- Home
- Public Sector
- Public Sector Blog
- April 2023 - Microsoft 365 US Public Sector Roadmap Newsletter
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Newsworthy Highlights |
What’s New in Microsoft Teams at Enterprise Connect 2023
SIP Gateway is now available for Government Community Cloud customers to enable core Teams calling functionality on legacy devices. For organizations with investment in SIP devices, SIP Gateway provides calling, meeting dial-in, voicemail and other core telephony features.
FedMake Focus on Civilian Government: Solutions Show & Share
FedMake attendees often say the most valuable outcome is connecting with their peers to explore and share their experiences and approaches to solving common unmet challenges. Join us in-person at the Reston Garage or remotely from your computer, to see the solutions developed using the Power Platform during that week's FedMake event. Share your own experiences, ask questions, and meet your peers.
FedMake Focus on Civilian Government: Meeting Missions with No/Low Code
Microsoft’s Power Platform empowers everyone to be a maker. Those who understand a challenge best are the same people best equipped to solve them. Until now programming languages and coding experience have stood in the way of creating sophisticated and effective solutions. The Power Platform toolset brings this power to all. Microsoft is uniquely positioned to help you meet your mission by leveraging your existing investments.
Viva Insights in DoD and GCC High environments
We’re excited to announce that Viva Insights with personal insights has rolled out to the Department of Defense (DoD) and Government Community Cloud High (GCC High) environments.
Viva Insights in DoD and GCC High environments
We’re excited to announce that Viva Insights with personal insights has rolled out to the Department of Defense (DoD) and Government Community Cloud High (GCC High) environments.
Conversational Bots and Message Extensions are now available in DOD
To bring full functionality of Microsoft Teams Platform into DOD, we are very excited to announce the availability of Conversational Bots and Message Extensions in DOD, as a Line of Business (LOB) app. Please note that Third-Party (3P) and calling and meeting apps are not available as a part of this release.
Microsoft Federal Successfully Completes Voluntary CMMC Assessment
Microsoft is demonstrating its continued commitment to U.S. Department of Defense (DoD) and the Defense Industrial Base (DIB) by announcing its successful completion of a DCMA (Defense Contract Management Agency) Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) Joint Surveillance Voluntary Assessment Program (JSVAP). Microsoft operates its US Federal business out of the GCC-H and Azure Government cloud. We leverage the same security and monitoring suite available to all our customers in this environment. DIBCAC and Redspin, a Certified 3rd Party Assessment Organization (C3PAO), completed their assessments and awarded Microsoft with a perfect 110-point score. This DIBCAC High certificate will be converted into a Cybersecurity Maturity Model Certification (CMMC) Level 2 accreditation as federal rulemaking allows.
Microsoft 365 Government Community Call
Join Jay Leask and other members of the Government Community live on LinkedIn!
Where to Start with Microsoft Teams Apps in Gov Clouds
Customers in our Office 365 government clouds, GCC, GCCH, and DoD, are continuing to evolve how they do business in the hybrid workplace. As Microsoft Teams is the primary tool for communication and collaboration, customers are looking to improve productivity by integrating their business processes directly into Microsoft Teams via third-party party (3P) applications or line-of-business (LOB)/homegrown application integrations.
Microsoft 365 Government Adoption Resources
Empowering US public sector organizations to transition to Microsoft 365
Release News |
SharePoint Server 2019 and SharePoint Designer workflows are now supported on SharePoint Migration T...
SAM is a M365 add on license SKU that provides a suite of features designed to significantly enhance...
Users will have the ability to add pronouns to their profile card – GCC & GCCH April 11, DoD May
Changes in Get-CsTenant in Teams PowerShell Module
Authorized users can change call queue and auto attendant greetings and announcements
The new landing experience offers expanded navigational tools between Viva apps and acts as the home...
Simulation mode for retention & auto-labeling policies is now in Public Preview
References and Information Resources |
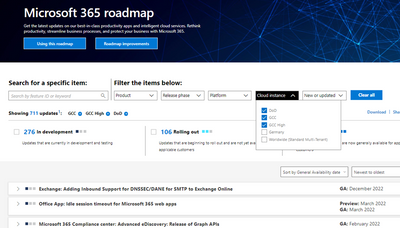
Microsoft 365 Public Roadmap
This link is filtered to show GCC, GCC High and DOD specific items. For more general information uncheck these boxes under “Cloud Instance”.
Stay on top of Microsoft 365 changes
Here are a few ways that you can stay on top of the Office 365 updates in your organization.
Microsoft Tech Community for Public Sector
Your community for discussion surrounding the public sector, local and state governments.
Microsoft 365 for US Government Service Descriptions
· Office 365 Platform (GCC, GCCH, DoD)
· Office 365 U.S. Government GCC High endpoints
· Office 365 U.S. Government DoD endpoints
· Microsoft Purview (GCC, GCCH, DoD)
· Enterprise Mobility & Security (GCC, GCCH, DoD)
· Microsoft Defender for Endpoint (GCC, GCCH, DoD)
· Microsoft Defender for Cloud Apps Security (GCC, GCCH, DoD)
· Microsoft Defender for Identity Security (GCC, GCCH, DoD)
· Azure Information Protection Premium
· Exchange Online (GCC, GCCH, DoD)
· Office 365 Government (GCC, GCCH, DoD)
· Power Automate US Government (GCC, GCCH, DoD)
· Outlook Mobile (GCC, GCCH, DoD)
Be a Learn-it-All |
|
Public Sector Center of Expertise We bring together thought leadership and research relating to digital transformation and innovation in the public sector. We highlight the stories of public servants around the globe, while fostering a community of decision makers. Join us as we discover and share the learnings and achievements of public sector communities. |

|
|
Microsoft Teams for US Government Adoption Guide
|

|
|
|
|
Message Center Posts and Updates for Microsoft Teams in GCC |
Looking for what’s on the map for Microsoft Teams and only Teams in GCC?
Go right to the GCC Teams Feature Communications Guide
Message Center Highlights |
Microsoft 365 Copilot
MC528800 — Announcing Microsoft 365 Copilot
TBD
Today we announced Microsoft 365 Copilot – new experience that combines the power of large language models with your data in the Microsoft Graph and the Microsoft 365 apps. Copilot is integrated into Microsoft 365 in two ways. First, it works alongside the user, embedded in Word, Excel, PowerPoint, Outlook, Teams, and more. Second, we’ve also introduced Business Chat that works across all Microsoft 365 apps and data in real-time: user’s calendar, emails, chats, documents, meetings, and contacts.
How this will affect your organization:
Integrated into Microsoft 365, Copilot automatically inherits all of your company’s security, compliance, identity, and privacy policies and processes. Two-factor authentication, compliance boundaries, privacy protections, and more make Copilot the AI solution you can trust. Copilot works only with content to which your users already have permission to access.
Today’s announcement does not impact any Azure Active Directory (AAD) users in your organization, as the new features are currently only available to a limited set of commercial customers through a Private Preview program.
As these services become more broadly available, we will be providing admins with an advance notice and technical documentation about available controls and policies.
What you need to do to prepare:
There is nothing you need to do at this time. As soon as the additional roll out dates are ready to be announced, we will inform you through the Message Center in the Microsoft 365 admin center. You can also follow these features on Microsoft 365 public roadmap website.
Learn more about other technical details in this blog.
SharePoint Online / OneDrive for Business
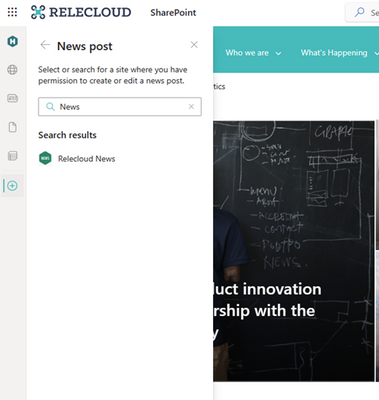
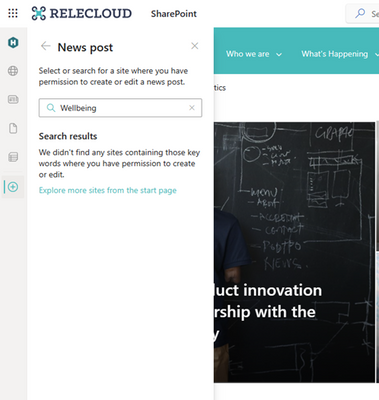
MC535266 — (Updated) SharePoint: Create Pages and News from the SharePoint app bar
30-60 Days
Microsoft 365 Roadmap ID 98143
Updated April 4, 2023: We have updated the rollout timeline below. Thank you for your patience.
With this update, users will soon be able to start creating pages and news as an action from the SharePoint app bar. This means that no matter where users are in SharePoint, they can jump right into the creation process and stay in the flow of work.
When this will happen:
Targeted Release: We will begin rolling out in mid-April (previously early April) and expect rollout to be complete by late April (previously mid-April).
Standard Release: We will begin rolling out in early May (previously late-April) and expect rollout to be complete by late May (previously mid-May).
How this will affect your organization:
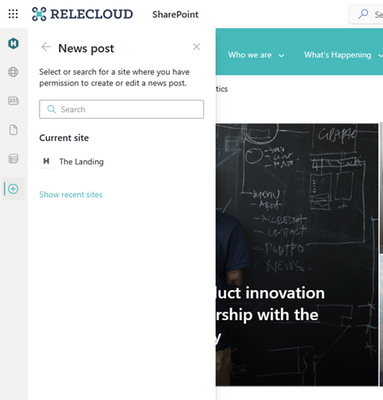
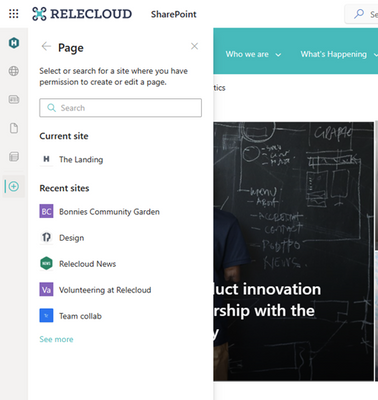
This new feature allows users to create pages and news from the SharePoint app bar. Users will be able to select the Create command on the app and then select an option from SharePoint News post or SharePoint page, in addition to the SharePoint sites, Microsoft Lists or the Office files (Word, PowerPoint, Excel, OneNote) that are currently available.
As a user creates pages and news posts from the panel, they will be prompted to select a destination where they want to create the page or news post.
- Current site: If users are on a SharePoint site when launching the Create command from the app bar, the service will verify that the user has permission to edit before displaying the site.
- Recent sites: Users can select Recent Sites to see sites where they have edit permissions to create a page or news post.
- Search for a site: Users can search for a site to create a page or news post. If no sites were found matching the query where the user has edit permissions, they'll be guided to explore sites on the start page.
What you need to do to prepare:
You do not need to do anything to prepare. The SharePoint app bar cannot be customized. If you haven't already enabled and customized global navigation in the SharePoint app bar, it's highly recommended that you do so to take advantage of the best navigational experience for end users.
Visit this page to learn more on the SharePoint app bar.
MC533812 — Recent SharePoint admin actions
Rolled Out
Microsoft 365 Roadmap ID 117553
We are delighted to announce a new feature release for the SharePoint admin center. With the recent actions panel, you can track progress of site setting changes you made from the Active sites page. A premium version of this feature is offered as part of Microsoft Syntex - SharePoint Advanced Management. The premium version allows you to review your most recent actions in the SharePoint admin center up to the last 30 days. Starting in the beginning of March, this feature will be rolled out to all organizations. You can try this feature by selecting “Your recent actions” on the Active Sites page in the SharePoint admin center. Please refer to the below documentation for more details about the feature:
When this will happen:
Standard release: This feature is now available.
How this will affect your organization:
Admins can use this feature to get a quick overview of the most recent actions performed by them in the SharePoint admin center, within the current session.
What you need to do to prepare:
There is no work required to prepare for this feature release. If you want to try the premium version of the feature, you need to buy the Microsoft Syntex – SharePoint Advanced Management license.
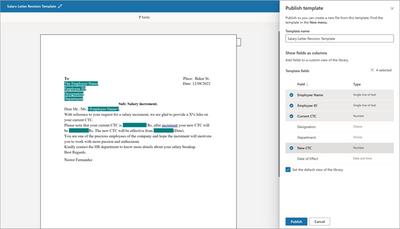
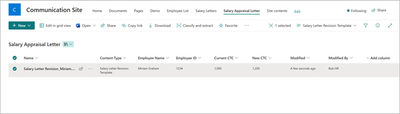
MC533807 — Microsoft Syntex: Content Assembly - Choose Fields in Modern Templates to Create Document Library Columns
<30 Days
Microsoft 365 Roadmap ID 98126
We will be rolling out the ability to map fields of a modern template to library columns in Microsoft Syntex Content Assembly.
When this will happen:
Targeted Release: Rollout is expected to start in mid-March and is expected to be complete by late March 2023.
Standard Release: Rollout is expected to start in late March and is expected to be complete by early April 2023.
How this will affect your organization:
Users will see a new “Select from managed metadata term set/term” option as an input source while creating placeholders in modern templates.
When users select the Publish option to publish a modern template after creating the necessary fields, they can now choose to add some or all of the created fields into a custom view of the library.
Now when users generate documents from the modern template, the values against the mapped fields will automatically start showing up in the library view.
Before this update, users had to train and build AI models to extract the information already configured as fields while publishing modern templates. With this feature, all the relevant metadata for your generated documents will be automatically available as columns in your document library.
What you need to do to prepare:
You may want to notify users about this new capability and update your training and documentation as appropriate.
MC531214 — SharePoint: Improving the Page Authoring Experience
30-60 Days
Microsoft 365 Roadmap ID 117376 and 117377
We are releasing new improvements to the Page authoring experience in SharePoint. These new improvements should help reduce clutter, increase productivity, and add more value for users when editing a page.
When this will happen:
We will begin rolling out in late-March and expect to complete rollout by late June.
How this will affect your organization:
The new updates will include:
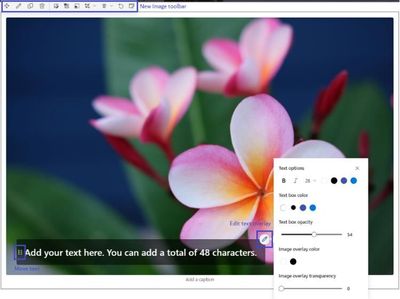
- Surfacing the layout options in the web part toolbars, including in Quick Links, Events, People, Hero, News, and Title Region
- Moving the “add section” action to be inline on canvas and visible on hover
- Introducing a consolidated and enhanced Image web part toolbar
- Adding new text overlay capabilities in the Image web part, such as the ability to change positions, text size and styling, text box color and opacity, and image overlay color and transparency.
What you need to do to prepare:
There is nothing you need to do at this time.
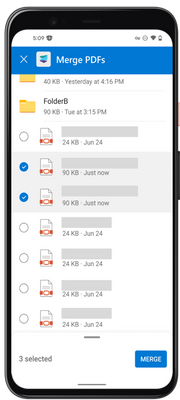
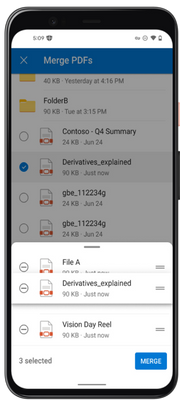
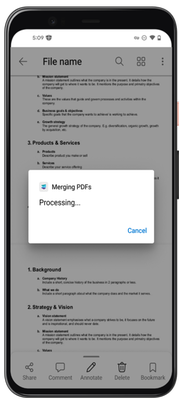
MC530467 — Microsoft Syntex: Combine Two or More PDF Files with Merge PDFs action in OneDrive for Android and for iOS
30-60 Days
This post is associated with Microsoft Roadmap ID 117547, 117549
Microsoft Syntex users can soon combine PDF files into one PDF file with the Merge PDFs action in OneDrive for Android and iOS. The Merge PDFs action lets you quickly combine multiple PDF files into a new PDF file stored in SharePoint or OneDrive.
When this will happen:
Standard release for Android: We will begin rolling out in late-March and expect to complete rollout by mid-April.
Standard release for iOS: We will begin rolling out in late April and expect to complete rollout by late May.
How this will affect your organization:
Syntex users won’t have to worry about organizing, sharing or sending multiple PDF files. Integrating multiple PDFs into a large PDF file lets users better organize and send information they want to view or share with others.
To combine multiple PDF files in Syntex using the Merge PDFs action:
- Open a PDF file you want to combine in OneDrive for Android or iOS.
- At the bottom of the screen, tap the horizontal bar or drag the bottom menu up to expand the new menu.
- Under File actions, select Merge PDFs.
- Choose the PDF file(s) you want to combine with.
- Users can wipe up the menu and organize the files order they want in the merged PDF and tap Merge PDFs.
- Select a location to save the merged PDF.
- After selection, Your PDFs will turn into merging process.
- After the new PDF is done processing, your new file will be opened directly.
Note: Some users may see this feature before others within your organization. PDF Merge is available only for Microsoft Syntex licensed users; users without a Syntex license will not see the feature. We will bring the capability to other clients, including OneDrive, SharePoint and Syntex browsers soon.
What you need to do to prepare:
You may want to notify your users about this new capability and update your training and documentation as appropriate.
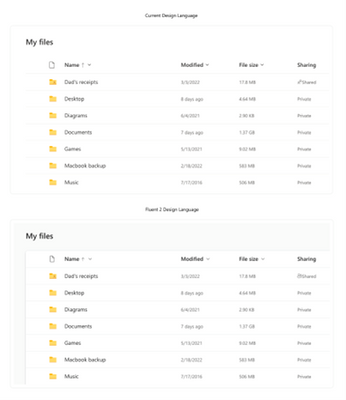
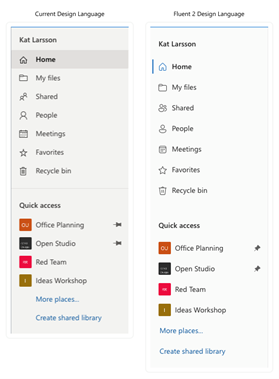
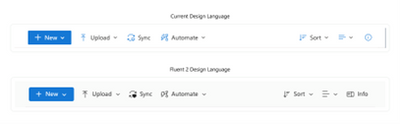
MC530466 — Updating the look and feel of OneDrive
<30 Days
We’re making a small set of visual updates to OneDrive to help align the product with the latest iteration of Microsoft’s design language. Microsoft uses the Fluent design system to ensure a cohesive and accessible design for all Microsoft products and users.
When this change is released, you will notice an updated color palette, refreshed icons, increased opacity for drop shadows, and rounded corners for square graphical elements.
When will this happen:
- We will begin rolling this out to Targeted Release customers in late March.
- We will begin rolling this out to Standard Release customers in early April.
- We expect the rollout to be completed by the mid-April.
How this will affect your organization:
This update will make slight visual changes to OneDrive. These small changes are designed to increase usability and accessibility.
Here’s a before-and-after look at some of these changes:
Files Container
Left Navigation
Command Bar
What you need to do to prepare:
You may consider updating your training and documentation as appropriate.
Learn more about Microsoft’s Fluent design system.
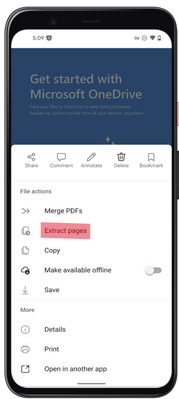
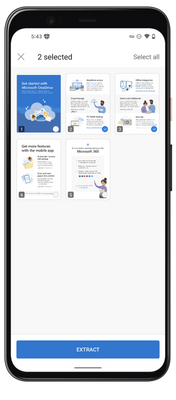
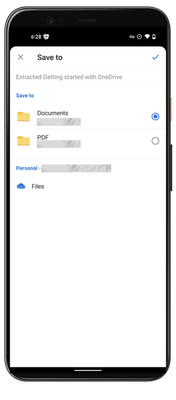
MC529434 — Microsoft Syntex: Split PDF Pages into new PDF files with the Extract action in OneDrive for iOS
30-60 Days
Microsoft 365 Roadmap ID 117548
Users of Microsoft Syntex can soon split a PDF file into multiple PDFs with the Extract file action in OneDrive for iOS. The Extract file action lets you quickly split and extract multiple pages of a PDF into a new PDF file stored in SharePoint or OneDrive.
