- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity
- Re: Is there a way to allow URLs that have been detonated and determined as malicious?
Is there a way to allow URLs that have been detonated and determined as malicious?
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Aug 27 2020
03:56 AM
- last edited on
May 24 2021
02:11 PM
by
TechCommunityAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 27 2020
03:56 AM
- last edited on
May 24 2021
02:11 PM
by
TechCommunityAP
Hi folks,
I'm attempting to run a phishing simulation using a non-Microsoft vendor (i.e. I'm not using the out-of-the-box Threat Simulator) and, during my test campaign, the phishing emails were being delivered to my chosen recipients' junk mail folders.
Is there a way to put URLs on an allow list to prevent M365 from junking my phishing simulation emails? Otherwise, I fear my test will only show that M365 will junk the emails rather than help me provide education to customers and strengthen our email security posture.
I'd be immensely grateful for any feedback you can provide.
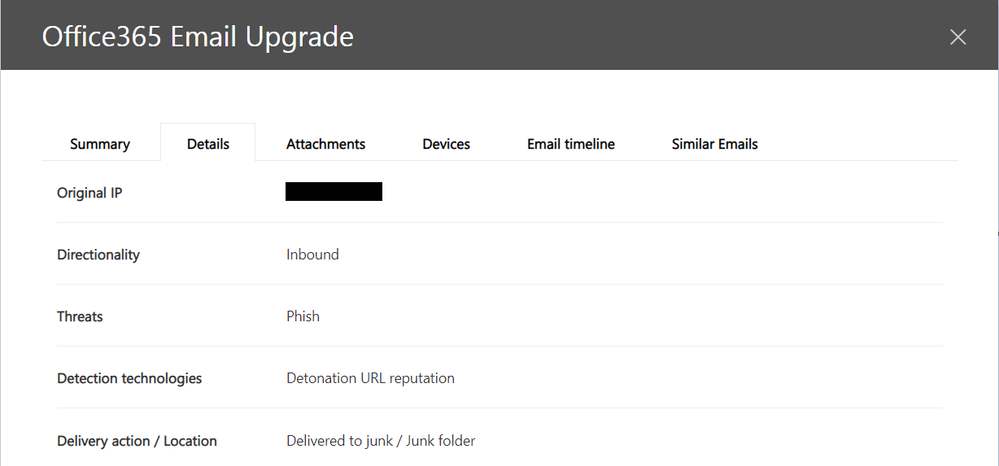
I've attached screenshot from Threat Explorer below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 27 2020 10:37 AM
SolutionYou can configure a whitelist of sorts as detailed here: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/set-up-a-custom-do-not-r...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 28 2020 07:20 AM
We had one of the leaders in on a proof-of-concept a year ago. I had to safelist everything; sending ranges, sending domains, landing zone domains, the lot. One mark of a good tester is that they will not only have this information to hand but also useful KB articles on what you need to do to EOP and ATP to let the tests through. Do your own diligence too, of course.
Once you are done, don't forget to remove these from your config. Some of the testers don't register / retain all of the domains they use, so an enterprising black hat might pick them up guessing that they will appear in safelists.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 28 2020 07:30 AM
Thanks for the advice. I've stumbled across the vendor's guidance documents this afternoon when I was looking for something else, so I have clear instructions so I'm going to wade through that and see if it works.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 27 2020 10:37 AM
SolutionYou can configure a whitelist of sorts as detailed here: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/set-up-a-custom-do-not-r...