- Home
- PowerShell Community
- Windows PowerShell
- Manage M365 MFA setting using Powershell
Manage M365 MFA setting using Powershell
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 06 2021 02:51 AM - edited Sep 06 2021 02:53 AM
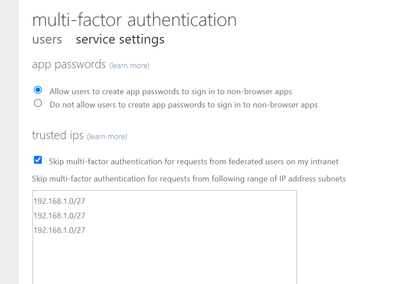
I am enforcing Multi-Factor Authentication for all my M365 users (azure ad plan 2) and it works as expected. Ability to set exceptions when users work from particular branch offices too works as expected. screenshot below.
however, i have many branch offices where the IP address can change every week, so need a way to automate updating the above list.
is there a power shell module i can use to update this list rather then login to the portal and type it out every time there is a change ?
- Labels:
-
MFA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 06 2021 05:17 AM
https://docs.microsoft.com/en-us/powershell/module/azuread/set-azureadmsnamedlocationpolicy?view=azu...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 06 2021 07:36 AM
@pvanberlothanks. but i want to set IP based exceptions only. not interested in conditional access in this case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 06 2021 07:49 AM - edited Sep 06 2021 07:51 AM
@sachin011390 I understand what you're saying, however, Microsoft actually recommends using Azure AD Conditional Access for MFA purposes nowadays. I do not believe there is a programmatic or PowerShell way to change the "trusted IPs for per user MFA" and the portal is the only way to manage this interactively.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 25 2021 09:10 PM
e.g.
New-MgIdentityConditionalAccessNamedLocation
https://docs.microsoft.com/en-us/powershell/module/microsoft.graph.identity.signins/new-mgidentityco...