When this will happen:
We will begin rolling out in late April and expect to complete rollout by late May.
How this will affect your organization:
Syntex users won’t have to worry about sharing unnecessary information from a large PDF file. Splitting a large PDF file into multiple, smaller files lets users tailor the information they want to view or share with others.
To split a PDF file in Syntex using the Extract action:
- Open the PDF file you want to split in OneDrive for iOS.
- At the bottom of the screen, tap the horizontal bar or drag the bottom menu up to expand the new menu.
- Under File actions, select Extract.
- Choose the page(s) you want to separate and tap Extract.
- Select a location to save the extracted PDF.
- After the new PDF is done processing, a Your PDF is ready banner will appear at the bottom of the screen. Tap Open from the banner to access your new file.
Note: Some users may see this feature before others within your organization. PDF extraction is available only for Microsoft Syntex licensed users; users without a Syntex license will not see the feature. We will bring the capability to other clients, including OneDrive, SharePoint and Syntex browsers soon.
What you need to do to prepare:
There is nothing you need to do to prepare for this feature. You may want to notify your users about this new capability and update your training and documentation as appropriate.
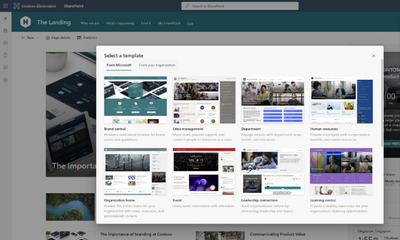
MC529412 — New SharePoint site templates
<30 Days
Microsoft 365 Roadmap ID 117554
We are introducing 3 new SharePoint site templates dedicated to helping you create sites for your portal home site, to provide guidance and assets for your brand, and a template powered by Microsoft Syntex for your Accounts payable team.
- Our new organization home site template you can quickly get started with a basic SharePoint portal destination for your organization.
- The new brand central template creates a destination for your organization to showcase and guide others through the use of your brand.
- With the Microsoft Syntex powered accounts payable template, you can learn more about how Syntex works and be able to get started right away. This template also comes with a prebuilt tutorial and some established models designed to help your team get started with Microsoft Syntex. (Syntex Roadmap ID 103607)
When this will happen:
Targeted Release: We will begin rolling out at the end of March.
Standard Release: We will begin rolling out in early April and complete in mid-April.
How this will affect your organization:
Users will be able to benefit from the ability to browse, preview, and apply site templates to a new or existing SharePoint site. Users can select a site template that meets organizational business objectives and best fits the site goal while ensuring a higher level of consistency throughout their organization. They can then review pre-populated content and customize the site to address their needs. This feature will be on by default with no admin control.
To apply a template to an existing site: Users can choose to browse site templates and can apply a template to an existing site at any time by accessing the template gallery from Settings and then select Apply a site template.
To apply a template to a new site: If a site owner is visiting their new site for the first time, they may see a message asking if they want to use a template that will then take them to the template gallery.
Choose desired template.
Communication site templates:
Organization home – serves as the home page for your organization and provides visitors with news, conversations, videos, and updates centered around your organization, along with easy access to popular links and important resources.
Brand central – is the central hub where employees can access the latest brand assets and guidelines for your organization, understand brand principles and values, see examples of brand expression in action, and get help with brand related questions.
Team site templates:
Accounts payable – where employees can manage, process, and track purchase orders, extract key information from invoices using a prebuilt invoice model, then use the preconfigured document libraries provided to store everything.
What you need to do to prepare:
Share this template guide with end-users: Learn how to apply and customize SharePoint site templates.
MC526130 — New Tenants as of March 31 will have Azure B2B Integration with SharePoint enabled by Default
Rolled Out
We're making some changes to the default configuration for new tenants for Azure B2B integration with SharePoint & OneDrive.
When this will happen:
Starting March 31, 2023, new tenants will have Azure B2B Integration with SharePoint & OneDrive enabled by default.
How this will affect your organization:
This message is for your information and there is no impact to existing tenants or tenants created before March 31, 2023.
What you need to do to prepare:
No change is needed for existing customers. New tenants can opt out of using Azure B2B Integration using the SharePoint Online Management Shell.
Please click Additional Information to learn more.
MC525664 — Renaming File viewer webpart to 'File and Media'
<30 Days
We are renaming file viewer webpart to 'File and Media' to make this webpart inclusive of more file types like videos.
When this will happen:
Standard Release: We will begin rolling out in mid-March and expect to complete rollout by mid-April 2023.
How this will affect your organization:
Users will see the new name for the webpart. Functionally, nothing changes w.r.t. the capabilities of the webpart. This is a step to educate users about the capabilities of the webpart beyond Word, Excel, PowerPoint, PDF and extended to videos as well.
MC525663 — (Updated) SPO Site Sharing will now use Azure B2B Invitation Manager
30-60 Days
Microsoft 365 Roadmap ID 117557
Updated March 21, 2023: We have updated the content for clarity. Thank you for your patience.
We are updating the SharePoint Online Site Sharing backend to use Azure B2B Invitation Manager instead of the legacy SharePoint Invitation Manager.
When this will happen:
This change will begin rolling out in late March, and complete rollout by late May (previously late April).
How this will affect your organization:
Today, sharing just the SharePoint site goes through the original SharePoint Invitation Manager which always creates guest users in your organization's directory. We are now updating this flow & experience to use the Azure B2B Invitation Manager instead. The sharing flow will remain identical to what users see today, but external recipients will now go through your organization's B2B Invitation Manager experience.
Note: This change will only impact sharing of sites. Users who share files or folders will continue to receive the same experience they have today.
What you need to do to prepare:
You may want to review your Azure B2B Invitation Manager policies.
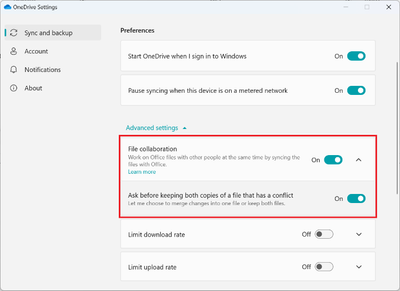
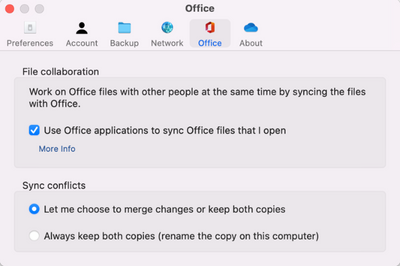
MC525659 — Updates to Office File Collaboration Settings on Windows and macOS
<30 Days
We have an update to the OneDrive sync app advanced settings for Office file collaboration.
Previously, two toggles were shown to allow users to opt out of Office file collaboration and decide on how to handle conflicts. After this change, users will no longer see these toggles and will be opted-in by default to avoid sync conflicts.
- File collaboration: This setting allows users to collaborate on and sync documents with Microsoft Office. Moving forward, this setting be hidden for users who have it enabled, which is the existing default behavior. If a user previously disabled the setting, they will see the toggle, allowing them to turn it back on.
- Handling conflicts: This setting manages how sync conflicts are handled. Moving forward, this setting will be enabled by default and hidden.
When will this happen:
Standard Release: We will begin rolling out in late March and expect to complete by mid-April.
How this will affect your organization:
Users will no longer see the Office file collaboration setting unless controlled by admin policy or if they had previously disabled it.
What you need to do to prepare
No action is required at this time. If you have documentation that describes how to disable the Office file collaboration settings, you will need to update it.
MC499439 — (Updated) Updated Files On-Demand Settings on Windows
<30 Days
Microsoft 365 Roadmap ID 101520
Updated April 4, 2023: We have updated the content below with new information and timing. Thank you for your patience.
We have an update to the OneDrive sync app advanced settings for Files On-Demand on Windows.
Previously, a toggle was shown to allow users to opt out of Files On-Demand. After this change, users who have Files On-Demand enabled will no longer see that toggle. Instead, users will see two buttons:
After this change, users who have Files On-Demand enabled will see two buttons:
- Free up disk space: This saves space on this PC by setting all your files to online-only, including files currently set to “Always keep on this device”. The first time you open a file in the future, you’ll need to be online.
- Download all files: This will us up to X MB of space on this PC and includes files currently set to “Free up Space” or online-only. Files download when you’re online and then you can use them offline.
Admins can still disable Files On-Demand, if necessary, by setting the Use OneDrive Files On-Demand policy to “dword:00000000”. If Files On-Demand is enabled by policy, the “Download all files” button in OneDrive Settings will be disabled.
When this will happen:
We will begin rolling out to the Production ring in early April and expect to complete by mid-April.
How this will affect your organization:
This change only affects users who have Files On-Demand enabled. There is no change at this time for users that have the feature disabled from OneDrive settings or by admin policy.
What you need to do to prepare:
No action is required at this time. If you have documentation that describes how to disable the Files On-Demand setting, you will need to update it.
MC455520 — (Updated) SharePoint admin center: Streamlining management of site information across Teams and Microsoft 365 Groups
<30 Days
Microsoft 365 Roadmap ID 100053
Updated March 16, 2023: We apologize for the delay and have updated the rollout timeline below. Thank you for your patience.
SharePoint is updating the site detail panel to include Microsoft Teams and Microsoft 365 Groups information.
Standard Release: We will begin rolling out mid-November 2022 and expect to complete by late April (previously late February).
How this will affect your organization:
Admins that have permissions to SharePoint, Teams and Groups admin centers can now manage all related attributes (membership, group name, description, etc.) from a single site detail panel in the SharePoint admin center 'Active Sites' tab. SharePoint admins with SharePoint only permissions will have read-only access to the new attributes.
What you need to do to prepare:
No preparation is required
MC408694 — (Updated) New 'Activity' Column in OneDrive 'My Files' list view
>60 Days
Microsoft 365 Roadmap ID 88913
Updated March 16, 2023: We have updated the timeline below. Thank you for your patience.
We are introducing a new Activity column in OneDrive My Files list view. The goal of this feature is to help users stay up-to-date on the files that they are working on with others by surfacing relevant activity information. We will show file activity related to actions, such as, user comments, edits, share, and @mentions.
When this will happen:
We will begin rolling out this feature in mid-October (previously mid-September) and expect to complete rollout by late March (previously mid-February).
How this will affect your organization:
There is no impact to your organization. This feature will be delivered as a user interface update in the form of an additional column in My Files list view with activity information related to files (e.g., file shared, user comment, @mentions).
What you need to do to prepare:
There is nothing you need to do to prepare for this change. You may want to notify your users about this change and update your training and documentation as appropriate.
Power BI
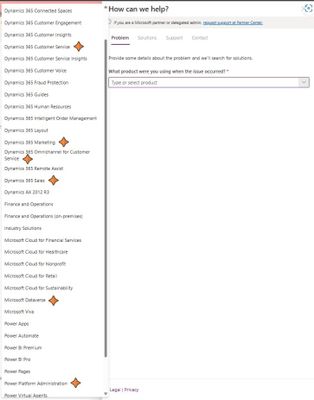
MC537127 — Power Platform admin center - Changes to support request product list - GCCH
<30 Days
We are making changes to the product listing when creating a new support request in the Help + support page within the Power Platform admin center. Starting on April 7, 2023, this update will begin rolling out per our normal deployment schedule.
How will this affect me?
- The following products, which were previously listed as problem subtypes under the Dynamics 365 Customer Engagement product, are now available in the primary product selection menu: Dynamics 365 Sales
- Dynamics 365 Marketing
- Dynamics 365 Customer Service
- Dynamics 365 Omnichannel for Customer Service
- Microsoft Dataverse
- Power Platform Administration
Note: This change will not have any functional impact on your license(s).
MC535549 — Power Platform and Dataverse coming to Service health and Message Center
<30 Days
In an effort to deliver greater clarity on service health communications, we are making changes to the service listings available on Service health and Message Center. Beginning April 2023, Service health and Message Center will include Dataverse and Power Platform.
When this will happen:
This will be rolled out to Service health and Message Center by the end of April 2023.
How this will affect your organization:
Administrators can track issues related to Power Platform admin center, and other Power Platform related issues, under the new service 'Power Platform'. Communications related to Dataverse will appear under “Microsoft Dataverse”.
What you need to do to prepare:
No preparation is needed. You can visit Microsoft 365 admin center's Service health dashboard and Message Center to view the new services.
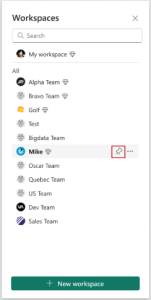
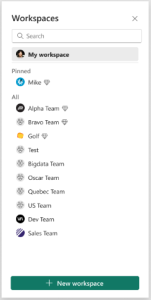
MC534307 — Pin workspaces is now available
<30 Days
We are excited to announce that the pin workspace feature is now available! You can pin your workspaces on top of the list. And unpin them anytime as needed. This functionality enables you to easily navigate to the workspaces that are most relevant to you without searching through the workspace list.
When this will happen:
Standard Release: We have started rolling this out and expect to complete by early April 2023.
How this will affect your organization:
User will see pin functionality in workspace flyout and can pin/unpin workspaces.
What you need to do to prepare:
No mandatory work for preparation. You can optionally consider notifying your users if needed.
MC530354 — Power Apps – Update regarding Monitor for model-driven apps - GCCH
TBD
We are reaching out to inform you that we are disabling the Monitor for model-driven apps while we work on making improvements. You may continue to use Monitor for canvas apps.
When will this change happen?
This change will go into effect following the usual deployment schedule. We will notify you when Monitor is available again for model-driven apps.
If you require assistance, please contact Microsoft Support.
Microsoft Viva
MC535703 — (Updated) Microsoft Viva: SharePoint content on Office.com and Edge New Tab Page Feed show related Viva Topics
<30 Days
Microsoft 365 Roadmap ID 118063
Updated April 4, 2023: We have updated the rollout timeline below. Thank you for your patience.
Microsoft Feed items will soon show a Viva Topic pill when it is relevant for SharePoint content. This allows the user to easily learn more about the topic and get to the people and content related to the topic for that item.
When this will happen:
Targeted Release: We will begin rolling out in early April (previously late March) and expect to complete rollout by mid-April (previously early April).
Standard Release: We will begin rolling out in mid-April (previously early April) and expect to complete rollout by late April (previously mid-April).
How this will affect your organization:
Licensed Viva Topics users in your organization will begin to see Topic pills alongside their feed items. This allows them to discover and engage with more knowledge for the content around these topics.
What you need to do to prepare:
There is nothing needed to prepare for this. You may want to notify users of this update.
MC534309 — Microsoft Viva Insights Powershell Tenant Controls
<30 Days
Admin controls to view and update Tenant’s default Microsoft Viva Insights settings using PowerShell.
When this will happen:
These changes will start to roll out in Preview in February 2023 and will be available worldwide by mid-April 2023.
How this will affect your organization:
Previously, admins could only update individual user settings using PowerShell. Going forward, they can also update their tenant settings in PowerShell, similar to how they would do it on the Microsoft 365 Admin Center.
Microsoft Viva Insights Tenant default settings that admins previously updated only on the Microsoft 365 Admin Center can also now be updated using PowerShell.
- Admins can view their tenant’s default settings using the cmdlet Get-DefaultTenantMyAnalyticsFeatureConfig.
- They can update the default settings of their tenant by using the cmdlet Set-DefaultTenantMyAnalyticsFeatureConfig –PrivacyMode [opt-in/opt-out] -Feature [all/dashboard/digest-email/add-in/meeting-effectiveness-survey/schedule-send] -IsEnabled [$True/$False].
What you need to do to prepare:
These general settings are applicable to new users added to the tenant as well as existing users that have not previously updated their settings. For any user in the tenant that has updated their settings, if an admin updated the tenant’s default settings, then this setting is not applicable to the user as the user’s setting takes precedence over the tenant’s default setting. Settings updates can take effect up to 24 hours after the change is made.
Documentation:
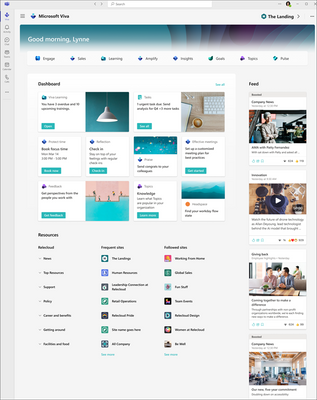
MC533820 — New Home Experience for Viva Connections desktop for GCC
30-60 Days
Microsoft Roadmap ID 99917
A new desktop experience is being released for Viva Connections that’s easier and faster to set up and optimizes content to deliver a modern employee experience. The new Viva Connections desktop design serves as a new home experience option that centers essential job tasks, personalized content, easy access to other Viva experiences, and better aligns with the mobile experience. The New home experiences for Viva Connections desktop will begin rolling out to GCC tenants.
When this will happen:
Rollout to GCC tenants will begin in late April and is expected to be complete by late May.
How this will affect your organization:
For customers who are currently using Viva Connections, the new home experience will automatically update in Microsoft Teams. Customers with existing home sites can choose to keep the existing desktop experience using a new PowerShell command that will become available to all customers by mid-November. For more details, please visit the customization guidance documentation.
If you’ve already set up Viva Connections, existing content will pre-populate into the new home experience.
If you haven’t set up Viva Connections yet, the default experience includes starter cards on the Dashboard, but otherwise does not impact the current mobile experience.
What you need to do to prepare:
With the new desktop experience, admins and editors will be able to edit content and manage permissions from Microsoft Teams. To prepare for this change, admins and editors for Viva Connections can learn more about how to customize the new home experience and how permissions work by visiting this documentation.
End users in your organization will use the same entry point in Teams as the previous desktop experience. When they view the new experience for the first time, visual prompts will walk them through the main functions of the design and how to interact with diff....
Microsoft Teams
MC538387 — Microsoft 365 admin center: Teams apps Usage Tracking Soon Available within Usage reports
<30 Days
Microsoft 365 admin center will soon support tracking on the usage of all Teams apps in usage reports. IT admins will have a first-hand view of monthly and daily active user counts for first-party, third-party store, and third-party line of business apps.
When this will happen:
Rollout will begin in mid-April and is expected to be complete by late April.
How this will affect your organization:
Admins will be able to monitor any active or blocked apps available for Teams users. The report will include app usage data for first-party, third-party store, and third-party tenant specific business applications. To access the new reports, go to: Microsoft 365 admin center -> Reports -> Usage ->Teams apps.
What you need to do to prepare:
There is no action required from you at this time. Please review supporting documentation at Microsoft 365 admin center activity reports and Microsoft Learn and Microsoft 365 admin center Teams app usage reports.
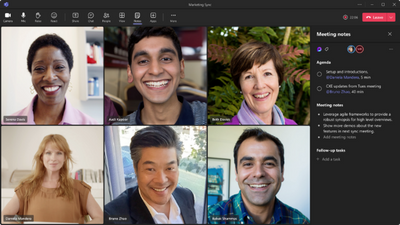
MC538385 — Collaborative Meeting Notes
>60 Days
Microsoft 365 Roadmap ID 101509
Teams across Microsoft are coming together to provide tools that help make meetings more effective. More specifically, we’re improving how you track what you want to discuss (Agenda), what you discussed/decided (Notes) and what you need to follow up on (Follow-up Tasks). These capabilities are now integrated into the end-to-end meeting experience in Teams, Loop, Planner, To Do, Office.com and OneDrive for Business.
When this will happen:
Preview Release: We will begin rolling out late April and expect to complete by mid-May.
Standard Release: We will begin rolling out late May and expect to complete by late June.
How this will affect your organization:
Users within your tenant will see a Notes button during meetings that invokes these new capabilities. The meeting notes will be shown on the right pane of the meeting window with the ability to open them in the browser for more room or on a second monitor. Participants can collaborate in real time, create an agenda, take notes and add tasks. When participants are assigned a task in the meeting, they will also receive an email notification and it will be synced with the Planner and To Do apps.
