- Home
- Windows Server
- Windows Server for IT Pro
- Re: RDP authentication failures not reflected in security log?
RDP authentication failures not reflected in security log?
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 27 2022 01:55 PM
Hi. We just installed a Windows Server 2019 test server. I am trying to have the server send me a notification if someone tries - and fails to authenticate.
I am doing this using the Task Scheduler in Windows Server. I created a task and set the trigger to check for event number 4625 in the security log. This approach worked great for our old Windows 2012 servers.
Oddly, in the new version, this doesn't work. It does work if i fail a physical logon attempt at the server, but if I try to RDP from my workstation and use the wrong password, nothing is logged in the security log.
I have tried these two articles but neither worked for me.
http://woshub.com/block-rdp-brute-force-powershell-firewall-rules/
https://community.spiceworks.com/topic/498564-remote-desktop-logon-failed-audit-events towards the bottom where they recommend changing the group policy. (the item marked best answer)
I am guessing in 2019 these events are somehow suppressed when using RDP to connect to the server. Is there a way I can get this event logging? I cant see any other events in the event log that get raised when I fail to authenticate over RDP.
- Labels:
-
Security
-
Windows Server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 27 2022 04:38 PM
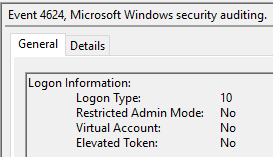
For Server 2019 and 2022, I'm seeing the relevant "Logon type = 10" (the type for Terminal Server logins) entries being logged in the Security event log under event 4624.
You may just be checking for the wrong event ID, or perhaps you need to run a resultant set of policy check (gpresult /h) to confirm there are no group policies (domain or local) overriding any manually-specified local settings.
Cheers,
Lain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 28 2022 09:50 AM
Thanks for responding! Oddly, these events are also not being reported. However, I discovered that if I use my surface (which is not joined to the domain) and access the server with invalid credentials, then it all works. They wound up being reported under event id 4776 in the security log.
I did run gpresult /h ... to check group policy and nothing stood out to me.
What makes me wonder is are the failed login events not reporting for in-domain computers? or is it that I am a domain admin logged into my workstation so that when I fail to log in to the domain controller it doesn't report those? Seems worrisome from a security perspective to me, but who knows?
Thanks again for your help on this!
Cory
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 28 2022 08:48 PM
Fair enough. That doesn't make a lot of sense to me as the two event IDs are for very different purposes, but if that's what you're seeing, there's not much else I can say.
Event IDs are very-well defined. I've dropped the references for both below.
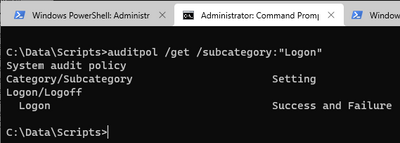
If you run the following as an administrator on the server/client into which you're RDP-ing, it will tell you how auditing is currently set (directly, meaning GPO would override it, but you say there is no GPO) on the Logon category, and if so, whether it's for successes and/or failures only, neither or both:
auditpol /get /subcategory:"Logon"
Example output showing both auditing types are set:
Reference articles:
- 4624(S) An account was successfully logged on. (Windows 10) - Windows security | Microsoft Docs
- Audit Logon (Windows 10) - Windows security | Microsoft Docs
- 4776(S, F) The computer attempted to validate the credentials for an account. (Windows 10) - Windows...
Cheers,
Lain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 05 2023 11:25 AM - edited Mar 05 2023 11:25 AM
SolutionThis is actually by design.
You see, when you attempt to logon to an RDP session, the security provider behind the logon process called CredSSP decides whether to employ Kerberos or NTLM to verify your identity to the remote computer.
If Kerberos is available for which you need direct line of sight towards the Domain Controller, CredSSP attempts to verify your credential with the Domain Controller. If the password provided is wrong, the Domain Controller logs an Event ID 4771 - Kerberos PreAuthentication Failed.
If Kerberos is not avaialble, CredSSP falls back to NTLM and attempts to verify your credential directly with the remote computer which in turn relays the credential verification to the Domain Controller. If, in this case, the password provided is wrong, the remote computer logs an Event ID 4625 - Logon Failed and the Domain Controller logs an Event ID 4776 - Credential Validation Failed.
Cheers,
Vojtech
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 10 2023 10:39 AM
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 05 2023 11:25 AM - edited Mar 05 2023 11:25 AM
SolutionThis is actually by design.
You see, when you attempt to logon to an RDP session, the security provider behind the logon process called CredSSP decides whether to employ Kerberos or NTLM to verify your identity to the remote computer.
If Kerberos is available for which you need direct line of sight towards the Domain Controller, CredSSP attempts to verify your credential with the Domain Controller. If the password provided is wrong, the Domain Controller logs an Event ID 4771 - Kerberos PreAuthentication Failed.
If Kerberos is not avaialble, CredSSP falls back to NTLM and attempts to verify your credential directly with the remote computer which in turn relays the credential verification to the Domain Controller. If, in this case, the password provided is wrong, the remote computer logs an Event ID 4625 - Logon Failed and the Domain Controller logs an Event ID 4776 - Credential Validation Failed.
Cheers,
Vojtech