- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity
- New Blog Post | Automation for responding to Microsoft Defender for Key Vault alerts
New Blog Post | Automation for responding to Microsoft Defender for Key Vault alerts
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 22 2022 02:24 PM
Automation for responding to Microsoft Defender for Key Vault alerts - Microsoft Tech Community
Azure Key Vault is an essential cloud service for storing and accessing secure data including secrets, keys, certificates, and passwords. If this data is compromised, attackers may be able to gain access to essential company resources and from there, perform lateral movement throughout the organization’s environment. Defender for Key Vault can be used to detect unusual and potentially harmful access to Azure native Key Vault accounts. When anomalous activity is detected, Defender for Key Vault shows an alert which includes details of the activity and suggested recommendations to remediate. The alerts for Defender for Key Vault fall in the “Credential Access” stage of the MITRE ATT&CK matrix where the attacker attempts to gain access or credentials that are used within the organization’s environment.
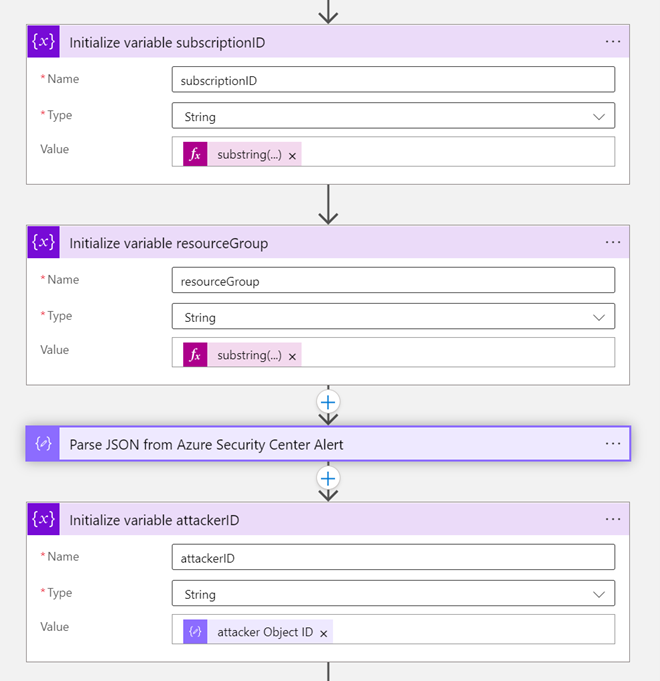
Aside from utilizing the alerts and recommendations that Microsoft Defender for Cloud already has in place for your Key Vault accounts, we have created a logic app that can be leveraged as response actions. When the logic app is executed, it will automatically respond to the Key Vault alert by removing the access policies and RBAC permissions the user has in the Key Vault. The rest of this blog addresses these two parts of the logic apps: how it removes access policies and how it removes RBAC permissions in the Key Vault.
- Labels:
-
Cloud Security