- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- A proactive and comprehensive approach to data security with Microsoft Purview Data Loss Prevention
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In today’s modern workplace data security incidents can happen any time as users collaborate on data across a myriad networks, devices, and applications. And the volume of data, people who interact with the data, and activities around the data are all constantly changing. All of this means that the data security risks are increasing exponentially, and many organizations are struggling to keep up given their limited resources. This comes at a time when a recent Microsoft study showed that two in five security leaders feel at extreme risk due to cybersecurity staff shortage [1]. Organizations are looking for a solution that can provide comprehensive coverage across apps and devices to address these risks and is also easy to deploy and manage.
At Microsoft, we are committed to providing a unified and cloud-native solution that can help you prevent the loss of your sensitive data across your applications, services, and devices without the need to deploy and maintain costly infrastructure or agents. Microsoft Purview Data Loss Prevention (DLP) is an integrated, and extensible offering that allows organizations to manage their DLP policies from a single location and has a familiar user experience for both administrators and end-users. DLP is easy to turn on, doesn't require any agents and has protection built-in to Microsoft 365 cloud services, Office apps, Microsoft Edge (on Windows and Mac), and on endpoint devices. DLP controls can also be extended to the Chrome and Firefox browsers through the Microsoft Purview extension and to various non-Microsoft cloud apps such as Dropbox, Box, Google Drive, and others through the integration with Microsoft Defender for Cloud Apps.
Today, we are extremely excited to announce several new capabilities in public preview in Microsoft Purview DLP across three categories:
- Increasing the depth of protection to help protect all types of sensitive information with comprehensive coverage, including support for optical character recognition (OCR), fingerprinting, proactive protection to endpoint devices, support for password protected 7zip and .rar files, as well as enhancement to the policy enforcement engine.
- Further extending protection to additional planes and platforms to help support your diverse digital estate, including virtualized environments and remote and mapped network drives as well as making the endpoint DLP on macOS comprehensive
- Empowering admins and users to be efficient by making their everyday tasks easier and educating them to better handle sensitive information, including enhancements to policy tips for Windows and visibility into device deployment and policy sync status, matched conditions in DLP policies, and the document that resulted in DLP policy match on endpoint.
These capabilities will be rolling out to tenants in the coming weeks.
Increasing the depth of protection
The first capability in this category is support for optical character recognition (OCR). The DLP engine will be able to extract text from images, quickly recognize if the image contains sensitive information such as credit card or social security numbers, and prevent users from sharing such images. OCR will be available across Exchange Online, SharePoint Online, One Drive for Business, Teams, as well as Windows endpoints and supports over 150 languages. You can enable OCR within the Microsoft Purview compliance portal Settings page.

Further expanding the classification type, we are making several enhancements to the fingerprinting capabilities including extending the support for document fingerprinting to cover additional workloads such as SharePoint Online, One Drive, Teams, and Windows endpoint. You will now be able to:
- Create a fingerprint sensitive information type (SIT) from within the Data classification page in the Microsoft Purview compliance portal. You will also be able to set confidence thresholds (high, medium, low) for the percentage of text that the SIT should detect in the document and configure different restrictions based on the thresholds
- Edit and test the fingerprint so that you can fine tune it before rolling it out to your organization
- Use the fingerprint as you would any other SIT in the content contains condition as you configure your DLP policies
If you are already using Fingerprint SITs today, you can migrate them using the new user experience in the Microsoft Purview compliance portal or PowerShell.

Additionally, we are announcing just-in-time protection, a capability that enables you to proactively protect files on your Windows endpoint devices. With this capability every document on your endpoint is scanned at the time of egress to determine sensitivity, no matter whether it contains sensitive information or not or when it was created or modified. If the file being egressed has sensitive content that violates any of your DLP policy rules, the appropriate restrictions are applied and if the file doesn’t contain any sensitive content, the action is allowed. This capability provides proactive protection at the time of egress for files on your endpoint devices that might not have been interacted with for a long time but could potentially contain sensitive information. Learn more here.
