- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity
- Re: Guest Accounts (non-ms) and encrypted documents
Guest Accounts (non-ms) and encrypted documents
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 03 2022 11:12 PM
Hi All,
I've done a search and have been combing through documents looking for confirmation that guest accounts that are not MS need to be tied to Microsoft to open a protected document in a desktop application. This is with the integration working between SPO and AAD to create accounts.
This seems to be the hunch looking at the following posts:
- Secure external collaboration using sensitivity labels - Microsoft Tech Community
- Manage sensitivity labels in Office apps - Microsoft 365 Compliance | Microsoft Docs t
Non protected document:
- Recipient authenticates to SPO
- Recipient opens the doc in Web Apps
- Everything is fine
Protected document:
- Recipient authenticates to SPO
- Web App asked to open in a desktop app
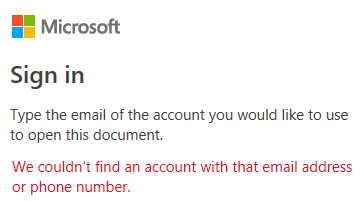
- Desktop App launches but asks the user to sign-in, they don't have a ms account e.g. @gmail.com
- User cant authenticate to view the data (Account not found)*
*Guest exists in the tenant and has authed previously via the web apps.
Completing some tests with co-authoring on in another environment, the user can open an encrypted document on the web without setting up a MS identity. I was hoping like with the web when federated they would just re-auth through the google workflow.
Does this seem right? Every guest using non-MS accounts that wants to open a document locally would need to setup a MS account when utilising but not when using Web Apps?
I have likely missed something, but keen to see how other people are working.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 04 2022 11:04 PM
- External Gmail users will need to use Web Apps in the sender's tenant as a guest user to access encrypted documents.
- External gmail users cannot use an office suite to sign in unless they have a MS enabled account to access the document.
Looks like this is a hard requirement