Meeting organizers will also see an ability to add Collaborative notes before meetings, to prepare by adding agendas or other materials in one place.
After the meeting, Collaborative notes will remain accessible for all participants on the Teams calendar meeting details page. The experience is a Loop component, so they can be copied easily out of the meeting and into chats, group chats, emails and other documents. This makes prepping and follow-up even more seamless.
What you need to do to prepare:
Nothing is required to prepare. This capability will be enabled by default when it rolls out.
Note: the new Collaborative notes file will generate a Company Shareable Link (CSL) by default.
You can manage this feature via SharePoint PowerShell with:
Set-SPOTenant -IsCollabMeetingNotesFluidEnabled (boolean)
You can read more about admin controls here: Manage Loop experiences (Loop app and Loop components) in SharePoint.
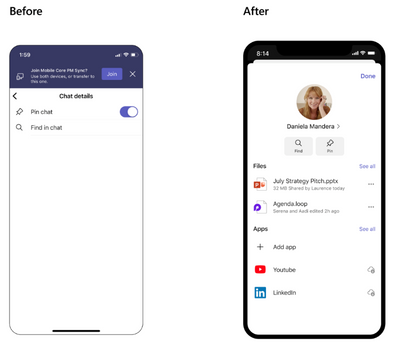
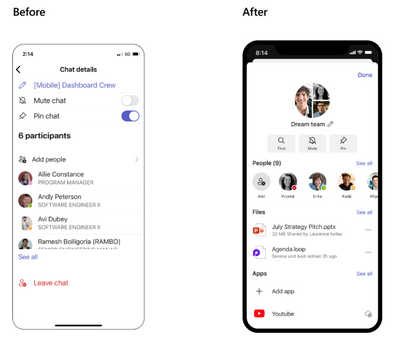
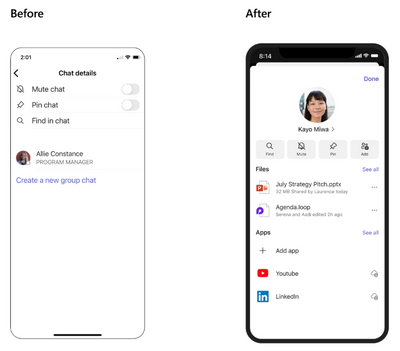
MC537952 — Microsoft Teams for Mobile: Chat Details Update
>60 Days
Microsoft 365 Roadmap ID 114938
We are updating the chat details experience for Teams Mobile Group Chats, One on One Chats, and Self Chats.
When this will happen:
Targeted Release (Preview): We will begin rolling out in mid-April and expect to complete rollout by mid-May.
Standard Release: We will begin rolling out in mid-April and expect to complete rollout by mid-May.
GCC, GCC-H, DoD: We will begin rolling out in late May and expect to complete rollout by early June.
How this will affect your organization:
The following items will be new:
- Updated UI and layout.
- Users are now able to access their own people card from the chat details and see Files and Apps from that conversation rather than seeing Files and Apps from the chat canvas, which will be deprecated.
What you need to do to prepare:
There is no action required at this time. You may want to notify your users of this change.
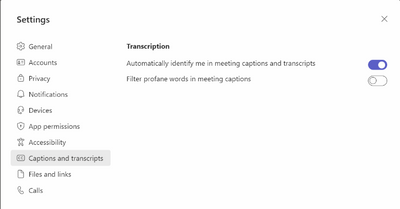
MC537415 — Profanity filtering on/off control for Live Captions in Teams meetings
>60 Days
Microsoft 365 Roadmap ID 113412
With the newly introduced toggle for turn on/off profanity filtering in Live Captions, users will now be able to control whether they want to continue to leverage the profanity filtering capability provided out of the box, or if they want to see every word as-is.
When this will happen:
Targeted Release (Public preview): We will begin rolling out early April and expect to complete by mid-April.
Standard Release: We will begin rolling out early May and expect to complete by mid-May.
GCC-High and DoD: We will begin rolling out early July and expect to complete by mid-July.
How this will affect your organization:
Users now have a new option to turn off the profanity filtering and be able to see the Captions as is. They can control this option via Settings in Teams > Captions and transcripts > Filter profane words in meeting captions.
What you need to do to prepare:
You may consider updating the training materials for you users to inform this feature is now available.
MC537412 — Teams Rooms: Windows 11 support for Teams Rooms on Windows devices
30-60 Days
Microsoft 365 Roadmap ID 122148
Teams Rooms on Windows devices that are eligible for Windows 11 upgrade will receive the Windows 11 22H2 release in May 2023. This will be offered and installed on their devices with 4.16 dot release (a newer release than 4.16.40.0 currently available). Devices that are not eligible due to an incompatible processor will continue to use Windows 10 per Windows hardware support policy. These devices will be offered Windows 10 22H2 release.
Devices that cannot upgrade to Windows 11 will continue to be supported until the end of Windows 10 End of servicing for General Availability Channel or hardware support from OEM, whichever comes first. Windows 10 releases information at https://learn.microsoft.com/en-us/windows/release-health/release-information. Please note, not all Windows releases are supported for Teams Rooms, to find supported version, see https://learn.microsoft.com/en-us/microsoftteams/rooms/rooms-lifecycle-support#windows-10-release-su....
In addition, Teams Rooms on Windows OEMs will shift their manufacturing to Windows 11 IoT Enterprise as Windows 10 IoT Enterprise end of license sales is fast approaching (10/14/2023). OEMs with existing Windows 10 licenses inventory (or to support recovery media for existing Windows 10 based devices) may continue to provide Windows 10 based images for some time that should automatically update to Windows 11 post setup. All OEMs are expected to move to Windows 11 IoT Enterprise based images in future. Customers should ensure all new hardware purchases check for Windows 11 compatibility to future proof their device investment.
When this will happen:
Standard Release: We will begin rolling out early May and expect to complete by late May.
How this will affect your organization:
Microsoft Teams Rooms on Windows application release 4.16.XX. X (a dot release, on top of current release 4.16.40.0) will be available in May 2023. This app will allow eligible Teams Rooms on Windows devices to receive Windows 11 22H2 update through Windows update. After the dot release has booted normally at least once, customers can either wait for 8 days for Windows 11 22H2 to install automatically or can pull the latest Windows 11 update from Windows Updates manually by checking for updates from the Windows Settings app. Devices that are not eligible will be offered Windows 10 22H2 release.
To check if your device is eligible for Windows 11, you can either check the list of eligible Intel processors for Windows 11 at https://learn.microsoft.com/en-us/windows-hardware/design/minimum/supported/windows-11-supported-int...
What you need to do to prepare:
To ensure that there are no issues preventing the Windows update in your environment, it is recommended to manually check for updates on a small set of devices, after the Windows 11 enabled 4.16.XX.X release has been installed and booted normally at least once on them. From admin mode, check for updates using the Windows Settings app: Windows 11 22H2 or Windows 10 22H2 (depending on what’s supported for your devices) should be offered and should download and install. If the updates are not offered or installed, check for external policies (such as MDM or Active Directory Group Policies) that might be in place for your organization that could block this update.
MC536885 — Changes in Normalization
>60 Days
Stopping normalization on number that starts with plus sign (+)
Normalization in Microsoft Teams was not designed to do normalization when the phone number starts with plus sign (+) as documented, but we've never enforced this in the Teams desktop or Web client. We are planning to enforce this in the future but for now we recommend avoiding this pattern.
We are making this change to align with our Calling Service, other Teams services, Azure Communication Services SDKs, and other Microsoft services. Numbers that start with a plus sign (+) will not pass through any normalization rules.
Translated numbers that do not start with a plus sign (+), will pass through normalization rules more than once. Please see :https://docs.microsoft.com/en-us/microsoftteams/create-and-manage-dial-plans for more information
When this will happen:
Standard Release: We will begin rolling out mid-July and expect to complete by late August.
How this will affect your organization:
No one gets impacted immediately. We are letting you know to make you prepare for this change. If you have dial plan policies that has a pattern to match the phone number that starts with plus sign (+) or you rely on the number that starts with plus sign (+) to be translated, you have to adjust your dial plan policies.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC536877 — Chat RSC in Microsoft Teams
30-60 Days
We are pleased to announce the extension of the resource-specific consent (RSC) permission model for chat and channel scope in Microsoft Teams. RSC permissions have been expanded to include the ability for chat members to grant access to chats for applications running within Teams.
When this will happen:
Standard Release: We will begin rolling out late April and expect to complete by late May.
How this will affect your organization:
Microsoft Teams is releasing the support for resource-specific consent permissions for chats. From this point, admins will no longer need to give broad org-wide permissions for apps to work with chats. Instead, authorized chat members will now be able to give scoped data access to a Teams app in only those chats where they want to install the app. This will prevent the presence of overprivileged apps in your organization. Apps will get access to only the data of the chat in which they are installed. Authorized chat members can revoke data access to the app by uninstalling the app from the chat. Admins will still be in control by allowing/blocking installation of apps through the Teams Admin Center.
What you need to do to prepare:
Admins don’t need to take any action to enable this feature in your organization. Chat RSC will be enabled by default. Instructions for toggling your Chat RSC settings are available here.
MC535700 — IT Admin Policy Change for the New Webinars experience on Teams
30-60 Days
With the launch of the new webinar experience, we introduced a new events policy.
In order to ensure smooth transition to the new webinar experience, we temporarily continued the old webinar policy setting of AllowMeetingRegistration in controlling the availability of the new webinar. Now with successful introduction of the new webinar, we will be decoupling the settings that control the availability of the old (via AllowMeetingRegistration in meeting policy) and the new (via AllowWebinar in events policy) webinar.
When this will happen:
This change will take effect on May 3, 2023.
How this will affect your organization:
The current state of enforcement with coupling of AllowMeetingRegistration and AllowWebinar controlled the behavior of the webinar entry point in New Meeting dropdown in Teams Calendar. Below is summary of the current state and changes this will bring highlighted in red if no action is taken:
By decoupling:
- AllowMeetingRegistration will only control whether require registration option is available in Teams meetings. Availability of require registration option is not impacted by this change.
- AllowWebinar will only control whether there will be the webinar entry point with the new webinar experience under new meeting dropdown in Teams Calendar.
You can configure the new events policy using Powershell cmdlets: New-CsTeamsEventsPolicy, Set-CsTeamsEventsPolicy, Grant-CsTeamsEventsPolicy, Get-CsTeamsEventsPolicy, Remove-CsTeamsEventsPolicy.
What you need to do to prepare:
If you want your users to still have a webinar entry point to create webinar, ensure AllowWebinar is set to ON. Note that users will be using the new webinar experience with the entry point and not meeting with registration moving forward.
If you want your users to only use meeting with registration and not the new webinar, you need to set AllowWebinar to be OFF and AllowMeetingRegistration to be ON. Note your users will not see a webinar entry point and will have to set require registration setting in a meeting.
For more information on getting started with Teams webinar, please visit this page.
MC535261 — Offline meetings in Microsoft Teams
>365 Days
Microsoft 365 Roadmap ID 122483
For events such as personal appointments, lunch break slots on calendar, and in-person meetings, you can now create a true appointment in Teams calendar by turning off the online toggle for a meeting.
What to expect: By default, all meetings created from teams will be teams online meeting. The toggle is currently available only for private meetings and appointments. Offline events will not create chat thread and other teams meeting artifacts that are tightly coupled with teams' online meetings.
When this will happen:
Standard Release: We will begin rolling out in late May.
GCC, GCCHigh, DoD: We will begin rolling out in early July.
How this will affect your organization:
No impact.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC534743 — Microsoft Teams: Speaker View in Teams Meetings
>60 Days
Microsoft 365 Roadmap ID 116009
Microsoft Teams is introducing a new feature: Speaker View. This option can be selected from the view switcher within meetings, allowing users to effortlessly track the current active speaker. Speaker View is particularly effective in scenarios with a limited number of key speakers and a large audience, such as town halls, trainings, or lectures - especially from the student's perspective.
When this will happen:
Targeted Release (Public Preview): We will begin rolling out in early April and expect to complete rollout by mid-April.
Standard Release: We will begin rolling out in early May and expect to complete rollout by mid-May.
GCC-High & DoD: We will begin rolling out in late May and expect to complete rollout by mid-June.
How this will affect your organization:
The Speaker View offers several enhancements, including:
- Easy tracking of the active speaker: The view includes a primary area on the stage to focus on key participants in the meeting.
- The active speaker's video will be rendered at a higher resolution, providing better visual clarity.
- Equal representation for audio and video participants: All attendees will be equally represented in the meeting, regardless of whether their video is enabled or disabled.
- Inclusive by default: Speaker View utilizes 16:9 tiles, providing ample space to fully display hand gestures and body language.
- Predictable experience: The use of 16:9 tiles and consistent placement of audio and video participants on the same stage ensures a fluid experience. Users toggling their videos on or off will not cause the entire stage to be re-rendered. The main area designated for the active speaker is also utilized for shared content, enabling seamless transitions during presentations.
In addition to the new view option, the button to disable incoming videos will be relocated from its current position in the "More" overflow menu to the same view switcher where Speaker View is located. Users will be able to select a new view from the view switcher. This view will not be set as a default view.
What you need to do to prepare:
No explicit user action is needed to enable or use this feature. You may want to update your user documentation to inform users of this update.
MC534741 — Collaboration Security for Microsoft Teams
>60 Days
Microsoft 365 Roadmap ID 117595
The rise of collaboration tools like Microsoft Teams also represents a new attack surface for adversaries. Attacks like phishing and ransomware that for decades have primarily used email as an entry point, are expanding to target collaboration tools more frequently. While Microsoft Defender for Office 365 has been providing protection in Microsoft Teams at time of click, we are excited today announcing a preview of enhancements to that protection, further protect users in Microsoft Teams and enhance the Security operations flows.
NOTE: this preview is only available to Microsoft Defender for Office P2 customers.
Description of the feature set:
Building on the current Safe Links protections for teams we are adding, in preview, additional functionality to enable end users in Microsoft Teams to report suspicious messages, zero hour auto-purge (ZAP) for malicious items along with the relevant Security operations flows such as alerting, submissions and quarantine.
When this will happen:
Public Preview: We will begin rolling out on late March and expect to complete by mid-May.
GA: We will begin rolling out late June 2023 and expect to complete by late July 2023.
How this will affect your organization:
Teams Admins, SecOps and End Users will see new added experiences in Teams Admin Center, Security Console and Teams Client (web and desktop) respectively for the following features:
- Enhanced visibility into the attack landscape through end-user reporting
- Effectively Respond with Post Delivery Analysis, ZAP & Quarantine
- Proactively hunt for threats in Microsoft Teams with advanced hunting
- Build Microsoft Teams user resilience in your organization.
What you need to do to prepare:
You can follow the instructions on how to Opt-in here Microsoft Defender for Office 365 support for Microsoft Teams (Preview)
MC534314 — New Breakout Rooms experience enabled on VDI clients
30-60 Days
This change is associated with Microsoft 365 Roadmap ID 119698
Breakout rooms allow meeting organizers to split main meetings into smaller sessions for focused discussions.
When this will happen:
- Preview: Begin rolling out early April and expect to complete by mid-April.
- Standard Release: Begin rolling out mid-May and expect to complete by late May.
How this will affect your organization:
Once available, follow the steps below to setup and use Breakout rooms.
Administrators
As an admin, ensure users can schedule private meetings with the following settings:
- Allow scheduling private meeting = on
- Allow Meet now in private meeting = on
- Allow channel meeting scheduling = on
- Allow meet now in channels = on
Meeting Organizers and Participants
- Breakout rooms option will be available within your meetings for VDI client (Min Desktop version 1.5.00.11865)
- Make sure all participants, including the meeting organizer are using the latest version of Teams.
- As a meeting organizer or co-organizer, join a channel / private scheduled meeting, or channel / private meet now meeting. Once you are in the meeting you should see the breakout room option next to the View control.
What you need to do to prepare:
As an admin, review and share the settings to ensure they are set correctly for your organization and your users.
Additionally, you may wish to share the information below with your users to help them prepare.
Features available for Organizer:
- Setup Breakout Rooms on Teams VDI client
- Create breakout rooms in scheduled private meetings (including recurring), Channel meetings and private meet now meetings
- Meeting organizers and co-organizer can manage rooms and hop between rooms freely
- Via the Breakout rooms settings panel meeting organizers can appoint Breakout Room managers to manage of rooms during the live session
- Setup breakout rooms during an active meeting or prior to the meeting
- Create up to 50 breakout rooms in a single meeting
- Add, remove, delete and rename breakout rooms
- Reassign room participants from one room to another before as well as while the rooms are open
- Send an announcement that will show up as a meeting chat message in each room.
- Chats, files, and recordings: organizer will always have access to all rooms meeting artifacts
- Organizers can set a timer for all breakout rooms created in a meeting session via the Breakout rooms settings panel.
Features available for participants:
- Join breakout rooms from web, desktop, iOS, iPads, Android mobiles and tablets, PSTN and VDI.
- Participants join the room as presenters, so they can present, share Whiteboard, etc. freely.
- Participants cannot add others to meeting chat, copy meeting details, nudge others to the meeting
- Participants cannot hop back to main meeting or between rooms on their own. They must wait for the meeting organizer to pull them back to the main meeting.
- Chat and artifacts shared during meeting are viewable for room participants.
- Participants remain assigned to their breakout rooms unless the meeting organizer chooses to change them. The assignment persists across subsequent sessions or recurring meetings.
MC533818 — Microsoft Teams: Teams button to Join Meeting from pre-join Screen for all Microsoft Teams Certified Peripherals
<30 Days
Microsoft 365 Roadmap ID 95632
Users can soon successfully join and participate in a meeting directly with their Teams Button on their Microsoft Teams certified peripheral.
When this will happen:
Preview: We will begin rolling out in early April 2023 and expect to complete rollout by mid-April 2023.
Standard Release: We will begin rolling out in mid-April 2023 and expect to complete rollout by late April 2023.
How this will affect your organization:
After a user receives a meeting start notification, the user can press the Teams Button to bring up their Meeting Pre-Join Screen.
This feature will be automatically available for all Microsoft Teams Certified Peripherals with a Teams Button.
What you need to do to prepare:
There is no action required from you at this time. You may want to update any relevant training documentation.
MC533817 — Microsoft Teams certified Peripherals: Teams Button to bring Teams Meeting Stage to Foreground During Meeting
<30 Days
Microsoft 365 Roadmap ID 98496
Microsoft Teams users can soon bring up the meeting stage to the foreground by pressing their Teams Button during a meeting.
Note: This feature only applies to devices with dedicated Teams Buttons. If the device has a dual-purpose button (supports both hookswitch and Teams Button), pressing the button will end the call.
When this will happen:
Preview: We will begin rolling out in early April 2023 and expect to complete rollout by mid-April 2023.
Standard Release: We will begin rolling out in mid-April 2023 and expect to complete rollout by late April 2023.
How this will affect your organization:
This feature will allow users to quickly return to the meeting stage to review chat discussions or the content being shared, especially if the meeting stage was hidden behind other windows.
This feature will be automatically available for all Microsoft Teams certified Peripherals with a dedicated Teams Button.
What you need to do to prepare:
There is nothing you need to do to prepare for this update.
MC533815 — Virtual Appointment as a new Teams Meeting Template in GCC
>60 Days
Microsoft 365 Roadmap ID 100705
A new Teams Meeting Template, Virtual Appointment, will be added as a new template type in GCC tenants accessible from the 'New meeting' dropdown menu in the Teams Calendar. This is a free experience that brings enhanced business-to-consumer meeting features into the lightweight and familiar Teams scheduling experience. When meeting with someone from outside of your organization, the Virtual Appointment meeting can be used to ensure the person you are meeting with has a seamless experience with the meeting from start to finish - all without having to learn new tools or leave the standard scheduling flow.
Users can use the Virtual Appointment template instead of a standard Teams meeting for meetings with external users. They can select the meeting type, fill out the tailored scheduling form, including external guests and meeting details, and then send the meeting. The external guests invited will receive a customized meeting invitation that includes key appointment details and a quick-join button, which allows users to join the meeting from anywhere - without downloading Teams - and enter a pre-appointment waiting room before the meeting begins. This provides a familiar experience to internal users and makes external user join a seamless experience.
