- Home
- Windows Server
- Windows Server for IT Pro
- Re: Using MMC Snap-Ins remotely
Using MMC Snap-Ins remotely
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 24 2018 12:52 PM
Hello there;
Just joined Microsoft Tech Community and I'm not really sure if it's the exact place to ask about this problem.
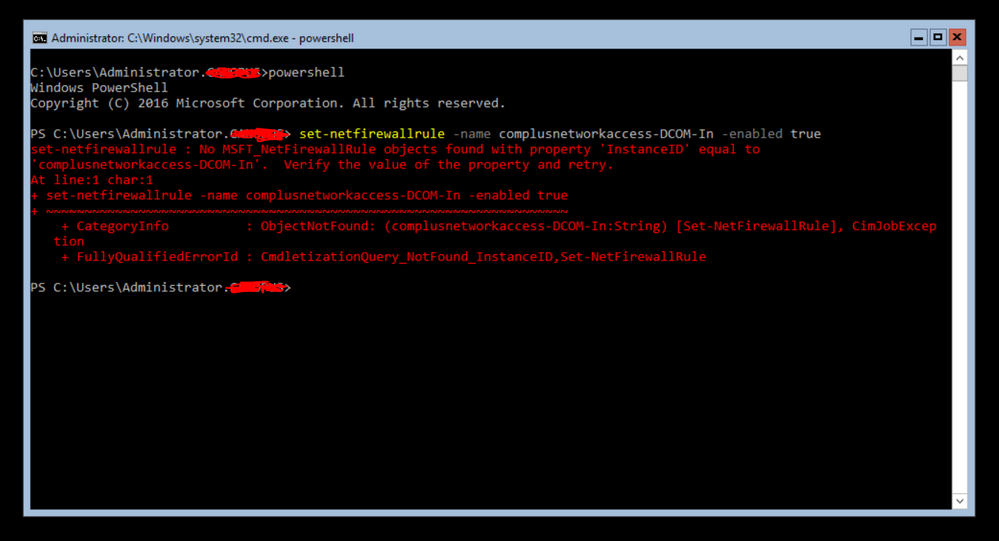
The problem is that I have set up a virtual environment(I'm using Hyper-V) with 2 virtual machines(Windows Server 2016 Data Center & Server Core 2016 Data Center)and I've been trying to manage the Server Core remotely. Despite the fact that both servers have been added to the Server pool, I get an error while trying to set the appropriate firewall settings for MMC Snap-Ins.
I'll be truly grateful if someone helps me figure out the solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 25 2018 11:42 AM
I don't believe that rule exists on 2016+ which would explain why you are seeing the error you shared. If I'm not mistaken, that rule opened up port 135 which is satisfied by other rules by default on Server.
The steps to enable remote management on Hyper-V on 2016 are here: https://docs.microsoft.com/en-us/windows-server/virtualization/hyper-v/manage/remotely-manage-hyper-...
I'd recommend reviewing that to confirm you have it configured properly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 26 2018 01:35 AM - edited Oct 26 2018 01:38 AM
Well, as far as I understand, this link is about managing VMs using host's PowerShell commands right?
But what I meant was managing a server's Snap-Ins remotely via another server(and both of these servers are actually Virtual Machines).

However, something goes wrong with the first command (the other commands work properly).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 26 2018 12:03 PM
SolutionOk, I see now. I was under the impression you were working between the two Hyper-V hosts.
I just loaded up a Server Core 2016 and Server 2016 w/ GUI (both Datacenter) and can confirm that firewall rule does not exist on ServerCore. Here's the code I used to check.
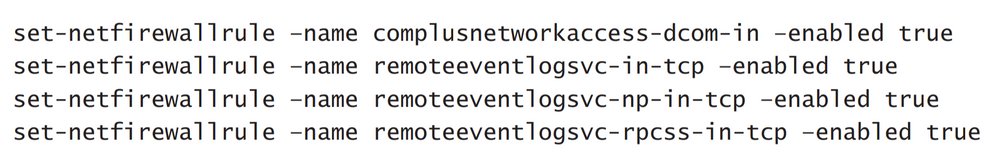
Write-Host "Server 2016 with GUI" Get-NetFirewallRule –Name COMPlusNetworkAccess-DCOM-In | select Name, Enabled Get-NetFirewallRule –Name RemoteEventLogSvc-In-TCP | select Name, Enabled Get-NetFirewallRule –Name RemoteEventlogSvc-NP-In-TCP | select Name, Enabled Get-NetFirewallRule –Name RemoteEentLogSvc-RPCSS-In-TCP | select Name, Enabled Invoke-Command -Computer ServerCore -ScriptBlock { Write-Host "" Write-Host "Server 2016 Core" Get-NetFirewallRule –Name COMPlusNetworkAccess-DCOM-In | select Name, Enabled
Get-NetFirewallRule –Name RemoteEventLogSvc-In-TCP | select Name, Enabled
Get-NetFirewallRule –Name RemoteEventlogSvc-NP-In-TCP | select Name, Enabled
Get-NetFirewallRule –Name RemoteEentLogSvc-RPCSS-In-TCP | select Name, Enabled } Server 2016 with GUI Name Enabled ---- ------- ComPlusNetworkAccess-DCOM-In False RemoteEventLogSvc-In-TCP False RemoteEventLogSvc-NP-In-TCP False RemoteEventLogSvc-RPCSS-In-TCP False Server 2016 Core No MSFT_NetFirewallRule objects found with property 'InstanceID' equal to 'complusnetworkaccess-dcom-in'. Verify the value of the property and retry. + CategoryInfo : ObjectNotFound: (complusnetworkaccess-dcom-in:String) [Get-NetFirewallRule], CimJobExc eption + FullyQualifiedErrorId : CmdletizationQuery_NotFound_InstanceID,Get-NetFirewallRule + PSComputerName : ServerCore RemoteEventLogSvc-In-TCP False RemoteEventLogSvc-NP-In-TCP False RemoteEventLogSvc-RPCSS-In-TCP False
So, that rule is related to the Desktop Experience (GUI) that is installed when you go the non-core route.
