- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Azure Rights Management: Logging and all that it enables
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hi Everyone,
I know you're all fed up with "Happy New Year" but I will offer such wishes anyway! In 2014 protecting your information will (should) be at the top of your list. Unlike the 3 or so weeks of drinking 64 oz of water and exercising daily for 30 minutes, this is one promise that we're all expected to be better about. With this in mind, the next few posts will be dedicated to 'tracking' your important documents. One often ignored aspect of RMS is the ability to mine (quite impressive) logs for hits of things not being 'quite right'. Said differently, even the practice of using RMS on "somewhat sensitive" documents with a "Your Company -- All employees" will yield a goldmine of very impressive usage data. At Microsoft we often send out "vision" documents, memos, etc with RMS protection so that we (the document owners, area leaders) can get a sense of the readership. Logs don't lie. Today's post was co-authored with Amrita, our logging expert. Enjoy.
Reminders: Follow us on twitter ( @TheRMSGuy ) and join in our our new RMS peer community at www.yammer.com/AskIPTeam .
Cheers,
Dan (on behalf of our wonderful team)
PS: Though this post is focused on Azure RMS, the AD RMS offering has wonderful SQL logs too so similar sentiments apply... especially the next post on how to use the new Microsoft "Power BI" to produce fantastic reports.
-------------------------------------
Hi, Amrita here, Let's talk logging! Using the usage logging feature in Microsoft Rights Management Service (Azure RMS), with a few simple steps you can capture and view logs for every administration action and request for your protected content to Microsoft Rights Management as soon as it happens.
This information is useful for a variety of reasons:
- Analyzing data access for business insight . Using these logs, you can create reports and drive insights such as: who is accessing your sensitive data, what devices are being used for access, which locations are your users accessing data from, and report on which users have read a given document.
- Monitoring for abuse . You can access your logs in near-real-time (delay: < 15 minutes). This allows you to continuously monitor usage of your Microsoft RMS assets. You know your employees best, and are uniquely qualified to identify any abuse patterns. For example, your tenant administrators may want to be alerted if there is a spike in access of your assets after business hours (why someone is trying to open lots of critical documents in a short time), or if the same user is accessing from two different IP addresses within 15 minutes (are my passwords compromised), or if someone is trying to read your content from a remote location (we don’t have any staff there).
- Performing Forensics . When there is an information leak, the top two questions are:
- Who recently accessed the specific document that got leaked?
- What information did a specific user access recently?
With the Azure RMS architecture, you can save and share documents with any number of great tools: email, O365, consumer cloud storage services such as SkyDrive or DropBox, USB drives, and others, but you remain in control of who can access these docs. Any time someone wants to open and read a document protected with Microsoft RMS, strong encryption keeps your document safe until the user can prove their identity and that they have authorization to use the doc. The logging service helps you verify and track all access to your documents, so you feel safe sharing your data.
The following sections provide instructions on how to opt in for receiving your tenant logs. The Microsoft Rights Management Service can write log records for each transaction as part of the basic service price. All you have to do is provide a Windows Azure storage account to store the logs. You can decide how much history of logs to pay for, or move data into your on-premises BI tools and prune your Azure storage costs.
Step - By - Step Guide
Step 1: Understanding the Pre-requisites
To exercise the Usage Logging feature, the pre-requisites are as follows:
|
Pre-requisite |
Description |
|
An IT-managed Microsoft Rights Management service subscription |
You must have a Microsoft RMS subscription managed by your organization. Organizations that use the free ‘RMS for Individuals’ offer cannot get logs. |
|
A Windows Azure subscription |
You must have a subscription for Windows Azure and sufficient Azure storage to store your logs. For testing purposes, you can subscribe for a free Windows Azure 1-month trial . |
|
Windows PowerShell for rights management |
You will use Windows PowerShell cmdlets to configure and manage your RMS logs. Please download and configure Windows PowerShell for rights management using instructions at Install Windows PowerShell for rights management . |
Step 2: Set up a Windows Azure Storage
As previously outlined, the Microsoft Rights Management service writes logs to a Windows Azure storage account that you provide. We recommend you set up a dedicated storage account for the Microsoft RMS logs. You will need to share the storage account keys with the Microsoft Rights Management service, and potentially with other users in your organization that report on your logs.
To set up a Windows Azure storage:
-
Open a browser and navigate to the Windows Azure management portal at https://manage.windowsazure.com
-
Sign in with your Windows Azure account credentials
-
Select STORAGE in the left pane and click NEW at the bottom of the screen. Select STORAGE and QUICK CREATE .
