- Home
- Azure
- Azure Arc Blog
- New options for Extended Security Updates enabled by Azure Arc
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
With Azure Arc, we want to empower businesses to transcend cloud boundaries and innovate from the cloud to the edge. As part of our commitment to enable seamless management. security, and innovation across diverse environments, we want to share a new offering today to help secure your end-of-support OS starting with Windows Server 2012 and SQL Server 2012.
We’re approaching some critical end-of-support (EoS) milestones for Windows Server 2012/R2 (October 10, 2023) and SQL Server end-of-support (July 2012, 2023 – end of ye.... We recognize that in some instances, customers are unable to migrate their IT infrastructure to Azure by the deadlines and need their Windows Server 2012 or SQL Server 2012 resources to stay on-premises to support their business-critical applications. To secure their EoS resources in the cloud or on-premises, many customers enroll in Extended Security Updates to avoid data breaches, malware infections, and other security breaches, which could potentially result in significant financial loss, reputational damage, and legal ramifications.
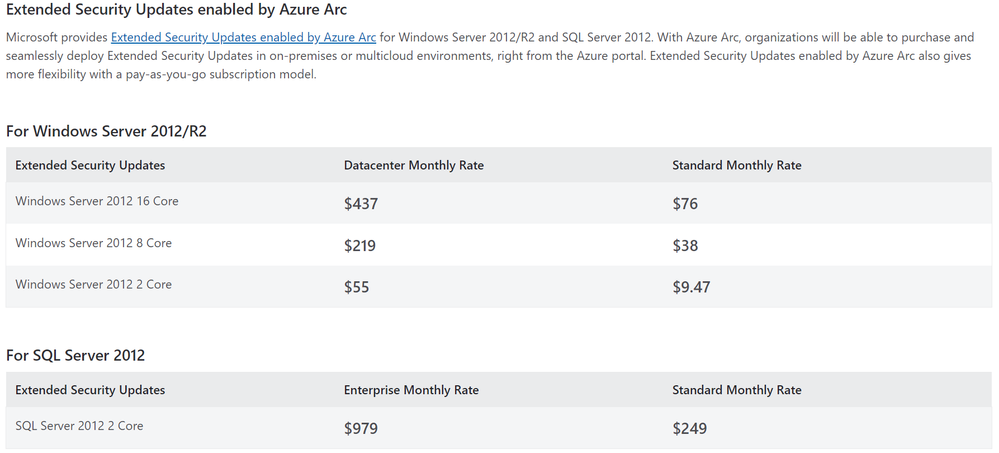
Today, we’re announcing Extended Security Updates enabled by Azure Arc for Windows Server 2012/R2 and SQL Server 2012 (year 2 onwards), a new and enhanced cloud experience alternative to traditional Extended Security Updates (classic). With this new option, security updates will be natively available in the Azure Portal through Azure Arc for resources for up to 3 years.
Extended Security enabled by Azure Arc is the best way for customers to get trusted security updates and benefit from cloud capabilities including discovery, management, and patching, all in one offering. Here are some key benefits:
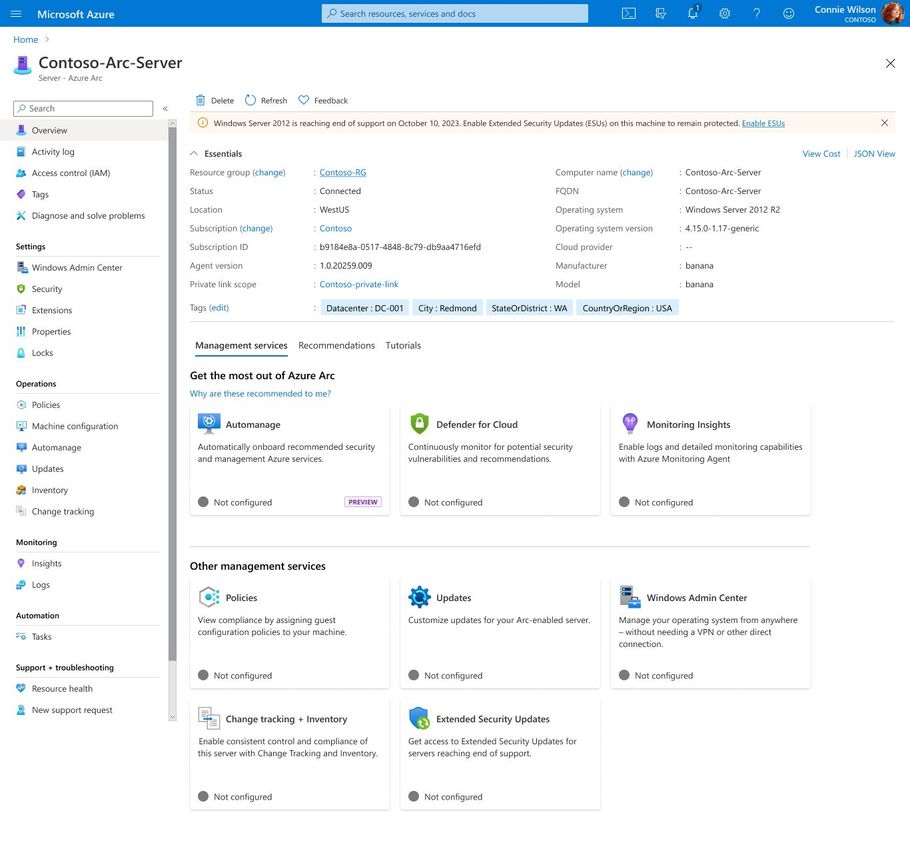
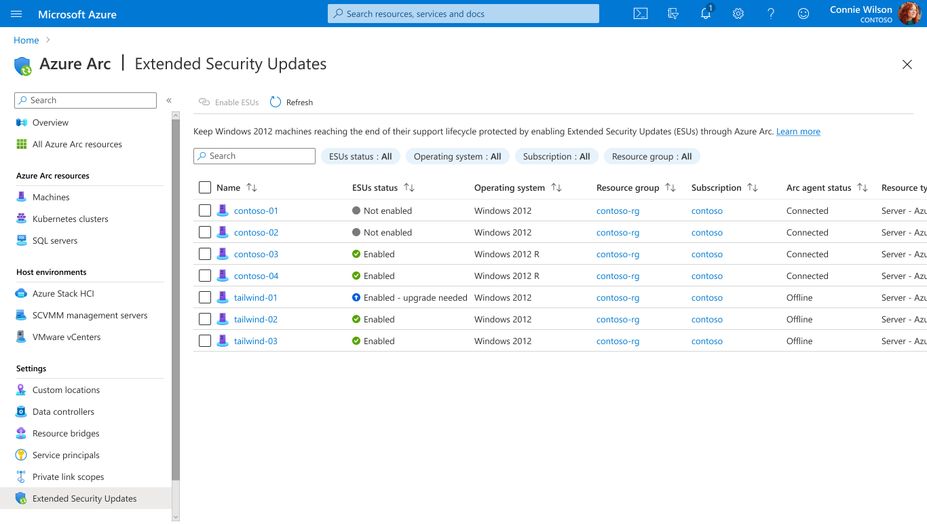
- Inventory and management: After deploying Azure Arc, customers can discover their Windows Server 2012 and SQL Server 2012 resources and manage the enrollment of Extended Security Updates in the Azure portal.
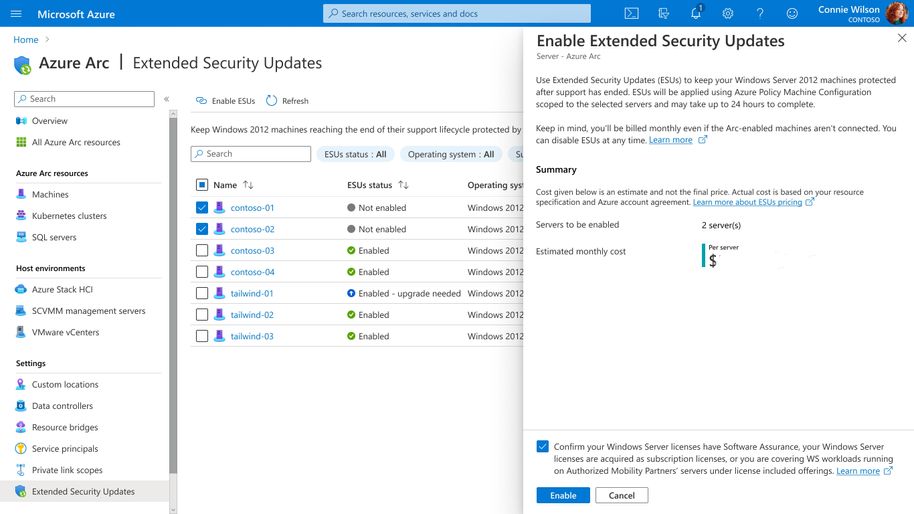
