- Home
- Content Management
- Discussions
- Re: Access has been blocked by Conditional Access policies.
Access has been blocked by Conditional Access policies.
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 17 2022 10:58 PM - last edited on Nov 09 2023 11:08 AM by
Hello,
I have added an new user outside our organisation. When he tries to login he gets this screen:
If I look in the admin portal I see this:
Access has been blocked by Conditional Access policies. The access policy does not allow token issuance.
Anyone who can help me whats wrong? thanks in advance!
- Labels:
-
SharePoint Online
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 18 2022 03:00 AM
https://aad.portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/SignIns
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 19 2022 04:38 AM
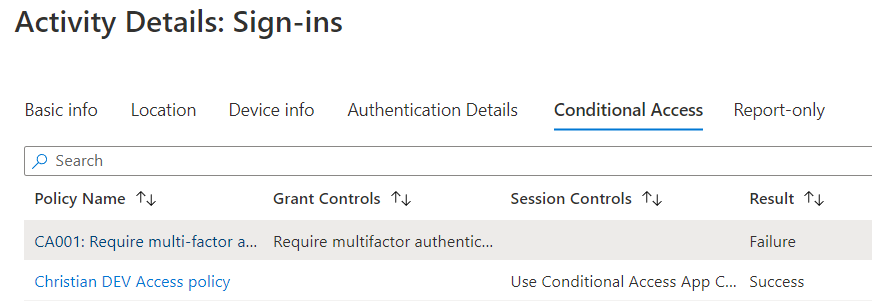
thanks for yuor reply. I did that, but does not give me any more info on what is wrong, see snapshot.
Any idea?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 19 2022 07:21 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 19 2022 07:33 AM
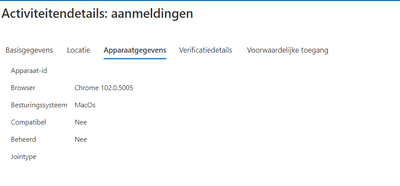
It does not give me any more info. I doe see the user uses a Mac. This might me an issue ?
Gr Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 19 2022 07:52 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 20 2022 11:56 AM
So I tried to log in on another Macbook. Worked fine.
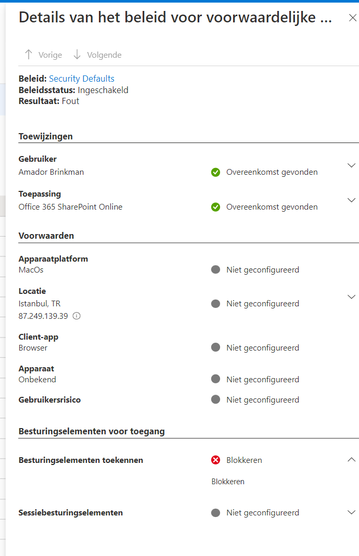
I searched the Azure detals and found that this keeps happening:
The "control elements" keep getting blocked.
Still not sure what this means
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 23 2022 02:30 AM
@Robertls6 Did this every get resolved as I have the same scenario / issue with security defaults.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 23 2022 02:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 23 2022 03:17 AM - edited Nov 23 2022 03:33 AM
This is what happens when security defaults are enabled.
Requiring all users to register for Azure AD Multi-Factor Authentication.
Requiring administrators to do multifactor authentication.
Requiring users to do multifactor authentication when necessary.
Blocking legacy authentication protocols.
Protecting privileged activities like access to the Azure portal.
My guess here is the legacy protocols.
In general, when using conditional access policies, they should be analyzed before turning them on, such as "report-only" mode to see what will happen. Let's say you have apps that doesn't support modern authentication, or your environment is enabled for modern authentication, if you then disable all legacy protocols... another example could be trying to sign in from a location that isn't specified in the trusted locations in the CA policy and so on.
To be able to configure CA policies though one cannot use Azure AD free (security defaults) as Azure AAD P1 is required.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 23 2022 03:22 AM - edited Nov 23 2022 03:29 AM
@Robertls6 Thanks for coming back to me.
Yes this is my fall back.
However just waiting on user feedback as I found the user on the risky users page as they have been making a mess of the 2FA sign up and I think security defaults now has some rule in there around that type of behaviour.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 23 2022 03:28 AM
see my previous reply I did ended up finding the user on the risky sign-in page though as they had been trying to avoid the auth app requirement. So this is my suspicion although you'd never know this from looking anywhere in the logs, I just went hunting and found the user listed.
I've removed them and waited a short while before asking the user to try again.
Oh yeah P1 / P2 the licence MS does not know what to do with.
I currently have a small essay with my reseller asking them how the heck we are supposed to be licencing these as things keep disappearing behind the you need a P1 licence for that and the licence terms so so unclear as to who needs what.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 23 2022 08:13 AM
Feel free to update the conversation when/if you find the solution.
Adding this for reference https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/block-legacy-authenticat...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 13 2022 08:15 PM
OK I experienced the same issue - turned out the user was trying to login from a VPN and AAD didn't like the IP address.
Hopped off the VPN and everything was fine.