- Home
- Windows Server
- Storage at Microsoft
- Windows Server 2022 is full of new file services!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Heya folks, Ned here again. As you’ve heard by now, Windows Server 2022 is available and supported for production deployments. This new OS brings many new features around security, storage, networking, web, containers, applications, virtualization, edge, and Azure hybrid.
Today I’ll highlight what we’ve introduced for the single most used scenario in organizations: File Services. Our goal with Windows Server 2022 was to make the same generational leap that we did with Windows Server 2012, where we first introduced SMB 3.0 and its security, scale, and performance options. With Windows Server 2022, we focused on today's world of hybrid cloud computing, mobile and telecommuter edge users, and increasingly congested and untrusted networks. We ended up with a large new catalog of options for your organization to stay productive.
Mount up!
SMB Compression
Windows Server 2022 introduces SMB compression, which shrinks files as they transfer over the network. Compressed files use less bandwidth and take less time to transfer, at the cost of slightly increased CPU usage during transfers. For files with compressible space, the savings can be huge – watch my demo below of copying VHD files!
Narrated demo of SMB compression on Youtube
You configure this feature with Windows Admin Center or PowerShell, and you can set compression on SMB shares, client mapped drives, clients, servers, or even on individual file copies using robocopy. SMB compression is most effective on networks with less bandwidth, such as a client's 1Gbps ethernet or Wi-Fi network. It supports your favorite SMB options like SMB signing, encryption, and multichannel. Windows 11 and Windows Server 2022 both have this new capability.
This is a game changing feature in a world where files and are bigger than ever on networks that are fuller than ever.
SMB Security
We added a raft of new SMB security features in Windows Server 2022 for use with client-server scenarios as well as failover clustering and high speed RDMA networking. Security is ever evolving and besides the new options below, we have additional security features coming retroactively to Windows 11 and Windows Server 2022.
Windows Admin Center and the SMB settings for encryption and signing
AES-256
SMB encryption protects your data from being read off the network. Windows Server 2022 now supports AES-256-GCM and AES-256-CCM, in addition to the primary AES-128 encryption used today. This isn’t some implication that AES security is flawed – there are no practical attacks that would allow someone without a key to decrypt AES-128 and none reasonably forecast, despite what the quantum computing marketing folks would have you believe – it’s to ensure that we met mandates like FIPS 197, NSA Suite B Cryptography, and others required by top secret networks. In fact, we still use AES-128 by default for performance reasons and let you opt into 256 bits with group policy and management tools. Windows 11 and Windows Server 2022 have this new capability.
Accelerated signing
SMB signing prevents tampering with data on the network, as well as relay, interception, and spoofing attacks. With Windows Server 2022, we added AES-GMAC acceleration to signing, meaning improved AES-NI hardware offloading provided by CPUs. When two AES-128-GMAC machines are signing SMB and running at least Nehalem processors – i.e., newer than 12 years old – you’ll see the latency of signed SMB really drop and transfer speeds improve, especially on busy processors. For more info on signing, check out Configure SMB Signing with Confidence. Windows 11 and Windows Server 2022 have this new capability.
SMB Direct and RDMA encryption
SMB Direct and RDMA supply high bandwidth, low latency networking fabric for workloads like Storage Spaces Direct, Storage Replica, Hyper-V, Scale-out File Server, and MS SQL server. Windows Server 2022 SMB Direct now supports encryption. Previously, enabling SMB encryption disabled direct data placement; this was intentional, but seriously impacted performance. Now we encrypt data before placement, leading to far less performance degradation while adding AES-128 and AES-256 protected packet privacy. Windows 11 Enterprise, Education, and Pro Workstation, as well as Windows Server 2022, have this new capability.
