- Home
- PowerShell Community
- Windows PowerShell
- Re: Inventory SSL Root Cert Remotely Using PowerShell
Inventory SSL Root Cert Remotely Using PowerShell
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 09 2019 05:11 AM
I am not well versed with PowerShell but after researching it appears PowerShell might be the tool I need. I have a need to inventory all computers on my AD to confirm whether or not they have the necessary SSL root certs that I have attempted to push out via GPO.
Most computers do have the certs but I need to identify the ones that do not.
All examples I've run across seem to include "Path Cert :\localmachine". How do I replace 'localmachine' for 'computer name' to gather SSL cert info from remote computers on my LAN?
One example but it is not entirely clear how I would modify this script to connect remotely to each machine:
Get certificate info into a CSV by using PowerShell
Using PowerShell to work with SSL Certificates
- Labels:
-
Windows PowerShell
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 09 2019 09:00 AM
"LocalMachine" is the name of the cert container, it will have the same value on all computers. You can either use Invoke-Command to run the cmdlet against each computer (example https://www.powershellbros.com/powershell-tip-of-the-week-get-certificate-remotely/) or use the built-in capabilities of the .NET method (example here: https://www.experts-exchange.com/questions/28623585/Need-to-get-certificates-inventory-for-each-serv...)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 21 2019 11:50 AM
Thanks @Vasil Michev ,
I've been trying to get up to speed by reviewing the links you sent. I can manually add the list of computers to scan as I learn how to read a CSV. But my question now is how do I turn "LocalMachine" into reading the "Trusted Root Certificate Authorities\Certificates" for both 'Current User' & 'Local Computer'?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 21 2019 11:34 PM
It's as simple as:
dir Cert:\CurrentUser\Root\
dir Cert:\LocalMachine\Root\- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 22 2019 10:50 AM
Hi @Vasil Michev, That seems simple enough in theory. But sadly once I ask for details on certs in that location I get nothing but the computer name when using the following example.:
I'm trying to find 2 specific certs in this location. And if they don't exist in this location I need to know which computer it is that needs them installed. Or stated another way if I can get a report that tells me the cert "IssuedTo" descriptor and the "Expiration Date". Ultimately I need to install the proper certs if they don't exist. I can do that manually. Heck, I can do all of this manually but it would be nice if I work smarter not harder.
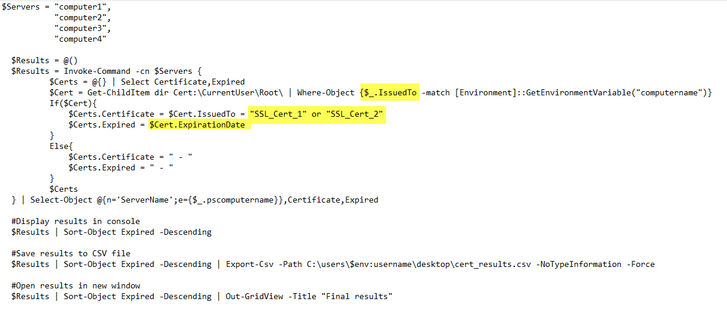
So if I could do this I would like to parse a csv that contains the computer names that I need to check for certs in 'CurrentUser\Root' & 'LocalMachine\Root' that have an 'Issue To' name of 'SSL_Cert_1' & 'SSL_Cert_2' and also display the 'Expiration Date' associated with each cert.
Each computer that does not have the required certs I would like to install these certs. Or at the very least list them so I can pay a visit.
Unfortunately I can't even begin to write the proper syntax to include something like the following.:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2019 12:09 AM
The first example will only list certificates with CN matching the name of the computer, so it's seem to me its working as expected. You can simply remove the where clause and get a full list of certificates, the filter it out in excel or something.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2019 05:41 AM
Well, I did get the first one to work so to speak. It output listed the computers that it ran against. But it was unable to provide any of the cert data. Those fields were blank.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2019 12:08 PM
@Vasil Michev, if you would kindly share with me the proper terminology I would be glad to research further on my own. I'm just not sure where to look for clarification on these commands.
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 24 2019 11:15 AM
Again, the example above checks only for a specific certificate, one that has the CN set to the computer name. Just remove/change that part to get all the certificates instead.