- Home
- Windows
- Windows security
- Re: Hardening Windows 10 on an IT Pro's laptop
Hardening Windows 10 on an IT Pro's laptop
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 08 2018 10:28 AM - edited Apr 09 2018 01:50 AM
Hi
I have just bought a new Windows 10 Pro laptop for work as a freelance IT Consultant and I figured this would be good time adopt some of the latest best practices, pertinent to securing my machine. Given, this machine is also for personal use, so I am looking to balance convenience against security and privacy in the event of loss or theft.
I have found some extensive posts on the subject including the one shown below:
I would however, like to hear any comments anyone has: from bitlocker and beyond....
- Labels:
-
security best practices
-
Window 10
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 05 2019 09:32 AM
@HotCakeX So glad my original question/post is hanging around =). I have a different AV so can I configure the changes you mention in addition to what I have or do I need to have Defender as my only AV?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 05 2019 10:33 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 07 2019 01:20 AM - edited Aug 07 2019 01:23 AM
core isolation/memory integrity is the HVCI feature i mentioned a while back, though like all things Microsoft there's a lack of consistency and even the link i gave is now broken haha
it can be enabled regardless of third party AV and its actually enabled by default on new/compatible devices so i see no reason to discourage it's usage, it may break some older drivers but only because they are doing things they shouldn't be, potentially worth noting that the feature has also been bypassed so its usefulness is questionable
the DEP setting mentioned is outdated, despite the wording apps do run with DEP enabled by default
one thing to note about third party AV is that most lack support for vital features like AMSI and ELAM which defender has enabled by default, you should check with your AV provider to see if these are implemented and encourage them to do so if they havent
main thing i've not mentioned that i do suggest looking into is "Attack Surface Reduction rules", ASR rules are part of windows defender but they are off by default, they are a collection of features blocking the most common behaviours seen in the wild, they will genuinely save you from spear & phishing attacks that wont be picked up by any AVs for about a week after its too late, they also seem to add a new one with each release of windows 10
you can learn about them here: https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-exploit-guard/a...
to enable the current ones without the hassle of figuring it out i refer to the powershell in my comment here: https://techcommunity.microsoft.com/t5/Windows-10-security/Harden-Windows-10/m-p/475686
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 07 2019 01:32 AM - edited Aug 07 2019 01:36 AM
1. press ctrl+F in this page and type in core isolation. no one else mentioned it before.
2. source for saying DEP is outdated?
3. that other thread you mentioned looks suspicious. created by "deleted" user name profile?
4. i don't know which AVs you've used before but something better than Windows Defender is Kaspersky AV (Internet Security or End point security which is equivalent to the Windows Defender ATP). Kaspersky has Online connection to their threat center. you say week? for them it takes only minutes to few hours to pass over the new malware's database to the other users. Kaspersky was the First and only company that found Stuxnet and blocked it, the world's Most advanced malware ever created by co-operation of U.S and Israel. then other AV companies copy Kaspersky's database and use it on their own system. Kaspersky even got them red handed by intentionally putting a false alarm in their database and then watched a lot of AVs giving the same false alarm. lol don't believe the news saying that Kaspersky is run by Russian government and it will steal your data, it's total BS and propaganda.
5. Microsoft constantly changes things and technet guides because Windows is constantly changing and getting better. it's the duty of system admins to stay up to date.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 07 2019 02:23 AM - edited Aug 07 2019 02:40 AM
im not trying to argue or anything, i have no conflict with most of what you're saying
1 correct, i was adding that this is what used to be known as HVCI, it was a more up and coming feature that didnt exist as core isolation at the time and now it does, memory isolation also has more features that arent exposed in the GUI so it may be useful for some to know
2 DEP as a memory feature isn't outdated, that GUI setting and its wording however is, if you want a gui to manage it the correct place to configure it now is via the "exploit protection" area of the security centre where you will also see that it is on by default
3 when i clear my microsoft account privacy settings it deletes my tech community account, the posts themselves would be deleted if there were any issues
4 again, not trying to argue, but since you bring it up i will say i am a kaspersky customer and my opinion is that kaspersky is generally as good as windows defender, their database is historically the best though defender in the last year has definitely caught up and is in second place, but toward my point: Kaspersky does indeed support AMSI and ELAM which most other AVs do not, Kaspersky also treats unknowns just as defender does which is why they pick up wrapped variants very quickly, but i maintain that it is impossible to catch everything the first time its ever seen, such as your example stuxnet was caught after the damage was done, not before, and something preventative like ASR could have prevented it ever getting into the supplier's systems
5 exactly, i just ask that you be less hostile, theres enough testosterone fuelled cesspits on the internet already
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 07 2019 05:27 AM
about DEP, the underlying code and script is the same and the OP is having just a Windows 10 pro, other 3rd party tools like that require additional paid licenses and they are supposed to be installed on a stationary server, not a portable device like OP's laptop.