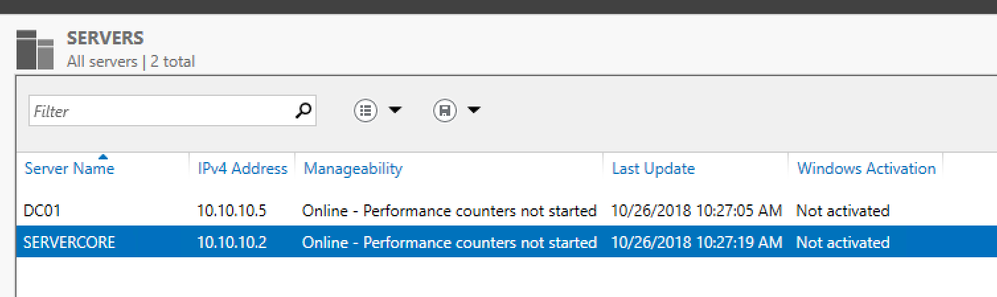
I can also confirm that, that rule won't prohibit you from managing a Core Server via Server Manager, as you can see below in the screenshot.
So, it looks as if that rule existed at one point in Server Core which was later removed from Server Core during a release, however, again, it's not required to manage it via Server Manager.
If you're running the full GUI Server, you need to and can enable that rule.
For the sake of the exam, that content may be out of date, but if you're asked that question, assume you need to use those four firewall rules to enable the communication channel.
I just pulled up that book and it was written in Jan 2017 so a lot of things have changed in Server. Unfortunately it looks like you've ran into one of those instances where pieces of the exam content isn't accurate any longer.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 26 2018 12:03 PM
SolutionOk, I see now. I was under the impression you were working between the two Hyper-V hosts.
I just loaded up a Server Core 2016 and Server 2016 w/ GUI (both Datacenter) and can confirm that firewall rule does not exist on ServerCore. Here's the code I used to check.
Write-Host "Server 2016 with GUI" Get-NetFirewallRule –Name COMPlusNetworkAccess-DCOM-In | select Name, Enabled Get-NetFirewallRule –Name RemoteEventLogSvc-In-TCP | select Name, Enabled Get-NetFirewallRule –Name RemoteEventlogSvc-NP-In-TCP | select Name, Enabled Get-NetFirewallRule –Name RemoteEentLogSvc-RPCSS-In-TCP | select Name, Enabled Invoke-Command -Computer ServerCore -ScriptBlock { Write-Host "" Write-Host "Server 2016 Core" Get-NetFirewallRule –Name COMPlusNetworkAccess-DCOM-In | select Name, Enabled
Get-NetFirewallRule –Name RemoteEventLogSvc-In-TCP | select Name, Enabled
Get-NetFirewallRule –Name RemoteEventlogSvc-NP-In-TCP | select Name, Enabled
Get-NetFirewallRule –Name RemoteEentLogSvc-RPCSS-In-TCP | select Name, Enabled } Server 2016 with GUI Name Enabled ---- ------- ComPlusNetworkAccess-DCOM-In False RemoteEventLogSvc-In-TCP False RemoteEventLogSvc-NP-In-TCP False RemoteEventLogSvc-RPCSS-In-TCP False Server 2016 Core No MSFT_NetFirewallRule objects found with property 'InstanceID' equal to 'complusnetworkaccess-dcom-in'. Verify the value of the property and retry. + CategoryInfo : ObjectNotFound: (complusnetworkaccess-dcom-in:String) [Get-NetFirewallRule], CimJobExc eption + FullyQualifiedErrorId : CmdletizationQuery_NotFound_InstanceID,Get-NetFirewallRule + PSComputerName : ServerCore RemoteEventLogSvc-In-TCP False RemoteEventLogSvc-NP-In-TCP False RemoteEventLogSvc-RPCSS-In-TCP False
So, that rule is related to the Desktop Experience (GUI) that is installed when you go the non-core route.
I can also confirm that, that rule won't prohibit you from managing a Core Server via Server Manager, as you can see below in the screenshot.
So, it looks as if that rule existed at one point in Server Core which was later removed from Server Core during a release, however, again, it's not required to manage it via Server Manager.
If you're running the full GUI Server, you need to and can enable that rule.
For the sake of the exam, that content may be out of date, but if you're asked that question, assume you need to use those four firewall rules to enable the communication channel.
I just pulled up that book and it was written in Jan 2017 so a lot of things have changed in Server. Unfortunately it looks like you've ran into one of those instances where pieces of the exam content isn't accurate any longer.