- Home
- Windows
- Universal Print
- Setting printer capabilities and defaults
Setting printer capabilities and defaults
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 25 2021 12:28 PM
Registering a printer with an API call of either
https://graph.microsoft.com/beta/print/printers/create using scope "Printer.Create"
or
https://register.print.microsoft.com/api/v1.0/register using scope "https://print.print.microsoft.com/.default"
works fine.
But setting the capabilities and defaults for the newly created printer does not work with the Microsoft Graph API. And I cannot find any other API docs saying anything about updating capabilities and defaults.
When using the dotnet beta client:
var app = ConfidentialClientApplicationBuilder
.Create("<clientid>")
.WithClientSecret("<secret>")
.WithAuthority(AzureCloudInstance.AzurePublic, "organizations")
.WithRedirectUri("https://localhost:44372/return").Build();
//...
// create printer and wait for completion
//...
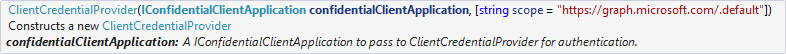
await new GraphServiceClient(new ClientCredentialProvider(app)).Print.Printers["<printerId>"].Request().UpdateAsync(printer);The default constructor uses the scope that is required according to the Universal Print docs.
The update call throws an exception, that
"The token does not have one or more required security scopes."
Also, if I pass a specific application permission e.g. "Printer.ReadWrite.All"
await new GraphServiceClient(new ClientCredentialProvider(app, "Printer.ReadWrite.All")).Print.Printers["<printerId>"].Request().UpdateAsync(printer);the exception now is:
"AADSTS70011: The provided request must include a 'scope' input parameter. The provided value for the input parameter 'scope' is not valid. The scope Printer.ReadWrite.All is not valid."
To make sure there is no issue on missing API rights I added all existing Universal Print rights in Azure.
Admin consent has been given also.
Have no ideas anymore. Can anyone help?
Would be nice to have the ability to set capabilities and defaults with the printer registration process instead of having to make a separate "update" call or similar.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 27 2021 12:32 PM
So after getting some help on github , the following does the trick
.WithAuthority(AzureCloudInstance.AzurePublic, "{tenantIdOfClientApplication}")
Using
"organizations"as tenant id does not work.