- Home
- PowerShell Community
- Windows PowerShell
- Re: Modifying NTFS Permissions Using the NTFSSecurity Module
Modifying NTFS Permissions Using the NTFSSecurity Module
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 01 2020 07:30 AM - edited Dec 02 2020 05:22 AM
Hi All,
I am hoping someone can help me crack this issue.
I have been tasked with changing the Access Rights on millions of files and folders for each user/group that has access to them currently. These will be set to Read,Execute,Delete as the highest access permissions granted. Anything less than that like List or Traverse will left as is.
This I can do ok with 'where-object' etc.
I am using the NTFSSecurity PowerShell module.
My biggest issue is that when I use Get-NTFSAccess -Path \\Folder\I\am\Checking and output to the console or OGV, I get the following headers.
Account Access Rights Applies to Type IsInherited InheritedFrom
Contoso\TestAccount1 FullControl ThisFolderSubfoldersAndFiles Allow False
Contoso\TestAccount2 Modify, Synchronize ThisFolderOnly Allow False
Contoso\TestAccount3 Traverse ThisFolderAndFiles Allow False
However, if I export to csv, I get the following headers.
AccountType, Name, FullName, InheritanceEnabled, InheritedFrom, AccessControlType, AccessRights, Account, InheritanceFlags, IsInherited, PropagationFlags
I know the InheritanceFlags refer to the Access Rights, but is it possible when using Add-NTFSAccess
to read the InheritanceFlags values as I am doing with the other values and set them so that the
“applies to this folder only, this folder and files, List”, etc are not changed from their current settings.
So, this:
AccessControlType AccessRights Account InheritanceFlags IsInherited PropagationFlags
Allow FullControl Contoso\TestAccount1 ContainerInherit, ObjectInherit FALSE None
Allow Modify, Synchronize Contoso\TestAccount2 ObjectInherit FALSE None
Allow Traverse Contoso\TestAccount3 ContainerInherit FALSE None
Would become this:
AccessControlType AccessRights Account InheritanceFlags IsInherited PropagationFlags
Allow Delete, ReadAndExecute, Synchronize Contoso\TestAccount1 ContainerInherit, ObjectInherit FALSE None
Allow Delete, ReadAndExecute, Synchronize Contoso\TestAccount2 ObjectInherit FALSE None
Allow Traverse Contoso\TestAccount3 ContainerInherit FALSE None
Or This:
Account Access Rights Applies to Type IsInherited InheritedFrom
Contoso\TestAccount1 Delete, ReadAndExecute, Synchronize ThisFolderSubfoldersAndFiles Allow False
Contoso\TestAccount2 Delete, ReadAndExecute, Synchronize ThisFolderOnly Allow False
Contoso\TestAccount3 Traverse ThisFolderAndFiles Allow False
And the "Applies to" settings would not change.
If I create variables from the csv for each value required
At the moment when I run the script that includes Add-NTFSAccess -Path $Fullname -Account $Account -AccessRights 'ReadAndExecute,Delete' -AccessType Allow -InheritanceFlags $InheritanceFlags
Everything is set to ThisFolderSubFoldersAndFiles.
If I could use the -AppliesTo instead of -InheritanceFlags and feed in exactly what is already present when displaying get-NTFSAccess in the console or OGV, I think this would resolve 99% of my issues.
I have looked at apps like NTFS Permission Reporter, but I am sure this should be achievable with PS.
I know there must be a simple solution, (Arrays, iCacls?) but I just cannot see how to do it.
Any help would be awesome!
- Labels:
-
powershell script
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 01 2020 12:52 PM
Take a look on this post.
https://stackoverflow.com/questions/37013298/powershell-acls-apply-to-this-folder-only
They have an example of how you can add a ACL entry and set it to Apply only to this Folder.
I did not work with the NTFS Security module, and usually like to do things without any module.
