- Home
- Security, Compliance, and Identity
- Azure Network Security Blog
- Azure DDoS Protection – SecOps Deep Dive
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
This blog is written in collaboration with @SaleemBseeu
Introduction:
Azure DDoS protection is a security solution offered by Microsoft Azure to protect applications and resources from Distributed Denial of Service (DDoS) attacks. DDoS attacks are a type of attacks that attempt to overwhelm a target application or service by flooding it with a massive volume of malicious traffic, thereby rendering it unavailable to legitimate users. Azure DDoS protection addresses these concerns by providing advanced mitigation capabilities and ensuring the availability of resources.
Some of the key features of Azure DDoS Protection include:
- Adaptive Tuning - Adaptive tuning will help with setting up protection policies tuned to your application’s traffic profiles. It automatically learns a baseline representing your application posture in peace time and sets mitigation threshold. The profile adjusts as traffic changes over time.
- Attack Analytics and Metrics - Attack analytics will help with detailed reports in five-minute increments during an attack, and a complete summary after the attack ends. We can stream these mitigation flow logs to Microsoft Sentinel or an offline security information and event management (SIEM) system for near real-time monitoring during an attack. On top of this, alerts can be configured at the start and stop of an attack, and over the attack's duration, using built-in attack metrics.
- DDoS Rapid Response - During an active attack, Azure DDoS Protection customers have access to the DDoS Rapid Response (DRR) team, who can help with attack investigation during an attack and post-attack analysis.
- Cost Guarantee - Receive data-transfer and application scale-out service credit for resource costs incurred as a result of documented DDoS attacks.
SecOps Deep Dive Investigation:
In this blog we will be focusing on how to investigate a DDoS Attack using the logs/metrics and newly built KQL queries.
Prerequisites:
To initiate an investigation into a DDOS attack, we must establish the following prerequisites. More information on configuration of the prerequisites can be found here.
- Create a DDoS Protection Plan.
- Associate the DDoS Protection Plan to an existing Virtual Network.
- Set Up Diagnostic Logging for the respective Public IP resource.
- Simulate a DDoS Attack using one of our Simulation Partners. For more information on attack simulation, refer to this documentation.
Once the Attack Simulation is completed, we can look in to following metrics available under a public IP resource to better understand the attack patterns.
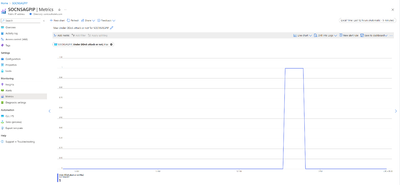
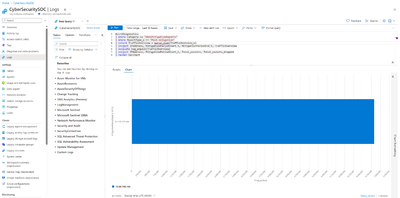
- Under DDoS Attack or Not: This Metric will give information on whether our Public IP resource is under a DDoS attack or not. This metric can also be used to set up an alert to notify about DDoS attacks via email and other available options. As we can see here, during the attack duration, the metric changed from 0 to 1 and rest of the times it remained 0.
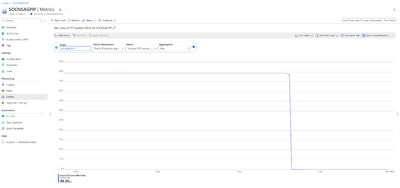
- Inbound SYN Packets to trigger DDoS Mitigation: This metric will provide information on the Threshold for Inbound Syn packets to trigger DDoS Mitigation. This threshold will be unique to each public IP resource depending on the average application traffic and adaptive tuning functionality of Azure DDoS Protection. In this case the threshold is 10k Syn Packets per second.
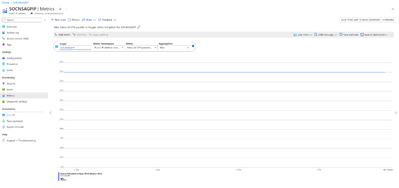
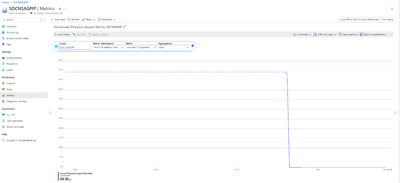
- Inbound TCP Packets DDoS: This metric will give us information on number of TCP packets came in during a DDoS Attack. In this case 49.30k Packets per second.
