- Home
- Microsoft Teams
- Teams Developer
- Authenticating with an access token Connect-MicrosoftTeams
Authenticating with an access token Connect-MicrosoftTeams
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 24 2021 04:38 PM
New-CsOnlineSession has been dropped and the SfB Connector is end of life in July and Connect-MicrosoftTeams does appear to support token for the telephony functions.
- Labels:
-
Administrator
-
Calling
-
Microsoft Teams
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 28 2021 12:28 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 21 2021 06:58 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 23 2021 08:16 AM - edited Jul 23 2021 08:18 AM
I'm trying to setup something similar in Softerra Adaxes, but I'm not getting very far
$clientId = ""
$clientSecret = ""
$tenantName = "tenant.onmicrosoft.com"
$tenantNameshort = ""
$tenantIdCode = ""
$graphResource = "https://graph.microsoft.com/"
$graphtokenBody = @{
Grant_Type = "client_credentials"
Scope = "https://graph.microsoft.com/.default"
Client_Id = $clientId
Client_Secret = $clientSecret
}
$graphTokenResponse = Invoke-RestMethod -Uri "https://login.microsoftonline.com/$tenantName/oauth2/v2.0/token" -Method POST -Body $graphtokenBody
$teamsResource = "https://api.interfaces.records.teams.microsoft.com"
$teamstokenBody = @{
Grant_Type = "client_credentials"
Scope = "48ac35b8-9aa8-4d74-927d-1f4a14a0b239/.default"
Client_Id = $clientId
Client_Secret = $clientSecret
}
$TeamsTokenResponse = Invoke-RestMethod -Uri "https://login.microsoftonline.com/$tenantName/oauth2/v2.0/token" -Method POST -Body $teamstokenBody
Connect-MicrosoftTeams -TenantId $tenantId -AccessTokens @($graphTokenResponse.access_token,$TeamsTokenResponse.access_token)
I get this error:
Connect-MicrosoftTeams : Not supported tenant type.
At C:\scripts\connect-teams.ps1:27 char:1
+ Connect-MicrosoftTeams -TenantId $tenantId -AccessTokens @($graphToke ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : AuthenticationError: (:) [Connect-MicrosoftTeams], ArgumentException
