- Home
- Azure
- Azure Virtual Desktop
- Windows Hello support available with our Remote Desktop client for Windows!
Windows Hello support available with our Remote Desktop client for Windows!
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 29 2019 03:15 PM
Windows Hello authentication to the session host (including Smartcard and PIN) is now supported. This feature requires that the user’s device has line of sight to the Domain Controller that can validate the credentials, for example from the corporate network or connected over VPN. When connecting from an external network, users still need to use their username and password.
Update to the latest version of our app today!
Haven't used our client yet? Follow this link for more information:
https://docs.microsoft.com/en-us/azure/virtual-desktop/connect-windows-7-and-10
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 26 2019 07:24 AM
@Eva Seydl Hello, are there plans to get windows virtual desktop to work without a password? We're trying to test going passwordless in Azure (no password hash sync, using fido2 keys, adfs, ect). Right now windows virtual desktop seems to behave like a legacy domain device and we can't seem to both test the virtual desktop preview at the same time as going passwordless. I feel it'd be great if these windows 10 virtual desktops were to be connected directly to Azure AD for native Azure AD authentication over setting up Azure AD Domain Services for a legacy style domain environment.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 26 2019 09:31 AM
@Mike McConnell : We definitely want to support both Azure AD Join and Passwordless going forward to align on those initiatives. These may end up being separate features, or may end up being intrinsically tied. However, this is not something we are planning for GA, as there are a bunch of moving parts we are investigating to handle this.
However, feel free to upvote or make these suggestions on our UserVoice forum.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 18 2019 04:36 AM
@Eva Seydl
When will support for Windows Hello key trust model be available?
We are all moving towards a modern desktop approach with Azure AD and Intune.
So It’s a real showstopper, if we still need legacy ADFS to use PIN/Fingerprint for this new great WVD service.
/Jesper Ravn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 18 2019 09:15 AM
@Jesper Ravn : We do not have dates yet for RDP to support the Key Trust Model for Windows Hello. As mentioned, we're working on supporting Azure AD Join and some of that work likely will make its way into RDP. However, can you file an item on our UserVoice so we can specifically track this request?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 27 2020 11:15 PM
Hello, can I able to use latest WVD image for pass wordless login like using FIDO device, PIN and smart card ?. Or RDP for windows will support WVD 2004 build ? @Eva Seydl
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 16 2020 11:09 AM
@Deepu_k WVD does support PIN and smartcards today for the Windows client as long as the user's device has line of sight to the domain controller, so on the local network or using VPN. Need to check on FIDO support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 23 2020 01:09 PM
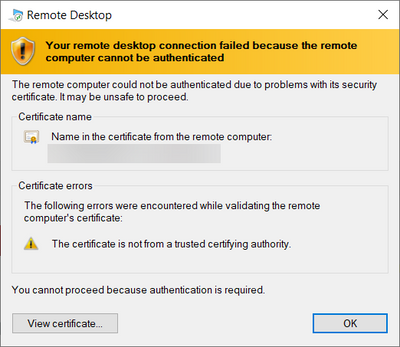
@Eva Seydl , I'm getting below error if we use PIN (Windows Hello enabled on workstation) & I assume, this is because I'm not on VPN to access domain controller from workstation to validate the credentials? Or Do I need to configure anything on WVD/Azure AD/Windows hello?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 23 2020 03:56 PM
@Udayabhanu2020 If you don't have line of sight to the domain controller it would be a different error that would indicate something along those lines. This error seems to indicate a problem with one of the certificate. You could see what that certificate is and replace it with one that is trusted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 23 2020 05:58 PM
Hi @David Belanger , certificate issuer is WVD session host. This works if I use domain credentials.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 19 2021 10:49 PM
Well, that's nice I guess, for those who have the extra bits in place.
I have a desktop at home, without line of sight to a DC, without a hardware token, and no biometrics. When I try to RDP via a work gateway, I get asked to use a PIN to log in. I don't have PINs on the remote machines, but do have MFA via mobile app once password is accepted.
It's fiddly and annoying to have to select "other account" since I happen to think stored credentials are not a good idea on a PC that's only protected with a PIN. Why would RD Client think I could or should use just a PIN for remote access? After all these years of trying to teach people to use long, high-entropy passwords.
Is there a way to tell my RD Client to never ask for a PIN, just go straight to password?