- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 20 2016 08:19 AM
I have a project site which I want to share with some external user. External Sharing is enabled in site collection level and the new setting "External users must accept sharing invitations using the same account that the invitations were sent to" is disabled:
Now I share the site with external user with his/hers work email address firstname.lastname@company.com
The external user receives invitation email to his/hers work email address and clicks the link. He/she uses (personal) Microsoft Account firstname.lastname@outlook.com to login the site and gives the username and password.
Then the external user is getting error "User is not found in the directory"
This article describes the issue but is somehow misleading when it says "if the user who accepts the invitation signs up by using an account other than the email address to which the invitation was sent, you may encounter an access denied message."
Does that mean that the external user has to use MS account, which has the same email address as where the invitation was sent to, to login? This all is a source of big confusion and in large customer projects it adds high management overhead to us and for our clients/customer. Microsoft, make it more simple!
- Labels:
-
SharePoint Online
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 25 2017 11:29 AM
@Reuben, you can enable the flow you're describing by using anonymous access links when you need to share externally. Any user who clicks on these links can view and edit the file without signing in.
Hope that helps!
Stephen Rice
OneDrive Program Manager II
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 26 2017 03:53 AM
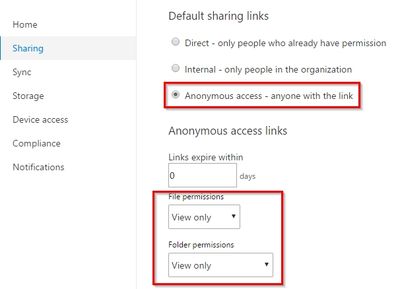
The behavior you are looking for is easily implemented going to the OneDrive Admin Center and configure the defaults for your tenant as in the following screenshot (for example):
Now, when you share an item, the default will be to share it as an anonymous read-only link, which can be used by everyone immediately, without authentication.
The default can be overridden case by case and it will also be possible to set an expiration.
Moreover you will be able to revoke the link in every moment using the details pane in the doc library.
If I have well understood, this is exactly what you are asking.
Hope it helps...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 26 2017 03:54 AM
Thanks @Stephen Rice !
It is always a pleasure to read your ultra-clear explanations!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 26 2017 04:57 AM - edited May 26 2017 05:02 AM
First: Thank you! That is exactly what we are looking for!
Second:
At the risk of sounding dumb.... Does that apply for sharepoint sharing as well? If it is changed in the OneDrive Admin settings will it affect our sharepoint files as well?
I assume it does because you mentioned libraries....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 26 2017 06:08 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 26 2017 07:10 AM
Sorry to disagree this time with @Dean Gross :-), but yes, the setting applies both to ODfB and SharePoint doc libraries, as you can easily verify.
Be aware that, for it to work, anonymous sharing must be enabled both at tenant level and at the single site collection level (which can be done in the UI). For Groups site collections, instead, it can be enabled only by PowerShell (at the moment).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 26 2017 07:27 AM
Thanks for the correction. I was thinking about the external sharing setting for OneDrive can be more restrictive than what's allowed for SharePoint Online, but not less restrictive and I thought that the controls in the OD admin center were only for OD, but in this case the settings changes apply to both types of SP sites.
Here is the official documentation, https://support.office.com/en-us/article/Manage-external-sharing-ee8b91c5-05ec-44c2-9796-78fa27ec842...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 30 2017 06:11 AM
Thanks @Stephen Rice for your excellent answer! Nice to hear that the external sharing experience and functionality is one of your top focuses. Can't wait for the Good Things! I hope that the sharing experience will be consistent when sharing individual files, folders, document libraries or whole sites.
I think in our case the MSA user account was configured as an EASI ID and that is why it was giving error. In one of the cases the user had Office 365 in use in their org but didn't realize it and created MSA user account by using the work email as an user name. I think this is not possible anymore which is good, but still there are a lot of early adopter users who have 2 identities (MSA and work account) with the same user name (email address).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 30 2017 09:44 AM
Hi @Teemu Strand,
Glad you were able to identify the root cause! We've been working with the AAD team on a few incidents related to the EASI ID MSA/AAD snafu so I'll be sure to pass this feedback along to the right folks. Let me know if you have any questions!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 08 2018 09:06 AM
I am an external user and need to access the tenant site without using the link in the invitation and generating a code each time.
I used the link in the invitation, then used the generated code to access the tenant's site. I am able to see and use everything I should.
I am unable to sign in to the tenant site without using the link in the invitation email.
My microsoft account signed in with a different email than the email the invitation was sent to. I have cancelled the microsoft account with the different email. I now have a microsoft account using the email that the invitation was sent to.
I need to be able to sign in to the tenant site without using the link in the invitation email.
Thank you!
- « Previous
-
- 1
- 2
- Next »