- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- MCAS: How to protect AWS Admins and Developers
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
By Richard Diver, Alex Weinert, @Matt Soseman
In this blog, I am going to tell you about a new deployment guide that will help you to apply several advanced security controls for access to AWS environments, using Microsoft Security solutions – this is one of the simplest implementations that can solve a myriad of problems when trying to provision identities and govern access to systems that may be business critical and hold very sensitive information.
Securing Access to AWS Environments
Management of AWS identities can be complex, especially when there are multiple environments to manage. The risk of compromise to administrators and developers is increasing as attackers attempt to gain access to critical resources. There is also a risk of misconfiguration and potential loss of data if the user credentials are not properly monitored for suspicious activity.
Azure AD supports single sign-on integration with AWS SSO. With AWS SSO you can connect Azure AD to AWS in one place and use AWS SSO to centrally govern access across hundreds of accounts and AWS SSO integrated applications, and have a seamless Azure AD sign-in experience to use the AWS CLI. Refer to this Tutorial: Azure Active Directory single sign-on (SSO) integration with Amazon Web Services (AWS) | M... for more details.
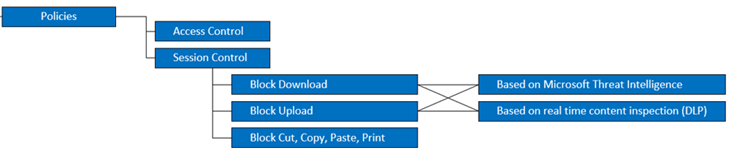
In this blog post for Azure AD (https://aka.ms/AWSIdentity), you can read about the implementation of secure authentication for AWS using Azure AD SSO. When the authentication and single sign-on with Azure AD is setup for AWS, you can implement advanced Conditional Access policies with MCAS to enable Session Control policies: this is the ability to continuously monitor the activities of the AWS user as they interact with resources. The diagram below shows some of the options available today with Microsoft Cloud App Security, when integrated with Azure AD to protect AWS:
For real-time data loss prevention (DLP), MCAS can use both the built-in content inspection or the Data Classification Service (Microsoft Information Protection) integration to block uploads or downloads.
Note: MCAS session controls apply to browser-based sessions. For thick clients, MCAS can only apply access policies (via Conditional Access App Control).
Implementing Advanced Security Controls
Microsoft Cloud App Security is a key component of securing any cloud application. When used to secure AWS, it can also be used to scan the environment and provide recommendations against the CIS Benchmark to ensure the correct configuration and security controls have been implemented. The diagram below explains the layers of security that can be gained by using some of the Microsoft security solutions together:
You can take advantage of this defense in depth approach using integrated solutions you very likely already own! Get the latest version of the deployment guides below and learn more about how to enable this within 30 minutes:
- Implement Azure AD to secure AWS Authentication: https://aka.ms/AWSIdentity
- Implement advanced Microsoft Security solutions for AWS: https://aka.ms/AWSSecurity
You can also read more about how Microsoft Cloud App Security helps to protect your AWS environment here: https://docs.microsoft.com/en-us/cloud-app-security/protect-aws
To learn more about Microsoft Cloud App Security, check out the resources below:
Best Practices: https://docs.microsoft.com/en-us/cloud-app-security/best-practices
MCAS POC: Aka.ms/mcaspoc
MCAS Podcast: Aka.ms/MCASPodcast
MCAS Ninja Training: Aka.ms/MCASNinja
Thank you!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.