- Home
- Windows Server
- Windows Server for IT Pro
- NTLM authentication failed because the account was a member of the Protected User group
NTLM authentication failed because the account was a member of the Protected User group
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 20 2020 05:29 PM
Hi everyone,
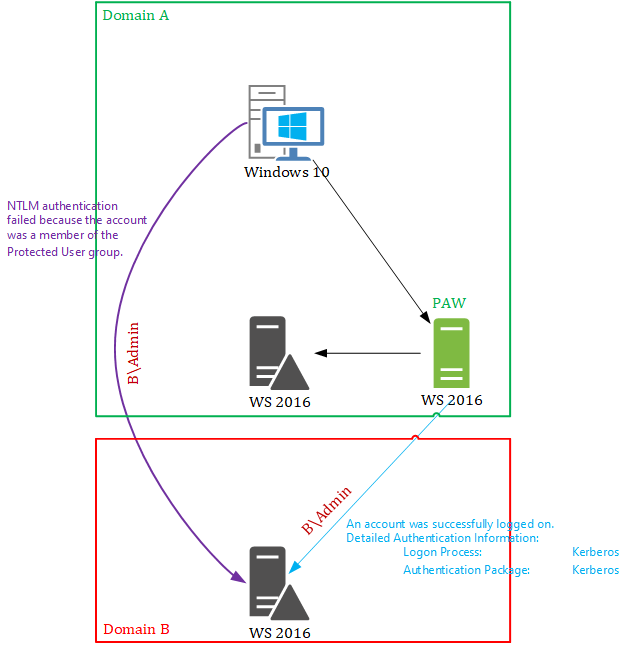
we have two domains (A and B), each has its own forest and two domain controllers. There is a trust between domains. Each admin has two Domain Admins account in each domain (like A\Admin and B\Admin).
Domain A has a PAW, where the admins are logging on with A\Admin and managing both domains (A\Admin was delegated some rights in domain B). But sometimes the admins have to connect (via RDP) to some servers in B domain using B\Admin account. If an admin connects from his own computer (Windows 10) - it fails because of NTLM authentication, which is not allowed for the members of the Protected Users group. Then the admins connect from PAW and it works. In the logs I see another type of the Authentication - Kerberos!
Questions:
- why the NTLS is used connecting from Windows 10 and Kerberos from WS 2016 (not from all servers, but from PAW only)?
- how to enable Kerberos authentication on Windows 10 to be able to connect to a server in another Domain using credentials of this domain? I've already set a policy "Send NTLMv2 response only, refuse LM and NTLM" - didn't help.
To better understand my issue I drew a picture of infrastructure:
Thank you in advance!
- Labels:
-
Active Directory
-
Kerberos
-
NTLM