Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Day Zero Support for iOS 9 with Intune
Day Zero Support for iOS 9 with Intune
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
By
Published
Sep 08 2018 07:25 AM
1,692
Views
Sep 08 2018
07:25 AM
Sep 08 2018
07:25 AM
First published on CloudBlogs on Sep 09, 2015
Updated 4/7/2016 Earlier today Apple released the final version of iOS 9 to developers worldwide (with public release set for Sept 16, and a new iOS 9.1 beta drop available). Over the past few months, we have been busy working to ensure that Intune is fully compatible with this latest version of Apple’s mobile operating system, and we are happy to announce that Microsoft Intune has Day 0 support for managing iOS 9 devices . All the existing Intune features currently available for managing iOS devices will continue to work seamlessly as users upgrade their devices to iOS 9. As a member of the Intune Product Engineering team that works closely with Apple on support for its platforms, I want to share insights into some of the new iOS 9 features for IT and the Enterprise and how they are supported in Microsoft Intune. As we continuously update the Intune service, you will begin to see these new features and many more. UPDATE: The iOS 9 extension is now available for System Center Configuration Manager. Managed App Conversion One of the most significant changes in iOS 9 is the ability to retroactively convert a personally-installed app to an Intune-managed app. Previously in iOS 8 and earlier, organizations wanting to take advantage of our family of managed Microsoft apps could deploy the managed apps using Intune. But in many cases, users had one of our popular productivity apps like Microsoft Word already installed. For Intune to manage that app, the user would have to manually un-install their “personal” version and allow the Intune-managed version to install. This was confusing and time-consuming, and since last year we’ve been discussing with Apple ways to improve the flow for managing apps on iOS devices. Now in iOS 9, Intune has the ability (with the user’s permission) to “take over” management of an app already installed on the device. Rest assured that after “conversion” of the app, all the same Intune mobile app management (MAM) policies and data protection mechanisms are immediately put in place for the app and its data. And with our new support for multi-identity app management , users can leverage a single productivity app for personal and work use while Intune manages only the corporate account. Under the covers, iOS 9 introduces a new “ChangeManagementState” key to the InstallApplication MDM command that Intune uses to push apps to devices. Setting this key to the value of “Managed” allows Intune to prompt the user to convert the app. Users on down-level versions (iOS 8 and earlier) will be unaffected by this new feature and will continue to see the “old” experience. This new iOS 9 capability will be made available in the next monthly update to the Intune service. UPDATE: This new feature is now available for all customers and will take effect automatically when deploying apps to iOS 9 devices.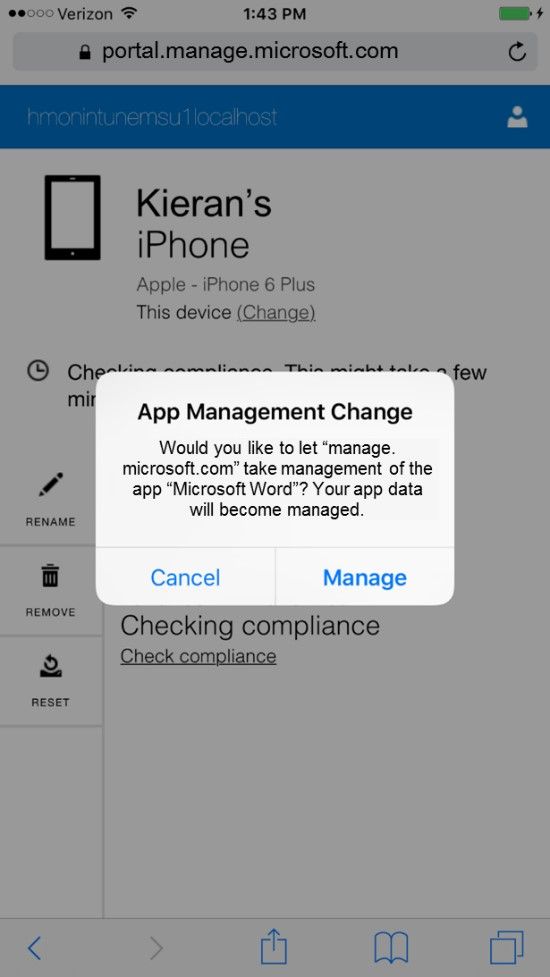 Enterprise Capabilities
From the IT administrator’s perspective, iOS 9 introduces a number of new configuration options and enterprise-ready features. I’ll highlight some of the most impactful changes to the MDM framework and enterprise feature set here. You can check out the full set of new MDM restrictions in the
MDM Configuration Profile
.
