- Home
- Public Sector
- Public Sector Blog
- Microsoft CMMC Acceleration Program Update – January 2021
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
There is an update to this article found at:
https://aka.ms/CMMCAccelerationProgramUpdate
This article has been replaced by the update and will be removed shortly.
We are actively building out our program by developing resources for both partners and Defense Industrial Base (DIB) companies to leverage in their Cybersecurity Maturity Model Certification (CMMC) journey. These tools cannot guarantee a positive CMMC adjudication, but they may assist candidate organizations by improving their CMMC posture going into a formal CMMC review in accordance with CMMC Accreditation Body (AB) standards. While we plan to release resources and guidance in waves, please keep in mind we are dependent upon the CMMC AB finalizing the CMMC guidance itself.
Here is a summary of current resources to help get you started:
 Microsoft Product Placemat for CMMC
Microsoft Product Placemat for CMMC
The Microsoft Product Placemat for CMMC is an interactive view representing how Microsoft cloud products and services satisfy requirements for CMMC practices. The user interface resembles a periodic table of CMMC Practice Families. The default view illustrates the practices with Microsoft Coverage that are inherited from the underlying cloud platform. It also depicts practices for Shared Coverage where the underlying cloud platform contributes coverage for specific practices but requires additional customer configuration to satisfy requirements for full coverage. For each practice that aligns with Microsoft Coverage or Shared Coverage, verbal customer implementation guidance and practice implementation details are documented. This enables you to drill down into each practice and discover details on inheritance and prescriptive guidance for actions to be taken by the customer to meet practice requirements in the shared scope of responsibility for compliance with CMMC.
In addition to the default view, you may select and include products, features and suite SKUs to adjust how each cloud product is placed with CMMC. For example, you may select the Microsoft 365 E5 SKU for maximum coverage of CMMC where 18 of the CMMC practices are Microsoft Coverage and 74 practices are Shared Coverage. This is extraordinary as nearly 80% of the practices for CMMC Level 3 have coverage leveraging the spectrum of capabilities on the Microsoft cloud with the E5 SKU!
The Microsoft Product Placemat for CMMC is currently in public preview. You may download a copy at:
https://aka.ms/cmmc/productplacemat
Please share feedback at https://aka.ms/cmmc/productplacematfeedback.
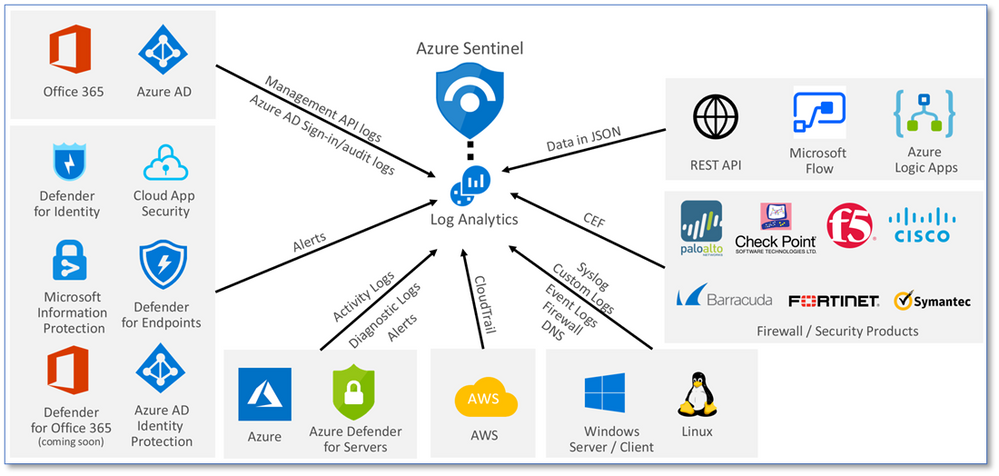
 Azure Sentinel: Cloud-Native SIEM
Azure Sentinel: Cloud-Native SIEM
See and stop threats before they cause harm, with SIEM reinvented for a modern world. Azure Sentinel is your birds-eye view across the enterprise. Put the cloud and large-scale intelligence from decades of Microsoft security experience to work. Make your threat detection and response smarter and faster with artificial intelligence (AI). Eliminate security infrastructure setup and maintenance, and elastically scale to meet your security needs—while reducing IT costs.
