- Home
- Content Management
- Discussions
- Re: Look Book Provisioning NOT restricted to tenant admins. HUGE PROBLEM. HELP!
Look Book Provisioning NOT restricted to tenant admins. HUGE PROBLEM. HELP!
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 11 2021 06:54 AM
I don't know if this is the right forum for this but I have just learned that, while the LookBook website indicates that only tenant admins are to be able to create sites using the templates, an E3 licensed user with no admin roles just created his own Comm site without any issue or assistance and I, as the SharePoint and TEAMS administrator had no idea he did so.
Our company has strict rules about who can create along with naming conventions, etc. to follow when creating and he was able to bypass ALL of it. I'm not faulting the user, I am faulting Microsoft's verbiage and/or security. Either the website is erroneous when it says only admins can create/use the templated or there is a security/management breach going on for this.
I am VERY concerned at what this means for our company: it will be Pandora's Box is a blink of an eye.
Please, would someone please explain what is going on and how I can stop this from being something anyone in my tenant can do? QUICK!
- Labels:
-
Admin
-
Developer
-
Look Book
-
Permissions
-
Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 11 2021 09:56 AM
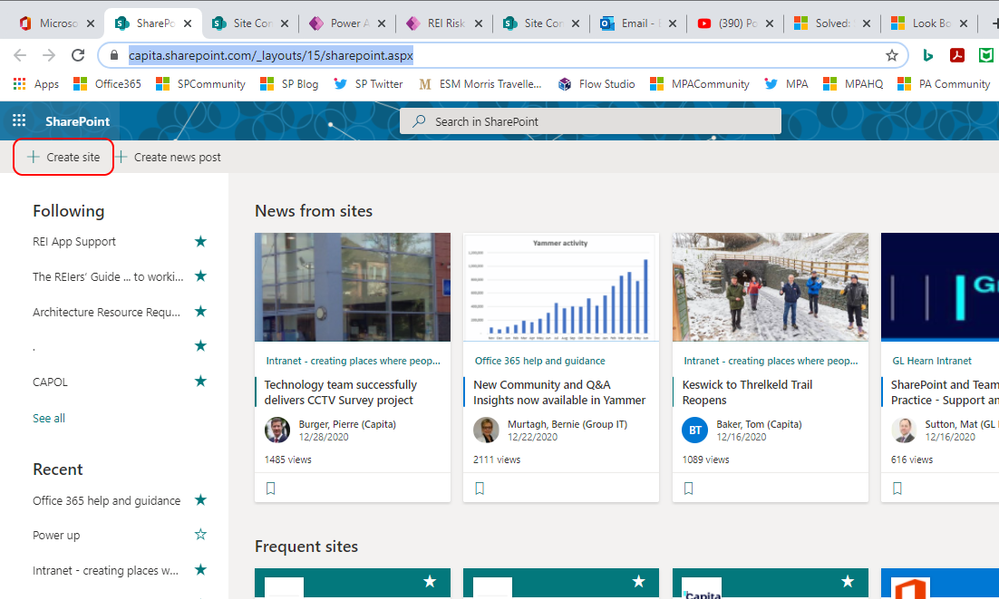
@Lisa Stebbins you are correct that sites created with the Look Book templates need tenant admin permissions(apart from those few education ones that don't). But a standard communications site with the basic sections and web parts can be built by any user, either from the far top left of the SharePoint homepage at https://capita.sharepoint.com/_layouts/15/sharepoint.aspx
or by going to the following link: https://capita.sharepoint.com/_layouts/15/CreateGroup.aspx
Rob
Los Gallardos
Microsoft Power Automate Community Super User
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 11 2021 10:51 AM
This setting that we've chosen, along with Microsoft's statement that only 'tenant admins' can create via the Look Book should stop everyone from being able to create anything except for the select few. It stops everything except the Look Book. I need the Look Book to only be created by a tenant admin, as it states.
I need a fix asap!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 16 2021 01:35 AM
Hi Lisa,
I am not sure if this can solve your issue or opens up even worse issues.
I meant to just publish my own questions on the Lookbook when I saw your post
and i am not yet 100% on top of the topic.
I think you can prohibit your users provisioning apps through the lookbook, by not allowing them to register apps in Azure AD - user settings - Users can register application set to No
To provision a site with the lookbook you need to an app called SharePoint.PnP.ProvisioningApp.