hmm that's weird. I've changed my privacy settings a lot of times and never had that happen to me.. if it's a bug in the site then report it. the only way i know it happens is that when you deliberately delete your account and create a new one with a different Email address..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 10 2019 09:22 AM
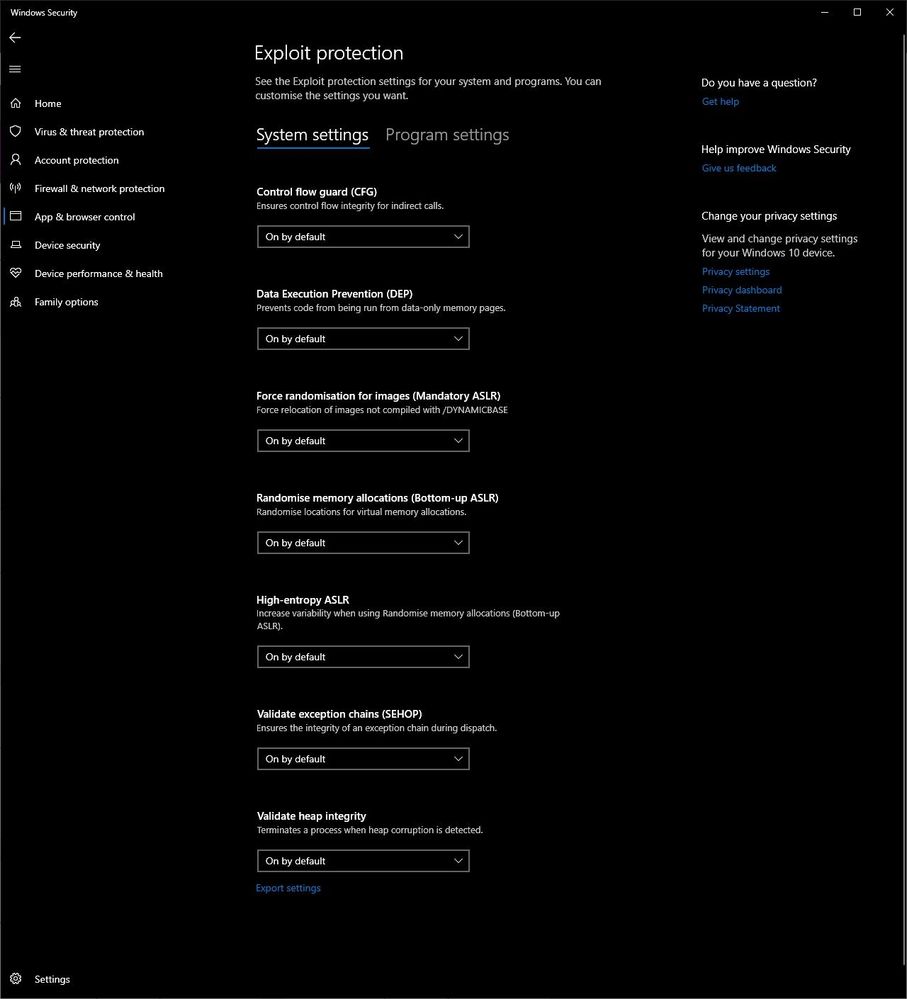
sorry i should be clearer, it is not third party, and it is not implemented the same way, i am talking about the below image, built into windows 10 for free
technically it is a replacement of a previously optional windows 7 tool known as "EMET" which itself was a gui tool for multiple exploit mitigations (not just DEP)
in current windows 10 DEP is enabled by default by this new implementation for applications despite of what you see in that older interface, hence i try to explain that the setting you are advising doesn't have the assumed impact as the outdated wording is misleading
that old interface is from 2003 and you will see in the new one that there are a whole 20 more configurable exploit mitigations (the ones pictured can be configured as system wide defaults, the rest have to be configured on an app by app basis)
i hope this information is interesting and valuable <3
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 10 2019 10:23 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 10 2019 04:08 PM
but it does not even matter, changing that option does not do that, it does not function like it says, i dont know how else to explain this to you, seriously
what i have shown is not part of windows defender, DEP is part of windows itself, the security centre GUI is just a way to manage some windows security features AND windows defender features, and it has the same TWO DEP options:
ON: this is the SAME as: "Turn on DEP for all programs and services" except it actually WORKS
OFF: this is the SAME as: "Turn on DEP for essential Windows programs and services only" except it actually WORKS
THE DEFAULT IS ON
but as you have noticed by default the OLD setting is set to "Turn on DEP for essential Windows programs and services only" which is the same as OFF
how can DEP be ON and OFF for any application at the same time?