When this will happen:
We will begin rolling out to GCC early June and expect to complete by early July.
How this will affect your organization:
Virtual Appointment will release as an out-of-the-box Teams Meeting Template and will appear as a configurable template type within the Teams Admin Center where the Meeting Options can be configured, and it can be hidden/shown for groups within your organization. The Virtual Appointment Teams Meeting Template will appear as a template type within the New Meeting dropdown menu in the Teams Calendar, unless hidden by an Admin (then it will not appear at all).
What you need to do to prepare:
When the Virtual Appointment Teams Meeting Template rolls out in June, it can be managed from the Teams Admin Center. To restrict who can access the template, navigate to Teams Admin Center > Meetings > Meeting template policies to show/hide the template based on global and group policies in the tenant. To restrict the default value and visibility of the Teams Meeting Options within the Virtual Appointment Meeting Template, navigate to Teams Admin Center > Meetings > Meeting templates > Virtual appointment > Edit and configure options.
MC532608 — (Updated) Enable second video stream with "Teams Content Camera on Desktop"
TBD
Microsoft 365 Roadmap ID 118580
Updated March 28, 2023: We are revising the schedule for this release and will communicate the new timeline, via Message center, once available. Thank you for your patience.
Users will be able to enable a second video stream to support both their Personal Video and Teams Content Camera on Desktop feature. When enabling the Teams Content Camera on Desktop feature, the Personal Video is expected to be maintained so long that the user selects a separate Camera to support the two video streams.
When this will happen:
We are revising the schedule for this release and will communicate the new timeline, via Message center, once available
How this will affect your organization:
This feature will be applied to the Teams Content Camera on Desktop feature automatically.
What you need to do to prepare:
Nonapplicable.
MC531213 — Microsoft Teams: Federated Group Calling - GCC-High and DoD Rollout
<30 Days
We are releasing the capability for Microsoft Teams users to easily start a group Teams call with federated colleagues outside of the organization, including video and screensharing, all over an internet connection without any PSTN usage charges.
This post is associated with Microsoft 365 Roadmap ID 117566
When this will happen:
Rollout will begin in early April 2023 and is expected to be complete by late April 2023.
How this will affect your organization:
Users will be able to start a group call within the chat that has federated users in it.
What you need to do to prepare:
Admins will have to enable federation for the tenant to be able to allow users to collaborate outside of the tenant.
For more information, please visit Use Guest Access and External Access to Collaborate with People Outside Your Organization
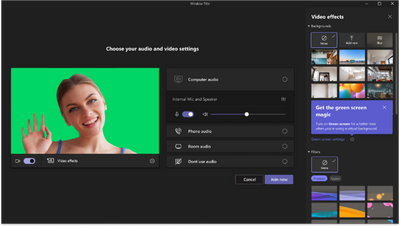
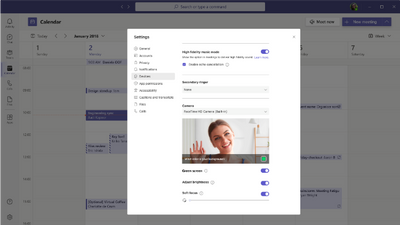
MC529415 — Microsoft Teams: Green screen feature in Teams Meetings
>60 Days
Microsoft 365 Roadmap ID 117941
Microsoft Teams will soon be releasing a new green screen feature for users. The virtual background with a green screen will provide an enhanced virtual background effect.
When this will happen:
Public Preview: We will complete rollout by late March.
Standard and GCC: We will begin rolling out in mid-April and expect to complete rollout by late April.
GCC-H: We will begin rolling out in early May and expect to complete rollout by mid-May.
DoD: We will begin rolling out in early June and expect to complete rollout by late June.
How this will affect your organization:
Green screen improves the sharpness and definition of the virtual background effect around your face, head, ears, and hair. It also allows you to show a prop or other object in your hand to be more visible to other participants in a call.
Supports the following:
- Desktop platforms: Windows and macOS with Intel chips, not supporting Mac M1/M2
- Device: Requires a solid color screen or clean background wall behind you
- User Experience: Users must apply a background effect in Teams meetings to enable the green screen effect and should select the correct backdrop color so that the effect is applied correctly and better quality is achieved
Known limitations:
- Green screen will automatically disable background blur and Together Mode while being compatible with Presenter modes like Standout, Side-by-Side and Reporter, PowerPoint Live Standout, and background replacement (JPEG/PNG).
- Transparent or translucent objects cannot produce a good green screen effect.
- If the object is too thin, it cannot be properly detected.
To enable:
Please make sure that you have applied a background effect in Teams meeting before enabling the green screen effect and chosen the correct backdrop color so that the effect is applied correctly. Please also ensure you have a solid color screen or clean background wall behind you.
- After you join a meeting, click the “More” icon in the meeting toolbar, go to “Video effects.”
- When the “Video effects” panel page is open, go to “Green Screen Settings” in Backgrounds section and click the link to turn on the Green screen toggle button under “Teams settings -> Devices -> Green screen.”
- Click the backdrop icon and move your mouse cursor into the Preview box to manually pick backdrop color.
- Return to your meeting.
What you need to do to prepare:
You may want to update your training materials indicating that this feature is available to users.
MC528955 — Microsoft Teams: New Files app in Teams
>60 Days
Microsoft 365 Roadmap ID 97677
Securely store, organize, and collaborate on all your files anytime, from anywhere and across all of your devices with the new files app experience in Teams. The new files app brings a modern experience to all of your content from your chats, channels or meetings including any location from OneDrive or SharePoint.
When this will happen:
Preview: We will complete rollout by late March.
Standard Release: We will begin rolling out in early April and expect to complete rollout by mid-April.
GCC, GCC-H: We will begin rolling out in early May and expect to complete rollout by late May.
DoD: We will begin rolling out in early June and expect to complete rollout by late June.
How this will affect your organization:
Users can easily discover and locate files that are relevant right within the Teams app. This makes it possible to locate, share and collaborate with OneDrive files without leaving the Teams app and switching between various apps. An updated menu bar will help you navigate to your content quickly.
- Home: Get back to your recently accessed files
- My files: Access your personal OneDrive files
- Shared: Find files shared with you and files you have shared across M365
- Downloads: Locate files downloaded from Teams on your computer
- Quick Access: Pin document libraries or channels files tab to access them quickly
The existing Files app that is enabled by default will automatically be updated with new files app experience.
What you need to do to prepare:
There is nothing you need to do to prepare.
MC528358 — Invoke Content Camera on Desktop feature
Rolled Out
Microsoft 365 Roadmap ID 118587
Currently, users must turn on sharing from a content camera in Microsoft Teams via the Share tray on the Teams Meeting stage.
Moving forward, users will be able to start and stop sharing content directly from a certified Teams device. This feature enables presenters to share a Whiteboard, document, or video more quickly during a meeting.
When this will happen:
Preview: This is now available in preview.
Standard Release: We will begin rolling out mid-March 2023 and expect to complete by late March 2023.
How this will affect your organization:
No impact. This feature will be made available on all Teams Certified Peripherals supporting this feature.
What you need to do to prepare:
You may consider updating your training and documentation as appropriate.
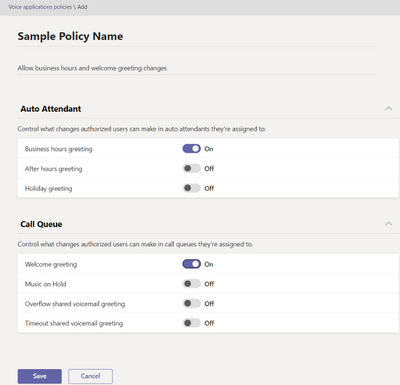
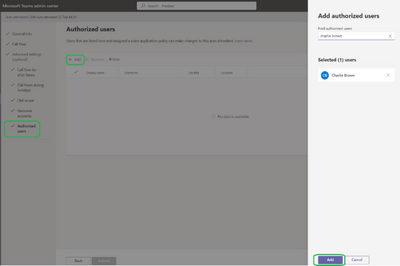
MC527929 — Microsoft Teams: Change Call Queue and Auto Attendant Greetings and Announcements by Authorized Users
<30 Days
Microsoft 365 Roadmap ID 116739
Updated March 21, 2023: We have updated the rollout timeline below. Thank you for your patience.
Changing business conditions often require adjustments to call queue/auto attendant greetings and announcements. However, it can be difficult to identify the right Teams admin to make these changes, and addressing high request volumes can be time-consuming for the responsible admins. With the introduction of user managed CQ/AA greetings for Teams Phone, authorized users (as identified by Teams tenant admins) can change greetings and announcements for their respective call queues and auto attendant directly from the user’s Teams settings, in the “Calls” settings. To implement this capability, tenant admins must select permissible greetings/announcement changes for a voice policy, and then authorize specific users in the Teams Admin Center.
When this will happen:
Preview: We will begin rolling out in mid-April (previously late March) and expect to complete rollout by early May (previously early April).
Standard Release: We will begin rolling out in mid-May (previously mid-April) and expect to complete rollout by early June (previously late April).
How this will affect your organization:
Admins can delegate to specific users the ability to manage Call Queue and Auto Attendant greetings and announcements, by creating and assigning Voice application policies in the Teams admin center or through PowerShell cmdlets.
To assign capabilities to an authorized user through Teams admin center, admins can follow the steps below:
- Go to Voice -> Voice applications policies, and click on Add to create a new policy.
- After setting the policy name and descriptions, admins can choose which settings to allow in the policy. The example below shows Business hour greeting and Welcome greeting enabled.
- After clicking Save, admins can assign the policy to the users who require it. To know more about policy assignment, check Assign policies to users.
- Add user as Authorized to Auto Attendants and/or Call Queues, by going to Voice -> Auto attendants or Voice -> Call Queues. Select Auto Attendant or Call Queue to add the authorized users. Only users who have a Voice Applications Policy assigned (step 3) will be searchable to be added as authorized.
Assigning a policy to a user is not enough to grant them the administrative capabilities enabled in the policy. Users must also be assigned as Authorized User (step 4) on the specific Auto Attendants and Calls Queues they need to administer.
A user will get the same set of capabilities across all Auto Attendants and Call Queues they are assigned to as an Authorized User (step 4). It is not possible to assign multiple versions of the same policy to a user.
What you need to do to prepare:
Please visit this page for additional information.
MC527924 — Teams Meeting Add-in Log Files Location Change
30-60 Days
We're making some changes to the location of Teams meeting add-in log files.
When this will happen:
We will begin rolling out to Standard tenants in mid-March and expect to complete rollout by mid-April.
GCC, GCCH, and DoD will begin rollout in mid-April and expect to complete by mid-May.
How this affects your organization:
Teams meeting add-in log files will be stored in %localappdata%\Temp\Microsoft\Teams\meeting-addin. Administrators will need to look at the new location when verifying issues with Teams meeting add-in from the log files, when this change is implemented.
What you can do to prepare:
When this change takes effect, IT Admins will need to update any scripts or tooling that is looking for Teams meeting add-in logs from the previous location.
MC526125 — Important Changes to Whiteboard in Teams tabs for Gov Clouds
Rolled Out
Microsoft Whiteboard is making Whiteboard tabs in Teams configurable using Teams app permission policies. This provides more control and flexibility to enable or disable Whiteboard tabs in Teams and complements the already existing meeting policy for Whiteboard in Teams meetings.
When this will happen:
Rollout will begin in mid-March and is expected to be complete by late March.
How this will affect your organization:
Whiteboard will become configurable via Teams app permission policies. This change applies to Whiteboard tabs but does not change Whiteboard in meetings or Teams Annotations.
Tenants who have the policy of "Allow specific apps and block all others" for Microsoft apps will need to add Whiteboard to the list of specific apps once this change is in place to keep Whiteboard tabs functioning.
What you need to do to prepare:
Verify if you are using “Allow specific apps and block all others” in the Teams Admin Center. If so, add Whiteboard to the list of allowed apps. Please note that Whiteboard will not appear until after it has rolled out to your tenant, so you will need to check after March 31, 2023.
Please click Additional Information to learn more.
MC525143 — (Updated) Microsoft Teams: Video Clip Feature in Teams for Government Clouds
>60 Days
Microsoft 365 Roadmap ID 114155
Updated April 4, 2023: We have updated the rollout timeline below. Thank you for your patience.
Video Clips are a new way of working and connecting with coworkers using short video in Microsoft Teams. Users can record, send, and playback video messages in chats on all Teams endpoints. Recording limited to 1min across all platforms.
When this will happen:
GCC: We will start rolling out in mid-March and complete rollout by late March. - Complete
GCC-H: We will begin rolling out in early June (previously mid-Apr) and complete rollout by mid-June (previously late April).
DoD: We will begin rolling out in mid-June (previously mid-May) and complete rollout by late June (previously late May).
How this will affect your organization:
Teams users will soon be able to record, send and playback video messages in 1:1 and group chats with the Video Clips feature. Recording time will be limited to one minute across all platforms. This feature will be enabled automatically for users, however, Admins can disable this feature via the Teams Admin center.
What you need to do to prepare:
There is no action required from you at this time. For additional information on messaging policies, please visit this documentation. You may want to notify your users of this change and update any relevant training documentation as appropriate.
MC524208 — (Updated) Autosuggest location for Emergency location
Rolled Out
Microsoft 365 Roadmap ID 94692
Updated March 22, 2023: The rollout of this feature is in progress.
This feature would allow users to easily get location recommendations for emergency location. Confirming the location via the autosuggest will mark the location as an assist driving emergency call directly to PSAP. We will still allow manual location confirmations.
When this will happen:
General Availability: We will begin rolling out early March and expect to complete by mid-March.
How this will affect your organization:
There are no admin changes required.
What you need to do to prepare:
There is no action needed to prepare for this change.
MC517333 — (Updated) Teams Help App Pops Out by Default
<30 Days
Updated April 4, 2023: We have updated the rollout timeline below. Thank you for your patience.
In Teams, the Help app provides Teams guidance and support content. Previously, the Help app opened in full screen mode, filling the Teams window. With this update, Help will open as a pop out, in a separate window. This experience will allow users to view help content alongside what they are working on in Teams.
When this will happen:
We will begin rollout in early March and expect to complete rollout by late April (previously late March).
How this will affect your organization:
The Help app can be accessed from the question mark icon in the app bar, on the bottom left side of the Teams application. When a user selects ‘Topics’, ‘Training’, or ‘What’s new’, the Help app will launch in a separate window. The pop out feature is available for Teams on desktop only, not Teams on web.
What you need to do to prepare:
There is nothing you need to do at this time to prepare for this feature. We recommend you update any relevant training documentation as appropriate.
MC514979 — (Updated) Enabling New Call Controls with Survivable Branch Appliance
Rolled Out
Microsoft 365 Roadmap ID 111421
Updated March 16, 2023: This functionality is now fully released. As part of the release users will have additional functionality during the survivability:
- Users can not only use a dialpad to call but can now call them using profile card and by searching by their name.
- Users can use call history to call a user with a PSTN.
Note: VOIP calls are only possible if Caller and Callee have PSTN numbers and proper policies in place.
In the event of a network outage, users will soon have access to new call controls with Survivable Branch Appliance. Users will be able to use contact search, dial by name, and initiate a call from their call history. When connected to the same SBA and network, VoIP calls to peers will be routed through PSTN if the call recipient has an associated phone number.
When this will happen:
Rollout will begin in mid-February and is expected to be complete by late February.
How this will affect your organization:
There is no change required by admins to enable this feature. It will be enabled automatically. For additional information, please visit this documentation.
MC513664 — (Updated) Suggested Files in 1:1 Chats
>60 Days
Microsoft 365 Roadmap ID 95065
Updated April 4, 2023: We have updated the rollout timeline below. Thank you for your patience.
As an extension of Suggested Replies in 1:1 chats, you can now easily save time when you need to send a file in a chat by tapping on a "Share file" suggestion.
When this will happen:
Standard Release: We will begin rolling this out early April (previously early March).
GCC: We will begin rolling this out early July (previously early April).
GCC-High: We will begin rolling this out early August (previously early May).
DoD: We will begin rolling this out early September (previously early June).
How this will affect your organization:
Once available, users will be able to tap on a "Share file" action in chat whenever intent is detected to send a file.
What you need to do to prepare:
This feature ships default on; review Manage messaging policies in Teams.
If you wish to disable this feature in your tenant, please disable the Suggested Replies setting that is found in Messaging Policies.
Users also have a setting within the app so they can disable the feature.
MC494734 — (Updated) Teams update: Expanded view of the profile card in Teams
30-60 Days
Microsoft 365 Roadmap ID 109526
Updated March 28, 2023: We have updated the rollout timeline below. Thank you for your patience.
Beginning in March, users in your organization will be able to use expanded views of the profile card in Teams. The expanded view is already available in Outlook and includes more information, like an overview of the profile, contact information, organizational chart, and LinkedIn tab.
When will this happen:
We will begin rolling out this feature in late April (previously late March) and expect to complete the rollout in early May (previously late April).
What you need to do to prepare:
No preparation is needed for this change. For more information about what users can see on profile cards, see Profile cards in Microsoft 365.
MC469578 — (Updated) Introducing OneNote viewer in Teams mobile apps
Rolled Out
Microsoft 365 Roadmap ID 103097
Updated March 16, 2023: We have updated the rollout timeline below. Thank you for your patience.
We are excited to announce the OneNote viewer feature within Teams mobile apps.
Through this new feature, users will be able to open and view OneNote notebooks right within their Teams mobile apps. Users interested in editing the content will be directed to the standalone OneNote mobile app. The experience will be available as part of the Teams mobile apps on Android and iOS (including iPads) starting with English language users, followed by international languages.
When this will happen:
Standard Release: We expect to begin rolling out the OneNote viewer starting early December 2022 and complete the rollout by late March (previously late February).
Rollout for Android has completed.
What you need to do to prepare:
No admin action is needed to support these changes.
MC466199 — (Updated) Microsoft Teams: Users ability to delete chats
<30 Days
Microsoft 365 Roadmap ID 90723
Updated March 14, 2023: We have updated the rollout timeline below. Thank you for your patience.
Due to an issue with admin controls in TAC that we are actively working on fixing, please refer to the PowerShell documentation to control the setting for enabling or disabling delete chat capability. Link: Set-CsTeamsMessagingPolicy
Users will be able to delete 1:1 chats, group chats, and meeting chats if they are a participant in Microsoft Teams. This permanently deletes the chat only for the user, other people in the chat and conversation history are not impacted.
When this will happen:
We will begin rolling out in early December and expect to complete rollout by mid-April (previously mid-February).
How this will affect your organization:
Once available, users will be able to delete 1:1 chat threads or chat groups from the Teams desktop or mobile application. By selecting the ellipsis, users can select the Delete option to clear their chat list.
If Admins want to turn off this capability, they can do so from the admin portal under messaging policies. If turned off, users in the tenant will no longer see the delete option for their chats.
What you need to do to prepare:
This feature will be enabled automatically and there is no action required at this time.
Intune
MC525652 — Plan for Change: Microsoft Bookings will soon not be supported for Intune app protection policies
Rolled Out
Announced in MC485091, Microsoft 365 has retired the Microsoft Bookings mobile app, and it is no longer available in the Google Play store or Apple App store. Starting in late April 2023 or soon after, Intune app protection policies (APP) will no longer support Microsoft Bookings.
How this will affect your organization:
If you are using APP for Microsoft Bookings, we recommend enabling a Conditional Access (CA) policy to prevent users from accessing your organization’s resources through this app.
User impact: Once you have enabled the CA policy, users attempting to sign-in with their organization’s email will receive an error message.
What you need to do to prepare:
Update your documentation and notify your helpdesk as needed. We recommend creating an app-based CA policy with Grant access > Require app protection policy selected, to ensure only managed apps can access your organizations resources. For more information, see Use app-based Conditional Access policies with Intune.