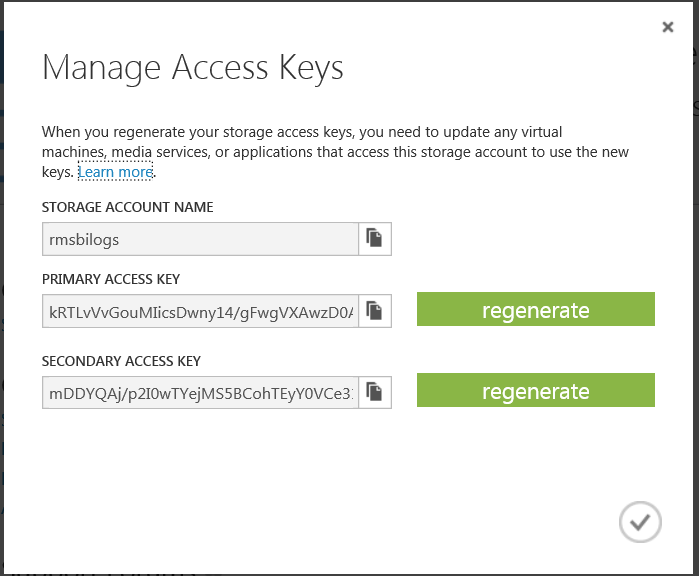
4. Type a unique name for your storage account URL,for example “ rmsbilogs ” for our fictitious company RMSBI Corporation, and select a location corresponding to the location of your RMS tenant, North Europe in our case. Click CREATE STORAGE ACCOUNT . Wait for Windows Azure to create your account. Once complete, you will see an Online status.
5. Click MANAGE ACCESS KEYS at the bottom of the screen. A Manage Access Keys dialog pops up and shows your primary and secondary access keys. Copy the primary access key to the clipboard, you will need this in the next step.
Step 3: Install Windows PowerShell for Rights Management
You will use the cmdlets of the Windows PowerShell for rights management to configure and manage your Microsoft RMS log. If you haven’t already done so, follow the instruction Install Windows PowerShell for rights management to download and configure Windows PowerShell for rights management .
Step 4: Configure Storage Account and Enable logging
To configure Microsoft RMS to log to the Windows Azure storage account:
1. Open an elevated Windows PowerShell command prompt.
2. Import the Microsoft Rights Management module for Windows PowerShell and connect to Azure RMS by typing the following commands.
PS C:Windowssystem32>Import-Module AADRM
PS C:Windowssystem32>Connect-AadrmService -verbose
3. When prompted for credentials, enter your Azure RMS tenant credentials (these credentials should have Global Administrator privilege) and wait to be authenticated. Example:
Username: admin@rmsbi.onmicrosoft.com
Password: ****************
4. Run the following commands to specify the Azure RMS where you want your logs. Replace the example access key in the ConvertTo-SecureString cmdlet with the storage access key that you copied from the Windows Azure management portal in step #2->#5 above. Replace the example storage account “RMSBILogs” with your real storage account name.
PS C:Windowssystem32> $accesskey = ConvertTo-SecureString"wUjKVV14XXUCrdpuLsIa8yQ5IgUmLSOLmlgS/CcHNZXiurEORjTItdtPf4OpCaIwGNyijjMPxvDEOG21HRKR7A==" –asplaintext -force
PS C:WindowsSystem32>Set-AadrmUsageLogStorageAccount -StorageAccount RMSBILogs -AccessKey $accesskey
RMSBILogs was set as the storage account for the usage log feature for the Rights management service.
PS C:Windowssystem32>
5. Finally, run the following cmdlet to enable logging:
PS C:Windowssystem32> Enable-AadrmUsageLogFeature
The usage log feature is enabled for the Rights management service.
PS C:Windowssystem32>
From this point onwards the Microsoft Rights Management service will log all requests served on behalf of your tenant to your storage account. Logs before this point are not available.
Step 5: Verify logs
You can verify the availability of logs by logging in to the Azure management portal. The logs should be available within 15 minutes.
How to Access and Use your RMS Logs
The storage account that you created for your RMS logs is like a mailbox and supports direct reading from the storage account. However this is not the optimal way to access it. For best performance and reduced costs, we recommend that you download the logs to local storage such as a local folder, database, or a map-reduce repository. You can access your logs in many different ways. Here are some commonly used methods:
Using Windows PowerShell Cmdlet
This is the simplest way to access your logs. The Get-AadrmUsageLog cmdlet downloads each blob as a file to the location you specify. You may analyze these files locally or import them into a database or Hadoop storage to do some serious crunching. For example:
-
To download all available logs to your E:logs folder:
Get-AadrmUsageLog -Path “e:logs” -
To download a specific range of blobs:
Get-AadrmUsageLog –Path “e:logs” –FromCounter 1024 –ToCounter 2047
Using Windows Azure Storage SDK
In some situations you may want more flexibility than Get-AadrmUsageLog provides. For example, you may need to delegate the downloading of logs to a person or process that cannot have your Microsoft RMS administrative credentials. Or you may want to poll for logs in real time in order to monitor abuse. In such situations,you can retrieve the logs by directly using the Windows Windows Azure Storage SDK .
