- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity
- Re: Issues trying to block non Azure AD Hybrid Joined devices from accessing Office 365
Issues trying to block non Azure AD Hybrid Joined devices from accessing Office 365
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Nov 03 2020
12:40 PM
- last edited on
May 24 2021
03:26 PM
by
TechCommunityAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 03 2020
12:40 PM
- last edited on
May 24 2021
03:26 PM
by
TechCommunityAP
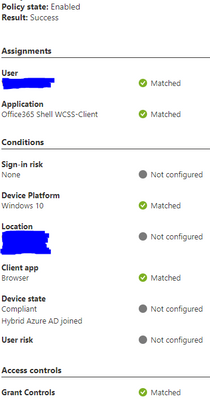
Here is what I'm trying to accomplish. Right now we have domain joined devices that are Azure AD hybrid joined as well. I want to create a conditional access policy that will block access to Office 365 web if a device is not Azure AD hybrid joined. I've created a policy and put the details below. Right now it's just blocking Office 365 web access on all devices and it doesn't care whether it's hybrid joined or not. What am I missing?
Assignments:
- Users and groups - One test user assigned
- Cloud apps or actions - Include - Office 365
- Conditions - Device Platforms - Include Any Device/ Exclude Android/iOS/macOS
Access Controls
- Grant - Grant Access - Require Hybrid Azure AD joined device - Require one of the selected controls
Nothing else if filled out. Here is a picture of the sign ins through Azure AD showing the policy applying:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 06 2020 09:43 AM - edited Nov 06 2020 09:43 AM
Anyone have any thoughts here? Or does anyone have a recommendation for another place where I might find an answer?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 07 2020 06:48 AM
If you use Chrome you need the 'Windows 10 accounts' extension in order for the browser to pass on it's hybrid joined.
Have you checked the sign-in logs in order to verify what exactly is going wrong?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 09 2020 03:40 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 12 2020 10:49 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 16 2020 08:46 AM
The first thing is that it's not possible for an Android or IOS device to be Azure AD Hybrid Joined. Am not 100% sure about MacOS but I don't think it can be either.
So any rule that says Compliant or Azure AD Hybrid Joined should suffice. I'm assuming you are trying to block Windows devices that are Azure AD Joined but not Hybrid Joined from accessing the Office 365 Web Services?
I've set this up in a demo tenant with a Block rule where the following is set
Target Users A single test users
App Included Office 365
Conditions Device Platform included Windows (Nothing Else Selected)
Device State Include All Device States & Exclude Azure AD Hybrid Joined
Access Controls Grant is set to Block
When I run a whatif the rule is applied only when the specified user attempts to access the selected app from a Windows device. If the device is Azure AD Hybrid Joined it will be granted access otherwise it won't. Any other platform the policy is not applied
Is that somewhere close to what you were trying to achieve?