Enterprise Capabilities
From the IT administrator’s perspective, iOS 9 introduces a number of new configuration options and enterprise-ready features. I’ll highlight some of the most impactful changes to the MDM framework and enterprise feature set here. You can check out the full set of new MDM restrictions in the
MDM Configuration Profile
.
 AirDrop
We’ve previously discussed Microsoft’s
multi-layered approach to data protection
(protecting the device, app, file, and identity). One of the key security models iOS uses to ensure device-level protection is the concept of “unmanaged” vs. “managed” data. To ensure the security of corporate data, you want to prevent managed data from leaking into unmanaged locations.
Back in iOS 7, Apple added iOS support for the wireless transfer protocol
AirDrop
– effectively adding a new data storage location. Around the same time, the MDM framework was updated to allow MDM providers to disable this file-sharing feature. The problem is that the MDM restriction only works on Supervised iOS devices, leaving BYOD users susceptible to accidental data leakage. With iOS 9, a new MDM setting “forceAirDropUnmanaged” designates AirDrop as an “unmanaged” destination for data storage. This setting pairs nicely with the “Allow managed documents in other unmanaged apps” restriction (found in the “Apps” section of the iOS Configuration Policy template in the Intune admin console) – and both settings work on any BYOD or corporate device (no supervision required)! Our guidance is to set the first restriction (AirDrop) to YES and the second restriction to NO. This will ensure users cannot accidentally wirelessly transit corporate data to another iOS or Mac device using AirDrop.
AirDrop
We’ve previously discussed Microsoft’s
multi-layered approach to data protection
(protecting the device, app, file, and identity). One of the key security models iOS uses to ensure device-level protection is the concept of “unmanaged” vs. “managed” data. To ensure the security of corporate data, you want to prevent managed data from leaking into unmanaged locations.
Back in iOS 7, Apple added iOS support for the wireless transfer protocol
AirDrop
– effectively adding a new data storage location. Around the same time, the MDM framework was updated to allow MDM providers to disable this file-sharing feature. The problem is that the MDM restriction only works on Supervised iOS devices, leaving BYOD users susceptible to accidental data leakage. With iOS 9, a new MDM setting “forceAirDropUnmanaged” designates AirDrop as an “unmanaged” destination for data storage. This setting pairs nicely with the “Allow managed documents in other unmanaged apps” restriction (found in the “Apps” section of the iOS Configuration Policy template in the Intune admin console) – and both settings work on any BYOD or corporate device (no supervision required)! Our guidance is to set the first restriction (AirDrop) to YES and the second restriction to NO. This will ensure users cannot accidentally wirelessly transit corporate data to another iOS or Mac device using AirDrop.
 iCloud Photo Library
As part of the iOS 8.1 update last year, a new feature called
iCloud Photo Library
made its debut. The successor to Photo Stream, iCloud Photo Library automatically syncs your entire collection of photos and videos to Apple’s cloud service, enabling anywhere access from any other device, and making it easy to share the content with contacts or family members – perfect for sharing photos of your recent snorkeling adventures in Hawaii; but problematic for snapshots of the whiteboard at yesterday afternoon’s quarterly sales meeting. The iOS 9 update adds an important new MDM setting “allowCloudPhotoLibrary” which disables this cloud syncing feature. Users can still share photos manually without the risk of accidentally leaking corporate images to the cloud.
App Whitelisting
For a while now, it’s been possible to limit the ability of end-users to install and uninstall apps on their device using these two MDM restrictions: allowAppInstallation and allowAppRemoval. Setting both of these to FALSE disables the App Store functionality (the icon disappears from the homescreen) and also disables the option to uninstall apps (the “x” symbol over the jiggling icons just doesn’t show up). This allows IT administrators to manage a device, provision it with all the requisite apps, then flip on the restrictions to prevent the user from disrupting the apps installed on the device. This works well enough – until one of the apps needs updating or a new app needs to be added. With the App Store disabled, neither of these actions is possible.
Fortunately, iOS 9 introduces a much-needed new setting: allowUIAppInstallation (note the “UI” part of the setting name). Setting this restriction on a Supervised iOS device removes the App Store icon from the homescreen, but allows app updates and new apps to continue to be deployed through MDM. This effectively limits the user’s ability to add or changes apps on the device, while offering the IT administrator maximum flexibility to continue deploying apps and updates to the device. The result: true app whitelisting capability on iOS.
