- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity
- Guest accounts get flagged as a threat in Identity & Access
Guest accounts get flagged as a threat in Identity & Access
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 12 2020 05:30 PM
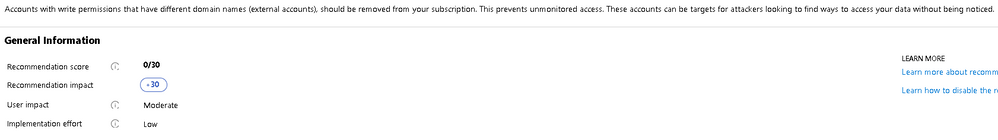
My question today is based around a threat I reviewed in a clients security center for Identity and Access (see screenshot below). FYI - I have asked this question in msdn forum, but havnt got any feedback https://social.msdn.microsoft.com/Forums/en-US/5a9dedc4-2ace-40b8-a624-da9bdcf4b215/guest-accounts-g...
This error is coming up for my account. As we are a service provider to our clients for Azure cloud solutions (build environments etc.), we get our clients to add our Microsoft accounts as a guest account to the subscription.
Is this not the best way to gain access to a clients environment? All our accounts are MFA etc. Also, is states this prevents "unmonitored access" what does that even mean? Everything I do is logged in the activity monitor, as far as I see, my guest account is locked down to the same level as any other account in the clients AD?
We also commonly see "External accounts with write permissions should be removed from your subscription" come up as well.
Can someone please advise on the implications of ignoring/supressing these recommendations? Furthermore if anyone has any insight into what the best practice is for consultants to gain access to client environments (e.g. use our own accounts, get the client to create us an account, etc.) that would be greatly appreciated.
We have always taken the approach of having our accounts added into their AAD as guests to avoid handling multiple identies across all our clients etc. Just seems like the route of having a new identity created for each client is less secure and cumbersome then utilizing 1 identity.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 13 2020 05:55 AM