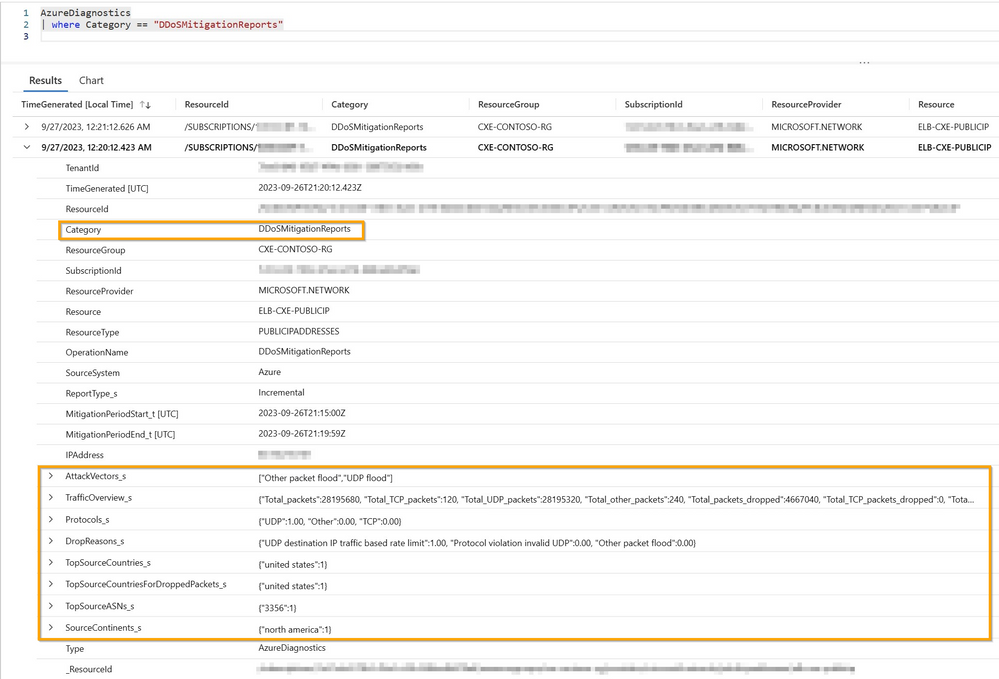
AzureDiagnostics
| where Category == "DDoSMitigationReports"
The above query displays DDoS Mitigation Reports Logs. These logs allow you to view aggregated detailed information on the DDoS attack. There will be an incremental report generated every five mins and a post-mitigation report for the whole mitigation period. The information viewed includes the attack type/vector, protocols, ports, top source attack countries and the Autonomous System Numbers (ASNs).
Conclusion
Protecting digital assets from DDoS attacks has never been more crucial, especially with the current prevalence of these attacks. UDP flood attacks are particularly formidable, taking advantage of the User Datagram Protocol, which is a foundation of many internet applications and services. These attacks aim to saturate server resources or network infrastructure by sending a deluge of packets, making legitimate traffic impossible to process.
Azure DDoS Protection provides a formidable defense against volumetric DDoS attacks such as UDP Flood. By proactively detecting, mitigating, and adapting to evolving threats, Azure DDoS Protection ensures that your critical online services remain accessible to legitimate users even in the face of relentless attacks.
Resources
- Types of attacks Azure DDoS Protection mitigates - Types of attacks Azure DDoS Protection mitigates | Microsoft Learn.
- Azure DDoS Protection Overview - Azure DDoS Protection Overview | Microsoft Learn.
- Create and configure Azure DDoS IP Protection using Azure portal - QuickStart: Create and configure Azure DDoS IP Protection - Azure portal | Microsoft Learn.
- Create and configure Azure DDoS Network Protection using the Azure portal - QuickStart: Create and configure Azure DDoS IP Protection - Azure portal | Microsoft Learn.
- Azure DDoS Protection Simulation testing - Azure DDoS Protection simulation testing | Microsoft Learn.
- Configure Azure DDoS Protection Diagnostic Logging - Configure Azure DDoS Protection diagnostic logging through portal | Microsoft Learn.
- View Azure DDoS Protection logs in Log Analytics workspace - View Azure DDoS Protection logs in Log Analytics workspace | Microsoft Learn.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.