+ FullyQualifiedErrorId : Connect-MicrosoftTeams,Microsoft.TeamsCmdlets.Powershell.Connect.ConnectMicrosoftTeams
If I try something along the lines of
Connect-MicrosoftTeams -TenantId $tenantId -ClientId $clientId -Certificatethumbprint $certificateThumbprint
I get the following:
Connecting to remote server api.interfaces.records.teams.microsoft.com failed with the following error message : The WinRM client cannot process the request....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 17 2021 03:48 AM
https://docs.microsoft.com/en-us/powershell/module/teams/connect-microsoftteams?view=teams-ps
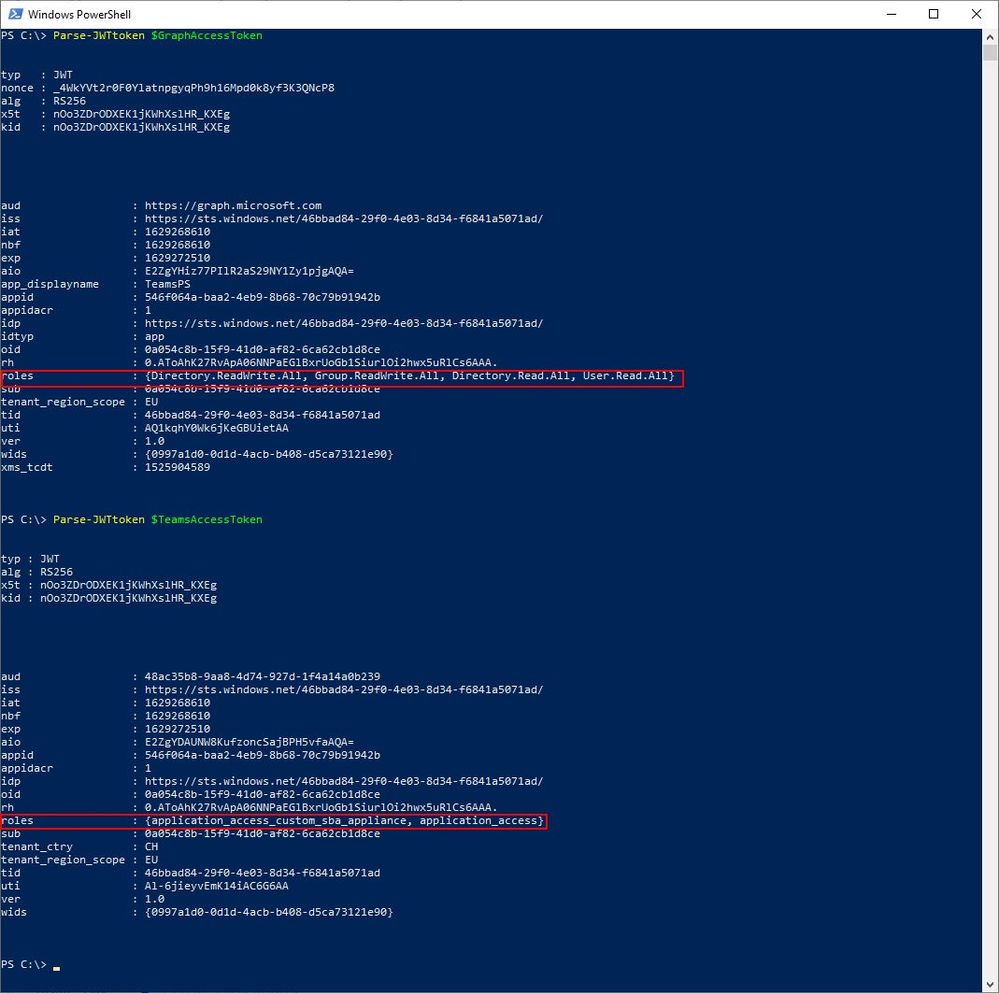
$graphtoken = #Get MSGraph Token for following for resource "https://graph.microsoft.com" and scopes "AppCatalog.ReadWrite.All", "Group.ReadWrite.All", "User.Read.All";
$teamstoken = #Get Teams resource token for resource id "48ac35b8-9aa8-4d74-927d-1f4a14a0b239" and scope "user_impersonation";
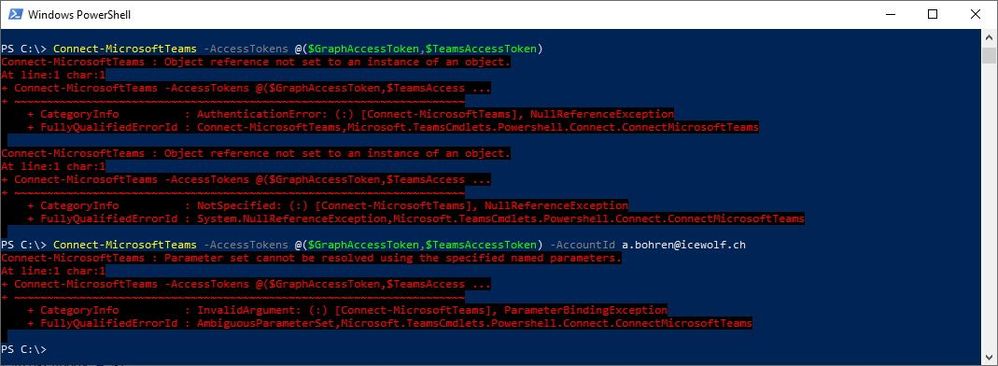
Connect-MicrosoftTeams -AccessTokens @($graphtoken, $teamstoken) -AccountId $adminaccount
Account Environment Tenant TenantId
------- ----------- ------------------------------------ ------------------------------------
user@contoso.com AzureCloud xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
Specifies a access tokens for "MSGraph" and "Skype and Teams Tenant Admin API" resources. This new parameter is added in version 2.3.2-preview.
Following steps must be performed by Tenant Admin in the Azure portal when using your own application.
Steps to configure the AAD application.
Go to Azure portal and go to App Registrations.
Create or select the existing application.
Add the following permission to this Application.
Click API permissions.
Click Add a permission.
Click on the Microsoft MS Graph, and then select Delegated Permission.
Add the following permissions: "AppCatalog.ReadWrite.All", "Group.ReadWrite.All", "User.Read.All";
Next, we need to add "Skype and Teams Tenant Admin API" resource permission. Click Add a permission.
Navigate to "APIs my organization uses"
Search for "Skype and Teams Tenant Admin API".
Add all the listed permissions.