All of these new iOS 9 MDM restrictions (and any of the MDM settings from previous releases) are supported today in Intune using
iOS Custom Policy
. So go ahead and take advantage of the new enterprise capabilities as your users upgrade to the latest version of iOS.
App Management
Every new release of iOS brings with it
exciting new features
and security enhancements that enable apps to interact more deeply with the device and the user. The Intune engineering team has evaluated all the facets of iOS 9 and assessed the potential impact on corporate data security of apps.
iCloud Photo Library
As part of the iOS 8.1 update last year, a new feature called
iCloud Photo Library
made its debut. The successor to Photo Stream, iCloud Photo Library automatically syncs your entire collection of photos and videos to Apple’s cloud service, enabling anywhere access from any other device, and making it easy to share the content with contacts or family members – perfect for sharing photos of your recent snorkeling adventures in Hawaii; but problematic for snapshots of the whiteboard at yesterday afternoon’s quarterly sales meeting. The iOS 9 update adds an important new MDM setting “allowCloudPhotoLibrary” which disables this cloud syncing feature. Users can still share photos manually without the risk of accidentally leaking corporate images to the cloud.
App Whitelisting
For a while now, it’s been possible to limit the ability of end-users to install and uninstall apps on their device using these two MDM restrictions: allowAppInstallation and allowAppRemoval. Setting both of these to FALSE disables the App Store functionality (the icon disappears from the homescreen) and also disables the option to uninstall apps (the “x” symbol over the jiggling icons just doesn’t show up). This allows IT administrators to manage a device, provision it with all the requisite apps, then flip on the restrictions to prevent the user from disrupting the apps installed on the device. This works well enough – until one of the apps needs updating or a new app needs to be added. With the App Store disabled, neither of these actions is possible.
Fortunately, iOS 9 introduces a much-needed new setting: allowUIAppInstallation (note the “UI” part of the setting name). Setting this restriction on a Supervised iOS device removes the App Store icon from the homescreen, but allows app updates and new apps to continue to be deployed through MDM. This effectively limits the user’s ability to add or changes apps on the device, while offering the IT administrator maximum flexibility to continue deploying apps and updates to the device. The result: true app whitelisting capability on iOS.
All of these new iOS 9 MDM restrictions (and any of the MDM settings from previous releases) are supported today in Intune using
iOS Custom Policy
. So go ahead and take advantage of the new enterprise capabilities as your users upgrade to the latest version of iOS.
App Management
Every new release of iOS brings with it
exciting new features
and security enhancements that enable apps to interact more deeply with the device and the user. The Intune engineering team has evaluated all the facets of iOS 9 and assessed the potential impact on corporate data security of apps.
Updated 4/7/2016 Earlier today Apple released the final version of iOS 9 to developers worldwide (with public release set for Sept 16, and a new iOS 9.1 beta drop available). Over the past few months, we have been busy working to ensure that Intune is fully compatible with this latest version of Apple’s mobile operating system, and we are happy to announce that Microsoft Intune has Day 0 support for managing iOS 9 devices . All the existing Intune features currently available for managing iOS devices will continue to work seamlessly as users upgrade their devices to iOS 9. As a member of the Intune Product Engineering team that works closely with Apple on support for its platforms, I want to share insights into some of the new iOS 9 features for IT and the Enterprise and how they are supported in Microsoft Intune. As we continuously update the Intune service, you will begin to see these new features and many more. UPDATE: The iOS 9 extension is now available for System Center Configuration Manager. Managed App Conversion One of the most significant changes in iOS 9 is the ability to retroactively convert a personally-installed app to an Intune-managed app. Previously in iOS 8 and earlier, organizations wanting to take advantage of our family of managed Microsoft apps could deploy the managed apps using Intune. But in many cases, users had one of our popular productivity apps like Microsoft Word already installed. For Intune to manage that app, the user would have to manually un-install their “personal” version and allow the Intune-managed version to install. This was confusing and time-consuming, and since last year we’ve been discussing with Apple ways to improve the flow for managing apps on iOS devices. Now in iOS 9, Intune has the ability (with the user’s permission) to “take over” management of an app already installed on the device. Rest assured that after “conversion” of the app, all the same Intune mobile app management (MAM) policies and data protection mechanisms are immediately put in place for the app and its data. And with our new support for multi-identity app management , users can leverage a single productivity app for personal and work use while Intune manages only the corporate account. Under the covers, iOS 9 introduces a new “ChangeManagementState” key to the InstallApplication MDM command that Intune uses to push apps to devices. Setting this key to the value of “Managed” allows Intune to prompt the user to convert the app. Users on down-level versions (iOS 8 and earlier) will be unaffected by this new feature and will continue to see the “old” experience. This new iOS 9 capability will be made available in the next monthly update to the Intune service. UPDATE: This new feature is now available for all customers and will take effect automatically when deploying apps to iOS 9 devices.
