- Home
- Azure
- Azure Architecture Blog
- Secure Linux Access Using Azure Virtual Desktop
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
I've heard time and time again that Azure Virtual Desktop does not support Linux VMs in Azure. I think that's really semantics, based on the realities of and complexities of Linux (so many distros / kernel version / management tools / access methods). While Azure Virtual Desktop does not itself provision or manage Linux VMs, it does a wonderful job of supporting secure access to those Linux VMs through publishing access tools for Linux on Windows!
I know that many developers and testers love using the Windows Subsystem for Linux (WSL) on Windows VMs via AVD, but that can be complex to install, and usually means users leverage personal (expensive!) VMs to support one-to-one installs.
Azure Virtual Desktop lets you publish access tools via RemoteApp for users to connect to shared Linux VMs, saving money by centralizing compute, as well as wrapping the security benefits of Azure Active Directory / MFA / Conditional Access around your Linux VMs!
A deployment pattern growing in popularity is to publish access to Linux resources via AVD. The AAD requirement for AVD is a perfect security wrapper for many dev and test Linux deployments, since it creates a security wrapper for those environments which might otherwise be challenging to implement (example: where devs want to manage passwords on their own Linux machines!).
The common emerging patterns (outside of WSL) I have seen for secure Linux access using AVD include:
- Leveraging AVD RemoteApp using:
- Telnet (PuTTY, MobaXterm, other)
- Xrdp access either with MSTC or MobaXterm
- X11 access using X2go
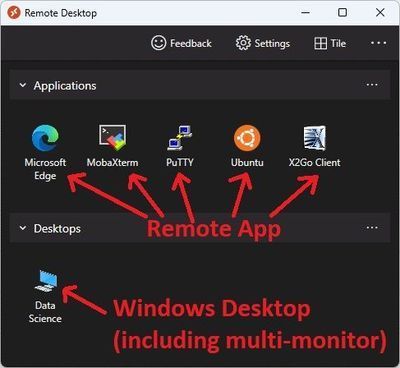
AVD lets you publish either individual applications (Remote Apps) or the full Windows desktop experience:
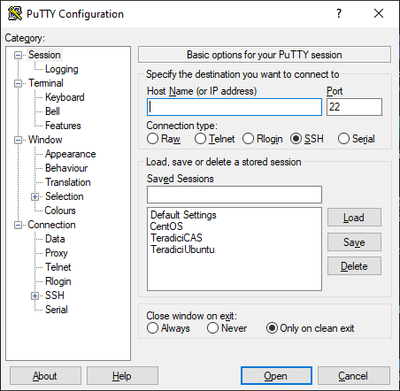
PuTTY – Easy (if you don’t need GUI!)
PuTTY is well known to your Linux users (I’ll bet, and super easy to install / publish via RemoteApp!).
Once it’s deployed, just share the IP address(es) of the hosts your users need access to, and they can setup the “saved sessions”:
Xrdp with MSTSC
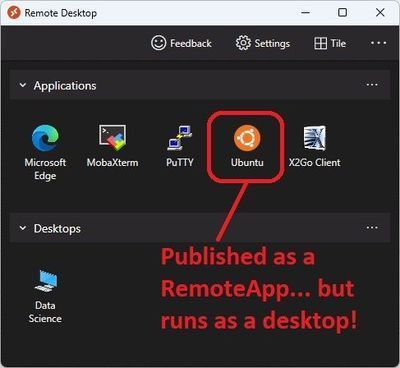
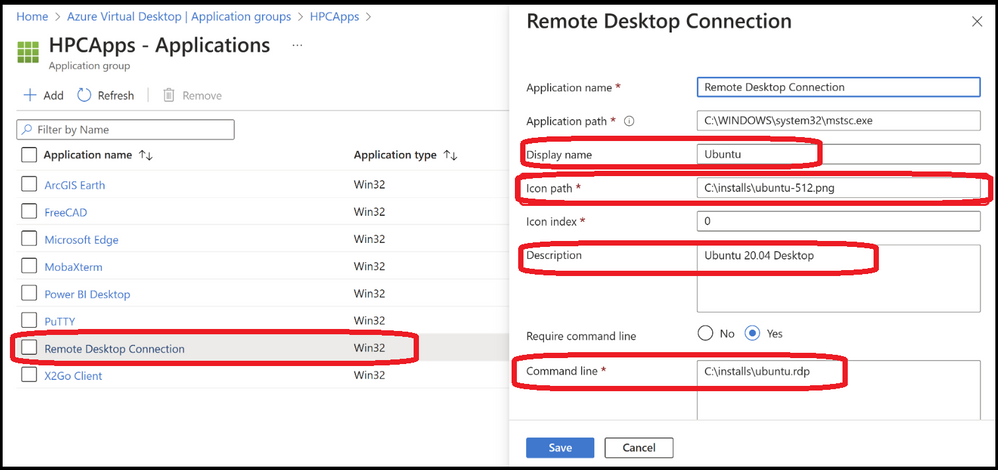
Let's look at that Ubuntu Icon in the Remote Desktop application.