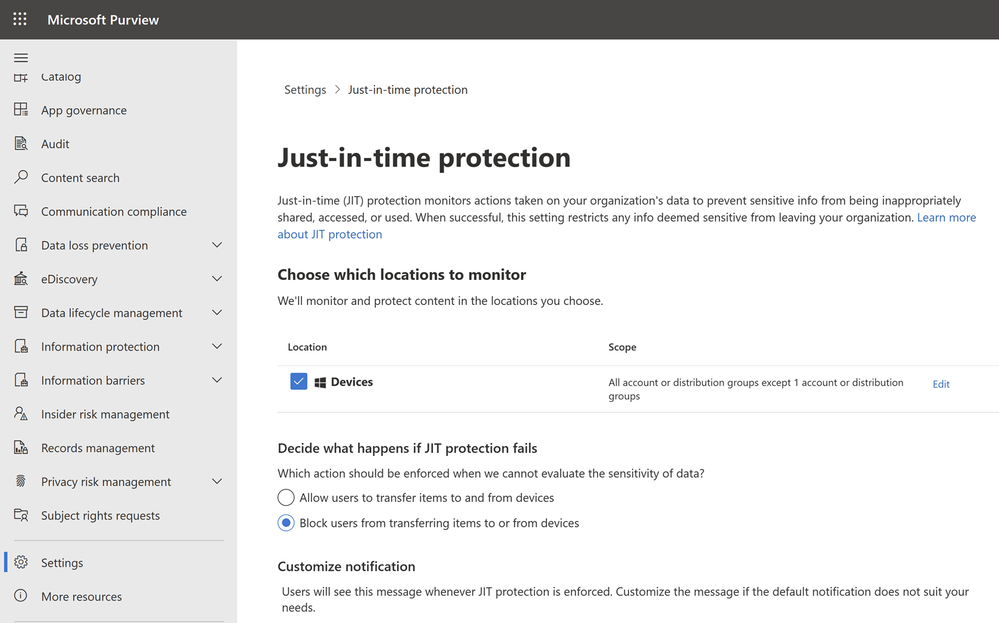
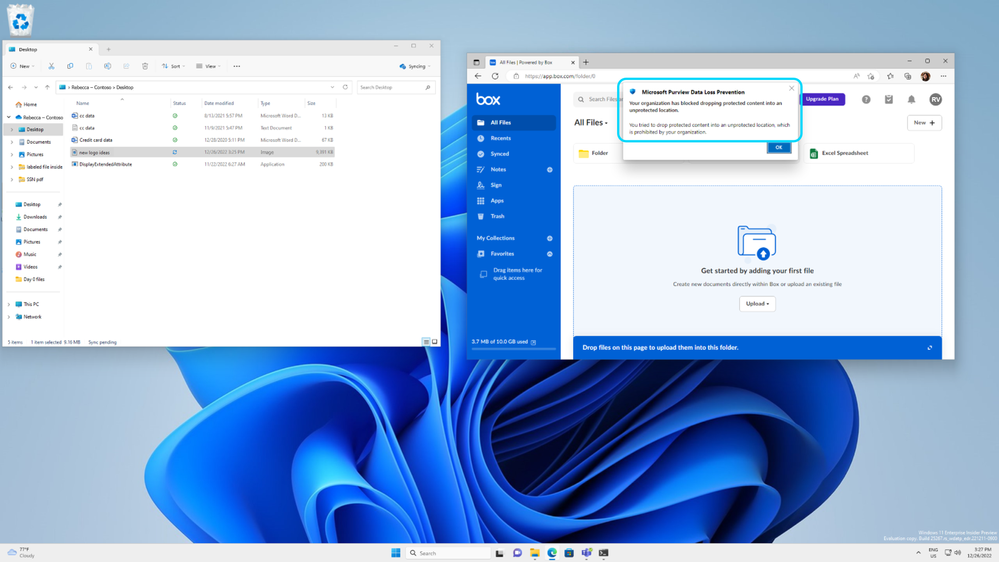 Figure 4a: An old document being proactively blocked from being uploaded to cloud until its sensitivity is determined Figure 4a: An old document being proactively blocked from being uploaded to cloud until its sensitivity is determined |
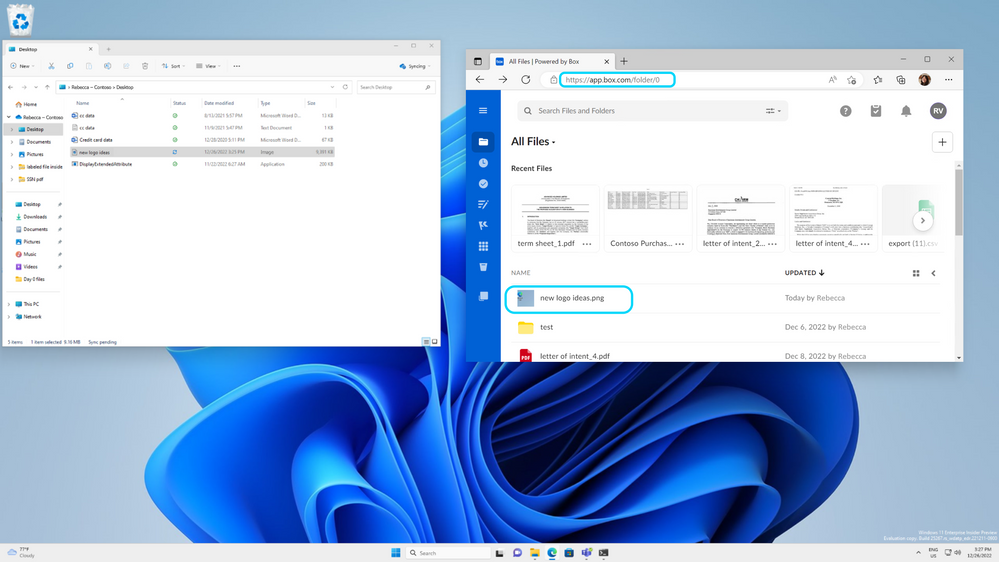 Figure 4b: Upload is successful once the document is assessed to contain non-sensitive content and action is tried again Figure 4b: Upload is successful once the document is assessed to contain non-sensitive content and action is tried again |
The next capability provides organizations the ability to detect the presence of password protected 7zip and .RAR files on the endpoint devices and configure specific restrictions for these files. This can be done by leveraging the condition ‘Document or attachment is password protected’. Learn more here.
And finally, we have made enhancements to our policy enforcement capabilities for files on Windows endpoint devices such that most restrictive actions amongst audit, block with override, or block across multiple matching DLP rules will apply on files that match a DLP policy. With this enhancement the DLP rules with the most restrictive action (block being the most restrictive, followed by block with override, and then audit) will apply when an egress activity is performed on a sensitive file on an endpoint device. Learn more here.
Extending protection to additional planes
We understand that most customers have a multicloud and multiplatform strategy, and we are investing heavily to support that reality. We are excited to share that organizations can now extend existing protection for sensitive files resting on endpoint devices against actions such as print, copy to USB, upload to cloud, and copy to clipboard, and more to virtualized environments including Windows Virtual Desktop, Citrix, AWS workspace, and Hyper-V platforms. Organizations can now protect sensitive data accessed via single and multi-session Windows 10 and 11 environments across several virtualized environments. Learn more here.
