- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity
- An example of how you can use a custom Sensitive Info Type in the Microsoft 365 compliance center!
An example of how you can use a custom Sensitive Info Type in the Microsoft 365 compliance center!
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 23 2021 05:18 AM - edited Sep 23 2021 05:28 AM
Dear Microsoft 365 Security and Compliance Friends,
Collaboration in today's world, with a wide variety of Microsoft cloud services, is here to stay. As in all situations, there are pros and cons. For this reason, in this article I will show you how to work with Sensitive Info Types. But I won't use the "general" classic with the credit card numbers, but a real situation with a customer.
Here's the scenario I encountered with a customer. Technical manuals are created by engineers, including PowerShell blocks that are used for various configurations. These documents are the precious asset for the company/organization. These documents cannot simply "leave" the company or be shared. This is where "our" Sensitive Info Type comes into play. But how exactly does a Sensitive Info Type work? I will show you in a moment in the Microsoft 365 compliance center (and yes with the example of credit card numbers ;-). After that, we create our own Sensitive Info Type.
We start by navigating to the Micosoft 365 Compliance Center. https://compliance.microsoft.com
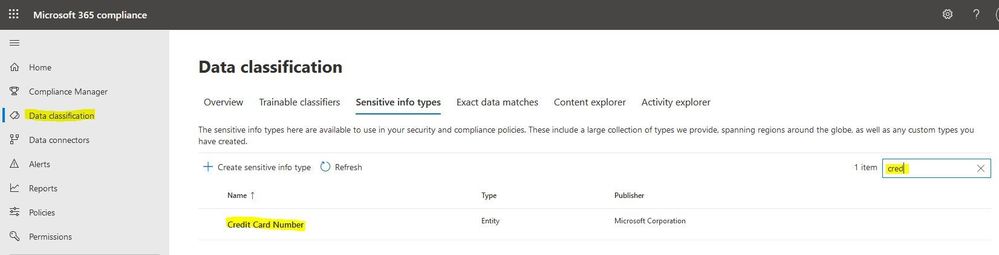
In the menu click on "Data classification" and navigate to "Sensitive info types" to the right you will see the search box, enter "cred". Then the Sensitive Infos Type "Credit Card Number"appears.
Click on "Credit Card Number. A new "Card" will open. Click on "Test".
Select "Upload file", I have prepared a text file with a fake credit card number.
Now click on "Test".
We see there is a match. This is how a Sensitive Info Type works (for example, in a policy). Click Finish.
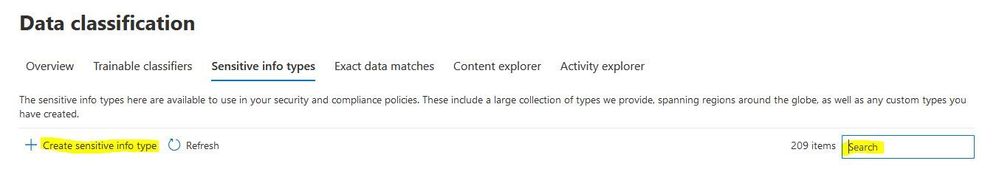
Now we create our own Sensitive Info Type. We go back to Sensitive Info Type, delete keyword in the search box and click on "Create sensitive info type".
Assign a name and description.
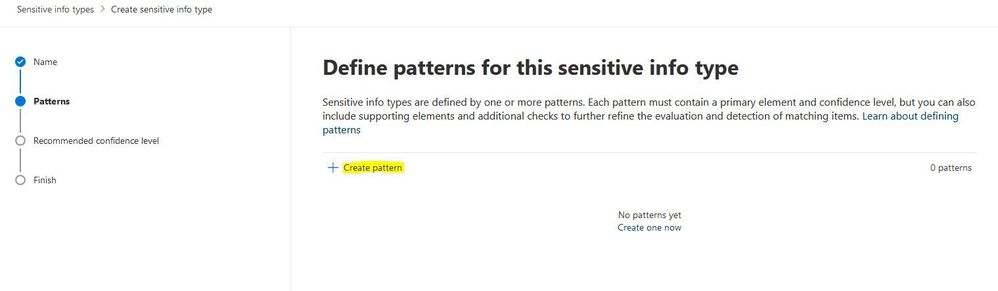
Click on "Create pattern".