Failover Cluster East-West security control
Windows Server failover clusters use intra-node communications instances for cluster shared volumes (CSV) and the storage bus layer (SBL). Windows Server 2022 now allows granular control of encrypting intra-node storage communications for those networks beyond the “default” instance of SMB Server. This means that when using clusters and RDMA networks, you can decide to encrypt or sign east-west communications within the cluster itself for higher security, but not necessarily for north-south communications like file copies or Hyper-V Live Migration – and the reverse as well. You can control this with PowerShell currently, there’s more info at Security Settings for Failover Clustering. Windows Server 2022 failover clusters have this new capability.
Storage Migration Service
The Storage Migration Service migrates servers, their storage, and their SMB config from old Windows and Linux to modern Windows Servers and clusters running on-prem or in Azure. You can now also migrate from NetApp FAS arrays running NetApp ONTAP 9 or later. The process is almost identical to migrating from an old Windows Server 2008 or 2012 machine, except that now you point to a NetApp FAS and pick from its running CIFS SVMs, and you can migrate the data into folders on one or more volumes as NetApp storage doesn’t have drive letters.
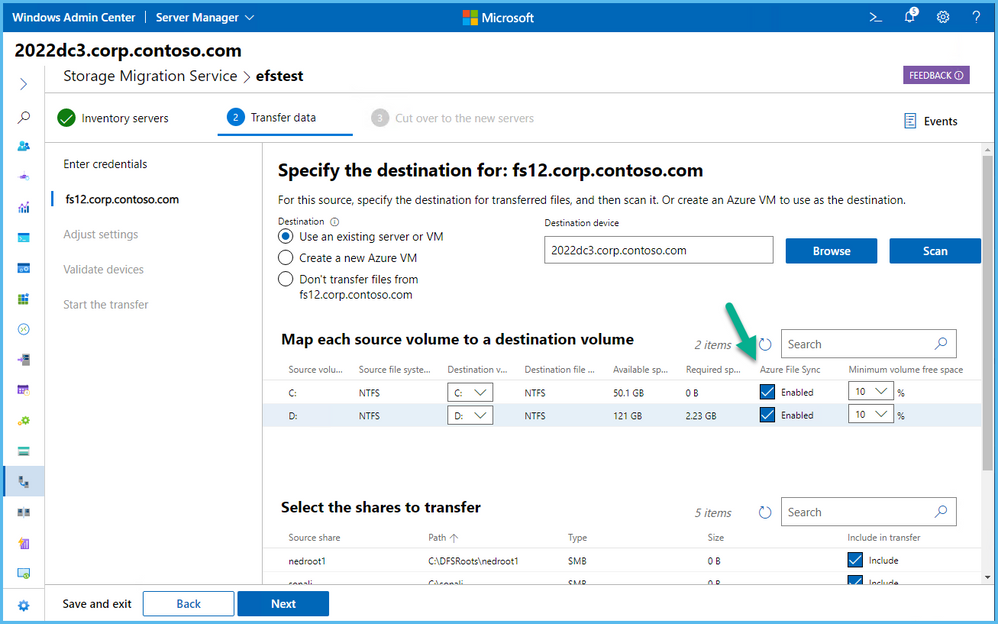
Furthermore, SMS now integrates with Azure File Sync cloud tiering! AFS cloud tiering allows you to use less storage in your Windows File Server and tier your data into Azure for backups and added ransomware protection.
