Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity
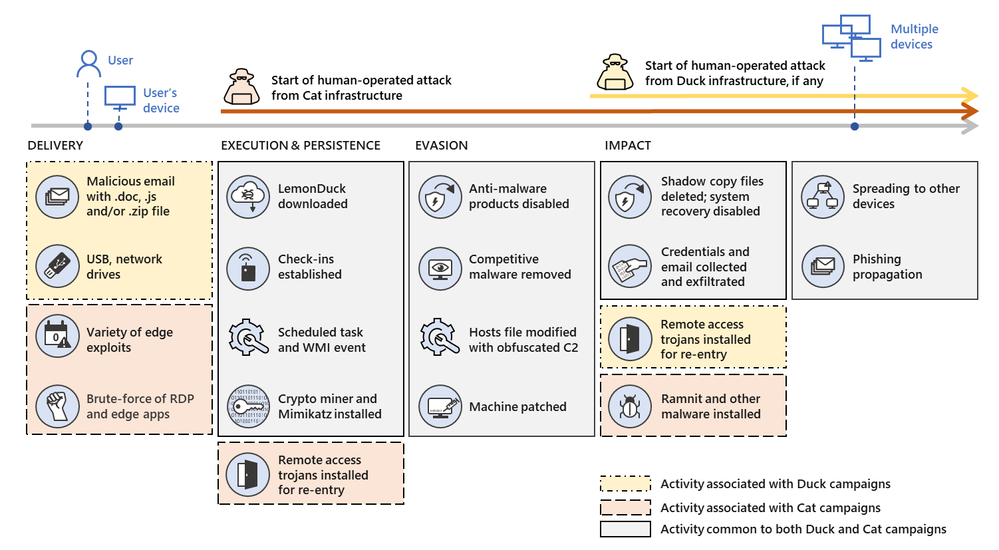
- New Blog Post | When coin miners evolve, Part 2: Hunting down LemonDuck and LemonCat attacks
New Blog Post | When coin miners evolve, Part 2: Hunting down LemonDuck and LemonCat attacks
Discussion Options
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 29 2021 12:32 PM
In this two-part blog series, we expose a modern malware infrastructure and provide guidance for protecting against the wide range of threats it enables. Part 1 covered the evolution of the threat, how it spreads, and how it impacts organizations. Part 2 provides a deep dive on the attacker behavior and outlines investigation guidance.
Labels:
0 Replies