- Pay as you Go billing: Customers will be charged on a monthly basis to enable flexibility for managing their costs and timelines.
- Keyless delivery: Azure Arc-enabled machines do not require the acquisition or activation of keys for Extended Security Updates.
- Modernize: Add Azure services like Microsoft Defender, Microsoft Sentinel, SQL Managed Instance, Azure Monitor, and more in your preferred environment.
- Azure investments: Customers can leverage their Microsoft Azure Consumption Commitment (MACC) investments and manage their costs using Azure Cost Management.
How to deploy Extended Security Updates enabled by Azure Arc
Customers should start with enabling Azure Arc on their servers with their preferred option for deployment and networking.
- Establish Azure foundation. Create an Azure account, setting up billing alongside the subscriptions and resource groups to server as a landing zone for your Arc-enabled servers.
- Define networking approach. Select from public endpoint, proxy server, and private endpoint connectivity options to meet your organization’s networking requirements.
- Onboard to Azure Arc. Install the Azure Connected Machine agent to connect your servers to Azure with the flexibility of at-scale deployment options like Group Policy and Configuration Manager.
- Deploy Extended Security Updates: Once onboarded, the servers will be visible in the Azure portal with an option for activating Extended Security Updates for Windows Server 2012 Standard and R2 through the Azure portal or Azure Policy.
Get started today!
Extended Security Updates enabled by Azure Arc are available today for purchase for Windows 2012/2012 R2 and SQL Server 2012. To prepare for the deployment, customers should ensure that their Windows Server 2012, Windows Server 2012 R2, and SQL Server 2012 machines are onboarded to Azure Arc by September 2023.
Learn more:
- Extended Security Updates enabled by Azure Arc technical documentation: Extended Security Updates (ESUs) enabled by Azure Arc
- John Savill YouTube video on how to configure ESUs:
- FAQ: https://www.microsoft.com/en-us/windows-server/extended-security-updates
- General Availability announcement
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.