- Collect data at cloud scale—across all users, devices, applications, and infrastructure, both on-premises and in multiple clouds
- Detect previously uncovered threats and minimize false positives using analytics and unparalleled threat intelligence from Microsoft
- Investigate threats with AI and hunt suspicious activities at scale, tapping into decades of cybersecurity work at Microsoft
- Respond to incidents rapidly with built-in orchestration and automation of common tasks
Invest in security, not infrastructure setup and maintenance with the first cloud-native SIEM from a major cloud provider. Never again let a storage limit or a query limit prevent you from protecting your enterprise. Start using Azure Sentinel immediately, automatically scale to meet your organizational needs, and only pay for the resources you need.
For more information, please see https://azure.microsoft.com/en-us/services/azure-sentinel
Collect data at cloud scale—across all users, devices, applications, and infrastructure, both on-premises and in multiple clouds
 Azure Sentinel: CMMC Workbook
Azure Sentinel: CMMC Workbook
The Azure Sentinel CMMC Workbook provides a mechanism for viewing log queries aligned to CMMC controls across the Microsoft portfolio including Microsoft security offerings, Office 365, Teams, Intune, Windows Virtual Desktop and many more. This workbook enables Security Architects, Engineers, SecOps Analysts, Managers, and IT Pros to gain situational awareness visibility for the security posture of cloud workloads. There are also recommendations for selecting, designing, deploying, and configuring Microsoft offerings for alignment with respective CMMC requirements and practices.
Note: The Azure Sentinel CMMC Workbook is currently in Private Preview and will release in a Public Preview in early February 2021.
 Quickly deploy DoD STIG-compliant images and visualize compliance using Azure
Quickly deploy DoD STIG-compliant images and visualize compliance using Azure
At Microsoft, our security and compliance story is one of our greatest differentiators. Microsoft recognizes the criticality of security compliance accreditations for DIB and DoD customers. Maintaining Defense Information Systems Agency (DISA) Security Technical Implementation Guides (STIGs) compliance is critical and often time consuming. STIGs are secure configuration standards for installation and maintenance of DoD Information Assurance (IA) and IA-enabled devices and systems. Azure provides automation and compliance dashboarding capabilities at cloud speed and scale, allowing customers to reduce the heavy costs of compliance when they choose Azure.
The Azure Team has created sample solutions using first-party Azure tooling to deliver STIG automation and compliance reporting. The STIG Automation GitHub Repository, enables customers to: Automate STIG implementation and baseline updates with Azure Image Builder visualize compliance with Azure Monitor Log Analytics or Sentinel.
Available for use with Azure commercial today and coming soon to Azure Government. You can read more about the solution here: Quickly deploy DoD STIG-compliant images and visualize compliance using Azure.
Microsoft Compliance Manager with Assessment Templates
Compliance Manager
Microsoft Compliance Manager is a feature in the Microsoft 365 compliance center that helps you manage your organization’s compliance requirements with greater ease and convenience. Compliance Manager may help you throughout your compliance journey, from taking inventory of your apparent data protection risks to managing the complexities of implementing controls, staying current with regulations and certifications, and reporting to auditors.
Compliance Manager helps simplify compliance and reduces risk by providing:
- Pre-built assessments for common industry and regional standards and regulations, or custom assessments to meet your unique compliance needs.
- The Assessment Templates include NIST SP 800-171 and projected requirements for CMMC Levels 1-5.
- The Assessment Templates that are available to your organization depend on your licensing agreement. Review the details. HINT: You will need an E5 SKU.
- Workflow capabilities to help you efficiently complete your risk assessments through a single tool.