simple: it cannot, it is either off or it is on, and it is ON because
THE NEW SETTING WORKS
THE OLD SETTING DOES NOT
how can you suggest that i "really cant tell the difference" when i am wasting my time trying to explain this to you that what you SEE is a misconception
theres many obscure features in windows that have been depreciated, buttons that connect to nothing, text that is incorrect
the option you place trust in is 15 years old, yes it has two options, but DEP has four states
DEP is already enabled, for all programs and services, even though that option is not selected
because that option is overridden by the ON setting in the GUI in the image i showed you
it is YOU that cannot tell the difference
manual exceptions is the only reason why that old interface is still there, because sometimes you need to opt out of this 15 year old security feature to run even older software
but even that is essentially broken too as manual exceptions is replaced by application opt outs
DEP is already enabled, for all programs and services, with application opt outs instead of manual exceptions
enabling the option you are suggesting, only disables those application opt outs causing some old software to be unable to run, thats why its NOT SELECTED BY DEFAULT
things are the way they are for a reason, Microsoft did not spend the last fifteen years doing random engineering for the fun of it
to put it in your own words, "Windows is constantly changing and getting better. it's the duty of system admins to stay up to date." and im not even sure you are a system admin
stuff changes, the best option changes, new becomes old
using windows 7 changing the option is better than the default, feel free to enable it, i encourage it
using windows 10 changing the option is worse than the default, leave it alone, you dont understand what you are breaking
only reason i am responding at all is because there is so much outdated windows advice that people still follow and share online to the detriment of many
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 11 2019 02:07 AM
The problem is that it's just You talking about it WITHOUT PROOF.
just because you say something works or doesn't work doesn't mean it's true. how hard is it to understand. people on the internet don't just believe what someone else says without proof. i can go ahead and say real time protection of Windows Defender doesn't work, turn it off. should you believe me then? of course not.
so unless you understand this basic idea then it's pointless to continue this conversation. sure you can believe whatever you want but don't try to shove it into others.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 01 2020 07:56 AM - edited Jun 01 2020 08:09 AM
Ha ha, I see my original question seem to have triggered a quite protracted or is that just tedious discussion ![]() . Let's switch gears and go back to the original post as I've just ordered a new Dell laptop. So again, I want to harden this from a hardware and Win 10 perspective, making full use of the latest innovations and standards. I did a bit googling, however I think I would get lost without your guru level insight:
. Let's switch gears and go back to the original post as I've just ordered a new Dell laptop. So again, I want to harden this from a hardware and Win 10 perspective, making full use of the latest innovations and standards. I did a bit googling, however I think I would get lost without your guru level insight:
Windows Hello with, or without Bitlocker - it comes with TPM 2.0
Can I get my security config scored by something - see step below:
Which bits of the Windows 10 Security Configuration Framework
Options for antitheft and retrieval.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 02 2020 03:15 AM
Why not buy Windows Secured-core C instead of some random Dell ?
https://www.microsoft.com/en-us/windowsforbusiness/windows10-secured-core-computers
Much better start.
Anyway you should use Bitlocker with TPM.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 02 2020 03:34 AM
@Deleted
You do have a point - interesting article that . I guess security is not the primary driver. The new 15 XPS offers a lot of horsepower, and decent battery life.
Yes , I think I will be configuring bitlocker with Windows Hello.
- « Previous
-
- 1
- 2
- Next »