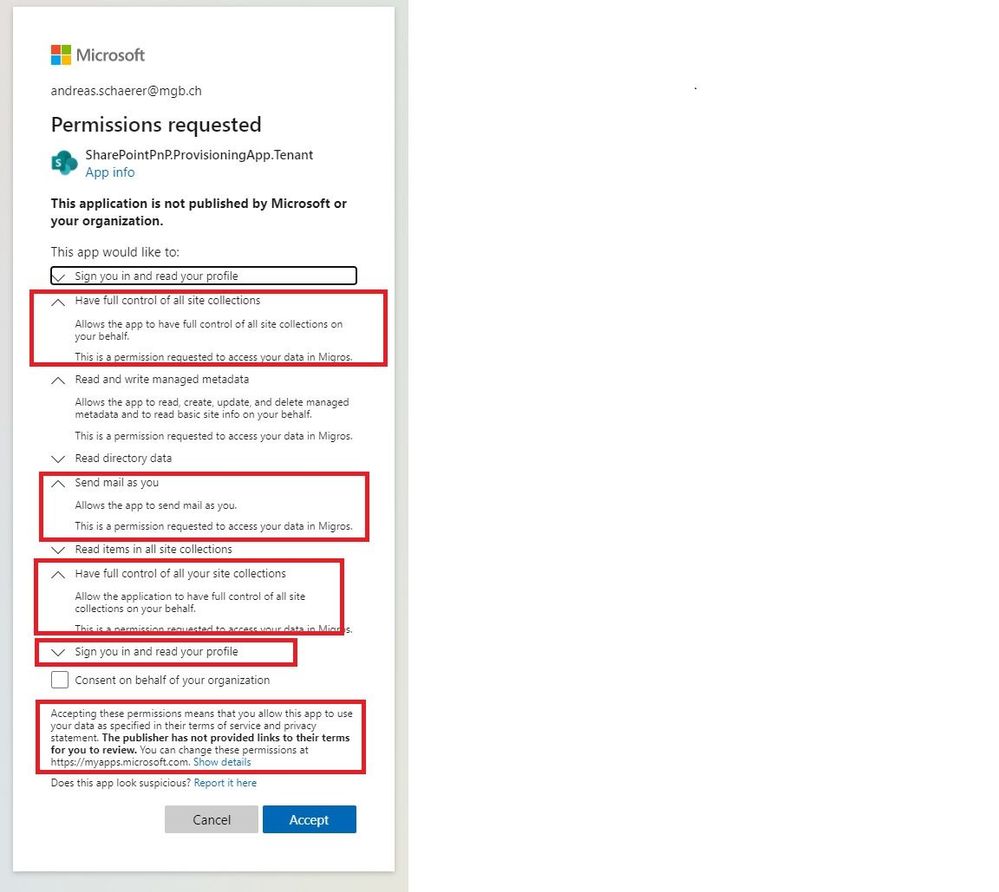
When the first user tried to provision a site from the Lookbook, this App is given permissions in your tennant. Often this is done by a Global Admin, since only he has the role to register this App with the Azure AD. He will get a permission request as shown in the attached picture.
I think if he checks the check box in the bottom, this is now available for all your users.
Also this would allow your users further provision web sites with the lookbook.
the Global Admin should manuall give some SPO Admins these permissions in Azure AD - Enterprise Applications. Here you should find the SharePoint.PnP App.
What really bothers me is the amount of rights, this App requests:
- Have full control of all site collections
- Send mail as you.
- Sign you in and read you profile
- ....
And i cannot even be sure if this App is from Microsoft. This is not signed. The T&Cs are empty....
So currently we only use the Lookbook in our Test Tenant but not in production.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 16 2021 06:26 AM
SolutionHere's what worked for me, thanks to Beau Cameron in another post:
Sounds like when you or another tenant admin used the Lookbook previously, you consented the application "on behalf of the organization". What this means is essentially a Tenant Admin has approved this application for use and the permissions required by this application. I have attached the image of the check box you checked.
I do not think you meant to click this checkbox. When you provision using a tenant admin account, you do not need to select this box. As a result, the other users in your environment can now provision through the lookbook because you provided the consent.
What you will need to do is....
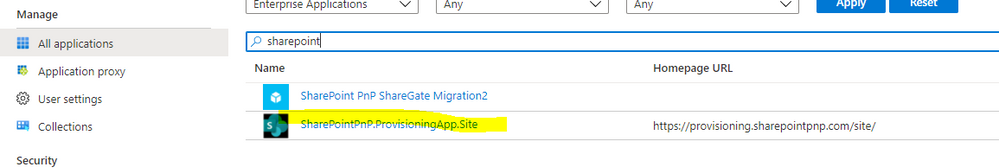
1. Go to the Azure Portal to your Azure Active Directory settings
2. Go to Enterprise Applications
3. Locate SharePointPnP.ProvisioningApp.Tenant
4. Select Properties on the left
5. Delete this application
The next time you or a tenant admin use the Lookbook, do not consent on-behalf of your organization.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 16 2021 06:26 AM
SolutionHere's what worked for me, thanks to Beau Cameron in another post:
Sounds like when you or another tenant admin used the Lookbook previously, you consented the application "on behalf of the organization". What this means is essentially a Tenant Admin has approved this application for use and the permissions required by this application. I have attached the image of the check box you checked.
I do not think you meant to click this checkbox. When you provision using a tenant admin account, you do not need to select this box. As a result, the other users in your environment can now provision through the lookbook because you provided the consent.
What you will need to do is....
1. Go to the Azure Portal to your Azure Active Directory settings
2. Go to Enterprise Applications
3. Locate SharePointPnP.ProvisioningApp.Tenant
4. Select Properties on the left
5. Delete this application
The next time you or a tenant admin use the Lookbook, do not consent on-behalf of your organization.