Windows Admin Center and the Storage Migration Service enabling AFS sync on each volume
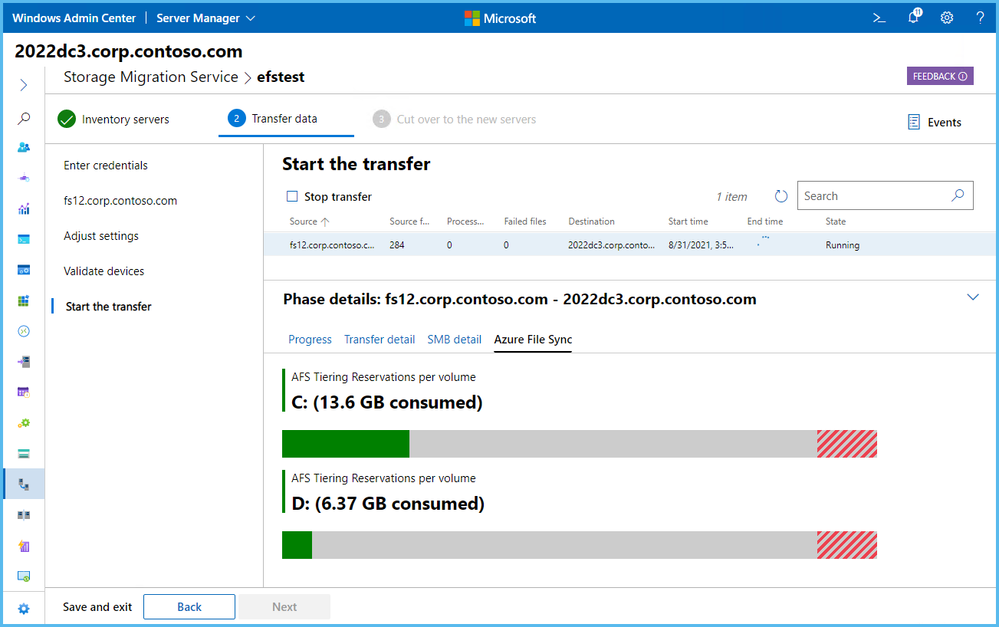
Applications must be aware of AFS cloud tiering, though; when they copy a large data set and AFS says “hey, this volume is full – please wait for me to dehydrate these old files into Azure,” the app has to pause IO. SMS understands this and you can configure AFS cloud tiering on your destination so that the migration and AFS happen simultaneously. For more info on AFS cloud tiering, see Understand Azure File Sync cloud tiering.
Windows Admin Center and the Storage Migration Service about to begin a transfer with AFS enabled
For steps on SMS, see Use Storage Migration Service to migrate a server. Windows Server 2022 and Windows Server 2019 with an update both have this new capability.
Storage and Networking
While not specific to File Services, the Networking, Hyper-V, and local storage teams have been busy adding more performance options for SMB and file servers to gain on Windows Server 2022. You’ll be configuring the new standalone storage bus cache feature based on your drive configuration; the networking features are on by default and just work!
TCP & UDP Networking
Windows Server 2022 implements TCP HyStart++ to reduce packet loss during connection start up - especially helpful in high-speed networks - and RACK to reduce Retransmit Time Outs (RTO). These features are enabled in the transport stack by default and provide a smoother network data flow with better performance at high speeds. Windows 11 and Windows Server 2022 both have this new capability.
Furthermore, UDP is becoming a more popular protocol carrying more networking traffic. In Windows Server 2022 we added the game changing UDP Segmentation Offload (USO). USO moves much of the work needed to send UDP packets from the CPU to the NIC's specialized hardware. We also added UDP Receive Side Coalescing (UDP RSC) which coalesces packets and reduces CPU usage for UDP processing. “But” you exclaim, “SMB uses TCP and RDMA, what does this matter?” Read on, noble IT Pro, to see why this is important. Windows 11 and Windows Server 2022 both have this new capability.
vSwitch networking
The odds that your file servers are virtualized are extremely high and Windows Server 2022 improves the Hyper-V vSwitch with updated Receive Segment Coalescing (RSC). This allows the hypervisor network to coalesce packets and process as one larger segment. This reduces CPU cycles and segments will remain coalesced across the entire data path until processed by the intended application. This means improved performance in both network traffic from an external host, received by a virtual NIC, as well as from a virtual NIC to another virtual NIC on the same host. Windows Server 2022 has this new capability.