 Enterprise Capabilities
From the IT administrator’s perspective, iOS 9 introduces a number of new configuration options and enterprise-ready features. I’ll highlight some of the most impactful changes to the MDM framework and enterprise feature set here. You can check out the full set of new MDM restrictions in the
MDM Configuration Profile
.
Enterprise Capabilities
From the IT administrator’s perspective, iOS 9 introduces a number of new configuration options and enterprise-ready features. I’ll highlight some of the most impactful changes to the MDM framework and enterprise feature set here. You can check out the full set of new MDM restrictions in the
MDM Configuration Profile
.
- A new App Trust Flow now prevents side-loaded apps from launching by default.
- Support for Exchange ActiveSync v16 protocol is enabled in the native Mail and Calendar apps (see more details on the Outlook dev blog ).
- AirDrop can now be designated as an unmanaged storage location, helping to prevent a potential source of data leakage.
- iCloud Photo Library can be disabled to ensure photos containing sensitive content are not uploaded to third-party cloud services.
- A new MDM restriction hides the App Store icon while still allowing app installs and updates.
 AirDrop
We’ve previously discussed Microsoft’s
multi-layered approach to data protection
(protecting the device, app, file, and identity). One of the key security models iOS uses to ensure device-level protection is the concept of “unmanaged” vs. “managed” data. To ensure the security of corporate data, you want to prevent managed data from leaking into unmanaged locations.
Back in iOS 7, Apple added iOS support for the wireless transfer protocol
AirDrop
– effectively adding a new data storage location. Around the same time, the MDM framework was updated to allow MDM providers to disable this file-sharing feature. The problem is that the MDM restriction only works on Supervised iOS devices, leaving BYOD users susceptible to accidental data leakage. With iOS 9, a new MDM setting “forceAirDropUnmanaged” designates AirDrop as an “unmanaged” destination for data storage. This setting pairs nicely with the “Allow managed documents in other unmanaged apps” restriction (found in the “Apps” section of the iOS Configuration Policy template in the Intune admin console) – and both settings work on any BYOD or corporate device (no supervision required)! Our guidance is to set the first restriction (AirDrop) to YES and the second restriction to NO. This will ensure users cannot accidentally wirelessly transit corporate data to another iOS or Mac device using AirDrop.
AirDrop
We’ve previously discussed Microsoft’s
multi-layered approach to data protection
(protecting the device, app, file, and identity). One of the key security models iOS uses to ensure device-level protection is the concept of “unmanaged” vs. “managed” data. To ensure the security of corporate data, you want to prevent managed data from leaking into unmanaged locations.
Back in iOS 7, Apple added iOS support for the wireless transfer protocol
AirDrop
– effectively adding a new data storage location. Around the same time, the MDM framework was updated to allow MDM providers to disable this file-sharing feature. The problem is that the MDM restriction only works on Supervised iOS devices, leaving BYOD users susceptible to accidental data leakage. With iOS 9, a new MDM setting “forceAirDropUnmanaged” designates AirDrop as an “unmanaged” destination for data storage. This setting pairs nicely with the “Allow managed documents in other unmanaged apps” restriction (found in the “Apps” section of the iOS Configuration Policy template in the Intune admin console) – and both settings work on any BYOD or corporate device (no supervision required)! Our guidance is to set the first restriction (AirDrop) to YES and the second restriction to NO. This will ensure users cannot accidentally wirelessly transit corporate data to another iOS or Mac device using AirDrop.
 iCloud Photo Library
As part of the iOS 8.1 update last year, a new feature called
iCloud Photo Library
made its debut. The successor to Photo Stream, iCloud Photo Library automatically syncs your entire collection of photos and videos to Apple’s cloud service, enabling anywhere access from any other device, and making it easy to share the content with contacts or family members – perfect for sharing photos of your recent snorkeling adventures in Hawaii; but problematic for snapshots of the whiteboard at yesterday afternoon’s quarterly sales meeting. The iOS 9 update adds an important new MDM setting “allowCloudPhotoLibrary” which disables this cloud syncing feature. Users can still share photos manually without the risk of accidentally leaking corporate images to the cloud.
