- Home
- Security, Compliance, and Identity
- Microsoft Graph Security API
- How to get maximum scores by control Category?
How to get maximum scores by control Category?
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Jan 26 2020
11:59 AM
- last edited on
Dec 23 2021
11:13 AM
by
TechCommunityAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 26 2020
11:59 AM
- last edited on
Dec 23 2021
11:13 AM
by
TechCommunityAP
Hi everyone,
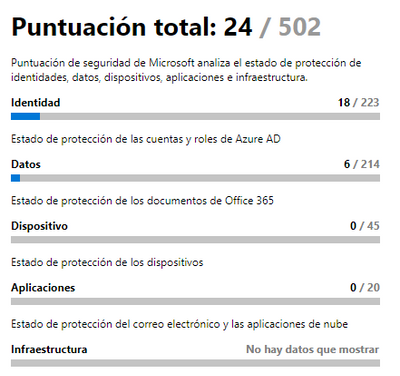
I am starting to use the MS Graph connector from power by and I am trying to reproduce a very simple graph, I can get almost all the data except the maximum score per control category
In the next picture I can obtent 24/502 but for each category I'm able to obtain the score but not the maximum, for example -> identity (18/223) I can obten the score 18 but not the maximum 223
Thanks in advance
Luis
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 01 2020 09:39 AM
SolutionBelow should help to get the aggregated score per control category
The customer should be using:
https://graph.microsoft.com/v1.0/security/secureScores
To get their score
{
"controlCategory": "Data",
"controlName": "Enable mailbox auditing for all users",
"description": "You should enable mailbox auditing for at least ninety percent of all users that have mailboxes in your tenancy. By default all non-owner access is audited, but you must enable auditing on the mailbox for owner access to also be audited. This will allow you to discover illicit access of Exchange Online activity if a user's account has been breached.",
"score": 10,
"total": "69",
"count": "50"
},
And then they can call:
https://graph.microsoft.com/v1.0/security/secureScoreControlProfiles
To get the max scores per control and group by control category an it should give max socre for that category
{
"id": "MailboxAuditingEnabled",
"azureTenantId": "00000001-0001-0001-0001-000000000001",
"actionType": "Config",
"actionUrl": "https://github.com/OfficeDev/O365-InvestigationTooling/blob/master/EnableMailboxAuditing.ps1",
"controlCategory": "Data",
"title": "Enable mailbox auditing for all users",
"deprecated": false,
"implementationCost": "Low",
"lastModifiedDateTime": "2019-12-30T15:36:00Z",
"maxScore": 15,
"rank": 6,
"remediation": "Running the PowerShell script linked below will turn on owner activity mailbox auditing for all mailboxes in your service. By default all non-owner access and administrative actions are recorded, but owner actions are not. Enabling mailbox auditing will include owner activity in the audit records, which will in turn enable you to investigate and scope a compromise of that user's account.",
"remediationImpact": "This change will have no effect on your users.",
"service": "EXO",
"threats": [
"Account Breach"
],
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 06 2020 01:17 PM
Thank you very much Nayna Sheth
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 01 2020 09:39 AM
SolutionBelow should help to get the aggregated score per control category
The customer should be using:
https://graph.microsoft.com/v1.0/security/secureScores
To get their score
{
"controlCategory": "Data",
"controlName": "Enable mailbox auditing for all users",
"description": "You should enable mailbox auditing for at least ninety percent of all users that have mailboxes in your tenancy. By default all non-owner access is audited, but you must enable auditing on the mailbox for owner access to also be audited. This will allow you to discover illicit access of Exchange Online activity if a user's account has been breached.",
"score": 10,
"total": "69",
"count": "50"
},
And then they can call:
https://graph.microsoft.com/v1.0/security/secureScoreControlProfiles
To get the max scores per control and group by control category an it should give max socre for that category
{
"id": "MailboxAuditingEnabled",
"azureTenantId": "00000001-0001-0001-0001-000000000001",
"actionType": "Config",
"actionUrl": "https://github.com/OfficeDev/O365-InvestigationTooling/blob/master/EnableMailboxAuditing.ps1",
"controlCategory": "Data",
"title": "Enable mailbox auditing for all users",
"deprecated": false,
"implementationCost": "Low",
"lastModifiedDateTime": "2019-12-30T15:36:00Z",
"maxScore": 15,
"rank": 6,
"remediation": "Running the PowerShell script linked below will turn on owner activity mailbox auditing for all mailboxes in your service. By default all non-owner access and administrative actions are recorded, but owner actions are not. Enabling mailbox auditing will include owner activity in the audit records, which will in turn enable you to investigate and scope a compromise of that user's account.",
"remediationImpact": "This change will have no effect on your users.",
"service": "EXO",
"threats": [
"Account Breach"
],