So maybe the thing you are asking is not implemented, did you check the documentation to see if its an existing feature ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 02 2020 06:20 AM
Hi @farismalaeb ,
Thank you for your reply. I can set the folders to the various options, but what I really trying to achieve is to read the current ACL Rule, reading them directly from a variable/array or csv
Account | Access Rights | Applies to | Type | IsInherited | InheritedFrom |
Contoso\TestAccount1 | FullControl | ThisFolderSubfoldersAndFiles | Allow | False |
|
Contoso\TestAccount2 | Modify, Synchronize | ThisFolderOnly | Allow | False |
|
Contoso\TestAccount3 | Traverse | ThisFolderAndFiles | Allow | False |
|
Modify any Access rights with the ability to create or modify existing files/folders and set them to ReadandExecute,Delete. BUT not to change the Applies To values, but read them straight from the existing variable/array or csv and but to reapply them exactly as they were prior to changing the Access Rights.
eg
Account | Access Rights | Applies to | Type | IsInherited | InheritedFrom |
Contoso\TestAccount1 | ReadAndExecute,Delete | ThisFolderSubfoldersAndFiles | Allow | False |
|
Contoso\TestAccount2 | ReadAndExecute,Delete | ThisFolderOnly | Allow | False |
|
Contoso\TestAccount3 | Traverse | ThisFolderAndFiles | Allow | False |
|
Hope that makes it a little clearer, I basically want to feed back into the ACL rule exactly what is there, but only modify the level of access rights.
Kind Regards
MoZZa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 03 2020 11:33 PM
SolutionHi @MoZZa
I tried The NTFSSecurity Module, but it seems that there still some missing features in it such as Set-NTFSAccess, or maybe I did not see it.
anyway.
I wrote a code that will do the following
will read the permission from the folder to a variable, set change the value in the variable (it was hardcoded), and then apply these settings to the folder back, this will not change the Apply to scope, and the only thing that should change is the permission only and nothing else
anyway
i did the test on my lab and its a small scope, try it from your side and let me know
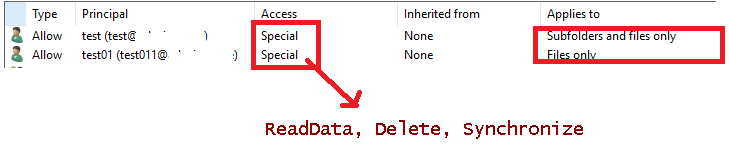
below are some pictures of the result, Oh, did I forget to tell you that i did not use the NTFSSecurity module.
Before the Script
After the Script
$acl=Get-Acl -Path C:\MyTestFolder
foreach ($singleACL in ($acl.Access | where {($_.FileSystemRights -like "*FullControl*") -and ($_.IsInherited -like $false)})){
$FileSystemRights=@("ReadData, Delete, Synchronize")
$AccessControlType=$singleACL.AccessControlType
$IdentityReference=$singleACL.IdentityReference
$InheritanceFlags=$singleACL.InheritanceFlags
$PropagationFlags=$singleACL.PropagationFlags
$rule = New-Object System.Security.AccessControl.FileSystemAccessRule($IdentityReference, $FileSystemRights,$InheritanceFlags, $PropagationFlags, $AccessControlType) # This folder only
$acl.SetAccessRule($rule)
Set-Acl -Path C:\MyTestFolder -AclObject $acl
}Try the script, and let me know
and I hope I understand the requirement correct (sometime my bad English fails me ![]() )
)
----------------
If this answer helped, please click on best Response and give like :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 07 2020 08:08 AM - edited Dec 07 2020 08:08 AM
Hi @farismalaeb ,
Many thanks for thanks, I will give it a go in my test environment and get back to you.
Thank you so much for your feedback!!!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 11 2020 11:10 AM
Hi @farismalaeb,
I have tested your script and with a few modifications to suite our environment IT WORKS!!!
Thank you so much , just 4 or 5 lines added to my script and its works.
Here is a sample of the script that just does the top layer where it is a root inheritance parent folder.
