- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity
- bulk Pre-registration for Azure MFA for more Seamless Single Sign on and smooth for MFA roll out
bulk Pre-registration for Azure MFA for more Seamless Single Sign on and smooth for MFA roll out
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Feb 29 2020
07:31 AM
- last edited on
May 24 2021
03:19 PM
by
TechCommunityAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 29 2020
07:31 AM
- last edited on
May 24 2021
03:19 PM
by
TechCommunityAP
We’ve been asked many times to do a bulk pre-registration for Azure Active Directory MFA to provide our customers’ users more Seamless Single Sign on and smooth for MFA rolling out.
This script helping you to:
- Configure MFA Strong Authentication Methods
- Set a default MFA authentication method for all users or number of users.
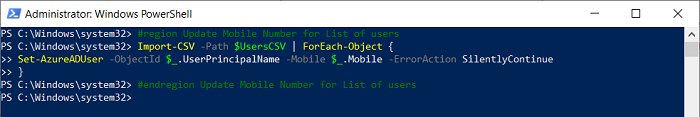
- Update Mobile Number for a List of users.
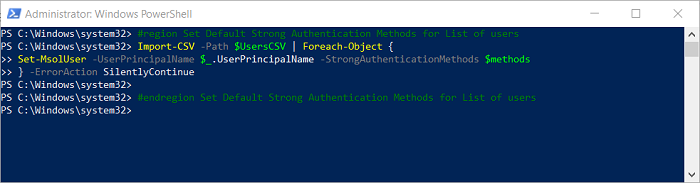
- Update Strong Authentication Methods for List of users
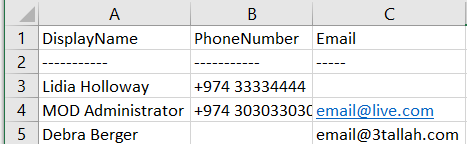
- Get MFA Strong Authentication Details for all users.
- Get MFA Authentication contact info where the phone number is Null
- Update Mobile Number Only If user Mobile is not exist
NOTE : Before we proceed with MFA and SSPR Enablement and configuration, Users will be able to change their Authentication mobile phone number whenever they need to, Admins won’t have a control on Authentication mobile phone number however they can pre-define them but still users will be able to change it.
Keep in mind:
- If you have provided a value for Mobile phone or Alternate email, users can immediately use those values to reset their passwords, even if they haven't registered for the service. In addition, users see those values when they register for the first time, and they can modify them if they want to. After they register successfully, these values are persisted in the Authentication Phone and Authentication Email fields, respectively.
- If the Phonefield is populated and Mobile phone is enabled in the SSPR policy, the user sees that number on the password reset registration page and during the password reset workflow.
- The Alternate phonefield isn't used for password reset.
- If the Emailfield is populated and Email is enabled in the SSPR policy, the user sees that email on the password reset registration page and during the password reset workflow.
- If the Alternate emailfield is populated and Email is enabled in the SSPR policy, the user won't see that email on the password reset registration page, but they see it during the password reset workflow.
Download here.
