- Home
- PowerShell Community
- Windows PowerShell
- Trying to resolve foreignsecurityprincipal information
Trying to resolve foreignsecurityprincipal information
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 17 2022 09:55 AM
Hi all
I'm trying to help a customer unpack some very large groups ie membercount>5000 and some of the members are groups and some are users and to add to the complexity some of the members are foreign security principals from other domains and forests.
I've come up with some thing that works but not completely and is very messy.
Is there a way in Powershell, using the AD Module cmdlets, to retrieve the information of a greignsecurityprincipal assuming the trust the domain in question still exists.
I've cobbled together something that but I was wondering if there is a more elegant approach.
I came across some information about the Translate method but I've not been able to figure that one out yet..
I find the syntax a bit arcane to be honest..
Any help would be appreciated
- Labels:
-
Windows PowerShell
-
Windows Server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 17 2022 05:36 PM - edited May 17 2022 06:57 PM
Hi, Peter.
Here's a basic example involving the foreignSecurityPrincipal class and .Translate() method.
I don't use the ActiveDirectory module much though since it limits portability, so it's calling .NET directly from PowerShell.
You should be able to customise it to fit your needs.
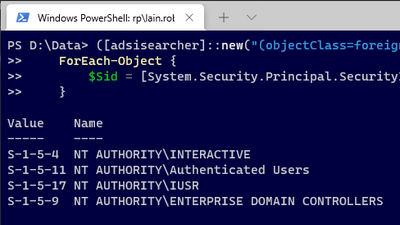
([adsisearcher]::new("(objectClass=foreignSecurityPrincipal)", @("objectSid"))).FindAll() |
ForEach-Object {
$Sid = [System.Security.Principal.SecurityIdentifier]::new($_.Properties["objectSid"][0], 0); $Sid | Select-Object -Property Value, @{n="Name"; e= { $Sid.Translate([System.Security.Principal.NTAccount]) } };
}
Assuming you're targeting classes that contains the objectSid attribute (only security principals contain an objectSid) then it returns output like the following:
Cheers,
Lain
Edited for spelling corrections.