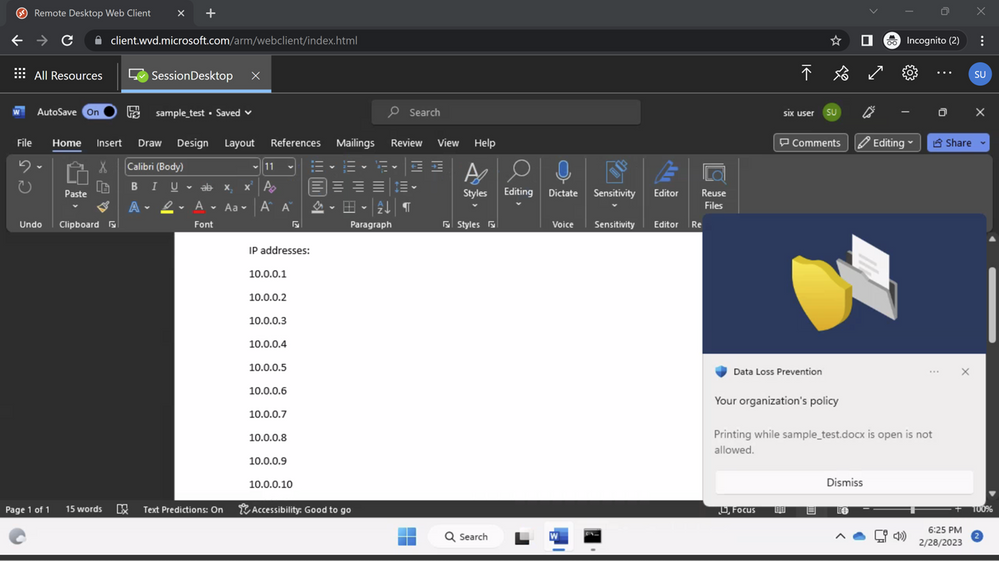
Next, we are also extending DLP protection for sensitive files stored on network shares. With this capability common egress actions such as copy to USB, print, upload to cloud and more on files containing sensitive information on network locations can be restricted as per organization’s DLP policies. Learn more here. 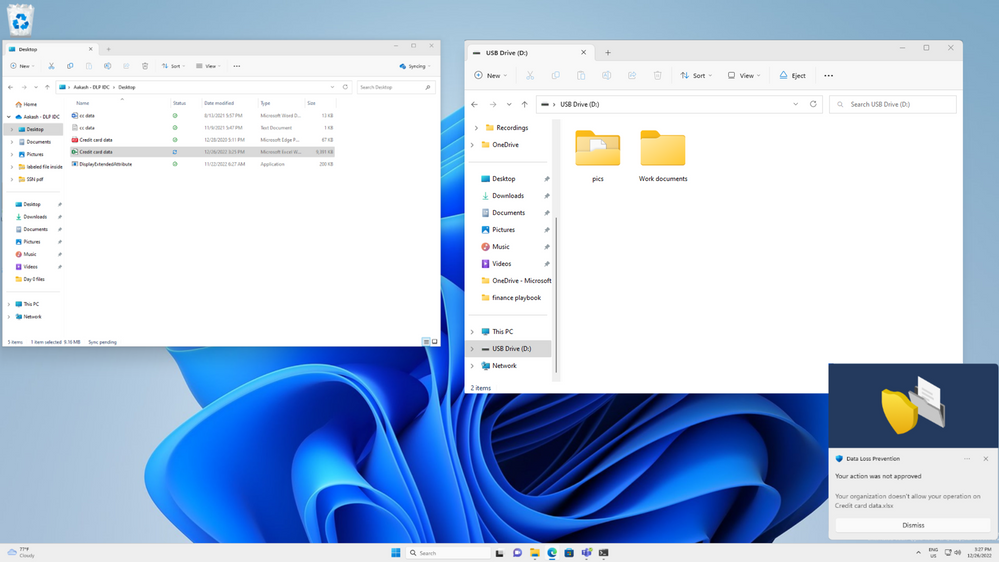
In addition, we are continuing to make the DLP solution on macOS comprehensive. You will now be able to protect sensitive file exfiltration through Bluetooth on Mac devices. We are extending the flexibility to create groups of apps and configure how sensitive data can be accessed by each of the apps as you define your DLP policy for Mac devices. Additionally, you will be able to customize notifications and policy tips to better educate users on handling sensitive data while using Mac devices.
