- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity
- Mapping Adaptive Application Controls to MITRE ATT&CK Framework
Mapping Adaptive Application Controls to MITRE ATT&CK Framework
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 08 2021 04:55 AM - edited Aug 08 2021 08:06 AM
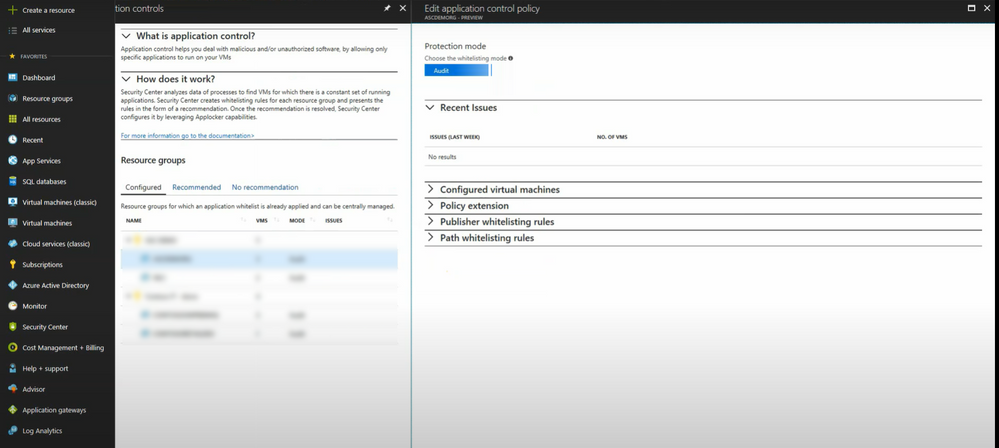
I want to draw your attention to a great feature in Azure called “Adaptive Application Controls”. It utilizes following three tools to accomplish its tasks:
- Azure Security Center
- Azure Security Center Recommendation
- Azure Defender for Servers
Azure’s Adaptive Applications Control uses advanced machine learning, with at least 2 weeks of data to train ML-algorithm to identify commonly run applications. This is to see how “normal” looks like. When this data is ready, a summary is presented to Security Administrators under the “Recommended” category. This service groups systems based on similar executables that run in these systems. Administrators can move systems from one group to another, based on what makes most sense. After checking and reviewing these executables, administrators can “Audit” or monitor these systems for any executable that was not initially allowed.
If an executable is detected which is not whitelisted, the service will alert on it. It does not block the applications from running in audit mode, which in turn gives administrators a chance to optimize the list of allowed executables and reduce false-positives.
Mapping to MITRE ATT&CK Framework:
There are some considerations based on the MITRE ATT&CK framework as well. These include techniques such as path-based masquerading, which may evade path-based rules defined in this control, causing false negatives. But hash-based and publisher-based rules will detect the unauthorized/ untrusted files that run. These detections occur every 12 hours and not in real-time. If the adversary uses space after filename for example “picture.jpg “ (MITRE technique id T1036.006), trying to exploit OS’s functionality to automatically find the true filetype and eventually execute malicious binary. Such attacks will be detected by these controls.
Similarly, another masquerading technique called invalid code signing (MITRE ID: T1036.001), where adversaries attempt to evade tools and detection by copying metadata and signature of a signed program. This is a technique used by the North Korean cyber espionage group APT37, among other groups like Regin, Windshift etc. Since the Adaptive Applications Control registers signatures of allowed applications, these invalid code signatures won’t check out, and will be detected.
Another technique (id T1554) is used where adversaries try to accomplish persistence, by modifying client software binaries for applications often used by users. Attackers can take the open source code, add backdoor to it, and replace the infected application with the original. Consider the example of famous OpenSSH backdoor. But since Azure’s Adaptive Application control has hash-based checks as well, these malicious executable will be detected.
Leveraging machine learning for automatically finding what normal looks like, saves security administrators’ and system owners’ time. Once approved, applications are white-listed and one still has time to optimize the whitelist while in “audit” mode, before enforcing rules.
PS: If you see Qualys in the list of your applications, its just something that comes free of cost with Azure Defender for servers for vulnerability scanning.