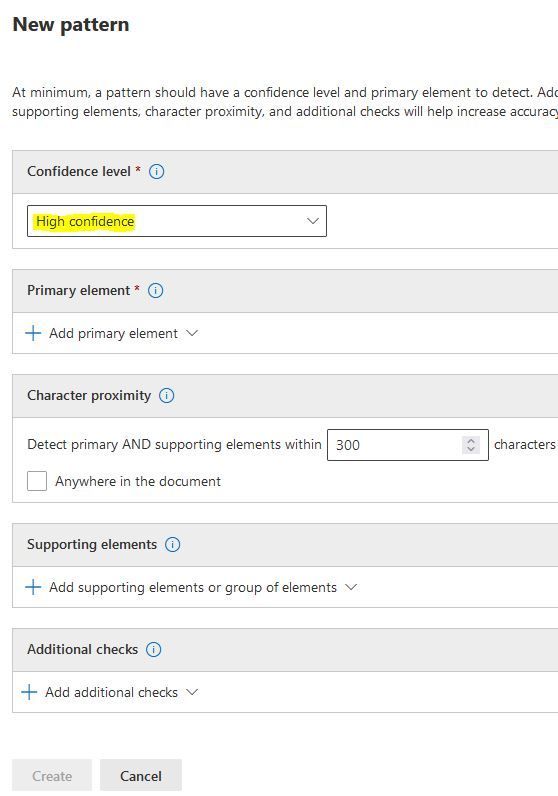
Confidence level: High Convidence.
Click "Add primary element" and select "Regular expression".
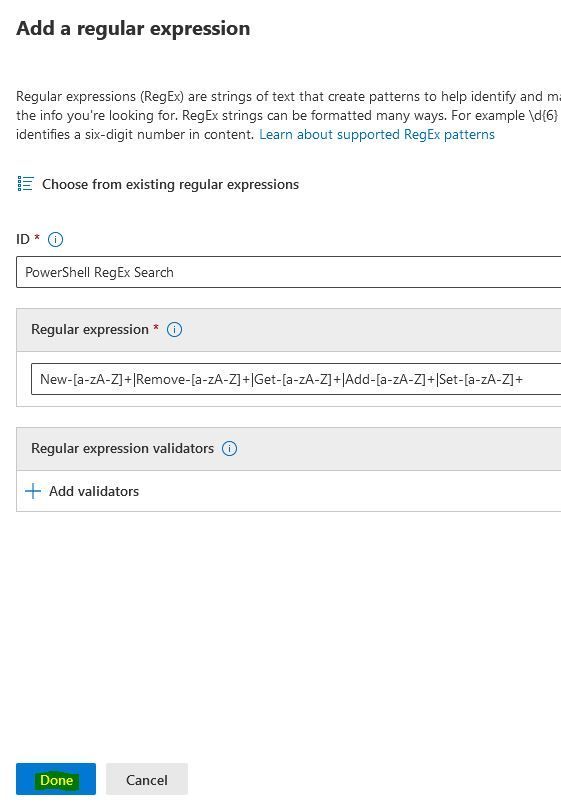
At "ID" you assign a name and at "Regular expression" you enter the following example and click on "Done".
(RegEx: New-[a-zA-Z]+|Remove-[a-zA-Z]+|Get-[a-zA-Z]+|Add-[a-zA-Z]+|Set-[a-zA-Z]+)
Click on "Supporting elements" and select "Regular expression" again.
Enter a name at "ID" and enter the following example and click "Done".
(RegEx: \s-[a-zA-Z]+\s)
We will create a second "pattern". Click on "Create pattern".
This time with a "Confidence level" of Medium. Click "Add primary elemtent" again.
At "ID" you assign a name and at "Regular expression" you enter the following example and click on "Done".