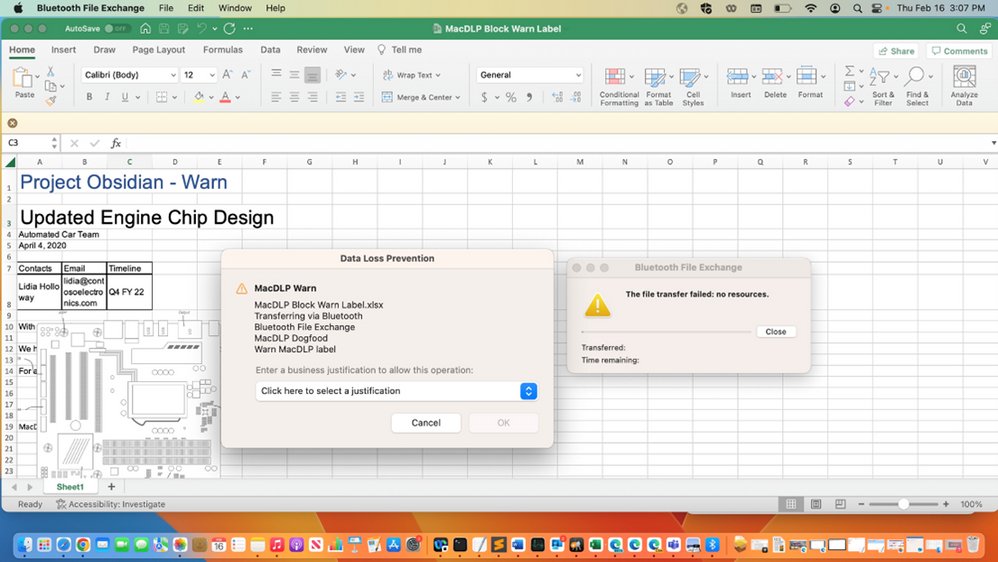
Lastly, we are also announcing support for advanced classification for Mac devices that enables you to leverage classification techniques like fingerprinting, exact data match, trainable classifiers, named entities, and more to detect sensitive content on Mac devices. Learn more about the capabilities supported on mac devices here.
Empowering admins and users to be efficient
Empowering admins to effectively perform their day-to-day tasks and educate end users to better handle sensitive data is critical to effective protection of data. Admins will now be able to see additional details about the device health as well as configuration status of all onboarded endpoint devices in the Device Onboarding tab in the Microsoft Purview compliance portal. Admins will get rich contextual information about the health of the device and visibility into which policies have synced to and apply on files for that device, allowing them to quickly identify and remediate any device misconfigurations as well as debug and self-heal common issues in their endpoint devices setup. 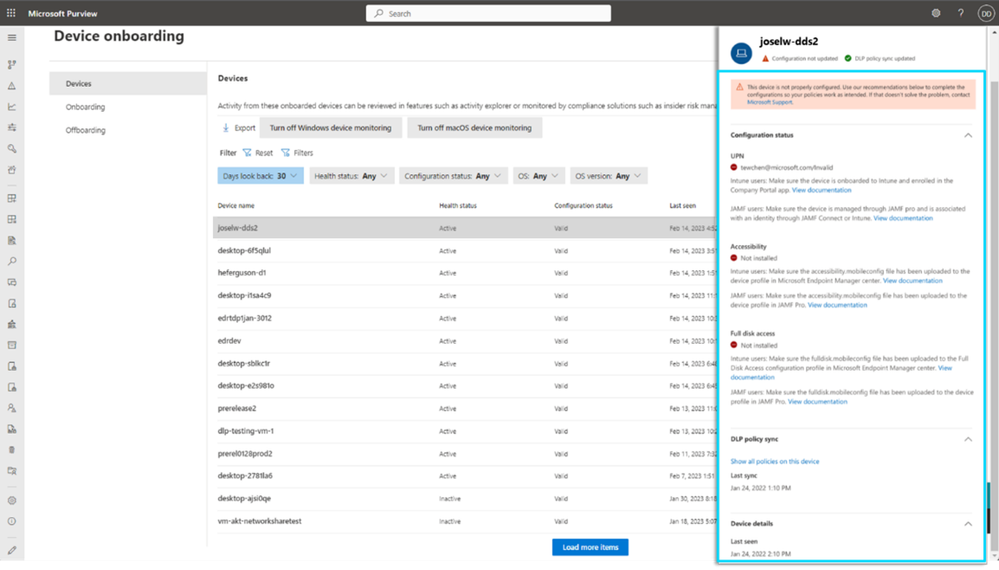
We have heard from customers that they need granular visibility to understand the exact cause of a DLP policy violation to perform necessary and quick remediation. In addition to the matched sensitive content and surrounding metadata, which we already provide, we are excited to share that DLP admins will now get visibility into matched