- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Schooling A Sea of Phish Part 2: Enhanced Anti-spoofing technology in Office 365
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
A few weeks ago, we released new enhanced Anti-impersonation capabilities for Office 365 Advanced Threat Protection (ATP). Today we’re excited to announce Office ATP’s enhanced anti-spoofing capability for protecting against spoofed emails from external domains. We believe this new capability will help lead the industry in further securing email. The new feature raises the required level of authentication checks for emails sent into Office 365, helping ensure greater protection for customers. Spoofing occurs when an email message appears to originate from someone or somewhere other than the actual source and is a technique often used in phishing campaigns designed to obtain user credentials. Microsoft’s anti-spoof technology specifically examines forgery in the ‘From: header’. Attackers can spoof the domain of an organization and send a spoofed email back to the organization or spoof an external domain and send emails as that spoofed domain to an organization. Exchange Online Protection (EOP) has been securing Office 365 customers from internal domain spoof for many years. Also, Office 365 admins are given tight control over their organization’s spoof filters from the Office 365 Security & Compliance Center. We recommend that admins further improve their organization's spoof protection by appropriately configuring SPF, DKIM, and DMARC.
The newest anti-spoof features help protect organizations from external domain spoof. Office 365 honors emails from external domains having proper SPF, DMARC, and DKIM authentication settings enabling them to pass authentication, and junks messages that fail this authentication. The challenge occurs when external domains do not have these settings properly configured. For example, studies (ftc report, dmarc.org report) show enforcement of DMARC remains low. Without enforcement of these settings, domains have a greater potential to be maliciously spoofed, exposing customers to phishing or spam attacks. The new external domain anti-spoofing capabilities help detect and block emails from external domains that do not have
- proper authentication configuration
- an email infrastructure source with unknown history
- a source which is anomalous to previous sending patterns from that domain.
Customers will see immediate effect from this enhancement as both email senders and recipients will notice more emails being junked. Admins can whitelist domains that will not meet the tighter authentication requirements from the Office 365 Security and Compliance Center. We also recommend admins of sender domains into Office 365 update SPF, DKIM, DMARC configurations so emails can pass the stricter authentication rules.
Anti-spoofing in Exchange Online Protection
For EOP customers, Office 365 honors emails from external domains which pass explicit authentication through proper SPF, DMARC, and DKIM configurations and enforcement. Since inception, EOP has also leveraged implicit authentication to further protect customers from internal domain spoofing. It is designed to check if a message’s destination is to your organization and if the message comes from any of your provisioned domains, or subdomains of any of your provisioned domains. To pass authentication, EOP checks the published DMARC/DKIM standards as well as the SPF framework, verifying the reputation of the sending domain, the reputation of the sender IP address, and also the recipient reputation (ie. how many messages do you receive from this sender?, how is your email routed through the EOP service?, etc). If EOP determines that an email is spoof, it will mark the email as spam in the email header. Additionally, EOP has provided safety tips in the message which serve as visual indicators letting end users know that a message is fraudulent or may be a phishing scam. Further details on EOP’s anti-spoofing are available here.

Anti-spoofing with Office 365 Advanced Threat Protection
In addition to the standard EOP filter protection, Office 365 ATP customers are now also protected from external domain spoof by default through a newly enhanced filter. For external domains, ATP first checks if the email passes SPF, DKIM, and DMARC. If it does not, ATP will check for historical sending patterns of that domain and associated infrastructure. If it detects anomalies and unknown patterns it will proceed to junk the message if the sender does not have good reputation. The filter constantly evolves and enhances itself based on mail flow patterns it observes. ATP customers can access the spoof intelligence report in their Antispam Policy (figures 2, 3) which provides insights into domains being flagged as spoof mail and allows admins to take necessary actions. As mentioned, determining legitimate or malicious spoof is made complicated because organization’s fail to publish SPF, DMARC,


or DKIM, yet have senders who are authorized to send for that domain. Admins can review internal and external domains being spoofed and sending emails into their organization. It is important to understand that there are scenarios (see figure 4) when email is legitimately spoofed and should be delivered.

Spoof intelligence enables admins to enhance spoof protection by specifying which senders are authorized to spoof their organization's domains and send email on its behalf. The setting also enables designating external domains which are permitted to spoof. Emails from unauthorized senders or domains are treated as spam by Office 365. By effectively managing the spoof intelligence settings, admins can customize and enhance the spoof protection for their organization.
Enhanced Granular Anti-spoofing Policy Controls
With the new anti-spoofing enhancements, admins can now control the strength of the spoof filters, the action taken when an email is flagged as malicious spoof, and the ability to turn safety tips on/off. The spoof filter threshold can be set to ‘default’ or ‘strict’ (figure 5). When set to default, messages passing implicit or explicit authentication will be considered legitimate with regard to spoofing and allowed to enter the remaining email filtering stack marked as ‘normal’ email. If the threshold is set to 'strict', only messages passing explicit authentication are marked ‘normal’. Under the 'strict' setting, when an email passes implicit authentication but with medium or low confidence, it is considered a ‘soft pass’ and will be marked as a spoofed email. Since the ‘strict’ setting is more aggressive it may lead to a small number of false positives.
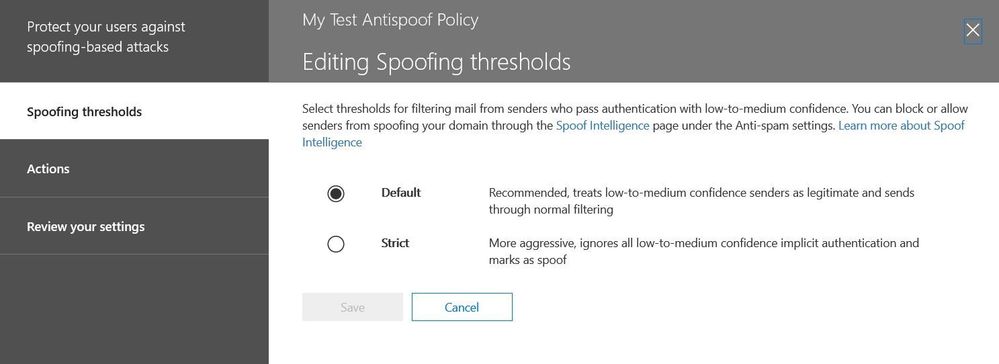
Admins also have more control over actions taken when an email is flagged as a spoof. Emails marked as spoof can either be sent to the recipient’s junk mail folder or the message can be directed to quarantine. The new anti-spoof policy controls also allow for safety tips in emails failing authentication or which pass authentication but with medium or low confidence (soft-pass) as shown in figure 6. It should be noted safety tips for soft-passes should only be enabled for a small group of users as many tips could be generated if a user receives email from legitimate yet unauthenticated sources.

Send Us Your Feedback
For more details on the new Anti-spoof capabilities, read our full article which will help guide your through setting up the new feature. Here are some other helpful articles and videos on Office 365 and Office 365 ATP anti-phish, anti-spam capabilities:
- Anti-phishing protection in Office 365 (article)
- Set up Office 365 ATP anti-phishing policies (article)
- Anti-phishing with Office 365 Advanced Threat Protection (video)
We look forward to your feedback once you experience the new Anti-spoof capabilities for Office 365 Advanced Threat Protection. The feedback helps us continue improving and adding features that will allow Office ATP to be the premiere advanced security service for Office 365. If you have not tried Office 365 ATP for your organization yet, you should begin a free Office 365 E5 trial today and start securing your organization from the modern threat landscape. Look for the final part of this series soon, where we will complete our overview of the enhanced anti-phishing capabilities for Office 365 ATP.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.