- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Auditing sensitive data on Windows endpoints using the Azure Information Protection client
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Getting an accurate visualization of sensitive data in your environment is a challenge that all companies face. This is even more of a challenge when you have thousands of employees that work remotely and do not connect to the corporate network on a regular basis. The Azure Information Protection client has a new passive auditing capability that will help with this challenge.
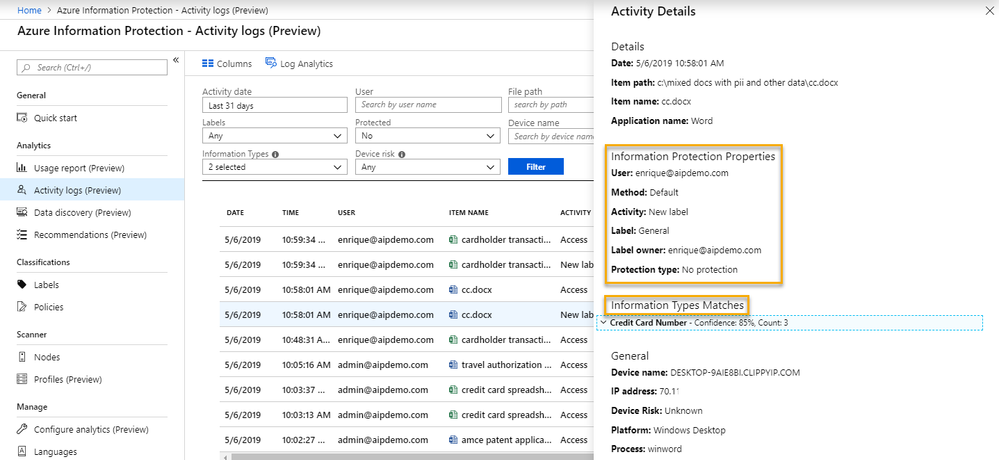
In the latest GA version of the Azure Information Protection client (1.48.204.0), you can now discover sensitive information in any document that is opened in Office on a machine with the AIP client installed. This will allow you to do passive data discovery across all your endpoints, even if they are not connected to your corporate network when they are working on that content. The image below shows a file that was labeled with an unprotected default label of General, yet contains Information Type Matches.
Once the AIP client is deployed throughout your environment, you will be able to run reports in the AIP Analytics activity pane or directly in Log Analytics to audit sensitive information that exists in unprotected documents.
This allows you to identify the types of sensitive information that exist on endpoints so you can create recommended conditions to help guide your users to classify sensitive data appropriately. You could also use this information to create automatic conditions to protect your mission critical sensitive information. And the beauty of this is that the AIP client does this without hurting performance the way that active scanners can.
Because we are aware that there may be privacy concerns with this, we have made this an opt-in capability that must be configured using an Advanced Setting in the global or a scoped policy in the AIP console. This way you can either turn it on for the full tenant and disable it for areas with privacy concerns, or you can only roll it out to your scoped policy for critical areas like Human Resources, Legal, or Engineering.
The steps to enable this are straight-forward and can be found in the official documentation. I will provide a quick primer below for convenience.
- Log into the AIP Console in the Azure Portal at https://aka.ms/AIPConsole
- In the left-hand blade, under Classifications, click on Policies
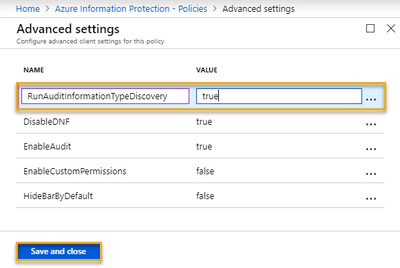
- In the Policies blade, right-click on either the Global or a Scoped Policy, and click Advanced settings
- In the Advanced settings blade, under Name, type RunAuditInformationTypeDiscovery, and under Value, type true
- Finally, click Save and close to finish enabling this amazing feature!
The result is analytics like the image shown in the beginning of this article. Please let us know if you have any questions in the comments below.
Thanks,
The Information Protection Customer Experience Engineering Team
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.