Import-Module ActiveDirectory
$ExcludedPaths = @()
$ForUser = "MoZZa"
$AnalysePath = "\\Contoso\X$\Shared\Some\Data\Here"
$ExcludedPaths = @('\\Contoso\X$\Shared\Some\Data\Here\Dont\Change\This\Path','\\Contoso\X$\Shared\Some\Data\Here\Dont\Change\This\Path\Either') #Place excluded paths here '\\path1','path2' format
$MasterACL=Get-Acl -Path $AnalysePath
ForEach($Master in $MasterACL.Access){
if ($Master.IdentityReference -notlike "BUILTIN\Administrators" -and
$Master.IdentityReference -notlike "Contoso\Domain Admins" -and
$Master.IdentityReference -notlike "Contoso\Domain Users" -and
$Master.IdentityReference -notlike "CREATOR OWNER" -and
$Master.IdentityReference -notlike "NT AUTHORITY\SYSTEM" -and
$Master.IdentityReference -notlike "BUILTIN\Users" -and
$Master.IdentityReference -notlike "Contoso\Backup Users" -and
$Master.IdentityReference -notlike "Contoso\SCCM Blah Blah" -and
$Master.IdentityReference -notlike "S-1-5-21-*" -and
$Master.FileSystemRights -notlike "Delete, ReadAndExecute, Synchronize" -and
$Master.FileSystemRights -notlike "ReadData, ExecuteFile, Synchronize" -and
$Master.FileSystemRights -notlike "ListDirectory, Traverse, Synchronize" -and
$Master.FileSystemRights -notlike "Delete, Read, Synchronize" -and
$Master.FileSystemRights -notlike "ReadAndExecute, Synchronize" -and
$Master.AccessRights -notlike "ListDirectory, Delete, Synchronize" -and
$Master.FileSystemRights -notlike "ListDirectory, ReadExtendedAttributes, Traverse, ReadAttributes, Synchronize" -and
$Master.IsInherited -like $False -and
$Master.FullName -notin $ExcludedPaths){
$FileSystemRights=@("Delete, ReadAndExecute, Synchronize")
$AccessControlType=$Master.AccessControlType
$IdentityReference=$Master.IdentityReference
$InheritanceFlags=$Master.InheritanceFlags
$PropagationFlags=$Master.PropagationFlags
$rule = New-Object System.Security.AccessControl.FileSystemAccessRule($IdentityReference, $FileSystemRights,$InheritanceFlags, $PropagationFlags, $AccessControlType) # This folder only
$MasterACL.SetAccessRule($rule)
Set-Acl -Path $AnalysePath -AclObject $MasterACL
}
I have also created a GUI version.
I will upload those tomorrow.
They make it easier for the 1st support team to run the analysis script without having any PS knowledge.
Many thanks again!!!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 24 2023 03:22 PM
@MoZZa hello, per your old post, did you ever make the GUI?
long story short, im very confused and you seem knowledgeable. So i want a program, or a script, that will just give me master rights to everything, every external hdd as well and all files inside so i never have a ANNOT DO X TAST BC OF RIGHTS ever again. i saw some code in the post that you or the other poster created (code might as well be Chinese to me) where would i even enter such code? and how?
is there any software that simply allows me to do this? i dont get why there is not. I see all of these NTFS REPORTER apps, but i dont need a report on anything. i need to be able to CHANGE folders.
If you or anyone can help me accomplish this task with a .bat or software i can use that will allow me to not have this problem. I tried the program, make me admin, didnt do much from what i can tell.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 03 2020 11:33 PM
SolutionHi @MoZZa
I tried The NTFSSecurity Module, but it seems that there still some missing features in it such as Set-NTFSAccess, or maybe I did not see it.
anyway.
I wrote a code that will do the following
will read the permission from the folder to a variable, set change the value in the variable (it was hardcoded), and then apply these settings to the folder back, this will not change the Apply to scope, and the only thing that should change is the permission only and nothing else
anyway
i did the test on my lab and its a small scope, try it from your side and let me know
below are some pictures of the result, Oh, did I forget to tell you that i did not use the NTFSSecurity module.
Before the Script
After the Script
$acl=Get-Acl -Path C:\MyTestFolder
foreach ($singleACL in ($acl.Access | where {($_.FileSystemRights -like "*FullControl*") -and ($_.IsInherited -like $false)})){
$FileSystemRights=@("ReadData, Delete, Synchronize")
$AccessControlType=$singleACL.AccessControlType
$IdentityReference=$singleACL.IdentityReference
$InheritanceFlags=$singleACL.InheritanceFlags
$PropagationFlags=$singleACL.PropagationFlags
$rule = New-Object System.Security.AccessControl.FileSystemAccessRule($IdentityReference, $FileSystemRights,$InheritanceFlags, $PropagationFlags, $AccessControlType) # This folder only
$acl.SetAccessRule($rule)
Set-Acl -Path C:\MyTestFolder -AclObject $acl
}Try the script, and let me know
and I hope I understand the requirement correct (sometime my bad English fails me ![]() )
)
----------------
If this answer helped, please click on best Response and give like :)