- Home
- Windows Server
- Windows Server for IT Pro
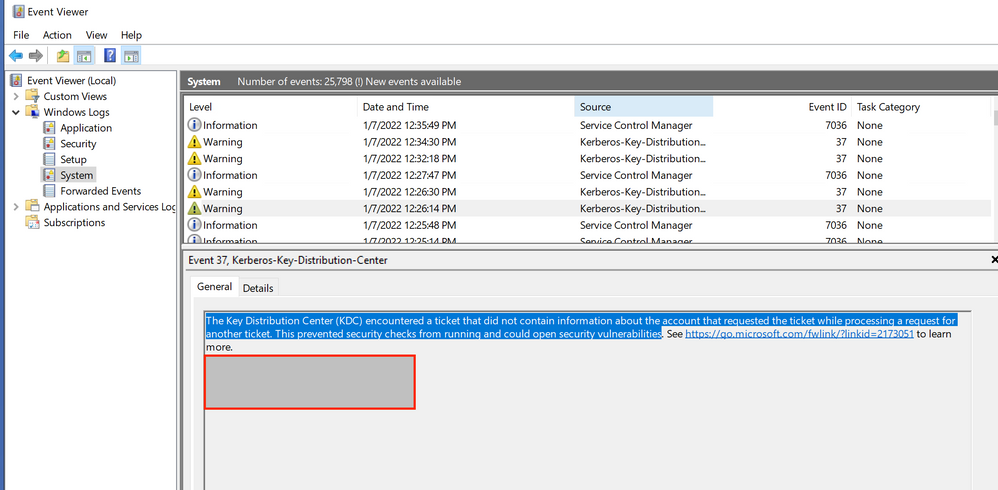
- Promoted Windows Sever 2019 to DC, getting many Event ID 37 errors
Promoted Windows Sever 2019 to DC, getting many Event ID 37 errors
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 07 2022 11:07 AM
I promoted a Windows Server 2019 server to a DC (the 2nd one in my domain). Now I am getting several Event ID 37 errors. Looks like I am getting them for user accounts and machines, that were working fine before this migration. Any ideas on what I need to to do secure and correct this issue?
The link provided in the Event Log is telling me I need to install an update from November 2021?
(Link from Event Viewer: https://support.microsoft.com/en-us/topic/kb5008380-authentication-updates-cve-2021-42287-9dafac11-e...
Thank you for your help.
- Labels:
-
Active Directory
-
Security
-
Windows Server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 07 2022 12:22 PM
Yes, install the latest SSU,
https://www.catalog.update.microsoft.com/Search.aspx?q=KB5005112
followed by the latest cumulative updates
https://www.catalog.update.microsoft.com/Search.aspx?q=KB5008218
Patch all the domain controllers as first step. Then each user will get the new improved authentication information PACs of Kerberos Ticket-Granting Tickets. (TGT) described in the KB
Then it looks like you may get one warning for every user.
https://support.microsoft.com/en-us/topic/kb5008380-authentication-updates-cve-2021-42287-9dafac11-e...
***Adds the new PAC to users who authenticated using an Active Directory domain controller that has the November 9, 2021 or later updates installed. When authenticating, if the user has the new PAC, the PAC is validated.***
the ***PacRequestorEnforcement*** registry value's only function is to allow you to transition to the Enforcement phase early. Otherwise not needed.
--please don't forget to upvote and Accept as answer if the reply is helpful--
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 07 2022 07:24 PM - edited Jan 07 2022 07:24 PM
Both of those are already installed on the 2019 server.
When I go to the 2008 DC and check Windows Updates there is only one (1) that is needed: It is a Windows Malicious Software Removal Tools x64 KB890830.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 07 2022 07:31 PM
For 2008 SP2 (vista kernel) install the SSU
https://www.catalog.update.microsoft.com/Search.aspx?q=KB4493730
followed by the latest cumulative update.
https://www.catalog.update.microsoft.com/Search.aspx?q=KB5008274
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 07 2022 07:59 PM - edited Jan 07 2022 08:01 PM
KB4493730 says "The update does not apply to your system"
KB5008274 says "The Windows Modules Installer must be updated before you can install this package. Please update the Windows Module Installer on your computer, then retry setup."
The URL in the above dialog box reply, is the same it takes me to - a general support page.
When I saw The update does not apply, I looked at the System Tab it says Windows Server Standard FE. (??)
I inherited this system from the previous employee, so I have no one to ask question about setup.
**UPDATE: When I try to search for the KB in the URL KB925316 in the Windows Catalog nothing shows.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 07 2022 08:11 PM - edited Jan 07 2022 08:14 PM
It might be time to get rid of that one.
Windows Server 2008 for Windows Essential Server Solutions - Microsoft Lifecycle | Microsoft Docs
I don't think that one can be covered by extend security updates
How to use Extended Security Updates (ESU) for Windows Server | Microsoft Docs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 08 2022 07:14 AM
I thought I would setup a new DC in the domain and then promote it to primary, so I could disable the 2008 DC.
Do you have any suggestions on how to accomplish this?
Everything was going along so well until this issue. :(
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 08 2022 07:25 AM
https://techcommunity.microsoft.com/t5/Storage-at-Microsoft/Streamlined-Migration-of-FRS-to-DFSR-SYS...
I'd use dcdiag / repadmin tools to verify health `correcting all errors found` before starting `any` operations. Then stand up the new 2019 or 2022, patch it fully, license it, join existing domain, add active directory domain services, promote it also making it a GC (recommended), transfer FSMO roles over (optional), transfer pdc emulator role (optional), use dcdiag / repadmin tools to again verify health, when all is good you can decommission / demote old one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 09 2022 02:12 PM
Just checking if there's any progress or updates?
--please don't forget to upvote and mark answer if the reply is helpful--
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 09 2022 06:06 PM - edited Jan 09 2022 06:07 PM
I have been off work and will start working on the new domain controller on Jan 10.