- Detailed step-by-step guidance on suggested improvement actions to help you comply with known CMMC standards and regulations that are most relevant for your organization. For actions that are managed by Microsoft, you’ll see implementation details and audit results.
- A projected risk-based compliance score to help you understand your compliance posture by measuring your progress in completing improvement actions.
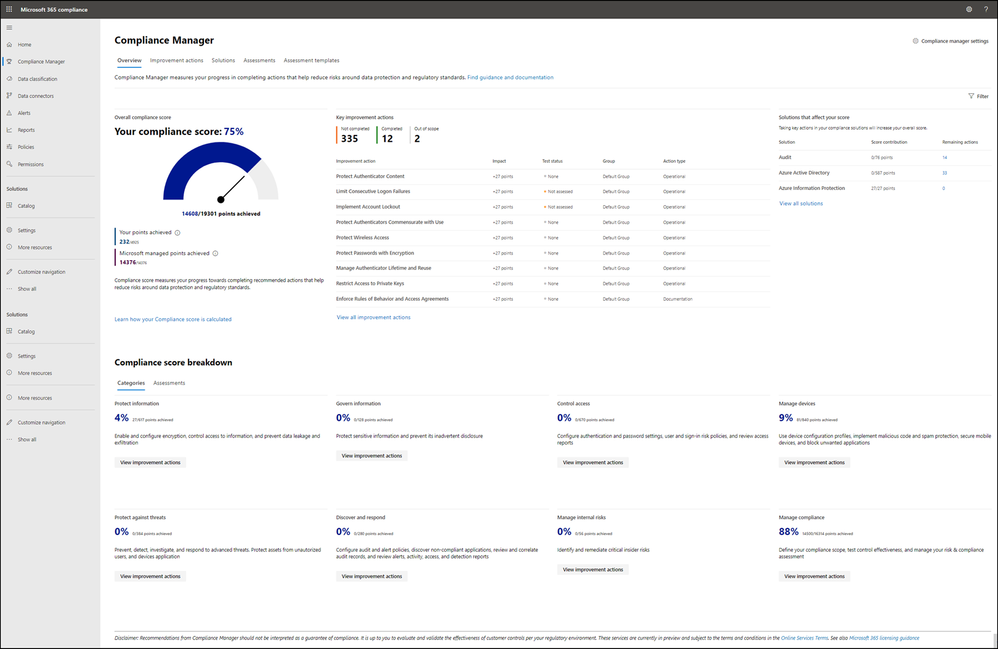
Your Compliance Manager dashboard shows your current projected CMMC compliance score, helps you see what needs attention, and guides you to key improvement actions. Below is an example of what your Compliance Manager dashboard will look like:
Please note, the Compliance Manager dashboard is a projection of your organization’s CMMC compliance profile based on all available information to date—Microsoft is not an accrediting body under the CMMC, and thus cannot guarantee any outcome under the formal CMMC review process.
Understanding your compliance score
Compliance Manager awards you points for completing improvement actions taken to comply with a regulation, standard, or policy, and combines those points into an overall compliance score. Each action has a different impact on your score depending on the potential risks involved. Your compliance score helps you prioritize which actions to focus on to improve your overall compliance posture.
Compliance Manager gives you an initial score based on the Microsoft 365 data protection baseline. This baseline is a set of controls that includes key regulations and standards for data protection and general data governance.
 Compliance Manager Availability in GCC and GCC High
Compliance Manager Availability in GCC and GCC High
The Compliance Manager is now available in all Microsoft 365 cloud offerings, including GCC and GCC High!
However, the Secure Score feature is still in preview within Commercial and GCC. Secure Score will not release in GCC High until it becomes Generally Available. As a result, automated testing does not work in GCC High. GCC High customers will need to manually implement and test their improvement actions in the Compliance Manager. For more information, please see Settings for automated testing and user history.
