- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Announcing the Public Preview of features in Microsoft Information Protection unified analytics
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Microsoft Information Protection (MIP) is a built-in, intelligent, unified, and extensible solution to know your data, protect your data and prevent data loss across an enterprise – in Microsoft 365 cloud services, on-premises, third-party SaaS applications, and more.
Microsoft’s unified analytics solution provides a simple and unified approach to protecting sensitive information from risky or inappropriate sharing, transfer or use. In this release, Analytics supports the customers with the ability to view the below activities within Microsoft 365 Activity Explorer and audit.
This public preview will showcase the below capabilities:
- Sensitivity labeling events from office native (Word, Excel, PowerPoint, Outlook) is available in M365 Audit and Activity explorer. You can view the label activities from Microsoft 365 apps for Windows via “Current Channel” (version 2011+), MacOS via “Current Channel” (version 16.43+), the latest release of iOS/Android apps and Online apps in M365 Activity Explorer in Compliance center. Additional details are available here.
- Activities from AIP in Microsoft 365 Activity Explorer and Audit
- DLP activities for Exchange, SharePoint, OneDrive, Teams and On-premise DLP in Microsoft 365 Activity Explorer
Office native sensitivity labeling events in the unified analytics solution
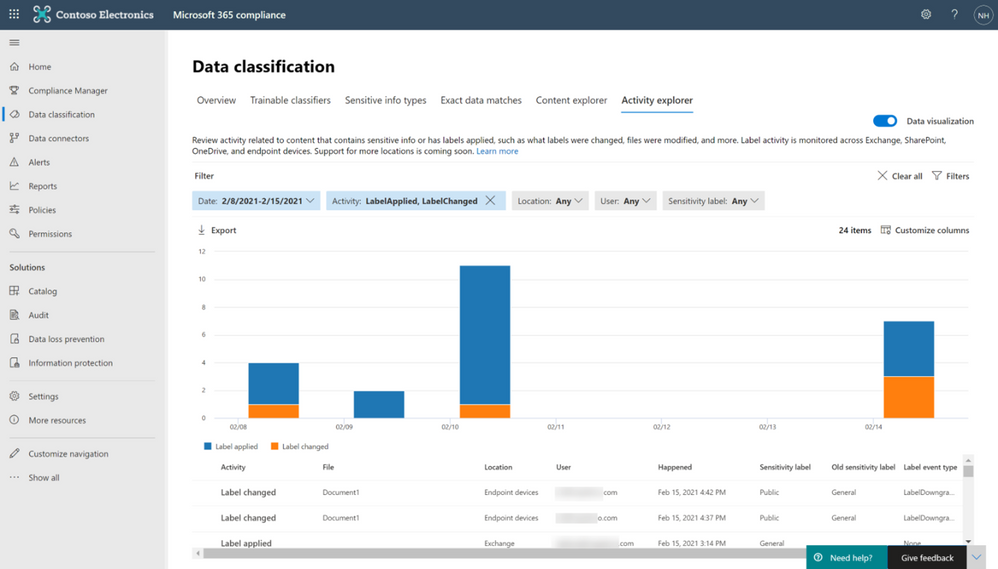
Audit log information includes label activities such as when label is applied, changed, removed and more. This is in addition to the already available logs in Activity Explorer covering Endpoint DLP, service based labeling and retention labeling activities.
Figure 1 – Activity Explorer view of label activity from office native
AIP audit events in the unified analytics solution
In Public Preview, Microsoft 365 Compliance Center’s enhanced unified labeling and analytics experience now offer support for the most awaited ‘Azure Information Protection (AIP) audit logs’ including exploration of all activities.
With this update, events reported by the AIP unified labeling client, AIP scanner, and MIP SDK can now be stored in Compliance Center and displayed along with events from Office 365 cloud labeling and DLP activities. See below representation of AIP audit events in M365 Activity explorer, you can use the application column to segment and investigate the data from AIP.
Figure 2 – Activity Explorer view of application detail from AIP
Note:
- Support for AIP audit logs in Compliance Center is a supplemental offering in addition to the existing AIP analytics solution. Storing AIP audit logs in the Log Analytics workspace and exploring them in the AIP Analytics (Preview) screens in the AIP area of the Azure portal continues to be available at this time. Customers should be aware that M365 Audit and Activity explorer will be the solution where all the AIP logs will eventually reside. While we will currently support AIP Analytics, it is important to note that future investments and developments to support Analytics capabilities will be focused on M365 Audit and Activity explorer.
- The Microsoft 365 Activity explorer is a premium service that is typically enabled as part of AIP P2 or via an E5 licenses. At this time and until further notice, as a courtesy to our customers, Microsoft is also making this experience available to existing AIP customers with AIP P1. You can refer to other permission and licensing details mentioned here for Activity explorer.
Known limitation: We had an issue of multiple "File read" ("Access") logs when a file is opened and saved with the AIP version of client lower than 2.8.85. This issue has been addressed in clients version since then and we recommend customers to upgrade to a version higher than the above so that the client sends only one "File read" ("Access") log when a user opens a labeled/protected document.
How to get started
If you have already configured your Log Analytics workspace in the AIP area of the Azure AIP portal, we have already onboarded your tenant and the audit events are now also stored also in the Compliance Center. You can start exploring them from within the Compliance Center experience in M365 Activity explorer.
If you have not configured your Log Analytics workspace in the Azure portal, and wish to explore your AIP audit events in the Compliance center, fill in this form and we will onboard your tenant.
DLP rule match events in the unified analytics solution
DLP rule matches generated in Exchange, Sharepoint, OneDrive, Teams and On-premise will be available in Activity explorer under an activity called ‘DLP rule matched’.
In addition, sensitive information type and matched text with the surrounding context (wherever available) will be available in the preview window. This capability provides DLP policy administrators with the ability to quickly assess if a detection is a true positive or not so they can initiate the appropriate remediation actions.
Figure 3 – DLP events available across locations
Clicking on the Sensitive information type opens up the panel with hit summary and contextual details:
Additional resources:
- For more information on M365 Activity explorer, please see this
- For more information on Data Loss Prevention, please see this and this
- For more information on DLP Alerts and Event Management, see this
- For more information on Sensitivity Labels as a condition for DLP policies, see this
- For more information on Sensitivity Labels, please see this
- For more information on conditions and actions for Unified DLP, please see this
- For the latest on Microsoft Information Protection, see this and this. For additional details on AIP audit logs in the Compliance Center – see the Public Preview documentation
- For more on Search the audit log in the Microsoft 365 Compliance Center see this
Thank you,
Bhavanesh Rengarajan (Microsoft Information Protection team)
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.