- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity
- Re: "Unusual volume of file deletion" Policy and Thumbs.db
"Unusual volume of file deletion" Policy and Thumbs.db
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 21 2019 08:39 AM - edited Aug 21 2019 08:40 AM
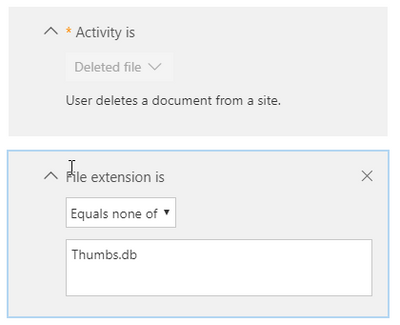
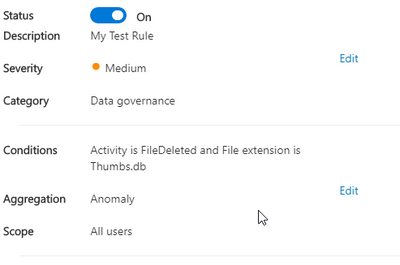
I enabled the "Unusual volume of file deletion" policy and been ok for several months. Yesterday I received over 2 dozens alerts when it deleted a user "deleting" a bunch of "Thumbs.db" files. She actually was not deleting files but from her statement, she was searching for images in a Sharepoint online site. Short story, I assume since Windows Explorer creates thumbs.db as folders are viewed, and when she as done, those files were deleted which prompted this alert (fyi, users sync SP libraries) . Not sure why it hasnt come up before. Whatever the case, I was looking to customize the alert anyways. I get these all of the time as users delete files they intend to delete. So I was thinking about creating some exclusions. For this example, the Thumbs.db. So I created this rule.
I would think this would exclude the extension thumbs.db; however when I save and look over the details it seems that it is setting the alert to ONLY look for this file.
Is this a typo or I am I misunderstanding this rule ? Long term, I would like to have a smarter rule; for example, ignore users download folders as we use OneDrive Sync and I get quite a few alerts when a user deletes old downloaded files.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 21 2019 10:58 AM
Looks like a display issue. But not sure the rule will work, as it's expecting a file *extension*, not the full file name.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 21 2019 11:05 AM
Solution@Vasil Michev .. Noticed the same issue when I created a condition to rule out a user "NT AUTHORITY\SYSTEM" when granting mailbox permissions. It too shows as an equal while I have "User is None of These". Weird.
Thanks for catching the syntax. I changed it to filename instead of extension. Will see if that works now.
Microsoft seems to have abandoned these rules. I reported over a year ago certain criteria should not get flagged. For example, the granting permissions. I do not know what exactly is setting off the alert, but every week, I get at least one that "NT AUTHORITY\SYSTEM" has added permissions to a mailbox. This has been going on since they enabled alerts and yet to this day, I still get the alert. I am hoping that adding the none of these to the alert, it will stop. I still want to know when someone grants permissions as that can be a sign of a hacker.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 21 2019 11:05 AM
Solution@Vasil Michev .. Noticed the same issue when I created a condition to rule out a user "NT AUTHORITY\SYSTEM" when granting mailbox permissions. It too shows as an equal while I have "User is None of These". Weird.
Thanks for catching the syntax. I changed it to filename instead of extension. Will see if that works now.
Microsoft seems to have abandoned these rules. I reported over a year ago certain criteria should not get flagged. For example, the granting permissions. I do not know what exactly is setting off the alert, but every week, I get at least one that "NT AUTHORITY\SYSTEM" has added permissions to a mailbox. This has been going on since they enabled alerts and yet to this day, I still get the alert. I am hoping that adding the none of these to the alert, it will stop. I still want to know when someone grants permissions as that can be a sign of a hacker.