DLP conditions configured as a part of DLP policies such as ‘Document type/extension is’, ‘Recipient or sender is a member of’, ‘Subject contains words’, ‘Content is received from’ and more, in the events tab on DLP Alerts page. The same information about the matched condition will also be available in the DLP alerts in the Microsoft Purview Audit logs, Microsoft 365 Defender portal, and Office365 Management Activity API. Learn more here.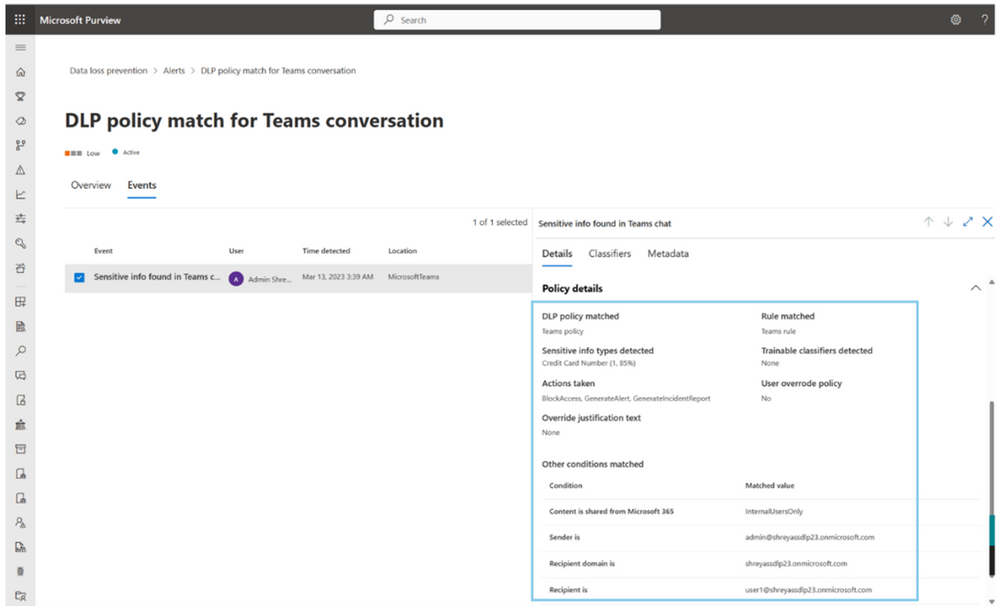
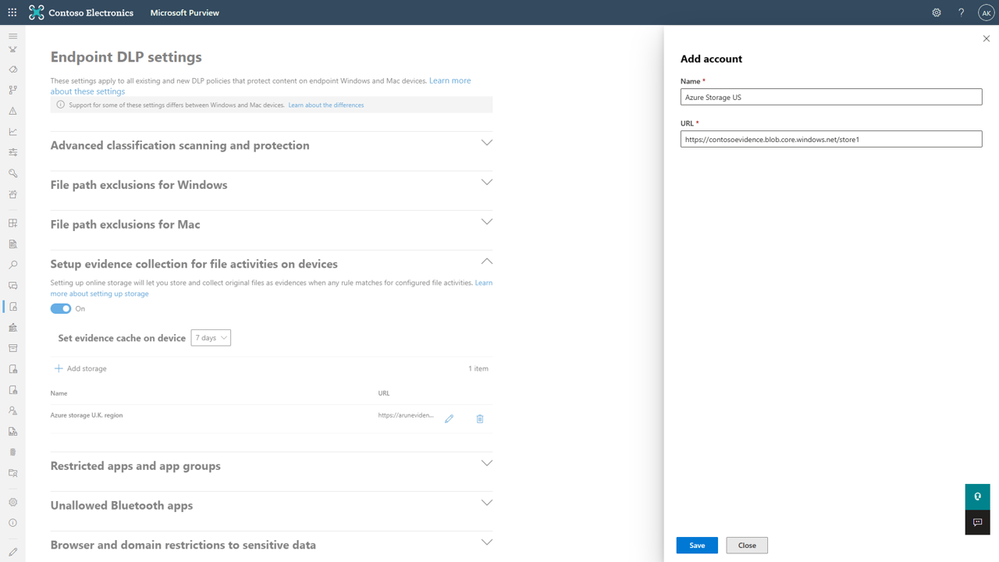
In addition to the matched condition, we are also providing visibility into the document that resulted in the DLP policy match on the Windows endpoint. This level of visibility will enable organizations to better triage false positives and fine tune their DLP policies to reduce noise. Additionally, in situations where the DLP alerts need further investigation, admins will be able to easily investigate the matched content and use it in case escalations. Customers will be able to provide a custom location as part of endpoint DLP settings where the files violating DLP policies will be stored. A link to the file uploaded on the customer-provided location will be made available as a part of the alert metadata at the time of investigation. Follow the steps below to get started:
- Navigate to endpoint DLP settings page in Microsoft Purview compliance center and enable the Store, which is turned off by default.
- Provide a valid URL to the Azure blob storage.
- Create and scope the policy to file activities for which you need to capture the original copy of the file.
- Navigate to the Activity Explorer page on the DLP tab and click on Details tab to view the link to file.

Recent research showed that 52% of respondents said educating their employees on safe data handling practices was a big challenge[2]. Microsoft Purview DLP has long supported policy tips and user notification, which educate users in real time when they are about to take a policy violating action, thus helping minimize the risk of accidental data loss. Administrators can configure policy tips such that users can be warned, blocked from performing the action, or blocked but allowed to perform the action with justification. Today, we are excited to share enhancements to the DLP policy tips for Outlook desktop for Windows. Users will now be able to see policy tips when working with advanced classifiers such as named entities, exact data match, credential scans, as well as trainable classifiers. Additionally, we are adding eight new predicates including ‘Sender is’, ‘Sender is a member of’, ‘Sender domain is’, ‘Recipient is’, ‘Recipient is a member of’, ‘Recipient domain is’, ‘Content contains sensitivity label’, and ‘Subject contains words’. As an example, you can now configure DLP policies such that if a user in your finance team is sending a labeled email on Outlook, the DLP engine will be able to analyze it and show the appropriate policy tip.