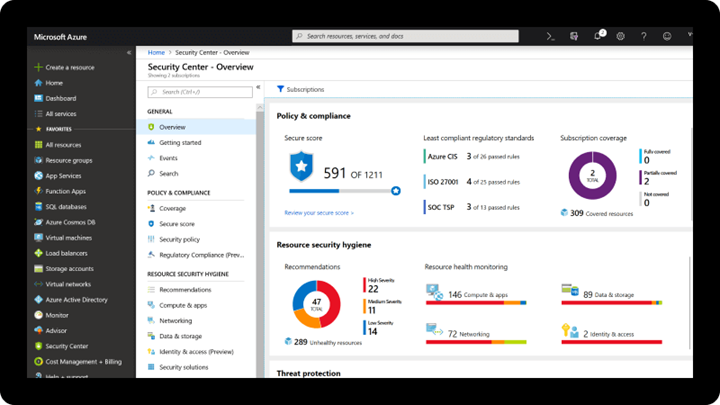
Azure Security Center with Azure Blueprints
Azure Security Center
Microsoft uses a wide variety of physical, infrastructure, and operational controls to help secure Azure, but there are additional actions you need to take to help safeguard your workloads. You may turn on the Azure Security Center to strengthen your cloud security posture:
- Assess and visualize the security state of your resources in Azure, on-premises, and in other clouds with Azure Secure Score;
- Simplify enterprise compliance and view your compliance against regulatory requirements such as NIST SP 800-171 and CMMC;
- Protect all your hybrid cloud workloads with Azure Defender, which is integrated with Security Center; and
- Use AI and automation to cut through false alarms, quickly identify threats, and streamline threat investigation.
You may assess the security state of all your cloud resources, including servers, storage, SQL, networks, applications, and workloads that are running in Azure, on-premises, and in other clouds. This includes the ability to visualize your security state and improve your security posture by using Azure Secure Score recommendations. You may view your compliance against a wide variety of regulatory requirements or company security requirements by centrally managing security policies to perform ongoing assessment and get rich, actionable insights and reports to simplify compliance.
Note: The Azure Security Center is available today in both Commercial and in Azure Government.
Azure Blueprints
Just as a blueprint allows an engineer or an architect to sketch a project's design parameters, Azure Blueprints enables cloud architects and central information technology groups to define a repeatable set of Azure resources that implements and adheres to an organization's standards, patterns, and requirements. Azure Blueprints makes it possible for development teams to rapidly build and stand up new environments with trust they're building within organizational compliance with a set of built-in components, such as networking, to speed up development and delivery.
Blueprints are a declarative way to orchestrate the deployment of various resource templates and other artifacts such as:
- Role Assignments
- Policy Assignments
- Azure Resource Manager templates (ARM templates)
- Resource Groups
The Azure Blueprints service is designed to help with environment setup. This setup often consists of a set of resource groups, policies, role assignments, and ARM template deployments. A blueprint is a package to bring each of these artifact types together and allow you to compose and version that package, including through a continuous integration and continuous delivery (CI/CD) pipeline. Ultimately, each is assigned to a subscription in a single operation that can be audited and tracked.
With Azure Blueprints, the relationship between the blueprint definition (what should be deployed) and the blueprint assignment (what was deployed) is preserved. This connection supports improved tracking and auditing of deployments. Azure Blueprints can also upgrade several subscriptions at once that are governed by the same blueprint.
 Azure Policy and Blueprint Sample for CMMC Level 3
Azure Policy and Blueprint Sample for CMMC Level 3
An Azure Policy and Blueprint allows organizations to easily establish compliant environments. Azure Policy is implemented via a centrally managed policy initiative that helps ensure cloud compliance, avoid misconfigurations, and practice consistent resource governance. An Azure blueprint simplifies large scale Azure deployments by packaging key artifacts such as policy initiatives, Azure Resource Manager (ARM) templates, and role-based access controls.
A new Azure policy initiative and blueprint sample for CMMC Level 3 are currently in development. The CMMC policy initiative builds upon the existing NIST SP 800-171 policy initiative/blueprint sample with the addition of 110 new policies. Any relevant new policies will be back-ported into the NIST SP 800-171 sample after the CMMC sample is finalized.
