- Home
- Windows Server
- Windows Server for IT Pro
- Re: Outdated patches being flagged out by offline WSUS scan
Outdated patches being flagged out by offline WSUS scan
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 10 2020 11:24 AM
Hi all, I currently have a Win 2008 R2 server on my environment.
As it is a isolated environment with no internet access, I have been patching the server manually through WSUS export/import process.
I understand that it has already been declared end of life by Microsoft early this year.
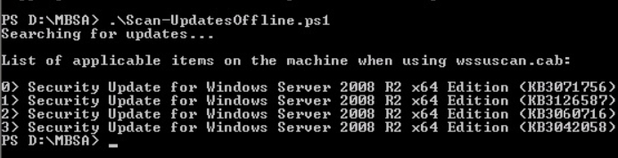
So to completely declare my server is free from any further updates, I ran the offline scan (Scan-UpdatesOffline.ps1), the script flags out that I am missing these 2017 patches although I have the Jan 2020 security updates installed.
Tried to install them manually but the installation keeps failing.
Is there any way to know safe to ignore them as a false positive so I can let my higher-ups know?
And does the CVE that comes with them are fixed from the Jan 2020 security updates?
Thank you
- Labels:
-
Windows Server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 10 2020 03:34 PM
unless you installed the big Rollup KB3125574, all those updates are still applicable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 11 2020 04:12 AM
Firstly, thanks for the reply.
I think its outdated because I already has the latest 2020 updates installed on my machine.
KB3125574 was installed on my machine, so the updates are no longer applicable?
May I know where do you get this information from?
Can you share it with me?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 11 2020 08:49 PM
@WaynerH Windows 7 / S2008 R2 still require updates that goes back to 2012
yes, KB3125574 replace them all on the contained components level (verified myself)
unfortunately, Microsoft have/had a rule rgarding metadata supersedence: optional or quality updates do not replace security updates
that's why you don't see in MU catalog that KB3125574 replace
i cannot provide you with a solid evidence of this
however, KB3125574 actually live-up to the info mentioed in its KB article
https://support.microsoft.com/en-us/help/3125574
meaning, it does replace all post SP1 updates, except the hotfixes listed explicitly (IE updates are exempted of course)