Currently these enhancements are available to E5 users in online mode with connected experiences turned on in Outlook settings. We will be making these capabilities available to Outlook on the web and other Office apps in the coming months. 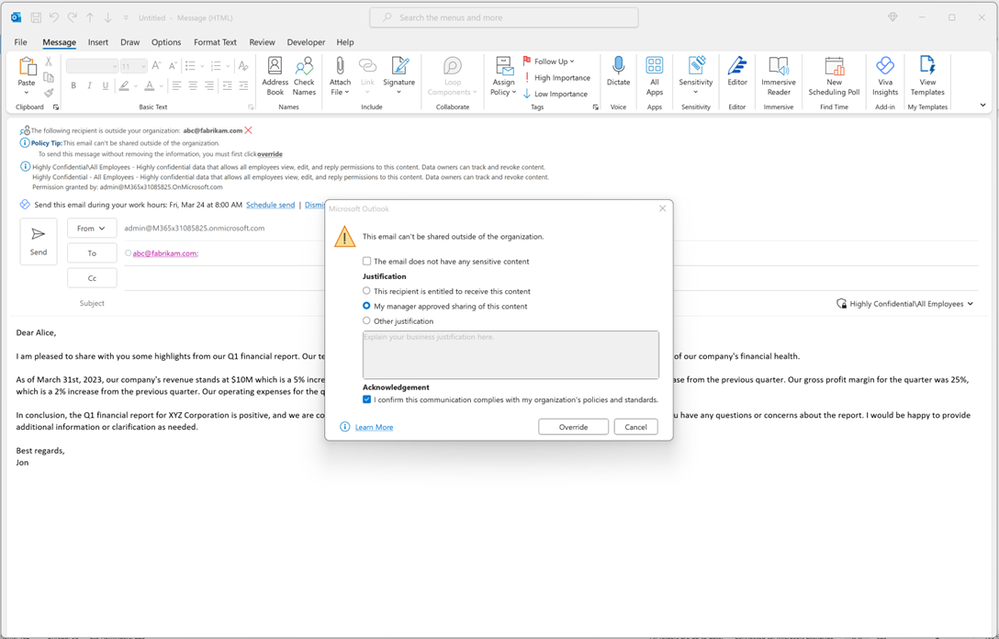
In addition to these public preview capabilities, we are also announcing the general availability of:
- Microsoft Purview Extension for Firefox to help organizations prevent sensitive data exfiltration while using the Firefox browser. With this capability users are automatically alerted when performing a risky action such as uploading a sensitive file to an unsanctioned application or printing sensitive content and are provided with actionable policy tips and remediation guidance. Learn more here.
- Contextual summary, including matched sensitive content and surrounding characters for DLP incidents and alerts for sensitive files on Windows endpoint devices. You can see the contextual evidence for Microsoft Office and PDF file matches on endpoint devices in the following places:
- In audit logs within activity explorer for DLP rule matches
- In the events details in DLP alerts page in the Microsoft Purview compliance portal
- In Microsoft 365 Defender portal as part of the DLP events details
Learn more here.
And finally, we have made enhancements (in public preview) to the Microsoft Purview DLP migration assistant for Symantec including
- checking if a SIT already exists before creating an identical SIT during the migration process,
- ability to include multiple keyword pairs in a DLP rule condition, and
- support for policy, file, and SIT names in additional languages such as Chinese, Japanese, Filipino, French, Spanish, German and more.
You can learn more about the migration assistant here and download it here.
Get started!
Get started today by turning on endpoint DLP as it is built into Windows 10 and 11 and doesn’t require an on-premises infrastructure or agent. Learn more about endpoint DLP here. You can try Microsoft Purview DLP and other Microsoft Purview solutions directly in the Microsoft Purview compliance portal with a free trial!
And don’t forget to watch the Microsoft Secure Breakout sessions - BRK31: Building out your data protection strategy and BRK32: Secure data with an intelligent and people-centric approach that showcase the new DLP capabilities.
Additional resources
- DLP whitepaper on moving from on-premises to cloud native DLP
- Uncover Hidden Risks podcast episode on adopting a cloud native DLP solution
- Mechanics video on how to create one DLP policy that works across your workloads
- Updated interactive guides on DLP policy configuration and management, and investigations
- Frequently asked questions on DLP for endpoints
- Guidance on optimal DLP incident management experience
- Investigating Microsoft Purview DLP alerts in Microsoft 365 Defender portal
- Latest announcements for Microsoft Purview Information Protection
And, lastly, join the Microsoft Purview DLP Customer Connection Program (CCP) to get information and access to upcoming capabilities in private previews in Microsoft Purview Data Loss Prevention. An active NDA is required. Click here to join.
We look forward to your feedback!
Thank you,
The Microsoft Purview Data Loss Prevention Team
[1] “Cyber Resilience”. May 2021, Microsoft Security Insider
[1] Survey of 297 DLP professionals at U.S. enterprise organizations, December 2022 by Concentrix, commissioned by Microsoft
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.