App Whitelisting
For a while now, it’s been possible to limit the ability of end-users to install and uninstall apps on their device using these two MDM restrictions: allowAppInstallation and allowAppRemoval. Setting both of these to FALSE disables the App Store functionality (the icon disappears from the homescreen) and also disables the option to uninstall apps (the “x” symbol over the jiggling icons just doesn’t show up). This allows IT administrators to manage a device, provision it with all the requisite apps, then flip on the restrictions to prevent the user from disrupting the apps installed on the device. This works well enough – until one of the apps needs updating or a new app needs to be added. With the App Store disabled, neither of these actions is possible.
Fortunately, iOS 9 introduces a much-needed new setting: allowUIAppInstallation (note the “UI” part of the setting name). Setting this restriction on a Supervised iOS device removes the App Store icon from the homescreen, but allows app updates and new apps to continue to be deployed through MDM. This effectively limits the user’s ability to add or changes apps on the device, while offering the IT administrator maximum flexibility to continue deploying apps and updates to the device. The result: true app whitelisting capability on iOS.
All of these new iOS 9 MDM restrictions (and any of the MDM settings from previous releases) are supported today in Intune using
iOS Custom Policy
. So go ahead and take advantage of the new enterprise capabilities as your users upgrade to the latest version of iOS.
App Management
Every new release of iOS brings with it
exciting new features
and security enhancements that enable apps to interact more deeply with the device and the user. The Intune engineering team has evaluated all the facets of iOS 9 and assessed the potential impact on corporate data security of apps.
iCloud Photo Library
As part of the iOS 8.1 update last year, a new feature called
iCloud Photo Library
made its debut. The successor to Photo Stream, iCloud Photo Library automatically syncs your entire collection of photos and videos to Apple’s cloud service, enabling anywhere access from any other device, and making it easy to share the content with contacts or family members – perfect for sharing photos of your recent snorkeling adventures in Hawaii; but problematic for snapshots of the whiteboard at yesterday afternoon’s quarterly sales meeting. The iOS 9 update adds an important new MDM setting “allowCloudPhotoLibrary” which disables this cloud syncing feature. Users can still share photos manually without the risk of accidentally leaking corporate images to the cloud.
App Whitelisting
For a while now, it’s been possible to limit the ability of end-users to install and uninstall apps on their device using these two MDM restrictions: allowAppInstallation and allowAppRemoval. Setting both of these to FALSE disables the App Store functionality (the icon disappears from the homescreen) and also disables the option to uninstall apps (the “x” symbol over the jiggling icons just doesn’t show up). This allows IT administrators to manage a device, provision it with all the requisite apps, then flip on the restrictions to prevent the user from disrupting the apps installed on the device. This works well enough – until one of the apps needs updating or a new app needs to be added. With the App Store disabled, neither of these actions is possible.
Fortunately, iOS 9 introduces a much-needed new setting: allowUIAppInstallation (note the “UI” part of the setting name). Setting this restriction on a Supervised iOS device removes the App Store icon from the homescreen, but allows app updates and new apps to continue to be deployed through MDM. This effectively limits the user’s ability to add or changes apps on the device, while offering the IT administrator maximum flexibility to continue deploying apps and updates to the device. The result: true app whitelisting capability on iOS.
All of these new iOS 9 MDM restrictions (and any of the MDM settings from previous releases) are supported today in Intune using
iOS Custom Policy
. So go ahead and take advantage of the new enterprise capabilities as your users upgrade to the latest version of iOS.
App Management
Every new release of iOS brings with it
exciting new features
and security enhancements that enable apps to interact more deeply with the device and the user. The Intune engineering team has evaluated all the facets of iOS 9 and assessed the potential impact on corporate data security of apps.
- Search integration for apps. For apps that implement this feature, two new indexes are created: a private on-device index, and a public “Apple cloud index.” The private index is stored securely on the device and never uploaded to third-party cloud services or synced across devices. For the cloud index, app developers must opt-in to have specific data anonymously-hashed and indexed, ensuring that by default corporate content is never indexed in the public cloud.
- Multi-tasking . The latest iPad Air 2 hardware supports multi-tasking, for the first time allowing multiple third-party apps to run side by side in the foreground. We’ve updated our Intune App SDK so that it’s ready to handle multi-tasking apps and keep content secure in the foreground and the background.
- canOpenURL limits . Due to recent concerns around apps “scanning” a user’s device to determine what other apps may be installed (which is both a privacy and security concern), iOS 9 now requires apps pre-declare which custom URL schemes they wish to open. This effectively prevents apps from indiscriminately calling canOpenURL repeatedly in order to query the presence of other apps on the device.
0
Likes
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.