MC524216 — (Updated) Planned Maintenance: Intune Service
TBD
Updated March 30, 2023: We have updated the list of impacted features in the content below. Thanks for your patience, you will receive an additional notice with the date and time of your maintenance.
We have an upcoming service maintenance planned for Intune to improve performance and scalability in the next month. Due to the nature of the maintenance, there will be a brief downtime (up to one hour) where some features and capabilities will be unavailable.
How this will affect you organization:
As part of this planned maintenance, the following feature areas will be affected:
- Reporting: Policy reporting may be unavailable. Additionally, admins may observe stale data for Data Warehouse and app reporting.
- Apps: Admins may be unable to create or edit apps in the Intune admin center.
- Customization policies: Admins may be unable to create or edit customization policies in the Intune admin center.
- Apple Volume Purchase Program (VPP): Admins will not be able to manually sync Apple VPP apps in the Intune admin center.
- Windows Autopilot: During the downtime, you will not be able to complete Windows Autopilot deployments that include Win32 app installations, and you will see an error during the device setup. If you attempt to set up a device during the maintenance and hit an error, you will need to reset the device after the maintenance has ended. For instructions, read Windows Autopilot Reset. Additionally, admins may be unable to manage Autopilot devices and deployment profiles.
- Microsoft Graph API: The following APIs will be unavailable during the maintenance window:
- WindowsAutopilotDeviceIdentities
- WindowsAutopilotDeploymentProfiles
- managedDevices
This maintenance is planned outside of normal business hours, to help minimize any impact to your organization. For organizations with users around the globe, we recognize that "outside of normal business hours" might affect you differently. We apologize for the impact this may have on your admins or users.
What you need to do to prepare:
Review the information above and notify your admins and users about the upcoming maintenance and functionality that may be impacted. We will post another message 5 days before this maintenance, with an exact downtime window for your planning purposes.
MC517323 — (Updated) Plan for Change: App protection and configuration reporting updates
30-60 Days
Updated March 31, 2023: We have updated the content and timing outlined below. Thank you for your patience.
Previously mentioned in MC458650, there are several upcoming changes to app protection and configuration reports to improve and simplify the reporting experience in Microsoft Intune. We will be updating the App protection status report and adding a new report, App configuration status. These reports will have robust filtering allowing you to achieve more slices of data while working from the same report. They will replace the following reports:
- User report
- App report
- User configuration report
- App configuration report
Additionally, we will be removing the following reports (located on the current App protection status report summary view):
- Assigned users
- Flagged users Note: We recommend leveraging compliance reports to determine which devices/users do not meet your organization’s compliance policies, such as jailbroken or rooted devices. For more information, see documentation for Monitor results of your Intune Device compliance policies.
- Users with potentially harmful appsReview documentation for additional system security options.
These changes are expected with Intune's May (2305) service release. At the time of this change or soon after, the corresponding Graph API’s will also be removed.
How this will affect your organization:
After this change, to monitor app protection policies and app configuration policies, leverage the filtering capabilities that will be available for the updated App protection status and new App configuration status reports.
What you need to do to prepare:
Update your documentation, as needed. Change any scripts that call these Graph APIs. Otherwise, no action is required, only awareness.
Additional information:
How to monitor app protection policies
Microsoft Purview
MC538383 — Microsoft Purview eDiscovery (Premium): Enhancements for Teams meeting recordings
<30 Days
Microsoft 365 Roadmap ID 106101
Coming soon to public preview, we're rolling out enhancements to Teams meeting recording and video files stored in OneDrive and SharePoint to improve management within eDiscovery workflows.
When this will happen:
Rollout will begin in early April and is expected to be complete by end of April.
How this will affect your organization:
This update enables collection and review of metadata associated with Teams meeting recordings and video files stored in OneDrive and SharePoint including transcripts/captions, chapters, and custom thumbnails.
What you need to do to prepare:
Assess whether these changes will impact your organization's eDiscovery workflow, then update internal documentation and provide user training as needed.
Get started with eDiscovery (Premium) in the Microsoft Purview compliance portal.
Learn more: Conduct an eDiscovery investigation of content in Microsoft Teams
MC536892 — Microsoft Purview | eDiscovery Premium - Collections progress, statistics, and workflow enhancements (GA)
30-60 Days
Microsoft 365 Roadmap IDs 93381 and 93382
Currently available in public preview (MC423139), we're rolling out enhancements for eDiscovery (Premium) Collections to simplify workflow and provide additional insights for eDiscovery admins.
When this will happen:
Rollout will begin in mid-April and is expected to be complete by late May.
How this will affect your organization:
With this update, eDiscovery admins can better understand the progress of Collections, see statistics on what content contributed to changes between estimated items with hits and actual collected items, and commit the collection directly from the estimate without navigating through the entire collection wizard.
What you need to do to prepare:
Get started with eDiscovery (Premium) in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: Overview of collections in eDiscovery (Premium)
MC535701 — Microsoft Purview Information Protection: Extend sensitivity labels to meetings (GA)
30-60 Days
Microsoft 365 Roadmap ID 117507
You will soon be able to extend Microsoft Purview Information Protection sensitivity labels to meetings.
When this will happen:
Rollout will begin in early May and is expected to be complete by end of May.
How this will affect your organization:
With this update, admins will be able to extend sensitivity labels to Microsoft Outlook appointments, meeting invites in Microsoft Teams and Outlook, and Teams online meetings*. This enables admins to include labeled meetings in the scope of Information Protection policies.
*Note: Applying sensitivity labels to protect Teams online meetings requires Teams Premium licensing.
What you need to do to prepare:
Get started by configuring sensitivity labels in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more:
- Create and publish sensitivity labels
- Learn about sensitivity labels
- Get started with sensitivity labels
MC534746 — Information Protection: Apply default sensitivity label to unlabeled files uploaded to SharePoint document library (GA)
30-60 Days
Microsoft 365 Roadmap ID 85621
Currently available in public preview for Microsoft Purview Information Protection (MC391948), all newly uploaded documents to a document library can “inherit” the configured label for the SharePoint Online document library (if not already labeled).
When this will happen:
This has started rolling out and is expected to be complete by early May.
How this will affect your organization:
Once a document library is configured with a default sensitivity label, SharePoint can ensure that any "new" Microsoft Office files (with no label or low priority label applied via automation or default policy) saved or uploaded to this library will be labeled with the configured library label.
Note that if the uploaded document is manually labeled, its label will not be modified. Moreover, existing unlabeled documents in the library will not be modified unless a user edits the file. The stamping of label is done in an asynchronous thread after the document is uploaded which means that there will be a delay of few minutes before you see the label applied automatically.
To configure a default sensitivity label for an existing SharePoint document library, go to Settings; from the Library settings flyout pane, select Default sensitivity label then choose a label from the drop-down box.
If you're creating a new document library, you can configure the default sensitivity label setting from the Create document library flyout pane.
What you need to do to prepare:
Library owners can turn this feature on or off using the “Edit library settings” option within the SharePoint document library.
Get started with Information Protection in the Microsoft Purview compliance portal.
Learn more: Use sensitivity labels with Microsoft Teams, Microsoft 365 Groups, and SharePoint sites
Important: Using this feature requires any one of the following licenses:
Microsoft Syntex - SharePoint Advanced Management
Microsoft 365 E5/A5/G5
Microsoft 365 E5/A5/G5/F5 Compliance
Microsoft 365 E5/F5 Information Protection and Governance
Office 365 E5/A5/G5
MC532198 — Microsoft Purview Data Lifecycle Management: Retention policy support for legacy Microsoft Teams call data records
>60 Days
Microsoft 365 Roadmap ID 106103
Microsoft Teams call data records (CDRs) are system-generated artifacts that contain information about meetings - for example, who joined and when they joined.
Currently, retention policies for Teams (user chats, standard channels, shared channels, and private channel user messages) only apply to CDRs that were generated after September 21st, 2022.
We now are pleased to include retention policy support for call data records generated prior to this date (legacy CDRs).
When this will happen:
This improvement for retention policy support on legacy CDRs will begin rolling out in April 2023 and rollout is expected to be complete before the end of June 2023.
How this will affect your organization:
Teams CDRs created before September 21, 2022, will now be governed per the rules specified in your Teams user chat and Teams channel messages retention policies. This inclusion happens automatically, no changes are required to your configuration.
Please note that Teams call data records generated from meetings in private channels (different than messages in private channel conversations) will be governed by the same policies as meetings held outside of a channel which are the “Teams chat” messages policies. CDRs for meetings held in standard channels or shared channels will be governed by the policies configured for “Teams channel messages”.
What you need to do to prepare:
No action is needed to enable this change; however, you may want to communicate this change to the team responsible for Data Lifecycle Management at your organization.
MC528979 — Microsoft Purview Data Lifecycle Management: Retention policy support for Microsoft Teams control messages
<30 Days
Microsoft Teams control messages are system-generated artifacts that contain information about actions taken in Teams - for example, adding or removing a user from a chat. These messages show up on the Teams client as system messages. Ex. User A added User B to the chat and shared all chat history. More information on these types of messages can be found here.
Until now, control messages were not included in the supported types of messages for retention policies for Teams (user chats, standard channels, shared channels, and private channel user messages).
We are pleased to announce an improvement to add support for retention and deletion of some types of Teams control messages using retention policies for Teams ("Phase 1"). Phase 1 includes support for control messages generated while adding or removing a member to a chat or Team, within Teams chats and Teams channels locations.
A separate communication will be shared for Phase 2.
When this will happen:
Phase 1 will begin rolling out in late March and will be complete in April.
How this will affect your organization:
These specific types of Teams control messages will now be governed per the rules specified in your Teams user chat and Teams channel messages retention policies. This inclusion happens automatically, no changes are required to your configuration.
What you need to do to prepare:
No action is needed to enable this change; however, you may want to communicate this change to the team responsible for Data Lifecycle Management at your organization.
MC524720 — Microsoft Purview eDiscovery (Premium): New case creation wizard
<30 Days
Microsoft 365 Roadmap ID 101524
We're introducing a new case creation wizard for eDiscovery (Premium) in the Microsoft Purview compliance portal.
When this will happen:
Rollout is now underway and is expected to be complete by early April.
How this will affect your organization:
The eDiscovery (Premium) case creation wizard will guide users through step-by-step configuration of case details in the recently released new case format.
During the case creation process, users will be able to add team members and configure settings such as search and analytics, text to ignore, and optical character recognition.
What you need to do to prepare:
Get started with eDiscovery (Premium) in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: Create and manage an eDiscovery (Premium) case
MC524716 — (Updated) Microsoft Purview eDiscovery (Premium): Review set - List page usability enhancements
<30 Days
Microsoft 365 Roadmap ID 106104
Updated April 6, 2023: We have updated the rollout timeline below. Thank you for your patience.
We're rolling out a set of usability enhancements impacting the Review set list page for the eDiscovery (Premium) solution in the Microsoft Purview compliance portal.
When this will happen:
Rollout will begin in early March and is expected to be complete by late April (previously late March).
How this will affect your organization:
The following enhancements will soon be available:
- Time zone: Switch between your local time and UTC.
- Filter your review sets by columns (size, last modified, collections, exports, and errors)
- Edit review set name and description.
- Get an overview
What you need to do to prepare:
You may wish to update your internal training documents to reflect the UX changes included in this rollout.
Get started with eDiscovery (Premium) in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more:
MC515536 — (Updated) Microsoft Purview | Data Lifecycle Management and Records Management – Microsoft Graph APIs for extensibility
<30 Days
Microsoft 365 Roadmap ID 88276
Updated March 9, 2023: We have updated the rollout timeline below. Thank you for your patience.
As a part of our extensibility vision and first release to Microsoft Graph, we are introducing three new APIs for retention labels, events, and event types in the Microsoft Graph beta environment. These APIs will enable you to customize and extend on what we have built in the product so far.
These APIs can be used by compliance admins and developers to manage retention labels in Data Lifecycle and Records Management solutions.
When this will happen:
Rollout will begin in late March (previously late February) and is expected to be complete by end of April.
How this will affect your organization:
If your organization needs to automate any operation related to retention labels or events, we recommend you achieve this by using the new Graph APIs instead of using PowerShell cmdlets. With Graph, we use REST APIs that support better security, extensibility, and app authentication features.
The three APIs are available under the security node and the endpoints to access them are as follows:
|
Entity name |
Endpoints |
Solution |
|
Labels |
security/labels/retentionLabels |
Data Lifecycle, Records Management |
|
Events |
security/triggers/retentionEvents |
Records Management |
|
Event types |
security/triggerTypes/retentionEventTypes |
Records Management |
What you need to do to prepare:
Permissions
Currently, these APIs are supported through delegated permissions only, which are managed through the Graph interface. We are introducing two new permissions which you will need to access these APIs:
- recordsmanagement.read.all
- recordsmanagement.readwrite.all
Licensing
Access to Data Lifecycle Management and Records Management features varies based on your Microsoft 365 license level. See Microsoft 365 guidance for security & compliance - Service Descriptions for licensing requirement details.
Get started with Data Lifecycle Management and Records Management in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more:
- Use the Microsoft Graph records management API
- Create retention labels for exceptions
- Start retention when an event occurs
MC515529 — (Updated) Microsoft Purview compliance portal: eDiscovery PowerShell cmdlet support for certificate-based authentication
<30 Days
Microsoft 365 Roadmap ID 106112
Updated April 4, 2023: We have updated the rollout timeline below. Thank you for your patience.
We are announcing eDiscovery PowerShell cmdlet’s official support for certificate-based authentication (CBA).
When this will happen:
Rollout will begin in early April (previously late February) and is expected to be complete by late April (previously late March).
How this will affect your organization:
Many organizations rely on unattended scripts built using the security and compliance PowerShell cmdlet to automate eDiscovery workflow. In the past, any unattended script relied on basic authentication techniques where it required the user to store the username and password in a local file or in a secret vault accessed at run-time. This method is no longer recommended as it poses the risk of stolen credentials. See Deprecation of Basic authentication in Exchange Online.
eDiscovery cmdlets will support CBA or app-only authentication as described in this article by end of February 2023. It supports unattended script and automation scenarios by using Azure AD apps and self-signed certificates. Certificate-based authentication provides admins the ability to run scripts without the need to create service-accounts or store credentials locally.
We encourage all eDiscovery users who rely on basic authentication with their unattended script to migrate the script authentication to use CBA as soon as possible. Please note that Service Principal will be needed to run eDiscovery cmdlets. Refer to this article for the steps.
Note:
- This change will affect the authentication method of your organization’s eDiscovery unattended script.
- After basic authentication is changed to CBA your script should be more secure against potential attackers who may be interested in stealing your locally stored credentials.
What you need to do to prepare:
Assess if the changes will change your organization’s eDiscovery automation workflow. If so, you may wish to update internal documentation and script authentication and provide training to all eDiscovery users in your organization.
Get started with eDiscovery in the Microsoft Purview compliance portal:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more: App-only authentication in Exchange Online PowerShell and Security & Compliance PowerShell
MC499443 — Microsoft Purview Data Loss Prevention: Upcoming migration of policy sync engine for Exchange, SharePoint, and OneDrive
30-60 Days
Updated March 30, 2023: We have updated the rollout timeline below. Thank you for your patience.
We’re making changes to the Microsoft Purview Data Loss Prevention (DLP) Policy Synchronization API.
Starting February 2023, we will replace and retire the legacy “Policy Sync Version V1” for DLP that applies to Exchange Online, SharePoint, and OneDrive for Business workloads and migrate all DLP policies from the previous “Policy Sync Version V1” to an upgraded “Policy Sync Version V2”.
When this will happen:
Rollout will begin in early May (previously late February) and is expected to be complete by late May (previously late March).
How this will affect your organization:
The DLP “Policy Sync Version V2” is a more secure and flexible solution that will enable you to access the latest and upcoming features across the entire Microsoft Purview Information Protection solution. This will be a back-end infrastructure upgrade activity that will be carried out by Microsoft.
Once this change is implemented, admins will see a “Last Modified Timestamp” column as the DLP policies* will be updated per the timestamp when Microsoft will be performing the migration on your consent. Changes will be visible in both PowerShell and the Microsoft Purview compliance portal (UX).
*Indicates DLP policies that are scoped to workloads – Exchange Online, SharePoint, OneDrive
What you need to do to prepare:
No action is needed to prepare for this change.
Get started with Information Protection and Data Loss Prevention in the Microsoft Purview compliance portal.
Learn more:
Microsoft Defender
MC536891 — Microsoft 365 Defender: Secure Score availability for government clouds
<30 Days
Microsoft 365 Roadmap ID 109579
Government cloud customers will soon be able to assess their security posture with Microsoft Secure Score.
Microsoft Secure Score will be available for GCC, GCC-High, DoD environments for assessments on the following Microsoft products: Defender for Endpoint, Defender for Office 365, Defender for Identify, Defender for Cloud Apps and 3rd party applications (through Defender for Cloud Apps).
When this will happen:
We will begin rollout in mid-April and expect to complete rollout by late April.
How this will affect your organization:
Microsoft Secure Score will help organizations:
- Report on the current state of the organization's security posture.
- Improve their security posture by providing discoverability, visibility, guidance, and control.
- Compare with benchmarks and establish key performance indicators (KPIs).
(Note: For GCC customers, you will see your Secure Score history calculated from February 9th).
What you need to do to prepare:
There is no action required on your end as this will be enabled automatically. Read more about Microsoft Secure Score in our documentation here.
MC533816 — Microsoft Defender for Endpoint: RealTimeSignatureDelivery will be Enabled for all Customers
30-60 Days
Microsoft Defender for Endpoint will be changing the behavior of RealtimeSignatureDelivery.
When this will happen:
We will be releasing this update in early April and expect rollout to be complete by mid-May.
How this will affect your organization:
With the new release, RealTimeSignatureDelivery will no longer be configurable by end-users, and it will be set to its default value which is enabled. Changes to this setting may appear to succeed, but the changes are being ignored and the value will always stay enabled.
This action is being taken to address issues raised by customers related to enabling tamper protection. Tamper protection was unexpectedly failing when RealtimeSignatureDelivery was disabled, and based on our analysis, there are currently no valid reasons to have RealtimeSignatureDelivery disabled.
What you need to do to prepare:
There is no action required in advanced on this change.
If you have any questions, please reach out to Microsoft Support or visit this documentation.
MC525142 — Safe Documents in Microsoft 365 apps
30-60 Days
We're pleased to announce that Safe Documents will be available soon in your environments. With Safe Documents, we’re bringing the power of Microsoft Defender for Endpoint to the desktop to verify that documents are safe at the endpoint.
When this will happen:
We will begin rolling this out in early April and expect to complete rollout by end of May, 2023.
How this will affect your organization:
Safe Documents improves the existing Protected View experience. Although Protected View helps secure documents originating outside the organization, people too often exit the protection sandbox without considering if the document is safe – leaving their organizations vulnerable. Safe Documents takes away the guesswork by automatically verifying the document against the latest known risks and threat profiles before allowing users to leave the Protected View container.
Note: This feature is already available in Microsoft 365 G5 for GCC.
Learn more:
- Safe Documents in Microsoft 365 E5 or A5 Security
- Safe Documents is Generally Available - Microsoft Tech Community
What you need to do to prepare:
Depending on your organization's Microsoft 365 Defender configuration, this feature may already be configured. To update the configuration in the Microsoft 365 Defender portal, see the instructions here.
You may want to notify your users about this change and update your training and documentation as appropriate.
MC509914 — (Updated) Network Protection for macOS starting deployment to General Availability on 1/31!
30-60 Days
Updated March 28, 2023: We have updated the rollout timeline below. Thank you for your patience.
Network Protection for macOS will soon be available for all Microsoft Defender for Endpoint onboarded macOS devices which meet the following criteria:
- Licensing: Microsoft Defender for Endpoint tenant (can be trial)
- Onboarded Machines:
- Minimum macOS version: 11 (Big Sur)
- Product version 101.94.13 or later
Note: If your organization does not utilize macOS devices you can safely disregard this message.
When this will happen:
Standard Release: Microsoft will begin incrementally rolling out the functionality for all macOS devices to enable Network Protection on January 31, 2023 with target completion, subject to change, by May 2023 (previously March).
