- Home
- Outlook
- General Discussion
- Re: How automatically delete ALL messages from sender ending in ".co"
How automatically delete ALL messages from sender ending in ".co"
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 12 2022 07:21 PM
It seems like this should be simple...
I want to automatically delete spam I'm getting every day that ends with .co. NOT .com, but .co. They're all from different addresses, so blocking them doesn't work.
I can create a rule, but how do I get it to delete just things that end in .co?
OR, is there some other simple way to block everything from .co
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 12 2022 08:18 PM
You can use regex to match sender address under rules:
\.co$
Expected result:
example.co.hk - not match
example.co - match
example.com - not match
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 13 2022 09:20 AM
Thanks. That looks like what I was trying to find!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 13 2022 02:30 PM
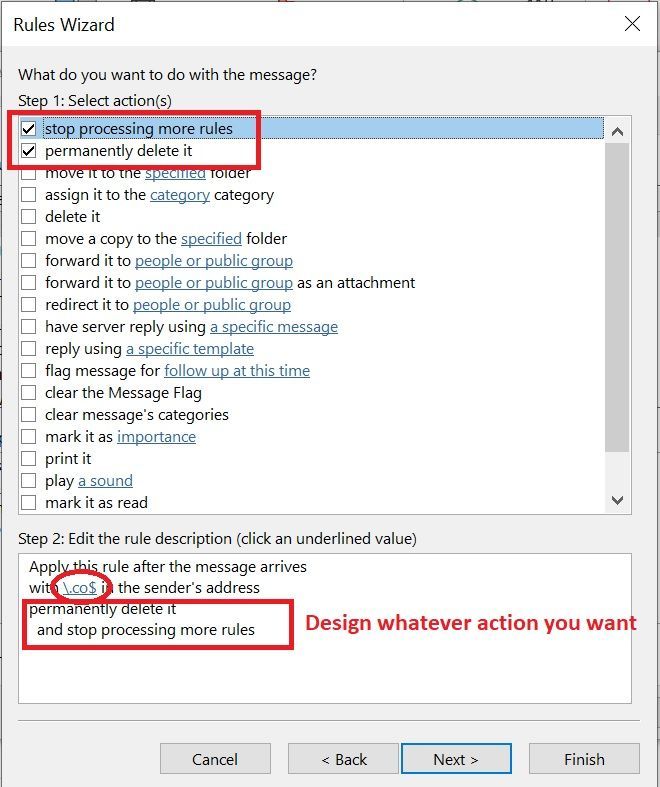
Apply this rule after the message arrives
with \.co$ in the sender's address
display SPAM in the New Item Alert windows
move it to the co_spam folder
Do I have the text incorrect? Does Outlook not like just moving it? - I'd like to see that it works before I start clobbering things.
Here are a couple of the addresses
Nerve Control 911 <Email address removed>
Power Pod <Email address removed>
I don't know if this will help, but here's one of the message headers:
Return-Path: <Email address removed>
Delivered-To: me
Received: from ecngx270.inmotionhosting.com
by ecngx270.inmotionhosting.com with LMTP
id oO8gLNdWLmJJCB4AI3UA7A
(envelope-from <Email address removed>)
for <me>; Sun, 13 Mar 2022 16:40:55 -0400
Return-path: <Email address removed>
Envelope-to: me
Delivery-date: Sun, 13 Mar 2022 16:40:55 -0400
Received: from gemward.co ([163.123.140.48]:59832)
by ecngx270.inmotionhosting.com with esmtp (Exim 4.94.2)
(envelope-from <Email address removed>)
id 1nTV1K-008L05-Tn
for me; Sun, 13 Mar 2022 16:40:55 -0400
Date: Sun, 13 Mar 2022 15:37:46 -0500
From: "Power Pod" <Email address removed>
MIME-Version: 1.0
Precedence: bulk
To: <me>
Subject: Power Pod gives you HOURS more power, and it fits on any keychain!