Using Microsoft Power BI
Using Microsoft Power BI you can connect to your Azure storage account directly and download the data to Excel. Now with the new Excel features such as Power View and Power Map, you can generate cool charts from your logs within minutes. In the next blog, we will see how to create RMS reports using Power BI. Stay tuned!
How to Interpret your RMS Logs
RMS writes logs to your Windows Azure storage account as a series of blobs. Each blob contains one or more log records, in W3C extended log format. The blob names are numbers, in the order in which they were created. Use the following information to help you interpret the RMS logs.
Understanding the log format
Here is an example log file.
#Software: RMS
#Version: 1.0
#Fields: date time row-id request-type user-id result correlation-id content-id c-info c-ip
2013-09-19 13:46:44 0d07036b-c66c-4e92-b887-f59ecd61dc96 AcquireLicense 'janet@corp-contoso.com' 'Success' ad18e935-bcf9-4b51-9d34-cf3391c451ef {9312A0DF-DA57-4854-9160-
603A1ED06CB3} 'MSIPC;version=1.0.622.36;AppName=WINWORD.EXE;AppVersion=15.0.4535.1000;AppArch=x86;OSName=Windows;OSVersion=6.2.9200;OSArch=x86' 94.245.87.113
The following table provides the field definitions.
|
Field name |
W3C data type |
Description |
Example value |
|
Date |
Date |
UTC Date when the request was served. The source is the local clock on the server that served the request. |
2013-09-19 |
|
Time |
Time |
UTC Time in 24H format when the request was served. The source is the local clock on the server that served the request. |
13:46:44 |
|
row-id |
Text |
Unique GUID for this log record. This is useful for provenance when you aggregate logs or copy logs into another format. |
0d07036b-c66c-4e92-b887-f59ecd61dc96 |
|
request-type |
Name |
Name of the RMS API that was requested |
AcquireLicense |
|
user-id |
String |
The user who made the request. The value is enclosed in single quotes. Some request types are anonymous, in which case this field is ‘’. |
'janet@corp-contoso.com' |
|
Result |
String |
‘Success’ if the request was served successfully. The error type in single quotes if the request failed. |
‘Success’ |
|
correlation-id |
Text |
GUID that is common between RMS client log and server log for a given request. This helps in troubleshooting client issues. |
ad18e935-bcf9-4b51-9d34-cf3391c451ef |
|
content-id |
Text |
GUID, enclosed in curly braces, that identifies the protected content e.g. a document. This field has a value only if request-type is AcquireLicense, it is blank for all other request types. |
{9312A0DF-DA57-4854-9160-603A1ED06CB3} |
|
c-info |
String |
Information about the client platform making the request. The specific string varies depending on the application, OS, browser. |
'MSIPC;version=1.0.622.36;...OSArch=x86' |
|
c-ip |
Address |
IP address of the client making the request |
94.245.87.113 |
Understanding Common Request Types
The number of request types in Azure RMS is long and growing. Here are some of the common request types.
|
Field name |
Description |
|
AcquireLicense |
Client is requesting a license for a specific piece of content, from a Windows computer. |
|
FECreateEndUserLicenseV1 |
This is similar to the AcquireLicence request. This endpoint is for mobile clients. |
|
Certify |
Client is requesting a certificate (which is later used to get a license) from a Windows computer. |
|
GetClientLicensorCert |
Client is requesting a publishing certificate (which is later used to protect content) from a Windows computer. |
|
FECreatePublishingLicenseV1 |
This is the same as the previous two combined, from mobile clients. |
|
FindServiceLocationsForUser |
This is sometimes anonymous, and sometimes with authenticated. This is an innocuous request that queries for the URLs to certify and acquire license from. |
|
Decrypt |
You will see this only if you brought in your own key (BYOK, see whitepaper http://technet.microsoft.com/en-us/library/dn440580.aspx ). The Microsoft Rights Management service logs this when your key is used for decrypt – typically once per AcquireLicense and Certify. |
|
Sign |
You will see this only if you brought in your own key (BYOK). RMS logs this when your key is used for signing – typically once per one time per AcquireLicence (or FECreateEndUserLicenseV1), Certify, and GetClientLicensorCert (or FECreatePublishingLicenseV1). |
Frequently Asked Questions
1. Is the Microsoft RMS logging format similar to AD RMS?
Answer: The logging format is different from ADRMS and there are fewer fields logged so that downloading logs over the network is practical.
2. Do the logs also contain interaction from mobile devices?
Answer: Yes
3. Is it possible to identify protected documents with their names instead of content-id?
Answer: Currently we just support content-id.
4. Can I track document usage using the logs?
Answer: Yes, you can. I will show how to do this using Power BI in my upcoming blogs – check back in a few weeks!
What’s Next…?
This blog hopefully provided you with an overview of how useful the Microsoft RMS logs are, and how to get started with using your RMS logs. You can also find more information on TechNet: Log and analyze rights management usage .
In the next blog, we will see how to easily create cool RMS reports using Power BI. Stay tuned!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.