- Home
- Windows Server
- Windows Server for IT Pro
- Proper security setting for GPO with loopback
Proper security setting for GPO with loopback
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 07 2020 02:45 PM - edited Apr 07 2020 02:47 PM
I am stuck at what the proper security settings should be for loopback processing GPOs. This is specifically applicable to terminal servers as many articles point out. Assume a very simple situation based on the following ad schema:
User U1 is member of the Organisational Unit OU1 and member of Security Group SG1. The Security Group SG1 resides in Organisational Unit OU2 (neither the same as OU1 its subOU or vice versa). The terminal server redides in Organisation Unit OU3 (again, neither the same nor sub as OU1 or OU2).
The goal is simple, if any user, which is a member of SG1, logs to S1, User Settings of a particular GPO (Say GPO1) should merge into other GPOs applied to S1.
My initial assumption for Delegation of GPO1:
- Authenticated Users - only read permission, not apply (otherwise this would apply to all other users as well, but at least read so that S1 can actually read that policy)
- SG1 - Read and Apply.
But this does not work. A test when both Authenticated Users as well as SG1 have "read and apply" rights results in application of the said GPO. But this is not what is intended. So the question is really simple, how to achieve the goal?
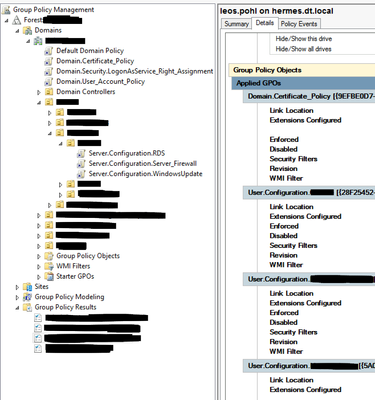
The whole situation is no helped by erroneous information (in my world, I would call this a bug) provided by policy modelling and policy results wizards. Eg in the case when Authenticated users only have read on GPO1 and SG1 have read an apply, policy results does not report correctly the applied GPOs:
This shows some applied settings in the GPO Results:
And listing down to Applied GPOs, it shows (note that NOWHERE in the the applied GPOs there is Default Domain Policy while as you can see above, it IS applied)