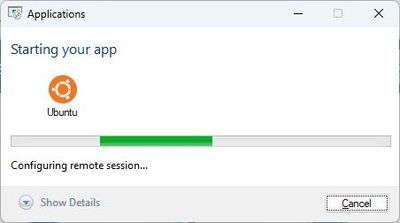
While it is implemented as a Remote Application (our old friend MSTSC) it publishes a full Ubuntu desktop:
When the user clicks on it, they get the familiar connection dialog:
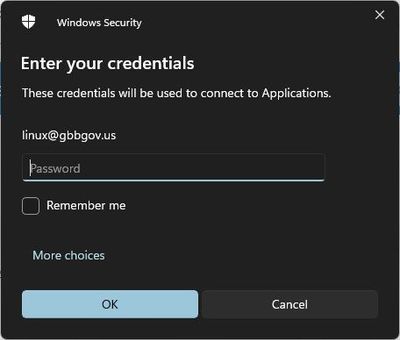
...and maybe that secondary authentication prompt for Windows
(again, this can be eliminated if you implement single sign on:)
BUT THEN they get to their Linux desktop:
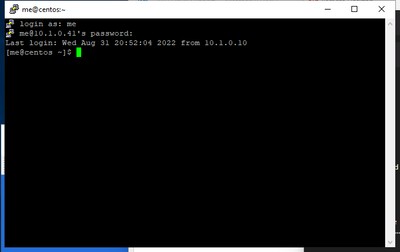
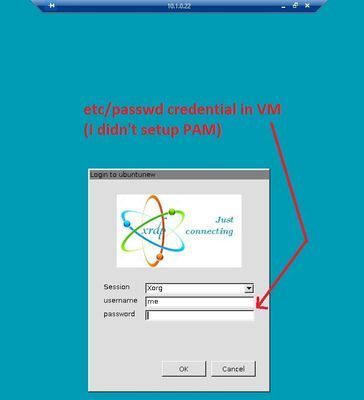
In this case, it's an xrdp login prompt for a local credential stored in etc/passwd (could also be PAM integrated).
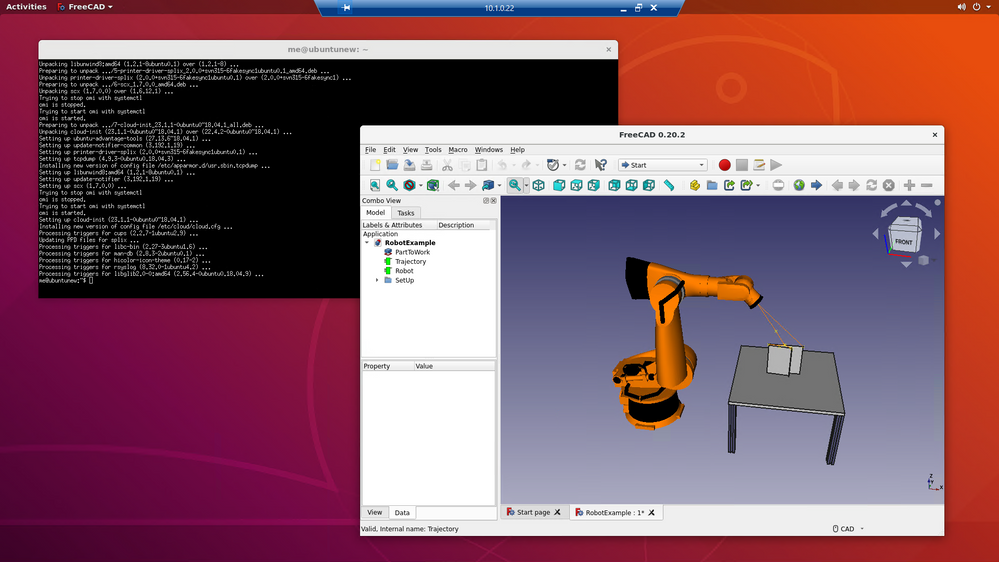
Once they log in - they have their desktop:
The secret sauce here is RemoteApp publishing! All I'm doing is using MSTSC (built in RDP client in Windows published from AVD as a RemoteApp, with a few updates to the defaults:
It’s pretty easy to setup in Azure – happy to walk you through it if you like.