$UsersCSV = "<Users CSV File Path>" # Example C:\Temp\UsersMFA.csv
$OutPutFolder = "C:\Temp" # Example C:\Temp
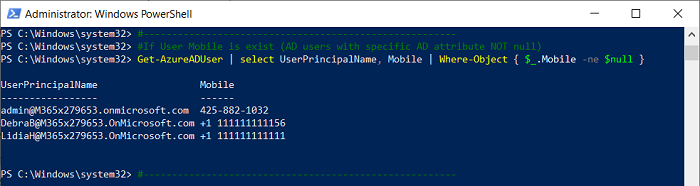
Get-AzureADUser | select UserPrincipalName, Mobile | Where-Object { $_.Mobile -ne $null }
Get-AzureADUser | select UserPrincipalName, Mobile | Where-Object { $_.Mobile -eq $null }
Get-AzureADUser | select DisplayName, UserPrincipalName, otherMails, Mobile, TelephoneNumber | Format-Table
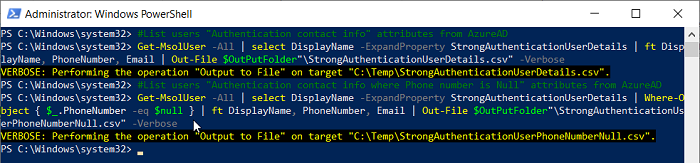
Get-MsolUser -All | select DisplayName -ExpandProperty StrongAuthenticationUserDetails | ft DisplayName, PhoneNumber, Email | Out-File $OutPutFolder"\StrongAuthenticationUserDetails.csv" -Verbose
Get-Msol User -All | select DisplayName -ExpandProperty StrongAuthenticationUserDetails | Where-Object { $_.PhoneNumber -eq $null } | ft DisplayName, PhoneNumber, Email | Out-File $OutPutFolder"\StrongAuthenticationUserPhoneNumberNull.csv" -Verbose
Get-MsolUser -All | select DisplayName, UserPrincipalName -ExpandProperty StrongAuthenticationMethods | select UserPrincipalName, IsDefault, MethodType
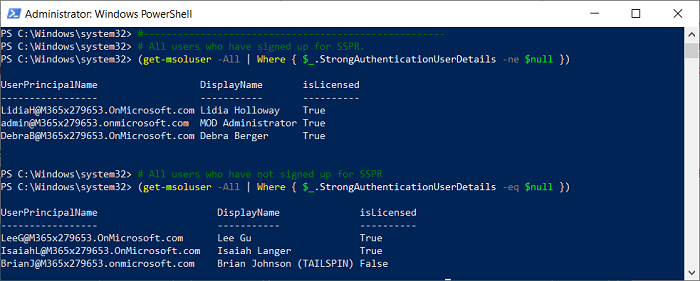
(get-msoluser -All | Where { $_.StrongAuthenticationUserDetails -ne $null })
(get-msoluser -All | Where { $_.StrongAuthenticationUserDetails -eq $null })
Import-CSV -Path $UsersCSV | ForEach-Object {
Set-AzureADUser -ObjectId $_.UserPrincipalName -Mobile $_.Mobile -ErrorAction SilentlyContinue}
$OneWaySMS = New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationMethod
$OneWaySMS.IsDefault = $false
$OneWaySMS.MethodType = "OneWaySMS"
$TwoWayVoiceMobile = New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationMethod
$TwoWayVoiceMobile.IsDefault = $true
$TwoWayVoiceMobile.MethodType = "TwoWayVoiceMobile"
$PhoneAppNotification = New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationMethod
$PhoneAppNotification.IsDefault = $false
$PhoneAppNotification.MethodType = "PhoneAppNotification"
$PhoneAppOTP = New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationMethod
$PhoneAppOTP.IsDefault = $false
$PhoneAppOTP.MethodType = "PhoneAppOTP"
$methods = @($OneWaySMS, $TwoWayVoiceMobile, $PhoneAppNotification, $PhoneAppOTP)
Import-CSV -Path $UsersCSV | Foreach-Object {
Set-MsolUser -UserPrincipalName $_.UserPrincipalName -StrongAuthenticationMethods $methods} -ErrorAction SilentlyContinue
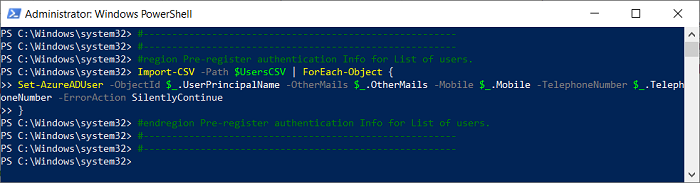
Import-CSV -Path $UsersCSV | ForEach-Object {
Set-AzureADUser -ObjectId $_.UserPrincipalName -OtherMails $_.OtherMails -Mobile $_.Mobile -TelephoneNumber $_.TelephoneNumber -ErrorAction SilentlyContinue}
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 26 2021 11:56 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 13 2023 12:40 PM