The CMMC policy initiative and blueprint sample is currently in Private Preview. It will transition to Public Preview in February 2021 with availability in both Azure Commercial and Government clouds.
Compliance Manager and the Azure Security Center
You may observe there are two different compliance tools depending on the use of Microsoft 365 or Microsoft Azure. While there are currently two different tools, they are not mutually exclusive in use. Holistic compliance with CMMC requires the use of both the Compliance Manager and the Azure Security Center. You deploy the Compliance Manager with the Assessment Template for CMMC for coverage of Microsoft 365 products and features, such as Office 365 and Enterprise Mobility & Security. Generally speaking, this includes coverage for most SaaS offerings. You will also want to deploy the Azure Security Center with the Azure Blueprint sample for CMMC (roadmap) for coverage of Azure IaaS and PaaS offerings. We are working on integration between the two tools along with integration with Azure Sentinel in the future roadmap. In the meantime, you will need to leverage both panes of glass for CMMC compliance.
Zero Trust Architecture with Azure Blueprints
Zero Trust Architecture
Today, many of our customers in regulated industries are adopting a Zero Trust architecture - moving to a security model that more effectively adapts to the complexity of the modern environment, embraces the mobile workforce, and protects people, devices, applications, and data wherever they’re located.
Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.” In a Zero Trust model, every access request is strongly authenticated, authorized within policy constraints, and inspected for anomalies before granting access. This approach aids the process of achieving compliance for industries that use NIST-based controls including the DIB and government.
A Zero Trust approach should extend throughout the entire digital estate and serve as an integrated security philosophy and end-to-end strategy, across three primary principles: (1) verify explicitly, (2) enforce least privilege access, and (3) assume breach.
 Azure blueprint for the Azure Security Benchmark Foundation
Azure blueprint for the Azure Security Benchmark Foundation
We have developed a GitHub Repo for an Azure Blueprint sample enabling Configuration-as-Code for Azure subscriptions. The Azure Blueprint for Azure Security Benchmark Foundation (formerly “Zero Trust”) enables application developers and security administrators to more easily create hardened environments for their application workloads. Essentially, the blueprint will help you implement Zero Trust controls across six foundational elements: identities, devices, applications, data, infrastructure, and networks.
Using the Azure Security Center and Azure Blueprints service, the blueprint sample will first configure your VNET to deny all network traffic by default, enabling you to extend it and/or set rules for selective traffic based on your business needs. In addition, the blueprint enforces and maintains Azure resource behaviors and configuration in compliance with specific NIST SP 800-53 security control requirements using Azure Policy.
The blueprint includes Azure Resource Manager templates to deploy and configure Azure resources such as Virtual Network, Network Security Groups, Azure Key Vault, Azure Monitor, Azure Security Center, and more. If you’re working with applications that need to comply with FedRAMP High or DoD Impact Level 4 requirements or just want to improve the security posture of your cloud deployment, the blueprint for Zero Trust is designed to help you get there faster.
The ASBF blueprint is currently in preview with limited support. To learn more and find instructions to deploy into Azure, see the ASBF repo. For more information, questions, and feedback, please contact us at ASBF feedback.
We are also working on updates in support of NIST SP 800-171 and CMMC for availability in the first half of calendar year 2021.
CMMC Documentation
CMMC Compliance Documentation
There are several artifacts we are working on for release this year 2021, to include:
- SSP: System Security Plan with customer scope of responsibility detailed
- CIS: Control Implementation Summary per environment (IaaS, PaaS and SaaS)
- SAR: Security Assessment Report from Microsoft’s C3PAO engagement
- Documented auditor observations based on pre-defined tenant configuration
Microsoft Cybersecurity Reference Architecture
The Microsoft Cybersecurity Reference Architecture (MCRA) describes Microsoft’s cybersecurity capabilities and how they integrate with existing security architectures. We have seen this document used for several purposes by our customers to include:
- Starting template for a security architecture - The most common use case we see is that organizations use the document to help define a target state for cybersecurity capabilities. Organizations find this architecture useful because it covers capabilities across the modern enterprise estate that now spans on-premises, mobile devices, many clouds, and IoT / Operational Technology.