How this will affect your organization:
When this feature rolls to production, all of your currently configured Network Protection and Web Threat Protection policies will be enforced on macOS devices where Network Protection is configured for block mode.
What you need to do to prepare:
For Network Protection for macOS to be active on your devices, Network Protection must be enabled by your organization. We suggest deploying the audit or block mode policy to a small set of devices and verify there are no issues or broken workstreams before gradually deploying to a larger set of devices.
Verify the Network Protection configuration on your macOS devices is set to the desired state.
Understand the impact of your Web Threat Protection, Custom Indicators of Compromise, Web Content Filtering, and MDA Endpoint Enforcement polices which target those macOS devices where Network Protection is in Block mode.
Identity
MC536889 — Updates to the User Administrator role in Microsoft Entra Entitlement Management
<30 Days
On May 3, 2023, Microsoft will update Microsoft Entra Entitlement Management. This update will remove the ability for a user in the User Administrator role to manage Entitlement Management catalogs and access packages. If your organization has relied on users having the User Administrator role to manage Entitlement Management catalogs and access packages, add those users to the Identity Governance Administrator role. This ensures that those users can manage catalogs and access packages in Entitlement Management.
We want to ensure minimal customer impact when we remove Entitlement Management permissions from the User Administrator role. By assigning admins the Identity Governance Administrator role, they will have the necessary permissions to continue managing catalogs and access packages.
In order to assign a user the Identity Governance Administrator role, follow these steps:
- Sign in to the Azure Active Directory admin center with Privileged Role Administrator permissions.
- Select Azure Active Directory > Roles and administrators.
- Select Identity Governance Administrator.
- Select Add assignments and add the users to whom you wish to assign this role.
You can also update these role assignments using Graph API. You can find more information on how to do that in our documentation.
Additionally, you can read more about roles and permissions here.
We greatly appreciate your understanding and cooperation as we release this update. In the meantime, if you have any questions or concerns, please feel free to file a support case.
MC532607 — Microsoft Authenticator Lite in Outlook
30-60 Days
Microsoft 365 Roadmap ID 122289
Authenticator Lite (in Outlook) is a feature that allows your users to complete multi-factor authentication for their work or school account using Outlook on their iOS or Android device. This feature will be enabled on May 26th for all tenants that have not disabled it. If you do not wish for this feature to be enabled on May 26th, move the state to ‘disabled’ or set user include and exclude groups prior to May 26th.
We always recommend having users download Authenticator to complete their sign-ins, where we can offer the most up-to-date security features. However, users that have not downloaded the app to their device can now approve authentication requests and receive TOTP codes in Outlook, bringing the security of Authenticator to a convenient location.
Admins can enable this feature by leveraging the Authentication Methods policy in Azure Active Directory.
When this will happen:
Rollout of this feature in Outlook will begin in early March, starting public preview. Feature controls are available via MS Graph.
This feature will move to general availability in late April 2023.
On May 26th, this feature will be enabled for all users by default unless admins have taken action to disable or enable it before then. Any settings configured before May 26th will not be changed.
What you need to do to prepare:
Starting mid-March, you can choose to enable this preview for your users from Azure Active Directory. We highly recommend that you enable users that are not already using the Microsoft Authenticator app (or another strong authentication method) for this feature at the start of public preview. This feature brings a security enhancement to those users still using telecom transports to authenticate.
This feature will roll out to tenants in the state ‘Microsoft managed’. For the duration of public preview, leaving the feature set to ‘Microsoft managed’ will have no impact on your users and the feature will remain turned off. In April 2023, we will remove preview tags and enter general availability. At GA, 'Microsoft managed' will remain set to disabled and there will be no tenant impact. On May 26th 2023, if the feature is still set to ‘Microsoft managed’, your tenant will be eligible to be enabled for this feature by Microsoft, as 'Microsoft managed' will be set to enabled. If you do not wish for this feature to be enabled on May 26th, move the state to ‘disabled’ or set users to include and exclude group prior to May 26th.
MC523051 — (Updated) Announcing Public preview - System preferred multi-factor authentication method
>60 Days
Updated April 6, 2023: We have updated the content with additional information. Thank you for your patience.
Today, various authentication methods are employed by users to provide varying levels of security. Depending on the situation, certain methods may be more secure than others, so it is important to have a range of options available to ensure the right level of security is provided.
Today we are announcing our solution for this challenge: System-preferred authentication for MFA –where we will evaluate at runtime, which is the most secure method for the user, of the methods the user has registered. This will help us move away from the erstwhile concept of the user selecting a ‘default’ method and always being prompted for that method first, even when more secure methods are registered and available.
When this will happen:
Public Preview: We will begin rolling out on March 1st, 2023.
How this will affect your organization:
In this feature, “System preferred multi-factor authentication method,” Microsoft will decide and prompt which among the user’s registered methods should be prompted for 2nd factor. This would be decided on run time and would be the best method of the methods registered at that given point in time.
This feature will be off by default, please enable this feature using MSGraph API. Once enabled, users will be required to sign in using the most preferred authentication method available.
This is an excellent approach for users to move away from the less secure telephony methods.
Presently the feature is in Private preview and the admins have the control to turn the feature On/Off using GraphAPI.
The public preview experience will be similar to the private preview where the admins will use the GraphAPI to turn on/off the feature. By the end of March, the admin screen will be available to the user. There would be a toggle available to configure the feature
At GA (in April), Microsoft managed will be set to "disable". Admins will have the UX and the toggle available
At GA+2 months (June), Microsoft managed will be set to "enable". The toggle will be available
At GA+ 6 months (October) Toggle will be taken away from the users and the feature will be enabled for all by default
What you need to do to prepare:
Review the documentation to determine whether or not to enable for your organization.
MC498471 — (Updated) IPv6 coming to Azure AD
Rolled Out
Updated March 21, 2023: Earlier, we had announced our plan to bring IPv6 support to Microsoft Azure Active Directory (Azure AD) enabling our customers to reach the Azure AD services over IPv4, IPv6 or dual stack endpoints. This is just a reminder that we’ll begin introducing IPv6 support into Azure AD services in a phased approach, starting March 31st, 2023.
If your networks don’t support IPv6, you don’t need to take any action to change your configurations or policies. For most customers, IPv4 won't completely disappear from their digital landscape, so we aren't planning to require IPv6 or to de-prioritize IPv4 in any Azure AD features or services. We will continue to share additional guidance on IPv6 enablement in Azure AD at this easy to remember link https://aka.ms/azureadipv6.
With the growing adoption and support of IPv6 across enterprise networks, service providers, and devices, many customers are wondering if their users can continue to access their services and applications from IPv6 clients and IPv6 networks.
Today, we’re excited to announce our plan to bring IPv6 support to Microsoft Azure Active Directory (Azure AD). This will allow customers to reach the Azure AD services over both IPv4 and IPv6 network protocols (dual stack).
For most customers, IPv4 won't completely disappear from their digital landscape, so we aren't planning to require IPv6 or to de-prioritize IPv4 in any Azure Active Directory features or services.
When this will happen:
We’ve been gradually rolling out IPv6 for some of our services for a while. Starting in late March 2023 we'll begin enabling IPv6 for Azure AD authentication. We will introduce IPv6 support into Azure AD authentication in a phased approach, beginning late March 2023.
What you can do to prepare:
We have guidance below which is specifically for Azure AD customers, who use IPv6 addresses and also use Named Locations in their Conditional Access policies.
If you have public IPv6 addresses representing your network, take the actions that are described in the following sections as soon as possible.
Customers who use named locations to identify specific network boundaries in their organization, need to:
- Conduct an audit of existing named locations to anticipate potential impact;
- Work with your network partner to identify egress IPv6 addresses in use in your environment.;
- Review and update existing named locations to include the identified IPv6 ranges.
Customers who use Conditional Access location based policies, to restrict and secure access to their apps from specific networks, need to:
- Conduct an audit of existing Conditional Access policies to identify use of named locations as a condition to anticipate potential impact;
- Review and update existing Conditional Access location based policies to ensure they continue to meet your organization’s security requirements.
Failing to follow these steps might result in the following impact:
- Users of IPv6 addresses may be blocked, depending on your organization's Conditional Access policies and Identity Protection configurations.
- False positive detections due to 'Mark as trust location' not being checked for your internal networks and VPN’s can result in users being marked as risky.
We will continue to share additional guidance on IPv6 enablement in Azure AD here: IPv6 Support in Azure Active Directory.
Learn more about Microsoft identity:
- Get to know Microsoft Entra – a comprehensive identity and access product family
- Return to the Microsoft Entra (Azure AD) blog home
- Share product suggestions on the Entra (Azure AD) forum
MC477013 — (Updated) Microsoft Entra admin center unites Azure AD with family of identity and access products
Rolled Out
Updated March 22, 2023: Beginning April 1, 2023, Azure AD Admin Center (https://aad.portal.azure.com) will redirect to Microsoft Entra Admin Center (https://entra.microsoft.com). You will still be able to complete all your Azure AD management tasks from within the new admin center. To ensure uninterrupted access to the management experience, organizations should update their firewall rules.
Will I still be able to access my Azure AD admin portal after April 1st, 2023?
- The Azure AD admin center (https://aad.portal.azure.com) will continue to function until May 2023.
- The Azure portal at https://portal.azure.com will also continue to offer Azure AD for Azure customers.
Microsoft Entra documentation | Microsoft Learn
Microsoft Entra admin center gives customers an entire toolset to secure access for everyone and everything in multicloud and multiplatform environments. The entire Microsoft Entra product family is available at this new admin center, including Azure Active Directory (Azure AD) and Microsoft Entra Permissions Management, formerly known as CloudKnox.
Starting this month, waves of customers will begin to be automatically directed to entra.microsoft.com from Microsoft 365 in place of the Azure AD admin center (aad.portal.azure.com).
You will still be able to complete all your Azure AD management tasks from the Microsoft Entra admin center – all the capabilities are available under the Azure AD tab in the navigation. Also, you’ll be able to return to the Azure AD admin center from a link on the Entra admin center.
When this will happen:
We will begin rollout in December 2022 and expect rollout to be completed in March 2023.
How this will affect your organization:
During the rollout customers who click the Azure Active Directory links in the Microsoft 365 admin center will now be redirected to the new Entra Admin Center.
What you need to do to prepare:
To ensure uninterrupted access to the management experience, you might need to update your firewall rules to allow *.entra.microsoft.com.
The Microsoft Entra admin center is available today at http://entra.microsoft.com, and we encourage you to explore it in preparation for the full migration.
MC468492 — (Updated) Authenticator number matching to be enabled for all Microsoft Authenticator users
30-60 Days
Updated March 16, 2023: We have updated the timing of this change, below. Thank you for your patience.
Microsoft Authenticator app’s number matching feature has been Generally Available since Nov 2022! If you have not already leveraged the rollout controls (via Azure Portal Admin UX and MSGraph APIs) to smoothly deploy number matching for users of Microsoft Authenticator push notifications, we highly encourage you to do so. We had previously announced that we will remove the admin controls and enforce the number match experience tenant-wide for all users of Microsoft Authenticator push notifications starting February 27, 2023. After listening to customers, we will extend the availability of the rollout controls for a few more weeks. Organizations can continue to use the existing rollout controls until May 8, 2023, to deploy number matching in their organizations. Microsoft services will start enforcing the number matching experience for all users of Microsoft Authenticator push notifications after May 8th, 2023. We will also remove the rollout controls for number matching after that date.
Please note that we have changed the expected behavior for NPS extension to be even more admin friendly. NPS versions 1.2.2216.1+ will be released once Microsoft starts to enable number matching for all Authenticator users. These NPS versions will automatically prefer OTP based sign-ins over traditional push notifications with the Authenticator app. An admin can choose to disable this behavior and fallback to traditional push notifications with Approve/Deny by setting the registry key OVERRIDE_NUMBER_MATCHING_WITH_OTP Value = FALSE. Previous NPS extension versions will not automatically switch Authenticator push notification authentications to OTP based authentications. Please refer to the NPS extension section of the number match documentation for further information.
When this will happen:
Beginning in May 2023.
How this affects your organization:
To prevent accidental approvals, admins can require users to enter a number displayed on the sign-in screen when approving an MFA request in the Microsoft Authenticator app. This feature is critical to protecting against MFA fatigue attacks which are on the rise.
Another way to reduce accidental approvals is to show users additional context in Authenticator notifications. Admins can now selectively choose to enable the following:
- Application context: Show users which application they are signing into.
- Geographic location context: Show users their sign-in location based on the IP address of the device they are signing into.
Number match behavior in different scenarios after May 2023:
- Authentication flows will require users to do number match when using the Microsoft Authenticator app. If the user is using a version of the Authenticator app that doesn’t support number match, their authentication will fail. Please make sure upgrade to the latest version of Microsoft Authenticator (App Store and Google Play Store) to use it for sign-in.
- Self Service Password Reset (SSPR) and combined registration flows will also require number match when users are using the Microsoft Authenticator app.
- ADFS adapter will require number matching on versions of Windows Server that support number matching. On earlier versions, users will continue to see the “Approve/Deny” experience and won’t see number matching till you upgrade.
- NPS extension versions beginning 1.2.2131.2 will require users to do number matching after May 2023. Because the NPS extension can’t show a number, the user will be asked to enter a One-Time Passcode (OTP). The user must have an OTP authentication method (e.g. Microsoft Authenticator app, software tokens etc.) registered to see this behavior. If the user doesn’t have an OTP method registered, they’ll continue to get the Approve/Deny experience. You can create a registry key that overrides this behavior and prompts users with Approve/Deny. More information can be found in the number matching documentation.
- Apple Watch – Apple Watch will remain unsupported for number matching. We recommend you uninstall the Microsoft Authenticator Apple Watch app because you have to approve notifications on your phone.
What you can do to prepare:
If customers don’t enable number match for all Microsoft Authenticator push notifications prior to May 8, 2023, users may experience inconsistent sign-ins while the services are rolling out this change. To ensure consistent behavior for all users, we highly recommend you enable number match for Microsoft Authenticator push notifications in advance.
Learn more at:
- Number match documentation
- Defend your users from MFA fatigue attacks - Microsoft Community Hub
- Advanced Microsoft Authenticator security features are now generally available! - Microsoft Communit...
MC382822 — (Updated) Insider Risk Management: General availability of security policy violations templates
>60 Days
Microsoft 365 Roadmap IDs 83961, 83962, and 83963
Updated April 6, 2023: We have updated the rollout timeline below. Thank you for your patience.
Currently available in public preview (MC289678), we're releasing additional features for Insider Risk Management that will help detect possible security violations by users including priority and departing users. These features will help enable your organization to detect security violations performed on devices onboarded to your organization using Microsoft Defender for Endpoint alerts.
When this will happen:
Rollout will begin in early July 2022 (previously late June 2022) and is expected to be complete by late June 2023 (previously late March).
How this will affect your organization:
The following policy templates will soon be generally available:
General security policy violations policy template detects general security violations by users. Based on severity of the Defender for Endpoint alert, a risk score will be assigned to a user's activity and alerts will then be generated based on activity severity.
Security violations by priority users policy template detects security violations by priority users which may have a significant impact on your organizations' critical areas. This policy template uses Microsoft Defender for Endpoint alerts to provide insights into security-related activities for these users.
Security policy violation by departing users policy template detects any inadvertent or malicious security violations for departing users and uses Microsoft Defender for Endpoint alerts to provide insights into security-related activities.
What you need to do to prepare:
You'll need to have Microsoft Defender for Endpoint configured in your organization and enable Defender for Endpoint for insider risk management integration in the Defender Security Center to import security violation alerts. For more information on configuring Defender for Endpoint for insider risk management integration, see Configure advanced features in Microsoft Defender for Endpoint.
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, security and policy violations, and more. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
You can access the Insider Risk Management solution:
- Microsoft Purview compliance portal for WW and GCC cloud environments
- Microsoft Purview compliance portal for GCC-High cloud environments
- Microsoft Purview compliance portal for DoD cloud environments
Learn more:
- General security policy violations
- Security policy violations by priority users
- Security policy violations by departing users
Exchange Online / Defender for Office 365
MC535702 — Upcoming behavior change to the "DoNotRewrite" List
<30 Days
With the deployment of the Tenant Allow/Block List, as being the single source of truth for Tenant Allows, other mechanisms for Tenant Allows are being removed. This will give SecOps teams one place to manage all Tenant Allows.
Today, the “DoNotRewrite” list is used to Skip:
- Wrapping URLs
- Detonation
- Verdicts
The intended purpose of "DoNotRewrite" is to give tenants the ability to skip the wrapping of URLs. With the deployment of the Tenant Allow Block List, it is expected that all tenant allows (ex Detonation and Verdicts) shall be managed there.
When this will happen:
In late April the entries on the Do Not Rewrite list will only skip Safe Links wrapping. After this change is made, entries on the Do Not Rewrite list will no longer skip Detonations or Verdicts in mailflow or at Time of Click.
In late April the following capabilities will be removed from the DNR list:
- Skip Detonation
- Skip Verdicts
How this will affect your organization:
With this change, the "DoNotRewrite" list behavior will be changed back to its intended purpose to skip the wrapping of URLs: Learn More here.
What you need to do to prepare:
Review your "DoNotRewrite" URLs list(s) and ensure you have not added entries to it for uses other than to skip wrapping of URLs.
MC535264 — Outlook: Mandatory Labeling Before Composing Emails for Mobile Users
30-60 Days
Microsoft 365 Roadmap ID 109544
We have listened to customer feedback for Outlook mobile needing to meet the mission of "On the Go", and for organizations to have mandatory labeling enabled without default labeling. We are releasing a feature that will allow Outlook mobile users to have a label selection before composing an email to send.
This release will also include a new sensitivity bar below the subject line as well as support label colors.
When this will happen:
Android: We will begin rolling out in mid-April and expect rollout to be complete by early May.
iOS: We will begin rolling out in late April and expect rollout to be complete by mid-May.
How this will affect your organization:
Outlook mobile will introduce a new MDM setting to allow admins to enable this mandatory configuration for Outlook mobile clients (iOS and Android) specifically. We will enable Android first in early Q1 of 2023, and iOS will release in Q2 of 2023.
If your organization wants to have a prompt mandatory label experience prior to composing an email, make sure you enable mandatory labels for specific users and then set the Intune MDM setting "com.microsoft.outlook.Mail.LouderMandatoryLabelEnabled" to be "true." The applied users will then see the select label page first before drafting a new email.
If your organization has set the Label policy -AdvancedSettings @{HideBarByDefault="False"}, on Outlook mobile you will see the label selection is now below the subject line. If you do not set that value or set it to be True, the Sensitivity label will still be under the ellipsis when composing a new email.
Outlook for Android will also support label colors if admins have configured to do so.
What you need to do to prepare:
If you do not want the prompt mandatory UX or the new sensitivity bar, you do not need configure any settings for it. The default new UX will be OFF by default.
MC535260 — Microsoft Defender for Office allows submission of up to 100 emails
30-60 Days
Microsoft 365 Roadmap ID 115509
Applicable to Tenants with Exchange Online Protection, Microsoft Defender for Plan 1 or Plan 2 or Microsoft 365 Defender plan.
Coming soon, Microsoft Defender for Office 365 will allow you to submit up to 100 emails at once from quarantine, threat explorer (or real-time detections tool) and User reported page to Microsoft for analysis.
When this will happen:
This change will start rolling out late April 2023 and will be completed by mid-May 2023.
How this will affect your organization:
This will allow you to make fewer manual submissions while increasing the number of emails you can submit at once.
What you need to do to prepare:
There is no action needed to prepare for this change. You may want to notify your users about this change and update any relevant documentation as appropriate.
MC532602 — Tenant Allow/Block List will allow related URLs
<30 Days
Applicable to Tenants with Exchange Online Protection, Microsoft Defender for Plan 1 or Plan 2 or Microsoft 365 Defender plan.
Email messages can be blocked because of a bad URL where the URL is a matched based on a sub path or portion of the URL contained in the message. In the case of a legitimate email getting blocked, this was difficult to correct through a submission. We have updated the way that we handle allowed URLs such that the partial matching behavior is included without the need to include wild cards or making multiple URL submissions.