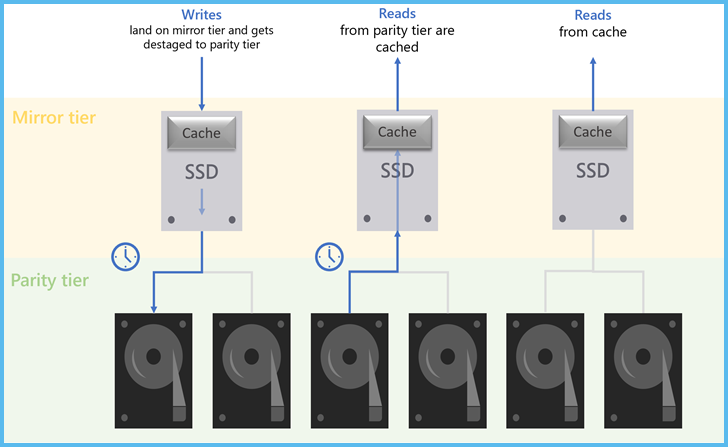
Storage bus cache
Windows failover clusters with Storage Spaces Direct have supported a caching feature for many years and now the option is available for standalone servers using Storage Spaces as the storage bus cache. Storage bus cache can significantly improve read and write performance by tiering smaller fast flash drives above slower but higher capacity drives.
A diagram of SSD and HDD drives arranged into mirror cache tiers and parity capacity tiers
SBC can work both as a read cache and a read-write cache, depending on your hardware. It adds performance to a file server without breaking the bank. Windows Server 2022 has this new capability.
SMB over QUIC (preview)
Finally, we come to the next generation of hybrid file services: SMB over QUIC. SMB over QUIC (preview) provides secure and reliable connectivity to edge file servers over untrusted networks like the Internet, and brings an "SMB VPN" to telecommuters, mobile device users, and high security organizations. QUIC is an IETF-standardized protocol with many benefits over TCP, including:
- All applications using QUIC travel over UDP and, by default, the firewall-friendly port 443
- TLS 1.3 ensures encryption of all packets and a certificate provides non-repudiation
- Parallel streams of reliable and unreliable application data
- Improved congestion control and loss recovery
All SMB traffic, including authentication and authorization, occurs within the tunnel and is never exposed to the underlying network. SMB over QUIC supports Kerberos but even if you decide to use NTLMv2, no challenge or response is exposed to the network.
Here's a demonstration of deploying SMB over QUIC and the user experience:
Narrated demo of SMB over QUIC on Youtube
SMB behaves normally within the QUIC tunnel; as you saw in the demo, the user experience doesn't change. SMB features like multichannel, signing, compression, continuous availability, and directory leasing work normally. Windows 11 and Automanage for Windows Server Services (with Windows Server 2022 Datacenter: Azure Edition Preview) both have this new capability, and it is coming to Azure Files and Android Phones later.
This is another game changer feature.
Summary
Woo that’s a bunch of new stuff to learn. If you’re looking to get your feet wet, I recommend SMB compression as the quickest place to start, then dig into SMB over QUIC. For more important info on Windows Server 2022 in general:
- Get Started - https://docs.microsoft.com/windows-server/get-started/get-started-with-windows-server
- What's New - https://docs.microsoft.com/windows-server/get-started/whats-new-in-windows-server-2022
- Editions Comparisons - https://docs.microsoft.com/windows-server/get-started/editions-comparison-windows-server-2022
- Hardware requirements - https://docs.microsoft.com/windows-server/get-started/hardware-requirements
- Removed Features - https://docs.microsoft.com/windows-server/get-started/removed-deprecated-features-windows-server-202...
- Windows 11 Insider Preview - Home | Windows Insider Blog
Don’t forget to add Microsoft Ignite to your calendar for November – there will be tons of Windows Server info. And really don’t forget to register for the free Windows Server Summit on September 16, 2021. I have a presentation with Rick Claus that features great info, discussion, demos, and a special guest! Who could it be?
Author's very embarrassed dogs wearing Halloween costumes of a viking and cowboy-riding horse
Until then,
- Ned “So Much Beauty” Pyle
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.