- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity
- Re: New Blog Post | Microsoft’s Response to CVE-2021-44228 Apache Log4j 2
New Blog Post | Microsoft’s Response to CVE-2021-44228 Apache Log4j 2
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 13 2021 09:55 AM
Microsoft’s Response to CVE-2021-44228 Apache Log4j 2 – Microsoft Security Response Center
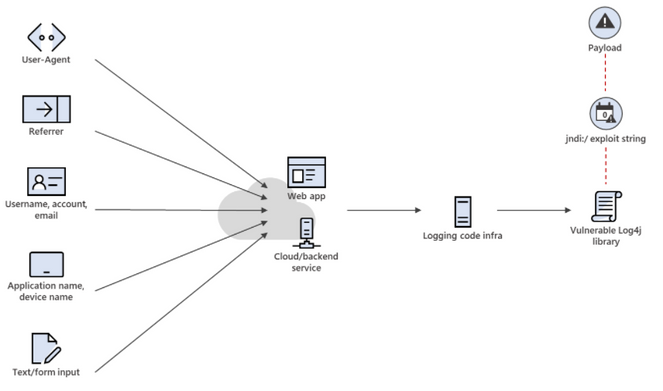
Microsoft continues our analysis of the remote code execution vulnerability (CVE-2021-44228) related to Apache Log4j (a logging tool used in many Java-based applications) disclosed on 9 Dec 2021. As we and the industry at large continue to gain a deeper understanding of the impact of this threat, we will publish technical information to help customers detect, investigate, and mitigate attacks, as well as guidance for using Microsoft security solutions to increase resilience against related attacks. We will update this blog with information and protection details as they become available.
In addition to monitoring the threat landscape for attacks and developing customer protections, our security teams have been analyzing our products and services to understand where Apache Log4j may be used and are taking expedited steps to mitigate any instances. If we identify any customer impact, we will notify the affected party. Our investigation to date has identified mitigation steps customers could take in their environments as well as on our services.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 22 2021 07:54 AM
@AshleyMartin Tnx for the article.
Is Microsoft planning on removing/patching log4j files in their products anytime soon? Just installed a SQL2019 server, which installes some old log4j files?!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 30 2021 08:15 AM
We also are seeing this with SQL2019. What remediation does Microsoft suggest for this file?
C:\Program Files\Microsoft SQL Server\150\DTS\Extensions\Common\Jars\log4j-1.2.17.jar
|
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 13 2022 05:39 AM
@KLawrence510Apache Log4J 1.x versions are even more vulnerable, but not for this vulnerability. There are plenty of other vulnerabilities in 1.x versions. What Microsoft is trying to say, is that they use super old version with even more vulnerabilities, but they don't care, because it is not new and popular vulnerability :)))