Message-ID: <Email address removed>
Content-Type: text/html; charset=ISO-8859-1
Content-Transfer-Encoding: 7bit
X-Spam-Status: No, score=3.3
X-Spam-Score: 33
X-Spam-Bar: +++
X-Ham-Report: Spam detection software, running on the system "ecngx270.inmotionhosting.com",
has NOT identified this incoming email as spam. The original
message has been attached to this so you can view it or label
similar future email. If you have any questions, see
root\@localhost for details.
Content preview: Don’t Get Stranded by a Dead Phone Battery! Power Pod gives
you HOURS more power, and it fits on any keychain! INSTANT POWER WHEN YOU
NEED IT MOST
Content analysis details: (3.3 points, 5.0 required)
pts rule name description
---- ---------------------- --------------------------------------------------
0.0 URIBL_BLOCKED ADMINISTRATOR NOTICE: The query to URIBL was
blocked. See
http://wiki.apache.org/spamassassin/DnsBlocklists#dnsbl-block
for more information.
[URIs: havemean.life]
0.8 BAYES_50 BODY: Bayes spam probability is 40 to 60%
[score: 0.4974]
-0.0 SPF_PASS SPF: sender matches SPF record
2.0 PDS_OTHER_BAD_TLD Untrustworthy TLDs
[URI: www.havemean.life (life)]
-0.0 SPF_HELO_PASS SPF: HELO matches SPF record
0.0 HTML_MESSAGE BODY: HTML included in message
0.1 MIME_HTML_ONLY BODY: Message only has text/html MIME parts
-0.0 T_SCC_BODY_TEXT_LINE No description available.
0.4 HTML_MIME_NO_HTML_TAG HTML-only message, but there is no HTML
tag
X-Spam-Flag: NO
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 14 2022 05:12 AM
I tried from server side and seems working, below link I searched from the Internet may help:
https://www.reddit.com/r/Outlook/comments/q6nbd4/how_to_block_only_co_and_not_com/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 14 2022 01:54 PM
What does "from the server side" mean? I'm sitting in Outlook 2019 on my desktop, creating a rule. Would it work differently than "from the server"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 15 2022 06:43 AM
I am saying in case environment hosting Exchange server \ Exchange Online, we can setup rule from the backend, and seem the rules are not 100% matched with the one we setup under Microsoft Outlook.
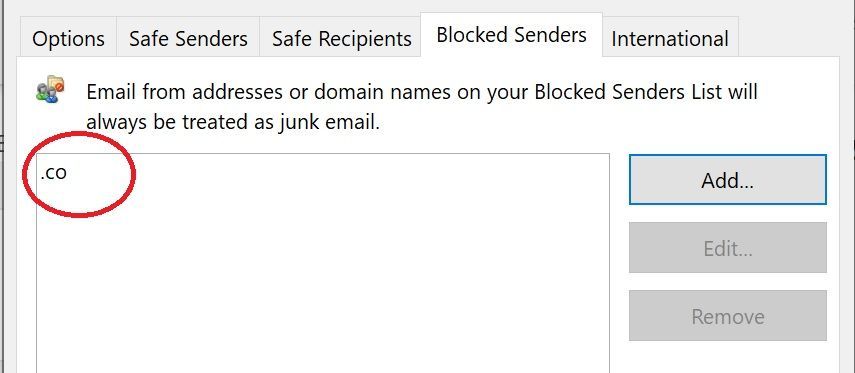
For your case, I did a search and seem we can handle in TDL (Top Domain Level) under Outlook Junk option, like below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 15 2022 01:46 PM
"in case environment hosting Exchange server \ Exchange Online, we can setup rule from the backend"
I don't know what the ISP is using, but the Outlook 2019 email is ordinary POP. I'm not in an exchange server environment on my end. Why that would matter, I don't know, but it doesn't appear to work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 15 2022 07:08 PM
It doesn't matter, just different ways to handle in case you own Exchange Server or Exchange Online, did you try the suggestion provided? To add .co under 'Junk' from Outlook?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 19 2022 08:13 PM
Thanks for the help.