- Inbound TCP Packets Dropped DDoS: This metric will give us information on number of TCP packets dropped out of the total incoming TCP packets. In this case almost all the packets 49.30k packets per second were dropped.
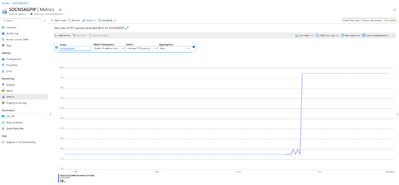
- Inbound TCP Packets Forwarded DDOS: This metric will give us information on number of TCP packets forwarded to the service or application. In this case only about 19 packets were forwarded and rest all the packets were dropped.
In this way we can utilize the Public IP resource metrics to get deeper insights into the DDoS attacks.
Queries for DDoS Mitigation Trends:
To understand the attack patterns easily, our team has developed 2 new KQL queries that will give detailed information on total packet trends and Attack Vectors as shown below. These Queries are available in our Net Sec GitHub Repository - GitHub
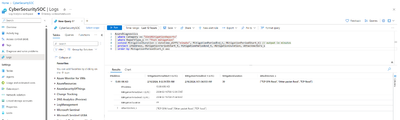
- To get the trend of the total and dropped packets for each public IP address:
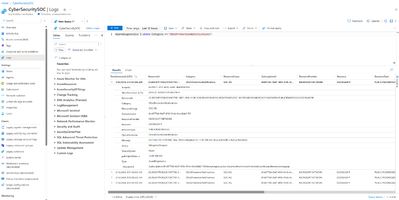
- To get the information on DDoS attack mitigation duration and attack vectors
As demonstrated earlier, the two queries yield essential insights into recent attacks occurring within a specified time frame. For a deeper analysis of these attacks, we can explore the following three log categories:
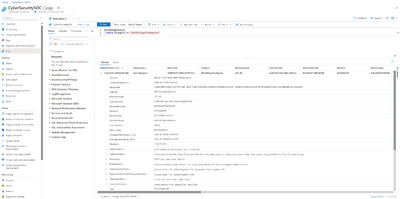
- AzureDiagnostics | where Category == “DDoSProtectionNotifications”: This log category furnishes details about the initiation and cessation of DDoS mitigation. These logs serve as a basis for configuring alerts to notify the Security Operations Center (SOC) Analyst as necessary.
- AzureDiagnostics | where Category == “DDoSMitigationReports”: Within this category, you’ll find comprehensive post-mitigation reports and incremental updates, generated every 5 minutes during an ongoing DDoS attack. These reports encompass critical information such as packet counts, attack types, protocols, and details about the attacker’s source. To get summarized information on this, we can also use the queries from GitHub.
- AzureDiagnostics | where Category == “DDoSMitigationFlowLogs”: This log category provides a granular view of each packet encountered during an attack. It includes crucial data such as packet forwarding or dropping status, along with specifics like source IP, destination IP, port, and protocol."
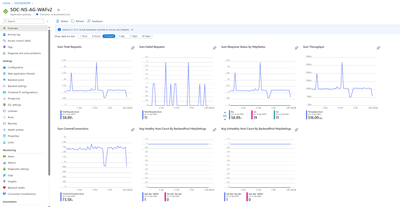
In this case, our application is situated behind an Azure Application Gateway WAF. Once we have conducted a comprehensive log analysis, we can proceed to evaluate the health of our application using the metrics furnished by the Application Gateway. These metrics offer detailed insights during the attack time, including but not limited to the metrics listed below:
- Failed Requests – Count of Failed Requests that the App Gateway has served.
- Throughput – Number of Bytes per second the App Gateway has served.
- Backend First Byte Response Time – Approximating Processing time of backend server.
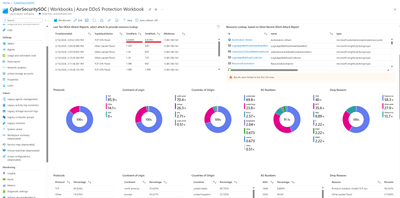
In addition to the details provided earlier, we have a predefined workbook that provides comprehensive insights into historical Distributed Denial of Service (DDoS) attacks targeting specific sets of public IP resources. This consolidated dashboard outlines critical attack information, including recent incidents, protocols involved, drop reasons, and the countries of origin etc.
Conclusion:
Azure DDoS protection provides a powerful shield for your infrastructure, helping you to defend against DDoS attacks. By investigating the telemetry, and using the provided metrics and logs, you can gain a deeper understanding of the nature of DDoS attacks and take appropriate action to protect your resources.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.