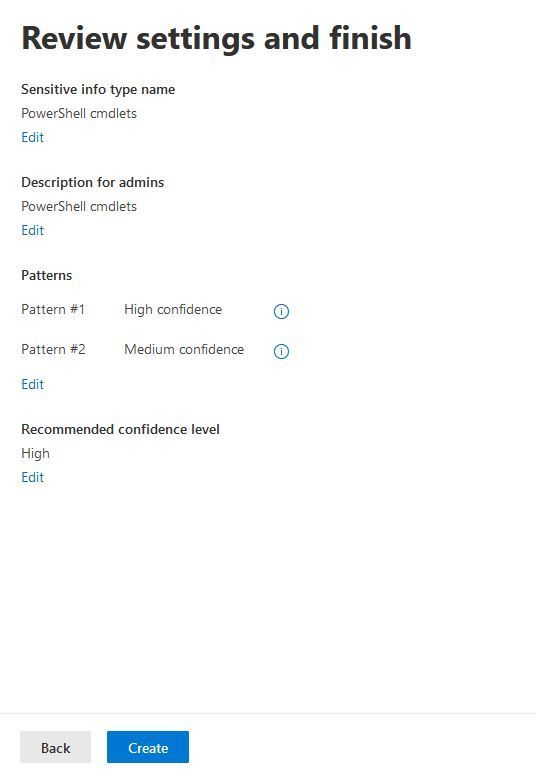
Now we have two patterns, we click on "Next".
Now we can determine the recommended confidence level.
We get the summary and click on "Create".
Perfect, click on "Done".
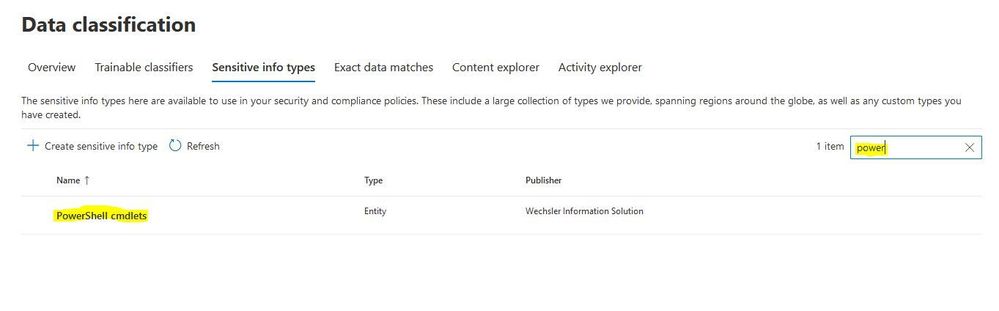
Back to the "Sensitive Info Type", we navigate to the search field again and enter "power". Now our new Sensitive Info Type appears. Click on the Sensitive Info Type.
Click on "Test".
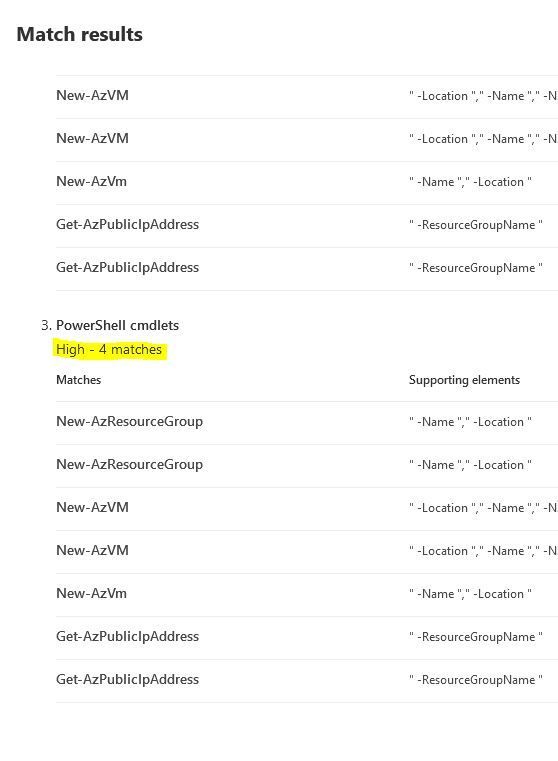
Now you need to upload a file again. I have prepared a Word document which is a guide for deploying a VM in Azure using PowerShell. After that click again on "Test".
Jackpot!! So we know for sure that our Sensitive Info Type will work in a policy!
Sure this wasn't super exciting, but I still wanted to share this information with you.
I hope this article was helpful for you? Thank you for taking the time to read this article.
Best regards, Tom Wechsler