Grant admin consent to both MS Graph and "Skype and Teams Tenant Admin API" name.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2021 03:25 PM
Connect-MicrosoftTeams -AccessTokens @($graphtoken, $teamstoken) -Verbose -AccountId "user@domain.com"
to at least access the new cmdlets, but now I get
Parameter set cannot be resolved using the specified named parameters. One or more parameters issued cannot be used together or an insufficient number of parameters were provided.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 26 2021 12:33 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 26 2021 12:39 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 26 2021 07:38 AM
Using Teams 2.5.0
Does not work here. I've created a GitHub Issue to clarify the Permissions needed https://github.com/MicrosoftDocs/office-docs-powershell/issues/8194
Regards
Andres
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 26 2021 09:30 AM
@MattLadewigWhen I do this I now get "Object reference not set to an instance of an object." on the Connect-MicrosoftTeams line.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 27 2021 12:56 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 01 2021 02:26 PM
There was a new version released today for MicrosoftTeams, but I still unsuccessful.
I have provided the App the relevant permissions as outlined in the documentation.
Connect-MicrosoftTeams -AccessTokens @($tokenResponse, $teams_tokenResponse) -AccountId $UPN
Connect-MicrosoftTeams : Parameter set cannot be resolved using the specified named parameters.
At line:1 char:1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 01 2021 03:05 PM
Install-Module -Name MicrosoftTeams -RequiredVersion "2.3.2-preview" -AllowPrerelease -force
Import-Module MicrosoftTeams -RequiredVersion 2.3.2
$ApplicationId = 'xx'
$ApplicationSecret = 'xx'
$TenantID = 'xx'
$UPN = "admin@xx"
$ReqTokenBody = @{
Grant_Type = "client_credentials"
client_Id = $ApplicationId
Client_Secret = $ApplicationSecret
Scope = "https://graph.microsoft.com/.default"
}
$graph_TokenResponse = Invoke-RestMethod -Uri "https://login.microsoftonline.com/$TenantID/oauth2/v2.0/token" -Method POST -Body $ReqTokenBody
$teams_ReqTokenBody = @{
Grant_Type = "client_credentials"
client_Id = $ApplicationId
Client_Secret = $ApplicationSecret
Scope = "48ac35b8-9aa8-4d74-927d-1f4a14a0b239/.default"
}
$teams_TokenResponse = Invoke-RestMethod -Uri "https://login.microsoftonline.com/$TenantID/oauth2/v2.0/token" -Method POST -Body $teams_ReqTokenBody
Connect-MicrosoftTeams -AccessTokens @($graph_tokenResponse.access_token,$teams_tokenResponse.access_token) -AccountId $UPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 15 2021 11:47 AM
SolutionIssue description:
Cannot properly run Connect-MicrosoftTeams -AccessTokens
Resolution Steps:
Escalated case with our engineering Team
Issue is known bug and currently being fixed
Expecting a fix to go out by NOV mid
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 26 2021 02:20 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 04 2021 05:56 AM
Hi,
We were successfully using Microsoft Teams powershell using Access Tokens. But today we are faced with strange issue:
We are getting error during authentication: Connect-MicrosoftTeams
The provided tokens must have less than 180 seconds difference in the time range of expiration. System.Management.Automation.RemoteException: The provided tokens must have less than 180 seconds difference in the time range of expiration.
We have checked the access tokens expiry, they do differ by more then 180 seconds. We are using Refresh tokens to generate Access tokens. This is done automatically using .NET code, both access tokens are fetched within few milliseconds, yet the expiry differs. And when we use these tokens we get above error.
Has anyone experienced this?
Regards,
Muhammad Usman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 10 2021 02:49 AM
@usman83 Muhammad, we stating to have this same error just today:
"The provided tokens must have less than 180 seconds difference in the time range of expiration."
I've compared these 2 tokens expiration time and there are almost 7 minutes of difference between them. We ask Microsoft to generate the tokens one right after the other.
If you get a solution, please share it here.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 10 2021 06:24 PM
We are having the same issue, this was working for till 10/11/2021 and it has suddenly stopped working today.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 11 2021 12:07 PM - edited Nov 15 2021 02:33 AM
Hi @Sridevi-MSFT,
I've also started experiencing this issue today. Was working fine before, but now I get the error: " The provided tokens must have less than 180 seconds difference in the time range of expiration."
Using Teams PowerShell Module 2.3.2 with a graph token and a Teams token that are created at the same time, but the expiration time can be as great as 20min.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 14 2021 01:52 PM
@Sridevi-MSFT Any update on the error with 180 seconds difference in token expiration?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 15 2021 01:51 AM
I am Using Teams PowerShell Module 2.6.1
But i am Still not able to Connect with the Access Tokens.
Any Updates?