- Comparison reference for security capabilities - We know of several organizations that have marked up a printed copy with what capabilities they already own from various Microsoft license suites (many customers don't know they own quite a bit of this technology), which ones they already have in place (from Microsoft or partner/3rd party), and which ones are new and could fill a need.
- Learn about Microsoft capabilities - In presentation mode, each capability has a "ScreenTip" with a short description of each capability + a link to documentation on that capability to learn more.
- Learn about Microsoft's integration investments - The architecture includes visuals of key integration points with partner capabilities (e.g. SIEM/Log integration, Security Appliances in Azure, DLP integration, and more) and within our own product capabilities among (e.g. Advanced Threat Protection, Conditional Access, and more).
- Learn about Cybersecurity - We have also heard reports of folks new to cybersecurity using this as a learning tool as they prepare for their first career or a career change.
The Microsoft Cybersecurity Reference Architecture is available here. Additional training resources are available here.
An update will be released early this year 2021 to include the branding updates announced at Ignite 2020. Most notably, the use of the Microsoft Defender branding will be incorporated in the update to MCRA.
Microsoft Blog Posts on CMMC
- Accelerating CMMC compliance for Microsoft cloud (in depth review)
- CMMC Blog Series
- Access Control Maturity
- Audit & Accountability Maturity
- Asset & Configuration Management Maturity
- Identification & Authentication Maturity
- Incident Response Maturity
- Maintenance & Media Protection Maturity
- Recovery & Risk Management Maturity
- Security Assessment & Situational Awareness Maturity
- System & Communications Protection Maturity
- System & Information Integrity Maturity
Program Scaffolding for Managed Service Providers
Behind the scenes, we are actively working with our partner community, and in particular the Managed Service Providers (MSP), to deliver scaffolding in the construction of CMMC offerings. The CMMC Acceleration Program is comprised of many different components as described above, and several that are yet unannounced. The intent is to provide building blocks, or what we call “scaffolding”, to our partners in support of their CMMC offers. Our partners will be enabled in our partner marketplace with advance specializations for CMMC and their concentration on the Defense Industrial Base. In alignment with the commitments made in our original CMMC Announcement, our MSP partners will implement reference architectures and compliance solutions for CMMC.
Into the Future
Microsoft is actively engaged with customers, partners, the CMMC Accreditation Body, and multiple industry working groups to refine what resources we should develop and make available as part of the CMMC Acceleration Program. We have many grand ideas, and welcome to feedback from the community at large. Please fill out this short survey to join our CMMC feedback loop if you are interested in learning more about the program.
For general comments on the CMMC Acceleration Program: Contact Us
Appendix
Please follow me here and on LinkedIn. Here are my additional blog articles:
Blog Title |
Aka Link |
|
Accelerating CMMC compliance for Microsoft cloud (in depth review) |
|
|
Updated! Microsoft CMMC Acceleration Program Update – January 2021 (This One) |
|
|
History of Microsoft Cloud Service Offerings leading to the US Sovereign Cloud for Government |
|
|
Gold Standard! Understanding Compliance Between Microsoft 365 Commercial, GCC, GCC-High and DoD Offerings |
|
|
The Microsoft 365 Government (GCC High) Conundrum - DIB Data Enclave vs Going All In |
|
|
Microsoft US Sovereign Cloud Myth Busters - A Global Address List (GAL) Can Span Multiple Tenants |
|
|
Microsoft US Sovereign Cloud Myth Busters - A Single Domain Should Not Span Multiple Tenants |
|
|
Microsoft US Sovereign Cloud Myth Busters - Active Directory Does Not Require Restructuring |
|
|
Microsoft US Sovereign Cloud Myth Busters - CUI Effectively Requires Data Sovereignty |
|
|
New! Microsoft expands qualification of contractors for government cloud offerings |
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.