Emails with this URL are being blocked www.contoso.com/abc.
You submit the email or the URL to Microsoft for analysis, and an allow entry is created for www.contoso.com/abc in the Tenant Allow/Block List.
If future emails contain URLs that are related to the allow entry, the emails won’t be blocked based on the URL. For example (but not limited to): www.contoso.com/abc or www.contoso.com/abc?id=1 or www.contoso.com/abc/def/gty/uyt?id=5.
When this will happen:
We will begin rolling out late March 2023 and expect to complete by mid-April 2023.
How this will affect your organization:
Now, when submitting an email or original URL as a False Positive (FP) to Microsoft, the URL will be added to the Allow list and handled correctly, removing the need to make multiple submissions.
What you need to do to prepare:
You don't need to do anything for existing or new URL allow entries in the Tenant/Allow Block List.
MC532600 — Easier to filter and sort messages reported by users
<30 Days
Microsoft 365 Roadmap ID 100159
Applicable to Tenants with Exchange Online Protection, Microsoft Defender for Plan 1 or Plan 2 or Microsoft 365 Defender plan.
It is easier to filter and sort messages now reported by end users either through Microsoft report message add-in or Microsoft report phish add-in or Outlook Web Access build-in report button on User Reported under Submissions.
When this will happen:
We will begin rolling out mid-April 2023 and expect to complete by late April 2023.
How this will affect your organization:
It will make it easier for you to triage and look through the emails reported by end users.
You can filter messages by the report types and phish simulation.
You can sort the reports by columns either in ascending or descending order.
You can filter either using a custom range or using pre-defined time periods.
You can apply multiple filters at once while triaging end user reports.
What you need to do to prepare:
You don't need to take any action to enable these changes.
If you have any feedback, please provide it from this Message center post using the text box after you do thumbs up or thumbs down as it will directly reach the responsible team.
MC531738 — Launching new way to open links in Edge from Outlook for iOS and Android
<30 Days
Currently users open links automatically from Outlook for iOS and Android in their default browser. This change will prompt users to choose their browser instead. Users can choose their default browser if they prefer and configure that preference in their Outlook Mobile settings.
We apologize for not communicating about this change sooner, per our commitment to proactive change communication.
When will this happen:
This is currently rolling out.
How will this affect your organization:
- Users will be seeing this experience launch when they open a link.
- If Edge is not installed, they will have the option to download it.
- We are working on a configuration for you to manage this feature if there is a browser your workplace already uses and will provide an update, via Message center, in the coming weeks.
MC528356 — (Updated) Microsoft Defender for Office 365: Filter Update for Quarantine Portal
>60 Days
Microsoft 365 Roadmap ID 117520
Updated April 4, 2023: We have updated the rollout timeline below. Thank you for your patience.
In the Microsoft 365 Defender portal, the Admin / SecOps can review quarantined messages on the Email & Collaboration > Review > Quarantine page. On this quarantine page, all the quarantined email messages are listed. These messages can be quarantined if the messages are classified as malicious or spam or other admin actions. Admins/ SecOps can view messages which are quarantined due to a specific policy anti-malware, Safe Attachments, anti-spam, etc.) with a specific reason for quarantining. These reasons are Phish, Malware, Spam etc.
When this will happen:
Standard Release: We will begin rollout in mid-May (previously early April) and expect to complete rollout by late June (previously late May).
GCC, GCC-H, DoD: We will begin rollout in mid-June (previously mid-May) and expect to complete rollout by late July (previously late June).
How this will affect your organization:
In the anti-malware policy, along with quarantining messages with attachments that are malicious (malware or phish), the common attachment filter settings can be configured to quarantine messages which contain attachments with specific file extensions. All of these email messages with specific file extensions are shown as Malware for the filter Quarantine reason. As a result, it’s not easy to identify messages that were quarantined due to attachments being malicious or simply matching the file type.
With this change, we’re adding a new filter known as Admin Action – File type block to the Quarantine reason filter. Applying this filter will show the email messages that were quarantined by the common attachment filter. This change will be visible on the Quarantine page and also in the respective Get-QuarantineMessage cmdlet (parameter QuarantineTypes to include AdminActionFileTypeBlock).
With the addition of this filter, it should make it easy for the Admin / SecOps to filter and review the messages which are blocked purely due to file type block.
What you need to do to prepare:
There is no action required on your end at this time. For more information, please visit this documentation.
MC525759 — MDO: Safe Attachments policy: Deprecate policy action ‘Replace’ for malware detections in attachments (Phase 2)
>60 Days
In Safe Attachment policies, as part of Phase 1 changes for ‘Replace’ action retirement (MC424901 August '22), the behavior of the ‘Block’ action was applied to the policies configured with ‘Replace’ action.
As part of Phase 2 of the ‘Replace’ action retirement work, the ‘Replace’ action selection will be removed from the Safe Attachment policies (Microsoft 365 Defender portal and cmdlets). As part of this change, any policies still configured with the ‘Replace’ action will be automatically changed to the ‘Block’ action.
When this will happen:
This change will start rolling out from mid-April 2023 and worldwide deployment will be complete by mid-May 2023. For Government clouds, the deployment will start in mid-June 2023 and will be complete by late-June 2023.
How this will affect your organization:
Once this change is rolled out, the ‘Replace’ action will no longer be available in Safe Attachment policies.
What you need to do to prepare:
No action is needed. Any Safe Attachments policies with the ‘Replace’ action will be updated to the ‘Block’ action.
Please review to learn more:
MC525658 — (Updated) Alerts when end user report a message as junk or not junk
Rolled Out
Microsoft 365 Roadmap ID 115510
Updated March 16, 2023: We have updated the content below for clarity. Thank you for your patience.
Applicable to Tenants with Exchange Online Protection, Microsoft Defender for Plan 1 or Plan 2 or Microsoft 365 Defender plan.
Today, Microsoft only generates alerts when end user reports an email as phish from outlook - "Email reported by user as malware or phish" (alert name)
Starting March 20th, 2023, Microsoft will start generating alerts when end user reports an email as junk or not junk.
- "Email reported by user as junk" (alert name) whenever end user reports an email -
- As junk from any folder within outlook either using the report message add-in or the built-in button within outlook for web.
- "Email reported by user as not junk" (alert name) whenever end user reports an email -
- As not junk from the junk folder within outlook either using the report message add-in or the built-in button within outlook for web.
- As not junk from end user quarantine folder.
Note: Regardless of whether user reports from Report-Message or Report Phish Add-ins or Outlook Web Access built-in report button, the alerts will be generated.
When this will happen:
The change will start rolling out in mid-March 2023 and will complete in late March 2023.
How this will affect your organization:
You might find these alerts within the alerts tab once the feature has been rolled out.
What you need to do to prepare:
You don't have to do any work to enable these two new alerts within your tenant as they are on by default.
To manage the alerts, follow the instructions mentioned here.
MC522572 — (Updated) Microsoft Defender for Office 365: Introducing the new Post-delivery Activities Report
<30 Days
Microsoft 365 Roadmap ID 117516
Updated April 4, 2023: We have updated the rollout timeline below. Thank you for your patience.
The new Post-delivery activities report will provide you with information on all things Zero Hour Auto-Purge (ZAP). From the report, you can view messages that were initially delivered but were later moved due to a threat.
When this will happen:
Standard Release: We will begin rolling this out in early March and expect to complete rollout by late April (previously late-March).
How this will affect your organization:
The new report will display all the ZAP events that occurred in your organization. If the verdict assigned to a message has been changed, the new report will display this updated data, making it easier to investigate the messages.
You can find the Post-delivery activities report under Email & collaboration reports.
What you need to do to prepare:
You may want to consider updating your training and documentation as appropriate.
You can review the following resources to learn more:
- View email security reports in the Microsoft 365 Defender portal
- View Defender for Office 365 reports in the Microsoft 365 Defender portal
- Introducing the New Post-delivery Activities Report in Microsoft Defender for Office 365
MC519224 — (Updated) New Message Recall in Exchange Online rolling out now
<30 Days
Microsoft 365 Roadmap ID 59438
Updated March 28, 2023: We have updated the rollout timeline below. Thank you for your patience.
The new Message Recall feature in Exchange Online is starting to roll out now and should be available to all Exchange Online tenants worldwide by mid-March. The new feature is more than twice as effective at successfully recalling messages than the classic Outlook for Windows Message Recall feature, and offers a single aggregated recall status report for each recall. Learn more here.
When this will happen:
We started rolling it out mid-February and expect to complete the roll-out by early April (previously mid-March).
How this will affect your organization:
When your organization’s users with mailboxes hosted in Exchange Online try to recall a message we’ll use the new cloud-based message recall feature to recall the message instead of the classic Outlook for Windows client based feature. Your end-users will experience significantly higher recall rates than ever before, typically > 95% for messages to recipients within the organization.
What you need to do to prepare:
There’s nothing you need to do for your end-users to take advantage of this functionality, it’s automatically done for them in the cloud.
However, should you wish to disable the new cloud-based Message Recall for your organization, or disable recalling read messages, you can use the following Remote PowerShell cmdlets:
- Disable the new Message Recall for your entire tenant: Set-OrganizationConfig -MessageRecallEnabled $false
- Disable recalling read messages: Set-OrganizationConfig -RecallReadMessagesEnabled $false
The setting to disable recalling read messages is also available in the Exchange Admin Center: EAC > Settings > Mail flow
MC516348 — (Updated) DMARC aggregate reports for enterprise
Rolled Out
Microsoft 365 Roadmap ID 109535
Updated March 21, 2023: We have updated the content below with additional details. Thank you for your patience.
As part of the DMARC (Domain-based Message Authentication Reporting & Conformance) standard, the owner of the domain whose MX is pointed to Office 365 can request DMARC aggregate reports through the RUA of the DMARC record. This will help the domain owner to monitor their domain's traffic passing through Office 365 and adjust their sender authentication configurations to reach an actionable DMARC policy.
When this will happen:
Standard Release: We will begin rolling out mid-March (previously mid-February) and expect to complete by late March.
How this will affect your organization:
Domain owners will receive DMARC reports to RUA email addresses.
What you need to do to prepare:
Office 365 will send out DMARC aggregate reports to all sender domain owners that has a valid RUA address defined in their DMARC record, independent of their platform/configuration. The only exception is if the MX record for the recipient domain does not directly points to Office 365. In this case Office 365 will not send DMARC reports to the sender domain owner RUA address.
For example, you have mailboxes with the recipient domain contoso.com, which domain has it's MX record pointed directly to Office 365. (contoso-com.mail.protection.outlook.com). In this scenario Office 365 will automatically send DMARC aggregate reports to all email sender domain owners which has a valid RUA address defined in their domain DMARC record.
If contoso.com MX record pointed to a different email security solution in front of Office 365, Office 365 will not send DMARC aggregate reports to any sender domains RUA address configured in their DMARC record as the information we see about the sending infrastructure is likely to have been affected by the complex mail flow routing.
You can learn more about DMARC here
MC505088 — (Updated) Microsoft Defender for Office 365: Quarantine Notifications enabled for Preset Security Policies
<30 Days
Updated March 22, 2023: We have updated the rollout timeline below. Thank you for your patience.
We are updating the recommended quarantine notification policy in the Standard and Strict preset security policies.
With the DefaultFullAccessWithNotificationPolicy, Users will receive quarantine notifications for emails quarantined due to the corresponding threat policy.
*Note that the Quarantine policy assigned here is ineffective since the delivery location is Junk folder
Here is what the quarantine notification looks like:
When this will happen:
We will begin rolling this out in mid-February 2023 and complete rolling out by mid-April 2023 (previously mid-March).
How this will affect your organization:
If your organization has enabled preset security policies, these will be automatically updated to include the quarantine notification policies (DefaultFullAccessWithNotificationPolicy) as listed in the above table for the standard and strict protection preset profiles.
What you need to do to prepare:
No action required. Please review the following links to learn more:
- What are quarantine notifications? Quarantine notifications (end-user spam notifications) in Microsoft 365 - Office 365 | Microsoft Lea...
- Specific controls set in Preset Security Policies: Microsoft recommendations for EOP and Defender for Office 365 security settings - Office 365 | Micro...
- We recommend enabling preset security policies for your organization: Steps to quickly set up the Standard or Strict preset security policies for Microsoft Defender for ...
MC504323 — (Updated) Microsoft Defender for Office 365: Built-in Protection Time of Click URL Email Protection
<30 Days
Updated April 4, 2023: We have updated the timeline below. Thank you for your patience.
Last year, we enabled Built-in-Protection in Defender for Office 365 by default for all new and existing Defender for Office 365 customers. Specifically, it added a base level of Safe Links and Safe Attachment protections - delivery time file and URL detonation as well as time of click protection across Teams, and Office workloads.
We are now enabling the final remaining aspect of the built-in protection policy: SafeLinks URL time of click email protections.
When this will happen:
We will begin rollout in late February and expect rollout to be complete by mid-April (previously late March).
How this will affect your organization:
Built-In-Protection will not impact users who currently have a Safe Links or Safe Attachments policy in place.
Note: For users already covered under the standard or strict preset; or under an explicit custom policy, built-in protection will not impact them as this policy has the lowest priority.
Policies will be applied in the following order of precedence:
- Strict
- Standard
- Custom
- Built-In-Protection or default
If additional domains are added to your tenant, they will automatically be protected through Built-In-Protection with a base level of Safe Links and Safe Attachment. This will reduce the administrative burden and time involved to protect these users, as they'll get instant protection under the Built-in preset.
What you need to do to prepare:
No security admin action is required. You may want to review the impact to users who are not already protected under a standard or strict preset or under an explicit Safe Links and Safe Attachment custom policy. Although we do not recommend it, you can also configure exceptions to built-in protection based on Users, Groups, and Domains so the protection isn't applied to specific users.
To learn about the specific settings set by Built-in-Protection, please see: Microsoft recommendations for EOP and Defender for Office 365 security settings
Additional links:
MC501737 — (Updated) Outlook on the web - Update locations to message compose options
<30 Days
Microsoft 365 Roadmap ID 98114
Updated March 16, 2023: We have updated the rollout timeline below. Thank you for your patience.
Originally announced in MC427760 (September '22), Outlook on the web is updating where some message-compose options are located, depending on how you use Outlook.
- For all users - The formatting bar will be relocated to the top of the message compose window, similar to the common "ribbon" you see in other Microsoft apps.
- For all users - When composing a new email message, the "Send", "Discard", and formatting bar will now be located at the top of the compose window.
- For users with "newest on top" option - When you reply to a message, the "Send", "Discard", and formatting bar will be located at top of the compose window.
Previously, those buttons and bar were located at the bottom of the message compose window.
This update will make the experiences across web and both classic and new Outlook for Windows have a similar UX.
The shortcut to send an email message will not change.
We apologize for the delay and are now proceeding with the rollout of this feature.
When this will happen:
We began rolling out mid-January and expect to complete by mid-April (previously mid-February).
How this will affect your organization:
Users will notice that some buttons have been updated with new locations to make the experience across Outlook more seamless.
What you need to do to prepare:
There is nothing you need to do for this update, but you might want to update your documentation and help desk.
MC455516 — (Updated) Automatic migration of legacy Office 365 Message Encryption to Microsoft Purview Message Encryption
>60 Days
Updated March 31, 2023: We have updated the timing for this change as well as provided additional information. Thank you for your patience.
Microsoft Purview Message Encryption will replace and retire the legacy Office 365 Message Encryption (OME) in the Exchange admin center. If you don’t do anything, Microsoft will process all mail flow rules that currently applies OME protection to Microsoft Purview Message Encryption protection. With this change, recipients will receive a much more customizable notification mail.
Retirement of OMEv1 is coming in 2 phases
- on June 30th OMEv1 mail flow rules become read-only or delete-only. No new rules or rule modifications will be allowed. These rules will be encrypt/decrypt with OMEv1
- One Dec 31 the OME v1 mail flow rules will be fully retired. All the OMEv1 rules will be automatcially process as OMEv2
For customers who need an exception to do OMEv1 mail flow rule updates between June 30th and Dec 31st, open a support ticket to request the exception.
Finally, we recommend all customers that use OMEv1 to receive email into a shared mailbox we highly recommend requesting the exception. We are targeting to release additional changes in Q3CY23 that will improve the shared mailbox experience.
How this will affect your organization:
Microsoft Purview Message Encryption is a more secure and flexible solution to provide encrypted mail to anyone inside or outside your organization, with an enhanced user experience for recipients. For example, with OME, all recipients receive an HTML attachment to open an encrypted mail. This has been greatly improved with Outlook clients for Microsoft 365 users who can now view the message inline. Non-Microsoft 365 users will instead receive a linked-based experience to open the mail. Additionally, supported attachments are also encrypted on download to protect sensitive data at rest.
*The encrypted attachments provide extra security by protecting the stored file at rest. Applications that can open Office documents may not be compatible with RMS protected Office documents. Admins can provide the same behavior as OME by enabling a global configuration to download Encrypt-only attachments without encryption: Set-IrmConfiguration – DecryptAttachmentForEncryptOnly $true
**By modifying existing the mail flow rules to apply Purview Message Encryption protection, external M365 recipients will receive encrypted mail containing a message.rpmsg attachment and supported Outlook clients can provide show the mail content directly in the application.
What you need to do to prepare:
If you want to compare the behavior before the deprecation, you can modify and test the changes with your mail flow rules by following the steps outlined in this documentation: Define mail flow rules to use Microsoft Purview Message Encryption
Learn more: How Microsoft Purview Message Encryption works
MC338988 — (Updated) REST API for On-Premises Mailboxes Preview Ending
>60 Days
Updated March 14, 2023: We have updated the timing of this change. Thank you for your patience.
Upcoming, we will be retiring the preview program enabling REST API access to on-premises mailboxes for Hybrid Exchange organizations.
Note: This will impact those who write code against Exchange mailboxes.
Key points
- Timing: Beginning early June (previously early March), we will begin to return errors for any requests made for mailboxes that remain on-premises.
- Action: Use Microsoft Graph for Exchange Online and Exchange Web Services (EWS) for Exchange Server on-premises
- Roll-out: tenant level
How this will affect your organization:
FAQ:
What API(s) should I use to work with Hybrid Orgs, where some mailboxes are in Exchange Online, and some are on Exchange Server?
- You should continue to use Microsoft Graph to work with Exchange Online mailboxes and use EWS to work with Exchange Server (on-premises) mailboxes.
Wasn't EWS going away?
- In 2018 we announced EWS in Exchange Online would no longer receive feature updates. But we have no plans currently to change the way EWS works on-premises, so using Microsoft Graph for Exchange Online and EWS for Exchange Server on-premises is the current recommendation.
- If you choose to continue using EWS against Exchange Online mailboxes, you should ensure that it uses OAuth (as Basic Authentication is being turned off in Exchange Online). You should also know that it now allows restricting access to mailboxes access through mailbox access policies.Authenticate an EWS application by using OAuth
- Application Access Policy Support in EWS
Where can I get help on using Microsoft Graph?
- One of the best places to start is Use the Microsoft Graph API and one of the best resources you can use to get practical is Use Graph Explorer to try Microsoft Graph APIs
Learn more:
Microsoft 365
MC538384 — Microsoft Search: Graph connector results in Bing 'All' tab
Rolled Out
Microsoft 365 Roadmap ID 93336
Microsoft Graph connectors results is available for users to query from Bing's 'All' tab. If the user's query contains a pattern with Custom vertical name, the system will return relevant results on top in the Bing 'All' tab from the Custom vertical content. This is applicable for Custom verticals defined on Graph connectors.
Examples: <query terms> in <vertical name> OR <vertical name> <query terms> etc.
When this will happen:
This is now available to users.
How this affects your organization:
This will help end users find their enterprise content easily in the Bing 'All' tab. It brings parity to Graph connectors content as this support is already available for Files and People content in Microsoft 365.
What you can do to prepare:
You may want to consider updating your training and documentation as appropriate and notifying your users of this change.