THE FINE PRINT: You may have to grant users Local Admin rights on the VM where you publish MSTSC to the Linux box (one downside of using Xrdp...beyond having to load the protocol on your Linux hosts).
X-Windows Access (likely the preferred method if you want a GUI)
You can do something similar with MobaXTerm or X2Go (and not mess around with XRDP!).
This may actually be my PREFFERED method so that the xRDP package is not required in the Linux VMs.
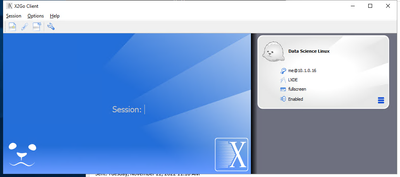
I do like X2Go published via RemoteApp – super simple user interface:
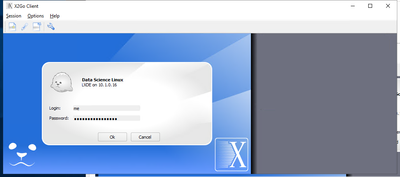
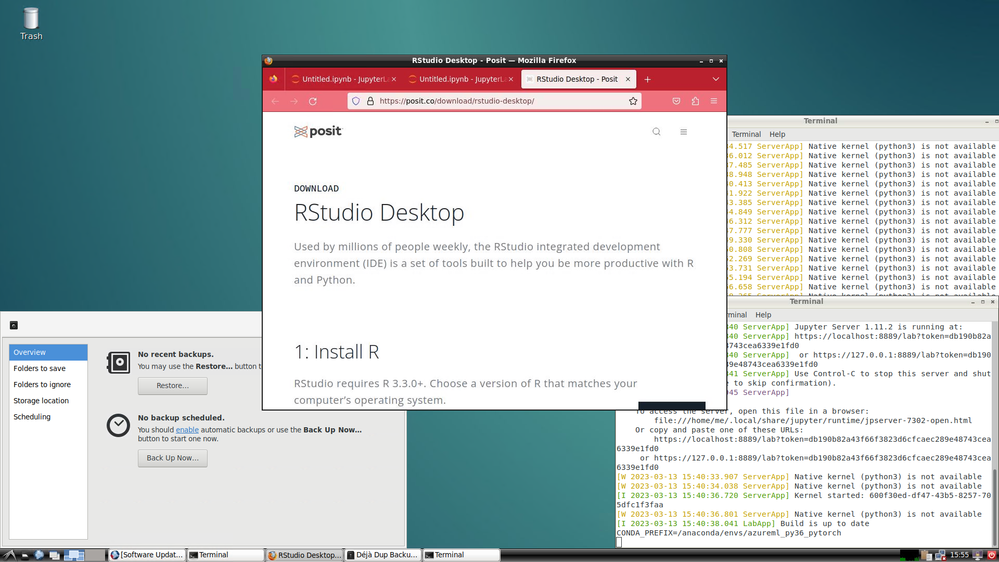
…and then I’m into my full Linux Desktop (in this case, a Linux Data Science VM in Azure):
Oh, and I'm in no way trying to slight MobaXterm here by not showing a picture of it... it's a great, multi-protocol access tool!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.