- Home
- PowerShell Community
- Windows PowerShell
- Part 3 - Manage Azure and Microsoft 365 with the Microsoft Graph PowerShell SDK!
Part 3 - Manage Azure and Microsoft 365 with the Microsoft Graph PowerShell SDK!
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 08 2022 06:00 AM
Dear Microsoft Azure and Microsoft 365 Friends,
This article continues with the topic Microsoft Graph PowerShell SDK.
Part 1 and 2 can be found here:
How to Connect to Microsoft 365?
1. With direct Command
or
2. Azure App Registration
Modifying an Existing Connection:
- Scopes are required for each connection
- Scope permissions are for the current session (unless using an Azure App Registration)
- Extra needed permissions require re-connecting with the specified scopes
Viewing Existing Connection Details:
#If needed
Import-Module Microsoft.Graph
#Connect to Microsoft 365 to Access Users and Groups
Connect-MgGraph -Scopes "User.ReadWrite.All","Group.ReadWrite.All"
#View Current Connection Details
Get-MgContext
(Get-MgContext).AuthType
(Get-MgContext).Scopes
Reconnect Connection with Updated Scopes:
#Original Connection
Connect-MgGraph -Scopes "User.ReadWrite.All","Group.ReadWrite.All"
#Update Connection to Allow "Group Members"
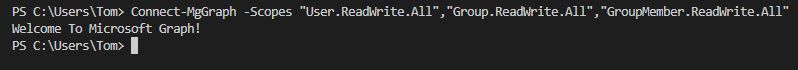
Connect-MgGraph
-Scopes "User.ReadWrite.All","Group.ReadWrite.All","GroupMember.ReadWrite.All"
Don't forget, when updating the connection, you need to confirm the consent again.
#View the new Current Connection Details
Get-MgContext
(Get-MgContext).AuthType
(Get-MgContext).Scopes
Connecting Using an Azure App Registration (Advantages of Azure App Registrations):
- App-only Access Grants Permissions to an Application
- Requires Administration Consent
- Predefined Permissions Control Access
Prerequisites to Using App-only Authentication:
- Require a Certificate
- Self-signed or from an Authority
- Register an Azure Active Directory App
- Assign Required Permissions Scopes
- Share the Public Key of the Certificate
Creating a Self-signed Certificate:
#Create the Certificate
#Export the Created Certificate
Export-Certificate -Cert $cert -FilePath "C:\Certs\{GraphCertificate}.cer"
#Set the Password and Export as "PFX"
$pwd = ConvertTo-SecureString -String "{Password}" -Force –AsPlainTextExport -PfxCertificate `
-Cert $cert -FilePath "C:\Certs\{GraphCertificate}.pfx" -Password $pwd
Create the Azure App Registration:
1. Navigate to the Azure Active Directory Admin Center
2. Register a New Application using Accounts in the Organizational Directory Only
3. Copy the Application and Directory ID
4. Assign API Permissions
5. Upload the Certificate
Connect Using Azure App Registration:
#Connect Using an Azure App Registration
Connect-MgGraph `
-ClientId "YOUR CLIENT ID" `
-TenantId "YOUR TENANT ID" `
-CertificateThumbprint "YOUR CERT THUMBPRINT"
#Check the Current Context
Get-MgContext
That's it for the third part. In the next part, we will continue with managing Users and Groups. See you soon!
I hope this article was useful. Thank you for taking the time to read the article.
Best regards, Tom Wechsler
P.S. All scripts (#PowerShell, Azure CLI, #Terraform, #ARM) that I use can be found on github! https://github.com/tomwechsler