MC536884 — Microsoft Stream: Search a Video Transcript to Stream
30-60 Days
Microsoft 365 Roadmap ID 117583
This feature allows users who are viewing a video to search for keywords contained in the video transcript. This feature is available on video files that have transcripts and are stored in OneDrive or SharePoint.
When this will happen:
Rollout will begin in late April and is expected to be complete by early May.
How this will affect your organization:
Users can navigate through the search results and click on a portion of the transcript to be taken to the respective spot in the video. Users will need view or edit permissions on a file to search the transcript.
Note: This feature is for searching the transcript of a single video. Users also have the option to search the transcripts of all videos they have permissions to view using Microsoft 365 search.
What you need to do to prepare:
There is no action required from you at this time as this feature will be enabled automatically. For information on viewing, editing and managing video transcripts, please visit this documentation.
MC534742 — OneNote to Block Embedded Files that Have Dangerous Extensions
30-60 Days
OneNote is making an important change to how it treats embedded files that have dangerous extensions. Previously, OneNote would show users a warning dialog when users tried to open an embedded file with a dangerous extension; users could open the file by choosing OK in the dialog.
With this update, OneNote will show users a dialog that will let them know that their administrator has blocked them from opening the embedded file that has a dangerous extension, to also align with the same extensions that Outlook, Word, Excel and PowerPoint currently block. For a list of extensions, please visit Blocked attachments in Outlook.
If the user trusts the person that sent the embedded file and they need to open the embedded file, they can save the file to their local device and open the file from there.
This post is associated with Microsoft Roadmap ID 122277
When will this happen:
This change will begin rolling out in Version 2304 in Current Channel (Preview) in late April 2023 and is expected to be complete by late May 2023.
For more information about the release schedule, see OneNote will block embedded files that have dangerous extensions.
How this will affect your organization:
This change only affects OneNote for Microsoft 365 on devices running Windows.
The change does not affect OneNote on a Mac, OneNote on Android or iOS devices, OneNote on the web, or OneNote for Windows 10.
What you need to do to prepare:
You should make users and your support organization aware of this upcoming change and update any relevant training documentation.
You can also use a Group Policy setting to block additional extensions that you deem to be dangerous. For more information, see OneNote will block embedded files that have dangerous extensions.
MC534739 — Office Apps on the Web can create PDFs that inherit the source files sensitivity labels
>60 Days
Microsoft 365 Roadmap ID 117594
When using Microsoft 365 Apps on the web for Word, Excel, and PowerPoint, files that have a sensitivity label will also apply those labels to PDFs created in those apps. Documents that also have encryption cannot be converted to PDF without first removing protection.
When this will happen:
Standard Release: We will begin rolling out early May 2023 and expect to complete by early June 2023.
How this will affect your organization:
Users who are already configured for sensitivity labels will automatically persist their document's label to PDFs they create in Word, Excel, and PowerPoint for the web. If a document is protected with encryption, the PDF functionality is not available. Users who try to convert a protected Office document to PDF are prevented from completing the scenario without removing protection if they have the rights to do so.
What you need to do to prepare:
No action is required by admins or users to enable this functionality.
MC534311 — Planner: Task Email Notifications for GCC and DoD
<30 Days
Microsoft 365 Roadmap ID 122286
Task Email Notifications for GCC and DoD aims at bringing existing Planner email notifications to customers in GCC and DoD. The two main categories of notifications are: Assignment email notifications and Due date digest email.
When this will happen:
Standard Release: We will begin rolling out early April and expect to complete by mid-April.
How this will affect your organization:
GCC and DoD customers will start receiving email notifications for planner tasks.
Assignment Notification - When a task gets assigned to the user, the user gets an Assignment Email Notification.
Due date digest - This is a digest email that carries information about users' late and upcoming tasks. The email address from which the customer would receive the digest email will be no-reply@sharepoint.us.
What you need to do to prepare:
Admins please ensure your organization can receive emails from no-reply@sharepoint.us
MC532199 — Microsoft Excel: Get
>60 Days
We will be updating Get & Transform Data tools in Excel (aka Power Query).
When this will happen:
Starting June 1, 2023, Get & Transform Data tools in Excel will require additional libraries to be installed to continue working.
How does this affect your organization:
If your tenant has any existing Get & Transform Data (aka Power Query) queries, Power Query will not be accessible after the specified date. Any user who tries to use it after June 1st will receive an error message.
If you don’t use Power Query, you may dismiss this message.
What you need to do to prepare:
You will need to install:
- .NET framework v4.7.2 - for Power Query, in general
- WebView2 framework - for the From Web (Power Query) data connector
Inform your helpdesk and update documentation as appropriate.
For additional information, please refer to About Get & Transform (Power Query) in Excel.
MC531211 — Microsoft 365 admin center: Bring your own domain to use for Microsoft 365 product emails
<30 Days
Microsoft 365 Roadmap ID 103628
Email notifications from products within Microsoft 365 are sent out to users in various ways. In many cases the emails are sent out from the user but there are system emails, like alerts, batched, or digest emails. These are sent from various product-specific no-reply email addresses, like no-reply@sharepointonline.com, no-reply@planner.com, no-reply@project.com.
Opting into this change means that administrators can select a verified domain to use for these emails. All products and features mentioned in the supported products link provided below can utilize this feature across Microsoft 365 and the support article will be updated as products onboard to utilize the setting. Emails will be routed to your Exchange Online instance within your tenant and the emails will then be sent out to your users from your tenant.
When this will happen:
Targeted Release: We will begin rollout in late March and expect rollout to be complete by early April.
Standard Release: We will begin rollout in early April and expect rollout to be complete by mid-April.
How this will affect your organization:
No action is required, as this is an opt-in feature.
Should your organization opt-in to utilize the feature, then all products listed in the supported products list, will change to use your own domain that you have selected. Adminstrators can configure the “no-reply” prefix, and create a matching email address in Exchange, if they would like to monitor responses from users.
As the emails are now being sent out by your Exchange Online Instance, the emails will no longer have the [EXTERNAL] indicator as they are now internal emails. Exchange administrators can monitor this traffic within their Exchange Online logs and create an Exchange rule to manage what domains are allowed to send email to your users. Once the tenant has been opted-into the setting the rule can be set to block the generic email addresses, to reduce spam risk to users.
What you need to do to prepare:
As with all domains used to send email, it is recommended that Exchange Administrators configure the selected domain’s DNS records for SPF, MX, DKIM, and DMARC, as noted in Learn more about Exchange Online Email Routing. This also protects the domain from email spoofing and email providers can validate domain ownership.
This is especially the case if relaying has been enabled from your Exchange Online instance to on-Premises or external email services, as that ensures that messages can be validated by the recipient services.
Learn more:
- Select your own domain for Microsoft 365 email and see what products are supported
- Learn more about Exchange Online Email Routing
MC529417 — Microsoft 365 Reports in the admin center: new APIs for Microsoft 365 Apps usage reports - GCCH
Rolled Out
We are adding new Graph APIs within Microsoft Admin center to support Microsoft 365 Apps usage reports.
When this will happen:
We will begin rolling out mid-March and expect to complete rollout by late March 2023.
How this will affect your organization:
The new APIs will continue to give Admins new insights of Microsoft App usage in their organization.
What you need to do to prepare:
- In the admin center, go to the Reports > Usage page.
- From the dashboard homepage, click on the View more button > Active users - Microsoft 365 Apps card.
Update getM365AppUserDetail Graph API:
- GET /reports/getM365AppUserDetail(period='{period_value}')
- GET /reports/getM365AppUserDetail(date='{date_value}')
Update getM365AppUserCounts Graph API:
- GET /reports/getM365AppUserCounts(period='{period_value}')
Update getM365App PlatformUserCounts Graph API:
- GET /reports/getM365AppPlatformUserCounts(period='{period_value}')
To learn more, please visit these pages:
• Microsoft 365 Apps usage reports - Microsoft Graph beta | Microsoft Learn
• Authorization for APIs to read Microsoft 365 usage reports - Microsoft Graph | Microsoft Learn
• Microsoft 365 Reports in the admin center
MC527442 — Microsoft Search: People Centric Search in SharePoint and Office.com Available in GCC and GCC-High
Rolled Out
This post is associated with Microsoft Roadmap ID 117556
People centric search will soon let users pivot search results around a person. You will be able to explore and search within someone's content (while honoring access control), and view contact and organization information. This functionality will soon be available in the GCC and GCC-H environment.
When this will happen:
We will begin rolling out in mid-March and expect to complete rollout by late March.
How this will affect your organization:
When you select a person in People centric search, you will be able to search through their work, however, this will only include items that you already have permissions to view or modify.
What you need to do to prepare:
There is nothing required from you at this time. You may want to let your users know of this change and update any relevant training documentation. For additional information, please visit this documentation.
MC526134 — Microsoft 365 roadmap updates
Rolled Out
We're making some changes to the Microsoft 365 roadmap to better articulate preview availability and when features are scheduled to start rolling out.
When this will happen:
We will begin rolling out in mid-March and expect to complete by late March.
How this will affect your organization:
With this change we will be updating the labels for timing:
- Preview will become Preview Available
- GA will become Rollout Start
Image for reference, final view may be different.
Additionally, the help content and "Sort by General Availability" filter will be updated to align with the new labels. There is no change to the dates, we are simply renaming the fields to make the meaning of the dates clearer.
What you need to do to prepare:
You may consider updating your training and documentation as appropriate.
MC519243 — (Updated) Message Vertical to be released to special clouds (GCC and GCC-H) in Office.com
30-60 Days
Microsoft 365 Roadmap ID 117389
Updated March 22, 2023: We have updated the rollout timeline below. Thank you for your patience.
Office.com users can now easily get messages from both Outlook and Teams that they previously shared with their colleagues. All they need to do is search for the particular communication and navigate to the messages tab. This feature which is currently available worldwide will now be available to GCC and GCC-H customers.
When this will happen:
Standard Release: We will begin rolling out this feature mid-April (previously late March) and expect to complete in mid-May (previously late April).
How this will affect your organization:
This feature will be shipped turned on by default and for organizations that don't use Teams or/and Outlook, there is an option to disable this from the Microsoft Admin Center. If your organisation uses both Team or/and Outlook, administrators do not need to do anything.
What you need to do to prepare:
Administrators need to inform their users about this new feature so that they can learn about it and use it to easily get Outlook and Teams messages when they are using Office.com without having to switch to the apps.
MC514084 — (Updated) Microsoft 365 admin center: Windows 365 cloud PC advanced deployment guide
30-60 Days
Microsoft 365 Roadmap ID 102406
Updated March 30, 2023: We have updated the rollout timing below. Thank you for your patience.
The Advanced deployment guides & assistance page in the Microsoft 365 admin center and the setup.microsoft.com website will have a new guide to help admins plan, deploy, and scale Windows 365 Enterprise in their organization. Windows 365 is a cloud-based service that provisions and hosts Cloud PCs as virtual machines for users. The guide includes a checklist with Cloud PC configuration tasks, best practices, tools, and recommendations based on a tenant's configuration.
When this will happen:
This guide will be available to Targeted Release in April 2023 and Standard Release in May 2023 (previously March). It can be found on the Advanced deployment guides & assistance page, and shortly after, on setup.microsoft.com.
How this will affect your organization:
Admins will use the Windows 365 Cloud PC advanced deployment guide for recommendations on how to make key decisions and identify prerequisites and tasks needed to deploy Cloud PCs in accordance with their org’s requirements. The guide is organized by IT area (Azure, networking, identity, management, security, and applications) to help admins work with multiple groups and staff members. Admins can track the status of each task within the guide and share tasks with others via email.
What you need to do to prepare:
You don’t need to do anything to prepare for this change.
MC512918 — (Updated) Microsoft Edge to replace built-in PDF engine with Adobe Acrobat PDF engine
>60 Days
Updated March 17, 2023: We have updated the content below with additional information for clarification. Thank you for your patience.
As part of the Adobe and Microsoft collaboration to re-envision the future workplace and digital experiences, we are natively embedding the Adobe Acrobat PDF engine into the Microsoft Edge built-in PDF reader. With the use of the Adobe Acrobat PDF engine, users will have a unique PDF experience that includes higher fidelity for more accurate colors and graphics, improved performance, strong security for PDF handling, and greater accessibility – including better text selection and read-aloud narration. There will be no loss of functionality with the use of the Adobe Acrobat PDF engine and these capabilities will continue to be free of cost. Organizations with Microsoft 365 E5 subscriptions can also view and validate certificate-based signatures and view PDF files protected through Microsoft Information Protection (MIP) at no extra cost.
Organizations with an existing Adobe Acrobat subscription can use the no-cost extension inside Microsoft Edge to unlock their subscription features—such as the ability to edit text and images, convert PDFs to other file formats, and combine files. Those who do not have an Adobe Acrobat subscription can purchase a license that enables access to these advanced features inside Microsoft Edge via an extension. There is no requirement to purchase an Adobe Acrobat subscription to use the Microsoft Edge built-in PDF free capabilities.
When this will happen:
Starting in March 2023, organizations can opt-in to use the Adobe Acrobat PDF engine in the Microsoft Edge built-in PDF reader via Intune policy. The policy will be available as soon as the Adobe Acrobat PDF engine is available. After opting-in, organizations have the option to opt-out of this experience via the same Intune policy.
To meet the needs of organizations with managed devices, the transition to the built-in Microsoft Edge PDF reader with the Adobe Acrobat PDF engine will occur in phases:
- March 2023: Unmanaged device rollout will begin in March 2023. Managed devices can opt-in using policy via Intune, SCCM or Group Policy.
- September 2023: Rollout to organizations will begin no earlier than September 2023. Organizations with managed devices may opt out of this experience via Intune policy.
- March 31st, 2024: The legacy PDF engine in the Microsoft Edge PDF reader is scheduled to be removed (and opt-out no longer available) on March 31st, 2024.
How this will affect your organization:
As rollout begins in March 2023, there will be no changes to managed devices in organizations unless they choose to opt in. With opt-in, the built-in Microsoft Edge PDF solution with the Adobe Acrobat PDF engine will have full feature parity with the legacy Microsoft Edge PDF solution. No functionality will be lost. Users will also gain higher fidelity for more accurate colors and graphics, improved performance, strong security for PDF handling, and greater accessibility – including better text selection and read-aloud narration. Users will see an unobtrusive Adobe brand mark in the bottom corner of their PDF view. These users will also see an option to try the advanced features, such as converting PDFs, combining files, editing text and images. Users can sign in with their existing Adobe Acrobat subscription or can select the option to purchase an Adobe Acrobat subscription and download the Adobe Acrobat extension to use those features in Microsoft Edge.
What you need to do to prepare:
To prepare, we recommend selecting users to test the addition of the Adobe Acrobat PDF engine into Microsoft Edge on the stable release in March 2023. For managed devices, admins in commercial organizations can enable or disable the “NewPDFReaderEnabled” policy to test the Adobe Acrobat PDF engine.
To hide the notification to try the paid Adobe Acrobat features, admins will need to enable the “ShowAcrobatSubscriptionButton” policy.
Starting no earlier than September 1, 2023, the rollout to organizations will begin. For organizations wanting to opt out of this experience, admins will need to disable the “NewPDFReaderEnabled” policy. Organizations can opt-out until the legacy Microsoft Edge PDF engine is removed, which is scheduled for March 31st, 2024.
Additional information:
- Read about the Microsoft and Adobe partnership here
- Read about the Microsoft Edge and Adobe Acrobat PDF announcement here
- Read about the joint approach by Microsoft and Adobe engineering teams to secure the PDF experience here
We always value feedback and questions from our customers. Feel free to submit either feedback or questions via Message Center.
MC498601 — (Updated) Pricing adjustments for Microsoft 365 Government, effective April 1, 2023
Rolled Out
Updated March 20, 2023: This is an update to the below price communication. GCC High and DOD G1 and G3 SKUs were not updated March 2023 and will be updated on April 1, 2023. If you have any questions, please reach out to your Microsoft account partner for support.
On August 2021 we announced an update to our pricing for Microsoft 365 (which applies to all commercial customers: Enterprise, US Government, and Business). You can find the full blog from our initial announcement here: New pricing for Microsoft 365 | Microsoft 365 Blog.
In the case of Microsoft 365 Government, due to local regulations, the price update was planned in a phased manner. Therefore, on April 1, 2023, the updated prices will be effective for the following suites:
- Office 365 G1 (+10%)
- Office 365 G3 (+5%)
- Microsoft 365 G3 (+2%)
This price update builds on the product innovation we’ve delivered over the past several years to meet the changing needs of customers. Since the initial release we’ve added new capabilities such as Teams, PowerApps, Power Automate, Microsoft Purview, Microsoft Defender, Whiteboard and many more applications and features2.
**Please note that product available will vary by cloud environment please reference the Microsoft 365 Government service descriptions and Microsoft 365 Roadmap for more information.
We also announced the extension of unlimited dial-in across our paid enterprise, business, frontline, and government suites, enabling users to dial-in and join a Teams meeting from virtually any device.
If you’re a Microsoft 365 Government customer and have questions about your licensing plans please reach out to your Microsoft account team or partner for support.
MC452253 — (Updated) Announcing the New Look of Office for the Web
>60 Days
Microsoft 365 Roadmap ID 87307
Updated March 14, 2023: We have updated the rollout timeline below. Thank you for your patience.
We are excited to announce a new look in Office for the Web. We've changed the visuals to give you a clean modern look to help you focus, but nothing has moved. We will start flighting at this date.
When this will happen:
Standard Release: We will begin rolling out early May (previously mid-December) and expect to complete rollout by late June (previously late February).
How this will affect your organization:
People will notice the look and feel changes and might have questions if commands moved. We have not moved location of commands nor changed any icons. Functionality and how you use things will not be affected.
What you need to do to prepare:
There is no action required from you at this time. We recommend sending this link to your organization for more information and updating any relevant training materials as necessary.
MC295027 — (Updated) Rich text and images in Planner task notes
<30 Days
Microsoft 365 Roadmap ID 85688
Updated March 14, 2023: We have updated the rollout timeline below. Thank you for your patience.
We are adding support for rich text (bold, italics, underline, etc.) in the Planner task notes field. Support for images is coming in the future.
NOTE: We will update this post once we have Microsoft Graph documentation for the new rich text task notes field available.
When this will happen:
We expect to begin rolling out the new rich text task notes field in late March (previously mid-February) and we expect to complete the rollout by mid-April (previously early March).
How this will affect your organization:
To support this capability, we are introducing a new rich text enabled task notes field in the Planner Microsoft Graph API. This will result in two task notes fields in our API – the new “rich text task notes field” and the existing “plain text task notes field.” When this feature launches, Planner for the Web and for Teams (Tasks app) will support rich text in task notes. Other Planner experiences in iOS, Android, SharePoint, and Power Automate will only support plain text task notes, but we plan to update these apps to support rich text at a later date.
When this feature update is deployed, all existing task notes content will be preserved in the new rich text enabled task notes field, so users will be able to continue viewing and editing notes without interruption.
We will maintain compatibility between the rich text task notes field and plain text task notes field by ensuring both fields’ contents stay in sync.
If a user edits the rich text task notes field, all content is synced to the plain text task notes field automatically. Any rich content is converted to plain text and synced to the plain text task notes field.
If a user edits the plain text task notes field via the Microsoft Graph API or via a client which only supports the plain text field, the contents in the plain text task notes field is synced to the rich text task notes field without modification. Therefore edits to the plain text task notes field will result in the removal of any pre-existing rich text, or text formatting in the rich text notes field.
What you need to do to prepare:
If your organization has custom applications interacting with our Microsoft Graph Planner API, make sure to update the apps to support the rich text task notes field as soon as it is available to take advantage of the new notes capabilities. We will maintain support for the existing plain text task notes field in our Microsoft Graph Planner API for at least 36 months.
If your organization has applications or workflows which parse the task notes to trigger logic based off contents in the notes field, we recommend users continue to input only plain text in task notes and not apply text formatting into task notes. Such apps should also be updated to avoid parsing task notes or applying logic to contents in the task notes as these are not recommended uses of the task notes field in our API.
Microsoft 365 IP and URL Endpoint Updates |
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.