- Home
- Windows Server
- Windows Admin Center Blog
- Windows Admin Center update 1910.2 is now generally available!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Windows Admin Center version 1910.2, which was released to Windows Insiders last month, is now generally available. Version 1910.2 is a cumulative update to our 1910 GA release from last November that includes updates to the platform’s accessibility and numerous bug fixes. Users who have installed version 1910.2 through the Windows Insider Program may continue to use the same version.
Download Windows Admin Center 1910.2 today!
In addition to bug fixes, we’ve evaluated user feedback and have implemented some highly requested features. Your contributions through user feedback continue to help inform and prioritize future investments to improve your user experience.
Windows Admin Center 1910.2 new features and updates
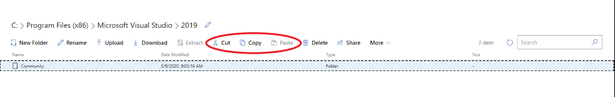
Cut, copy, and paste in the Files tool
A major new feature we’ve included is the cut, copy and paste feature in the Files tool. When you select a folder or file in the Files tool, users have the option to cut or copy the file or folder. After the file or folder is cut or copied, the paste option will become available, and a user can paste the file or folder into a different path.
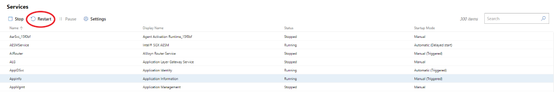
Service restart
We’ve also enhanced several other features, including the Services tool. When managing machines using the Services tool, there is now an option to restart a service. There is no longer a need to start and stop a service in order to restart it.
Other major additions
- Cluster quick update – On the cluster dashboard, updates for connected nodes will appear under the “Alerts” section
- File upload – when a large file upload fails, you are now able to retry the file upload
- Virtual machine filters – When viewing a list of VMs with multiple filters applied, the VMs no longer disappear after some time
- Azure Update Management login – Users no longer receive a logon error when they try to setup Azure update management after setting up Azure monitoring
- Active Directory account creation – We’ve fixed an error in Active Directory Domain Services where accounts could be created with passwords that didn’t meet the complexity requirements
In addition to the new features and fixes above, we are continuing to improve usability issues and make improvements to keyboard navigation and narrator support. We’ve also addressed reported bugs around CredSSP authentication.
Partner extensions
You’ll be excited to hear that the Windows Admin Center ecosystem continues to expand with the GA release of new partner extensions and improvements on existing extensions!
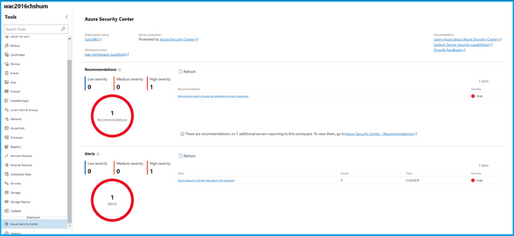
Azure Security Center (ASC) is now generally available
The Azure Security Center extension is no longer in preview and is now generally available! This extension brings hybrid cloud security capabilities to the Windows Admin Center managed servers and allows them to be protected by ASC through a one-click setup. Users of this extension will also see security recommendations and alerts in an embedded view in Windows Admin Center.
This integration is part of a larger Windows Admin Center evolution to offer hybrid Azure services capabilities to on-premises environments. This extends on-premises environments into Azure, allowing them to benefit from cutting edge cloud technologies - an important step as part of a lift and shift motion.
HP Enterprises WAC extension is now generally available
The HPE WAC extension combines the functionality of the HPE Server extension and the HPE Azure Stack HCI extension into a single extension for easier management. This extension utilizes HPE’s iLO technology to give users direct visibility into server inventory and diagnostics to manage and monitor HPE server infrastructure. Using this extension, users can:
- See the health of their servers and remediation options
- View the properties of server components (processor, memory, etc.) and BIOS settings
- Identify and highlight cluster health and node inconsistencies
QCT Management Suite update
The QCT Management Suite is designed to help users manage and monitor their Windows Server hyper-converged infrastructure and QCT system configuration information on a single dashboard. With the upgrade to version 2.0.0, fixes and additions include:
- Bug and typo fixes throughout the tool
- Support for HCI mode on the Overview, Disk, Firmware, and Settings tab
- Additional tooltips
- Addition of dialog panels and drop-down lists in HCI mode
- BMC account settings for Redfish support
- An updated project site URL
Thomas-Krenn.AG extension update
Thomas-Krenn.AG’s extension provides detailed information on cluster nodes and drives, cluster information and cluster network connectivity. With the upgrade to version 1.2.0, users can expect a handful of bug fixes as well as improvements targeted at version 1910.2.
Download today!
We hope you enjoy this update of Windows Admin Center and all the new content! Learn more about using Windows Admin Center and download it today.
Windows Admin Center is constantly improving thanks to feedback from the community. All existing customers will receive this update for free (a notification to update will appear in the product). We hope you enjoy this update, and we're already hard at work on the next one!
<3,
The Windows Admin Center team at Microsoft
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.